k8s基于CA签名的双向数字证书认证(三)
1、设置kube-apiserver的CA证书相关的文件和启动参数
1)创建CA证书和私钥相关的文件
openssl genrsa -out ca.key 2048 openssl req -x509 -new -nodes -key ca.key -subj "/CN=lile.com" -days 5000 -out ca.crt openssl genrsa -out server.key 2048
2)master_ssl.cnf文件
[req] req_extensions=v3_req distinguished_name=req_distinguished_name [req_distinguished_name] [v3_req] basicConstraints=CA:FALSE keyUsage=nonRepudiation, digitalSignature, keyEncipherment subjectAltName=@alt_names [alt_names] DNS.1=kubernetes DNS.2=kubernetes:default DNS.3=kubernetes:default.svc DNS.4=kubernetes:default.svc.cluster.local DNS.5=ip-172-29-1-113 IP.1=169.169.0.1 IP.2=172.29.1.113
DNS.5:主机名
IP.1:集群IP,--service-cluster-ip-range=169.169.0.0/16,这里设置的取第一个
IP.2:主机IP
openssl req -new -key server.key -subj "/CN=ip-172-29-1-113" -config master_ssl.cnf -out server.csr openssl x509 -req -in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial -days 5000 -extensions v3_req -extfile master_ssl.cnf -out server.crt
3)在apiserver的配置文件中加上以下参数,并把8080端口参数去掉
KUBE_CA="--client-ca-file=/var/run/kubernetes/ca.crt" KUBE_PRIVATE_KEY="--tls-private-key-file=/var/run/kubernetes/server.key" KUBE_CERT_FILE="--tls-cert-file=/var/run/kubernetes/server.crt" KUBE_INSECURE="--insecure-port=0" KUBE_SECURE_PORT="--secure-port=443"
--client-ca-file:代表CA根证书文件
--tls-cert-file:服务端私钥文件
--tls-private-key-file:服务端证书文件
2、设置kube-controller-manager的客户端证书、私钥和启动参数
1)
openssl genrsa -out cs_client.key 2048 openssl req -new -key cs_client.key -subj "/CN=k8s-node" -out cs_client.csr openssl x509 -req -in cs_client.csr -CA ca.crt -CAkey ca.key -CAcreateserial -days 5000 -out cs_client.crt
2)创建kubeconfig文件
vim /etc/kubernetes/kubeconfig
apiVersion: v1 kind: Config users: - name: controllermanager user: client-certificate: /var/run/kubernetes/cs_client.crt client-key: /var/run/kubernetes/cs_client.key clusters: - name: local cluster: certificate-authority: /var/run/kubernetes/ca.crt contexts: - context: cluster: local user: controllermanager name: my-context current-context: my-context
3)修改启动参数
KUBE_PRIVATE_KEY="--service-account-private-key-file=/var/run/kubernetes/server.key" KUBE_CA_FILE="--root-ca-file=/var/run/kubernetes/ca/crt" KUBE_CONFIG="--kubeconfig=/etc/kubernetes/kubeconfig"
3、设置kube-schedule启动参数
KUBE_MASTER="--master=http://172.29.1.113:443" KUBE_CONFIG="--kubeconfig=/etc/kubernetes/kubeconfig"
4、设置Node节点上的Kubelet客户端
1)拷贝master上的ca.crt和ca.key到node节点上
openssl genrsa -out kubelet_client.key 2048 openssl req -new -key kubelet_client.key -subj "/CN=k8s-node" -out kubelet_client.csr openssl x509 -req -in kubelet_client.csr -CA ca.crt -CAkey ca.key -CAcreateserial -days 5000 -out kubelet_client.crt
2)创建kubeconfig文件
vim /etc/kubernetes/kubeconfig
apiVersion: v1 kind: Config users: - name: kubelet user: client-certificate: /var/run/kubernetes/kubelet_client.crt client-key: /var/run/kubernetes/kubelet_client.key clusters: - name: local cluster: server: https://172.29.1.113:443 certificate-authority: /var/run/kubernetes/ca.crt contexts: - context: cluster: local user: kubelet name: my-context current-context: my-context
3)修改kubelet的启动参数(api_servers的地址 也要改)
KUBE_CONFIG="--kubeconfig=/etc/kubernetes/kubeconfig"
5、修改kube-proxy的启动参数
KUBE_MASTER="--master=http://172.29.1.113:443" KUBE_CONFIG="--kubeconfig=/etc/kubernetes/kubeconfig"
6、测试访问
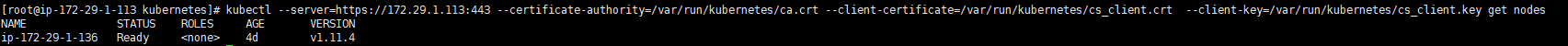
kubectl --server=https://172.29.1.113:443 --certificate-authority=/var/run/kubernetes/ca.crt --client-certificate=/var/run/kubernetes/cs_client.crt --client-key=/var/run/kubernetes/cs_client.key get nodes
作者:李先生
-------------------------------------------
个性签名:在平凡中坚持前行,总有一天会遇见不一样的自己!
如果觉得这篇文章对你有小小的帮助的话,记得在右下角点个“推荐”哦,博主在此感谢!
万水千山总是情,打赏一分行不行,所以如果你心情还比较高兴,也是可以扫码打赏博主,哈哈哈(っ•̀ω•́)っ✎⁾⁾!



微信公众号 微信打赏 支付宝打赏
posted on 2018-11-16 18:09 Captain_Li 阅读(2422) 评论(0) 编辑 收藏 举报


