1:环境
2:安装OpenSSL
[root@virtual_host ~]# yum install -y openssl openssl-devel
3:配置OpenSSL
今天的泛域名就是`*.layzer.com`
[root@virtual_host ~]# vim /etc/pki/tls/openssl.cnf
[ req ]
………………
# 将如下配置的注释放开,低版本的OpenSSL不支持,可以不放开注释
# req_extensions = v3_req # The extensions to add to a certificate request
………………
[ v3_req ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
# 添加如下行
subjectAltname = @SubjectAlternativename
# 同时增加如下信息
[SubjectAlternativename]
DNS.1 = layzer.com
DNS.2 = *.layzer.com
4:开始创建证书
[root@virtual_host ssl]# pwd
/root/ssl
# 创建CA私钥
[root@virtual_host ssl]# openssl genrsa -out CA.key 2048
# 制作CA公钥
[root@virtual_host ssl]# openssl req -sha256 -new -x509 -days 36500 -key CA.key -out CA.crt -config /etc/pki/tls/openssl.cnf
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:SH
Locality Name (eg, city) [Default City]:ShangHai
Organization Name (eg, company) [Default Company Ltd]:BTC
Organizational Unit Name (eg, section) []:LAYZER
Common Name (eg, your name or your server's hostname) []:LayzerSign CA
Email Address []:layzer@163.com
当然上述的公钥制作方式需要交互式输入信息,如果不想频繁输入,那么可以使用如下命令:
openssl req -sha256 -new -x509 -days 36500 -key CA.key -out CA.crt -config /etc/pki/tls/openssl.cnf -subj "/C=CN/ST=SH/L=ShangHai/O=BTC/OU=LAYZER/CN=LayzerSign CA/emailAddress=layzer@163.com"
上面做完之后我们看看现在我们的到了什么
[root@virtual_host ssl]# ls
CA.crt CA.key
5:自签发泛域名证书
我们的操作步骤为:
1:生成域名私钥
2:生成证书签发请求文件
3:使用自签署的CA,生成域名公钥
1:生成 layzer.com.key 密钥
[root@virtual_host ssl]# openssl genrsa -out layzer.com.key 2048
2:生成 layzer.com.csr 证书签发请求 交互式
[root@virtual_host ssl]# openssl req -new -sha256 -key layzer.com.key -out layzer.com.csr -config /etc/pki/tls/openssl.cnf
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:SH
Locality Name (eg, city) [Default City]:ShangHai
Organization Name (eg, company) [Default Company Ltd]:BTC
Organizational Unit Name (eg, section) []:LAYZER
Common Name (eg, your name or your server's hostname) []:*.layzer.com # 这个就是要申请的泛域名
Email Address []:layzer@163.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:BTC
当然了这个也有非交互式
openssl req -new -sha256 -key layzer.com.key -out layzer.com.csr -config /etc/pki/tls/openssl.cnf -subj "/C=CN/ST=SH/L=ShangHai/O=BTC/OU=LAYZER/CN=*.layzer.com/emailAddress=layzer@163.com"
查看签名请求文件信息
[root@virtual_host ssl]# openssl req -in layzer.com.csr -text
使用自签署的CA,签署layzer.com.crt
[root@virtual_host ssl]# openssl ca -in layzer.com.csr -md sha256 -days 36500 -out layzer.com.crt -cert CA.crt -keyfile CA.key -config /etc/pki/tls/openssl.cnf
当然了,我们可能会遇到如下报错
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/index.txt: No such file or directory
unable to open '/etc/pki/CA/index.txt'
140216322066320:error:02001002:system library:fopen:No such file or directory:bss_file.c:402:fopen('/etc/pki/CA/index.txt','r')
140216322066320:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:404:
解决方法如下:
[root@virtual_host ssl]# touch /etc/pki/CA/index.txt
还有另外的报错:
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/serial: No such file or directory
error while loading serial number
140152413099920:error:02001002:system library:fopen:No such file or directory:bss_file.c:402:fopen('/etc/pki/CA/serial','r')
140152413099920:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:404:
解决方法如下:
[root@virtual_host ssl]# echo "01" > /etc/pki/CA/serial
[root@virtual_host ssl]# openssl ca -in layzer.com.csr -md sha256 -days 36500 -out layzer.com.crt -cert CA.crt -keyfile CA.key -config /etc/pki/tls/openssl.cnf
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Aug 20 17:39:16 2022 GMT
Not After : Jul 27 17:39:16 2122 GMT
Subject:
countryName = CN
stateOrProvinceName = SH
organizationName = BTC
organizationalUnitName = LAYZER
commonName = *.layzer.com
emailAddress = layzer@163.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
46:F3:0D:B9:6B:7F:4C:6B:C0:F6:CE:47:F8:E6:39:9E:09:F9:2F:69
X509v3 Authority Key Identifier:
keyid:9B:E9:58:13:45:7F:EF:7D:92:7D:AE:73:09:A3:9A:77:99:16:3E:30
Certificate is to be certified until Jul 27 17:39:16 2122 GMT (36500 days)
Sign the certificate? [y/n]:y # 输入y确认
1 out of 1 certificate requests certified, commit? [y/n]y # 输入y确认
Write out database with 1 new entries
Data Base Updated
检查部署是否正常
[root@virtual_host ssl]# cat /etc/pki/CA/index.txt
V 21220727173916Z 01 unknown /C=CN/ST=SH/O=BTC/OU=LAYZER/CN=*.layzer.com/emailAddress=layzer@163.com
[root@virtual_host ssl]# cat /etc/pki/CA/serial
02
这证明我们的证书颁发已经被记录了。
注:同一个域名不能签署多次;由于签署了*.layzer.com,且已经被记录,因此不能再次被签署。除非删除该记录。
注:注意index.txt文件和serial文件的关系。serial文件内容为index.txt文件内容行数加1。
查看证书信息
[root@virtual_host ssl]# openssl x509 -in layzer.com.crt -text
验证签发证书是否有效
[root@virtual_host ssl]# openssl verify -CAfile CA.crt layzer.com.crt
layzer.com.crt: OK
看看目前我们有什么
[root@virtual_host ssl]# ll
total 24
-rw-r--r-- 1 root root 1399 Aug 20 13:27 CA.crt
-rw-r--r-- 1 root root 1675 Dec 27 2021 CA.key
-rw-r--r-- 1 root root 4576 Aug 20 13:39 layzer.com.crt
-rw-r--r-- 1 root root 1041 Aug 20 13:35 layzer.com.csr
-rw-r--r-- 1 root root 1675 Aug 20 13:31 layzer.com.key
转换证书给Nginx使用
[root@virtual_host ssl]# openssl x509 -in layzer.com.crt -out layzer.com.pem -outform PEM
[root@virtual_host ssl]# ll
total 28
-rw-r--r-- 1 root root 1399 Aug 20 13:27 CA.crt
-rw-r--r-- 1 root root 1675 Dec 27 2021 CA.key
-rw-r--r-- 1 root root 4576 Aug 20 13:39 layzer.com.crt
-rw-r--r-- 1 root root 1041 Aug 20 13:35 layzer.com.csr
-rw-r--r-- 1 root root 1675 Aug 20 13:31 layzer.com.key
-rw-r--r-- 1 root root 1419 Aug 20 13:44 layzer.com.pem
6:测试泛域名证书
[root@virtual_host ssl]# mkdir /etc/nginx/ssl
[root@virtual_host ssl]# cp layzer.com.pem layzer.com.key /etc/nginx/ssl/
server {
listen 80;
server_name layzer.com;
location /{
return 301 https://layzer.com;
}
}
server {
listen 443 ssl http2;
server_name layzer.com;
root /usr/share/nginx/html;
index index.html;
ssl_certificate /etc/nginx/ssl/layzer.com.pem;
ssl_certificate_key /etc/nginx/ssl/layzer.com.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
}
启动Nginx
[root@virtual_host ssl]# nginx
访问测试
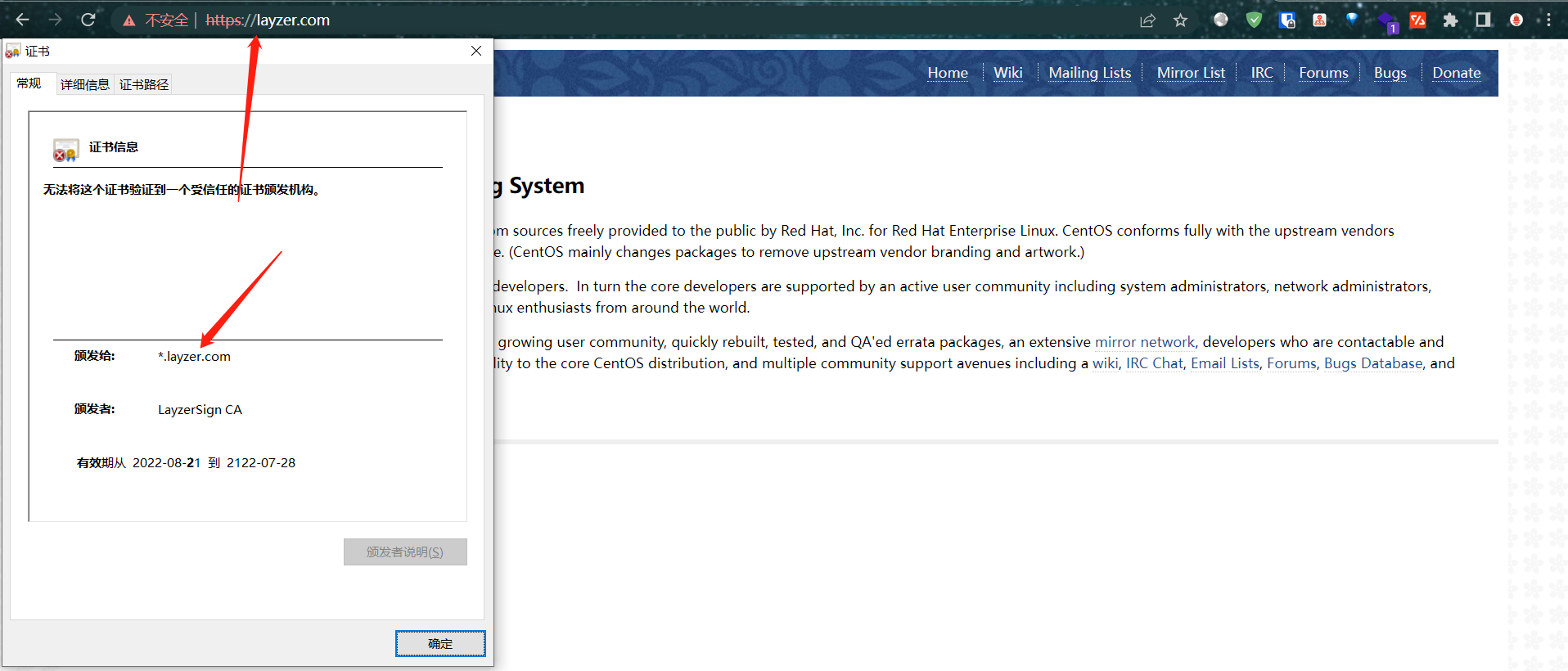
因为是自签证书,所以这里不受信任也是正常的,到这里,我们的泛域名证书就办法完成了。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号