Prometheus做API接口监控
运维过程中,很多时候,业务应用会出现假死的情况,应用进程正常,但是无法提供服务,此时监控进程没有任何意义,就需要监控接口
接口监控的方法很多,可以用链路监控,可以写脚本进行监控
由于监控整体采用的是prometheus,所以这里就直接用blackbox_exporter来做接口的监控
blackbox_exporter可以通过http、https、dns、tcp、ICMP对target进行探测,dns、tcp、ICMP都相对简单,我这边主要是要监控一个登录接口,所以要用https来进行探测,具体配置方法如下
部署blockbox_exporter
# 创建blackbox_exporter的目录
cd /usr/local/blackbox_exporter
# 下载blackbox_exporter的包
wget https://github.com/prometheus/blackbox_exporter/releases/download/v0.19.0/blackbox_exporter-0.19.0.linux-amd64.tar.gz
# 解压
tar -zxvf blackbox_exporter-0.19.0.linux-amd64.tar.gz
# 重命名
mv blackbox_exporter-0.19.0.linux-amd64.tar.gz blackbox_exporter用systemd管理blackbox_exporter
cat > /etc/systemd/system/blackbox_exporter.service << "EOF"
[Unit]
Description=Blackbox Exporter
Wants=network-online.target
After=network-online.target
[Service]
User=root
ExecStart=/usr/local/blackbox_exporter/blackbox_exporter/blackbox_exporter --config.file=/usr/local/blackbox_exporter/blackbox_exporter/blackbox.yml
Restart=on-failure
[Install]
WantedBy=default.target
EOF对于blackbox_exporter管理的话,还有很多方法,你可以直接nohup后台启动,也可以通过supervisor进行启动,我习惯用systemd进行管理
然后添加开机自启动
systemctl daemon-reload
systemctl enable blackbox_exporter
systemctl start blackbox_exporter因为没指定日志输出,所以是输出到message日志中
默认带的blacbox.yml只是个最简单配置,不能满足需求,所以配置blackbox.yml中,添加一个模块
modules:
xhj_login: # 模块名称,prometheus配置文件中要匹配
prober: http # 协议
timeout: 30s # 超时时间
http: # 模块的采集协议
method: POST # http请求的方法
preferred_ip_protocol: "ip4" # 使用的ipv4协议
headers: # 配置post请求的header头
Content-Type: application/json
body: ''{"mobile": "13572801829", "password": "ZWB123wyl"}'' # post请求参数
配置完成后,保存blackbox.yml,启动blackbox_exporter
systemctl start blackbox_exporter
systemctl status blackbox_exporter
● blackbox_exporter.service - Blackbox Exporter
Loaded: loaded (/etc/systemd/system/blackbox_exporter.service; enabled; vendor preset: disabled)
Active: active (running) since Tue 2022-01-04 21:33:28 CST; 6s ago
Main PID: 24679 (blackbox_export)
Tasks: 7
Memory: 1.9M
CGroup: /system.slice/blackbox_exporter.service
└─24679 /data/prometheus/blackbox_exporter/blackbox_exporter/blackbox_exporter --config.file=/data/prometheus/blackbox_exporter/blackbox_exporter/blackbox....
Jan 04 21:33:28 systemd[1]: Started Blackbox Exporter.
Jan 04 21:33:28 blackbox_exporter[24679]: level=info ts=2022-01-04T13:33:28.173Z caller=main.go:224 msg="Starting blackbox_exporter" version="(v...33d1ed0)"
Jan 04 21:33:28 blackbox_exporter[24679]: level=info ts=2022-01-04T13:33:28.173Z caller=main.go:225 build_context="(go=go1.16.4, user=root@2b025...2:56:44)"
Jan 04 21:33:28 blackbox_exporter[24679]: level=info ts=2022-01-04T13:33:28.173Z caller=main.go:237 msg="Loaded config file"
Jan 04 21:33:28 blackbox_exporter[24679]: level=info ts=2022-01-04T13:33:28.174Z caller=main.go:385 msg="Listening on address" address=:9115
Jan 04 21:33:28 blackbox_exporter[24679]: level=info ts=2022-01-04T13:33:28.174Z caller=tls_config.go:191 msg="TLS is disabled." http2=false
Hint: Some lines were ellipsized, use -l to show in full.配置prometheus
# blackbox
- job_name: "blackbox"
metrics_path: /probe
params:
module: [xhj_login]
static_configs:
- targets:
- https://xxx.aaa.com/api/pc/user/login/password
relabel_configs:
- source_labels: [__address__]
target_label: __param_target
- source_labels: [_param_target]
target_label: instance
- target_label: __address__
replacement: 172.17.0.1:9115
……省略
……省略配置完成后,保存,热加载prometheus配置文件
curl -X POST http://localhost:9090/-/reload加载完成后,通过prometheus的UI查看下targets
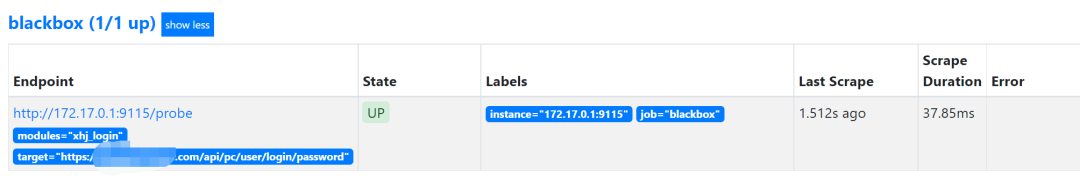
此时其实可以通过被请求端的日志就可以看到blackbox_exporter发起的请求了,我们也可以通过curl请求blackbox_exporter来进行查看
# 注意这里用&符号链接多个参数,需要转义
curl http://172.17.0.1:9115/probe?target=https://xxx.aaa.com/api/pc/user/login/password\&module=xhj_login\&debug=true
# 查看返回结果
Logs for the probe:
ts=2022-01-04T14:10:32.979231489Z caller=main.go:320 module=xhj_login target=https://xxx.aaa.com/api/pc/user/login/password level=info msg="Beginning probe" probe=http timeout_seconds=30
ts=2022-01-04T14:10:32.979411891Z caller=http.go:335 module=xhj_login target=https://xxx.aaa.com/api/pc/user/login/password level=info msg="Resolving target address" ip_protocol=ip4
ts=2022-01-04T14:10:32.986112778Z caller=http.go:335 module=xhj_login target=https://xxx.aaa.com/api/pc/user/login/password level=info msg="Resolved target address" ip=1.1.1.1
ts=2022-01-04T14:10:32.986225541Z caller=client.go:251 module=xhj_login target=https://xxx.aaa.com/api/pc/user/login/password level=info msg="Making HTTP request" url=https://1.1.1.1/api/pc/user/login/password host=xxx.aaa.com
ts=2022-01-04T14:10:33.05701057Z caller=main.go:130 module=xhj_login target=https://xxx.aaa.com/api/pc/user/login/password level=info msg="Received HTTP response" status_code=200
ts=2022-01-04T14:10:33.057095911Z caller=main.go:130 module=xhj_login target=https://xxx.aaa.com/api/pc/user/login/password level=info msg="Response timings for roundtrip" roundtrip=0 start=2022-01-04T22:10:32.986352765+08: