山东省网络技术大赛初赛
三道题目,一个web,一个杂项,一个逆向
气抖冷,为什么不考pwn
1,sql注入
payload如下
user: admin' or 1=1 # pass: 1
连个waf都不加,我与阁下无冤无仇,阁下为何把我当憨批???
好歹以为是个盲注,好家伙,直接给👴来个万能密码,5秒钟解决,有什么好说的
2,图片隐写
雪宝牛逼
stegsolve梭出来一张二维🐎

扫出来一串十六进制
解码脚本
string = "03F30D0A79CB05586300000000000000000100000040000000730D0000006400008400005A
00006401005328020000006300000000030000001600000043000000737800000064010064020064030064040
0640500640600640700640300640800640900640A00640600640B00640A00640700640800640C00640C00640D00640E0064
0900640F006716007D00006410007D0100781E007C0000445D16007D02007C01007400007C0200830100377D01007155
00577C010047486400005328110000004E6966000000696C00000069610000006967000000697B0000006933000000693800000069
35000000693700000069300000006932000000693400000069310000006965000000697D000000740000000028010000007403000000
636872280300000074030000007374727404000000666C6167740100000069280000000028000000007304000000312E707952030000
0001000000730A0000000001480106010D0114014E280100000052030000002800000000280000000028000000007304000000312E7
07974080000003C6D6F64756C653E010000007300000000" print string.decode("hex")
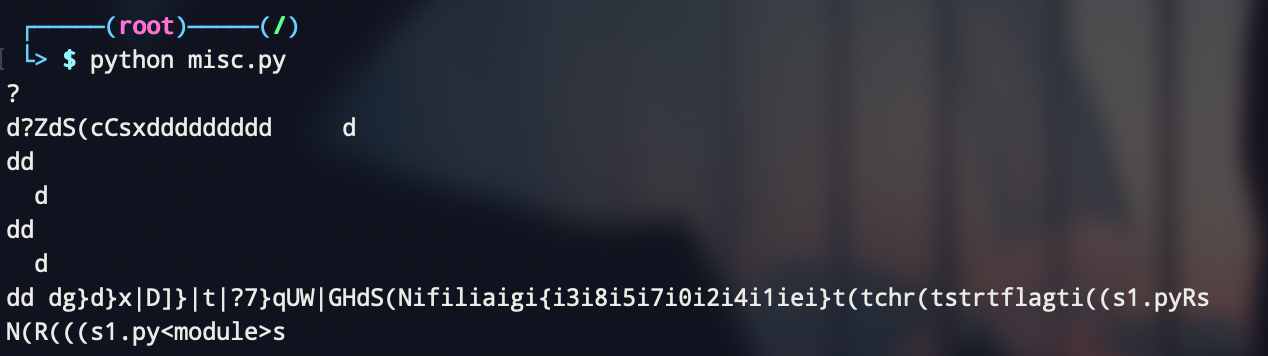
仔细观察,可以发现1.py<module>字样,而且输出疑似flag字段的字符串,考虑是pyc文件,反编译一下
反编译得到源文件,直接调用解密函数即可
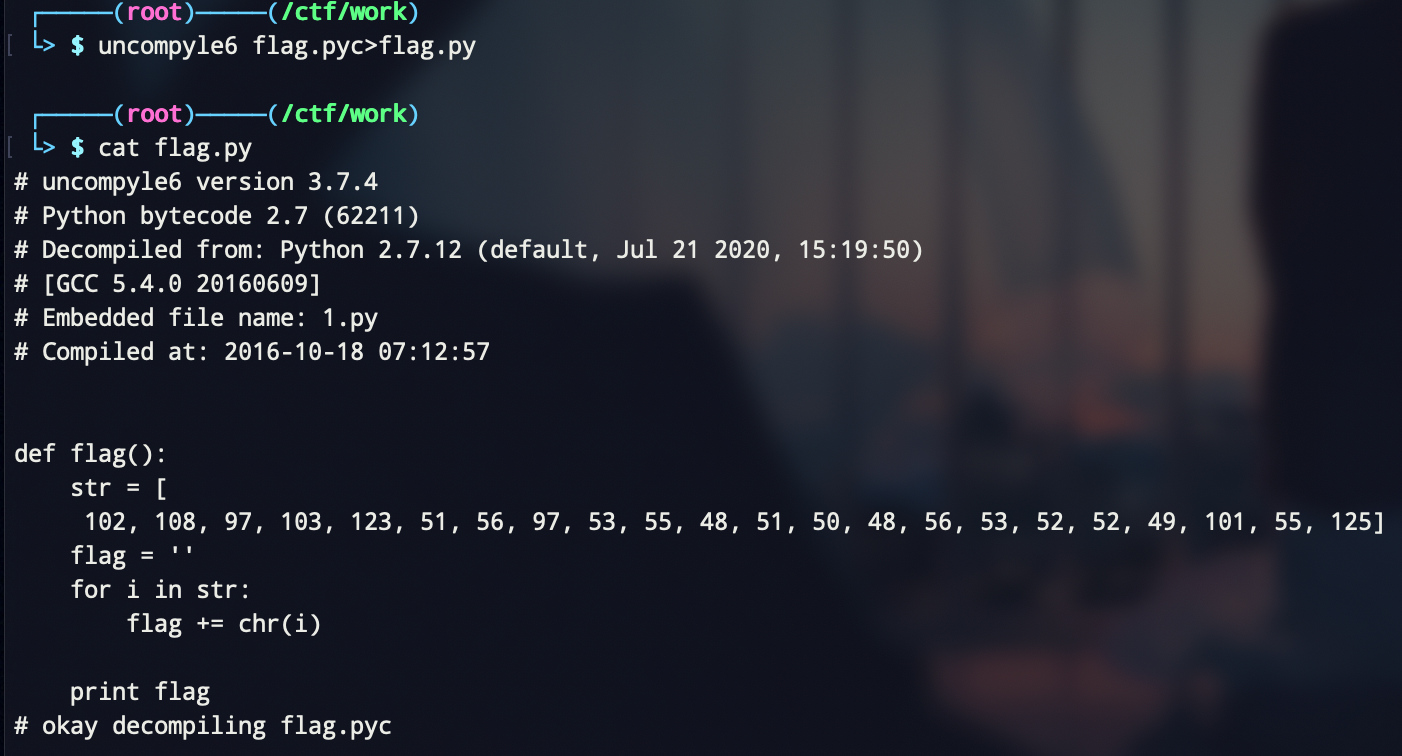
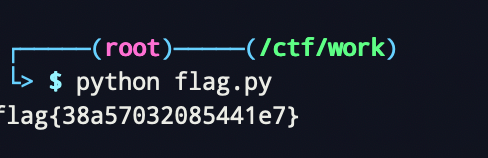
# uncompyle6 version 3.7.4 # Python bytecode 2.7 (62211) # Decompiled from: Python 2.7.12 (default, Jul 21 2020, 15:19:50) # [GCC 5.4.0 20160609] # Embedded file name: 1.py # Compiled at: 2016-10-18 07:12:57 def flag(): str = [ 102, 108, 97, 103, 123, 51, 56, 97, 53, 55, 48, 51, 50, 48, 56, 53, 52, 52, 49, 101, 55, 125] flag = '' for i in str: flag += chr(i) print flag # okay decompiling flag.pyc flag()
3,第三个100分,应该不难,可惜没时间看了,本地没有java反编译的工具,下载来不及了


