
1:环境
Kubernetes:1.23.1
Istio:13.2
2:安装Istio+部署测试服务
[root@k8s-master ~]# wget https://github.com/istio/istio/releases/download/1.13.2/istio-1.13.2-linux-amd64.tar.gz
[root@k8s-master ~]# tar xf istio-1.13.2-linux-amd64.tar.gz
[root@k8s-master ~]# ls
anaconda-ks.cfg calico.yaml istio-1.13.2 istio-1.13.2-linux-amd64.tar.gz
[root@k8s-master ~]# cd istio-1.13.2/
[root@k8s-master istio-1.13.2]# ls
bin LICENSE manifests manifest.yaml README.md samples tools
[root@k8s-master istio-1.13.2]# cp bin/istioctl /usr/local/bin/
[root@k8s-master istio-1.13.2]# istioctl version
no running Istio pods in "istio-system"
1.13.2
[root@k8s-master istio-1.13.2]# istioctl install --set profile=demo -y
✔ Istio core installed
✔ Istiod installed
✔ Ingress gateways installed
✔ Egress gateways installed
✔ Installation complete Making this installation the default for injection and validation.
Thank you for installing Istio 1.13. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/pzWZpAvMVBecaQ9h9
[root@k8s-master istio-1.13.2]# istioctl version
client version: 1.13.2
control plane version: 1.13.2
data plane version: 1.13.2 (2 proxies)
[root@k8s-master istio-1.13.2]# kubectl get ns --show-labels
NAME STATUS AGE LABELS
default Active 77d kubernetes.io/metadata.name=default
istio-system Active 25m kubernetes.io/metadata.name=istio-system
kube-node-lease Active 77d kubernetes.io/metadata.name=kube-node-lease
kube-public Active 77d kubernetes.io/metadata.name=kube-public
kube-system Active 77d kubernetes.io/metadata.name=kube-system
[root@k8s-master istio-1.13.2]# kubectl label namespace default istio-injection=enabled
namespace/default labeled
[root@k8s-master istio-1.13.2]# kubectl get pod -n istio-system
NAME READY STATUS RESTARTS AGE
istio-egressgateway-77568fc45c-qqq2b 1/1 Running 0 21m
istio-ingressgateway-76b86f6b45-ktw8f 1/1 Running 0 21m
istiod-85bf4789f7-5l2v9 1/1 Running 0 25m
[root@k8s-master istio-1.13.2]# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-egressgateway ClusterIP 172.1.128.62 <none> 80/TCP,443/TCP 21m
istio-ingressgateway LoadBalancer 172.1.36.110 <pending> 15021:31073/TCP,80:32423/TCP,443:31439/TCP,31400:30884/TCP,15443:30692/TCP 21m
istiod ClusterIP 172.1.93.37 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 26m
[root@k8s-master istio-1.13.2]# kubectl get deployment -n istio-system
NAME READY UP-TO-DATE AVAILABLE AGE
istio-egressgateway 1/1 1 1 21m
istio-ingressgateway 1/1 1 1 21m
istiod 1/1 1 1 26m
[root@k8s-master istio-1.13.2]# kubectl get secret -n istio-system
NAME TYPE DATA AGE
default-token-8nslc kubernetes.io/service-account-token 3 26m
istio-ca-secret istio.io/ca-root 5 22m
istio-egressgateway-service-account-token-9nwpp kubernetes.io/service-account-token 3 22m
istio-ingressgateway-service-account-token-56fcs kubernetes.io/service-account-token 3 22m
istio-reader-service-account-token-5pbxk kubernetes.io/service-account-token 3 26m
istiod-service-account-token-ksrkl kubernetes.io/service-account-token 3 26m
istiod-token-hljqd kubernetes.io/service-account-token 3 26m
[root@k8s-master istio-1.13.2]# kubectl get cm -n istio-system
NAME DATA AGE
istio 2 26m
istio-ca-root-cert 1 22m
istio-gateway-deployment-leader 0 22m
istio-gateway-status-leader 0 22m
istio-leader 0 22m
istio-namespace-controller-election 0 22m
istio-sidecar-injector 2 26m
kube-root-ca.crt 1 26m
[root@k8s-master istio-1.13.2]# kubectl get cm
NAME DATA AGE
istio-ca-root-cert 1 22m
kube-root-ca.crt 1 77d
[root@k8s-master istio-1.13.2]# kubectl get sa -n istio-system
NAME SECRETS AGE
default 1 27m
istio-egressgateway-service-account 1 22m
istio-ingressgateway-service-account 1 22m
istio-reader-service-account 1 26m
istiod 1 26m
istiod-service-account 1 26m
[root@k8s-master istio-1.13.2]# kubectl get ClusterRole | grep istio-system
istio-reader-clusterrole-istio-system 2022-04-12T17:09:19Z
istio-reader-istio-system 2022-04-12T17:09:17Z
istiod-clusterrole-istio-system 2022-04-12T17:09:19Z
istiod-gateway-controller-istio-system 2022-04-12T17:09:19Z
istiod-istio-system 2022-04-12T17:09:17Z
[root@k8s-master istio-1.13.2]# kubectl get ClusterRoleBinding | grep istio-system
istio-reader-clusterrole-istio-system ClusterRole/istio-reader-clusterrole-istio-system 27m
istio-reader-istio-system ClusterRole/istio-reader-istio-system 27m
istiod-clusterrole-istio-system ClusterRole/istiod-clusterrole-istio-system 27m
istiod-gateway-controller-istio-system ClusterRole/istiod-gateway-controller-istio-system 27m
istiod-istio-system ClusterRole/istiod-istio-system 27m
[root@k8s-master istio-1.13.2]# kubectl get Role -n istio-system
NAME CREATED AT
istio-egressgateway-sds 2022-04-12T17:13:33Z
istio-ingressgateway-sds 2022-04-12T17:13:33Z
istiod 2022-04-12T17:09:20Z
istiod-istio-system 2022-04-12T17:09:18Z
[root@k8s-master istio-1.13.2]# kubectl get RoleBinding -n istio-system
NAME ROLE AGE
istio-egressgateway-sds Role/istio-egressgateway-sds 23m
istio-ingressgateway-sds Role/istio-ingressgateway-sds 23m
istiod Role/istiod 27m
istiod-istio-system Role/istiod-istio-system 27m
[root@k8s-master istio-1.13.2]# kubectl apply -f samples/addons
serviceaccount/grafana created
configmap/grafana created
service/grafana created
deployment.apps/grafana created
configmap/istio-grafana-dashboards created
configmap/istio-services-grafana-dashboards created
deployment.apps/jaeger created
service/tracing created
service/zipkin created
service/jaeger-collector created
serviceaccount/kiali created
configmap/kiali created
clusterrole.rbac.authorization.k8s.io/kiali-viewer created
clusterrole.rbac.authorization.k8s.io/kiali created
clusterrolebinding.rbac.authorization.k8s.io/kiali created
role.rbac.authorization.k8s.io/kiali-controlplane created
rolebinding.rbac.authorization.k8s.io/kiali-controlplane created
service/kiali created
deployment.apps/kiali created
serviceaccount/prometheus created
configmap/prometheus created
clusterrole.rbac.authorization.k8s.io/prometheus created
clusterrolebinding.rbac.authorization.k8s.io/prometheus created
service/prometheus created
deployment.apps/prometheus created
[root@k8s-master istio-1.13.2]# kubectl get pod -n istio-system
NAME READY STATUS RESTARTS AGE
grafana-67f5ccd9d7-26xr4 1/1 Running 0 12m
istio-egressgateway-77568fc45c-qqq2b 1/1 Running 0 36m
istio-ingressgateway-76b86f6b45-ktw8f 1/1 Running 0 36m
istiod-85bf4789f7-5l2v9 1/1 Running 0 41m
jaeger-78cb4f7d4b-772ps 1/1 Running 0 12m
kiali-c946fb5bc-9lddh 1/1 Running 0 12m
prometheus-7cc96d969f-rlhrl 2/2 Running 0 12m
[root@k8s-master istio-1.13.2]# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 172.1.56.76 <none> 3000/TCP 12m
istio-egressgateway ClusterIP 172.1.128.62 <none> 80/TCP,443/TCP 37m
istio-ingressgateway LoadBalancer 172.1.36.110 <pending> 15021:31073/TCP,80:32423/TCP,443:31439/TCP,31400:30884/TCP,15443:30692/TCP 37m
istiod ClusterIP 172.1.93.37 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 41m
jaeger-collector ClusterIP 172.1.147.212 <none> 14268/TCP,14250/TCP,9411/TCP 12m
kiali ClusterIP 172.1.169.146 <none> 20001/TCP,9090/TCP 12m
prometheus ClusterIP 172.1.169.232 <none> 9090/TCP 12m
tracing ClusterIP 172.1.230.167 <none> 80/TCP,16685/TCP 12m
zipkin ClusterIP 172.1.136.111 <none> 9411/TCP 12m
# 这里如果您没LB 可以直接改SVC的模式为NodePort
[root@k8s-master istio-1.13.2]# kubectl get deployment -n istio-system
NAME READY UP-TO-DATE AVAILABLE AGE
grafana 1/1 1 1 15m
istio-egressgateway 1/1 1 1 40m
istio-ingressgateway 1/1 1 1 40m
istiod 1/1 1 1 44m
jaeger 1/1 1 1 15m
kiali 1/1 1 1 15m
prometheus 1/1 1 1 15m
[root@k8s-master istio-1.13.2]# kubectl get secret,cm,sa -n istio-system |grep kiali
secret/kiali-token-zxs8q kubernetes.io/service-account-token 3 25m
configmap/kiali 1 25m
serviceaccount/kiali 1 25m
[root@k8s-master istio-1.13.2]# kubectl get secret,cm,sa -n istio-system |grep prometheus
secret/prometheus-token-b7shc kubernetes.io/service-account-token 3 26m
configmap/prometheus 5 26m
serviceaccount/prometheus 1 26m
[root@k8s-master istio-1.13.2]# kubectl get secret,cm,sa -n istio-system |grep grafana
secret/grafana-token-k54t6 kubernetes.io/service-account-token 3 26m
configmap/grafana 3 26m
configmap/istio-grafana-dashboards 2 26m
configmap/istio-services-grafana-dashboards 4 26m
serviceaccount/grafana 1 26m
[root@k8s-master istio-1.13.2]# kubectl get ClusterRole,ClusterRoleBinding | grep kiali
clusterrole.rbac.authorization.k8s.io/kiali 2022-04-12T17:37:55Z
clusterrole.rbac.authorization.k8s.io/kiali-viewer 2022-04-12T17:37:55Z
clusterrolebinding.rbac.authorization.k8s.io/kiali ClusterRole/kiali 26m
[root@k8s-master istio-1.13.2]# kubectl get ClusterRole,ClusterRoleBinding | grep prometheus
clusterrole.rbac.authorization.k8s.io/prometheus 2022-04-12T17:37:56Z
clusterrolebinding.rbac.authorization.k8s.io/prometheus ClusterRole/prometheus 27m
# 修改暴露端口
[root@k8s-master istio-1.13.2]# kubectl edit svc istio-ingressgateway -n istio-system
[root@k8s-master istio-1.13.2]# kubectl edit svc kiali -n istio-system
service/kiali edited
[root@k8s-master istio-1.13.2]# kubectl edit svc tracing -n istio-system
service/tracing edited
[root@k8s-master istio-1.13.2]# kubectl edit svc prometheus -n istio-system
service/prometheus edited
[root@k8s-master istio-1.13.2]# kubectl edit svc grafana -n istio-system
service/grafana edited
[root@k8s-master istio-1.13.2]# kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml
gateway.networking.istio.io/bookinfo-gateway unchanged
virtualservice.networking.istio.io/bookinfo unchanged
[root@k8s-master istio-1.13.2]# kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml
service/details created
serviceaccount/bookinfo-details created
deployment.apps/details-v1 created
service/ratings created
serviceaccount/bookinfo-ratings created
deployment.apps/ratings-v1 created
service/reviews created
serviceaccount/bookinfo-reviews created
deployment.apps/reviews-v1 created
deployment.apps/reviews-v2 created
deployment.apps/reviews-v3 created
service/productpage created
serviceaccount/bookinfo-productpage created
deployment.apps/productpage-v1 created
[root@k8s-master istio-1.13.2]# kubectl get pods -n default
NAME READY STATUS RESTARTS AGE
details-v1-5498c86cf5-2kfh5 2/2 Running 0 3m3s
productpage-v1-65b75f6885-7b52z 2/2 Running 0 3m3s
ratings-v1-b477cf6cf-qs99s 2/2 Running 0 3m3s
reviews-v1-79d546878f-fqggn 2/2 Running 0 3m3s
reviews-v2-548c57f459-7d8rr 2/2 Running 0 3m3s
reviews-v3-6dd79655b9-7d8kc 2/2 Running 0 3m3s
[root@k8s-master istio-1.13.2]# kubectl get svc -n default
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
details ClusterIP 172.1.253.57 <none> 9080/TCP 3m16s
kubernetes ClusterIP 172.1.0.1 <none> 443/TCP 77d
productpage ClusterIP 172.1.105.122 <none> 9080/TCP 3m15s
ratings ClusterIP 172.1.79.81 <none> 9080/TCP 3m16s
reviews ClusterIP 172.1.135.204 <none> 9080/TCP 3m16s
[root@k8s-master istio-1.13.2]# kubectl get gateway -n default
NAME AGE
bookinfo-gateway 15m
[root@k8s-master istio-1.13.2]# kubectl get virtualservice -n default
NAME GATEWAYS HOSTS AGE
bookinfo ["bookinfo-gateway"] ["*"] 15m
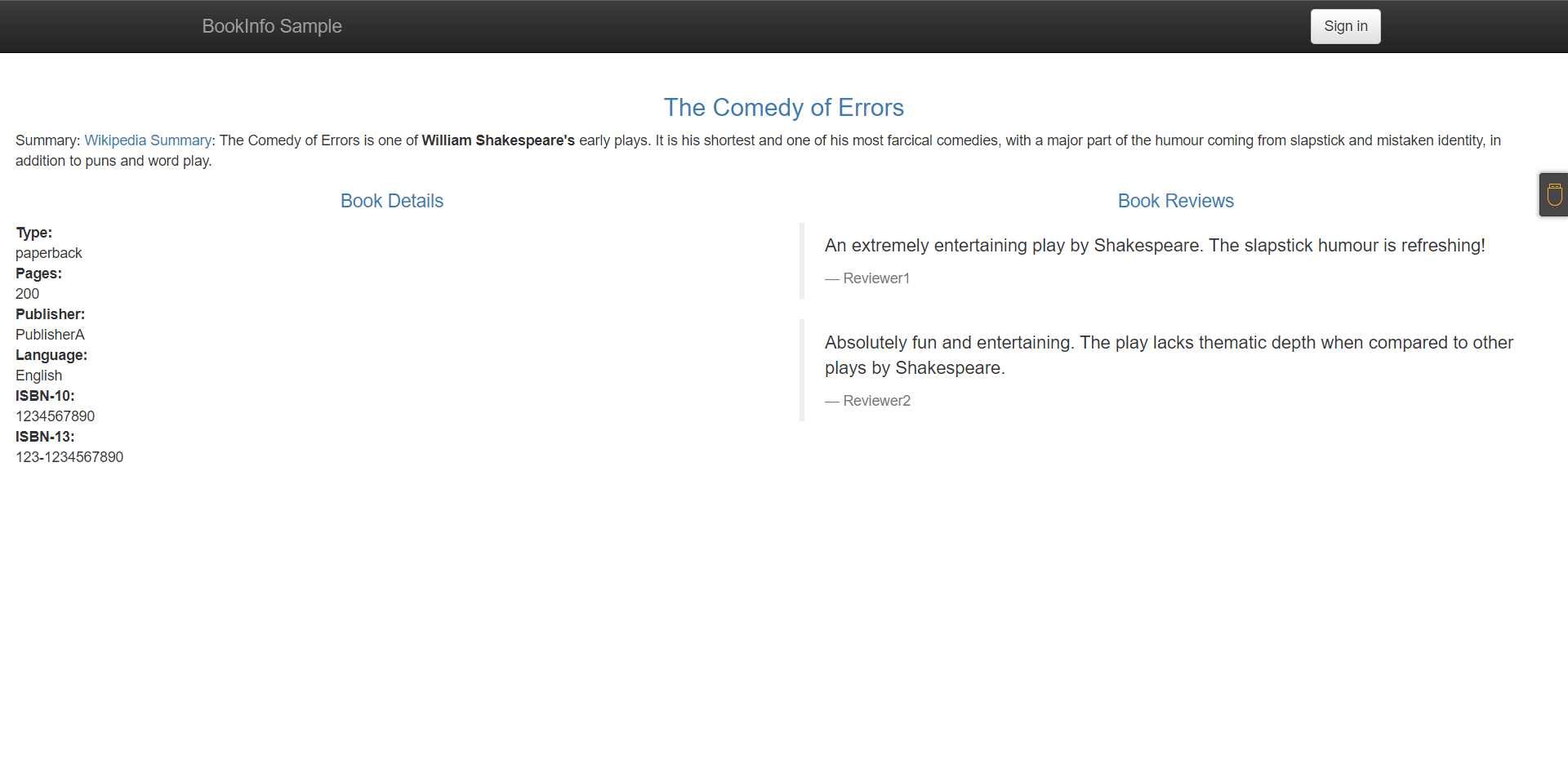
3:测试访问
http://10.0.0.10:32423/productpage
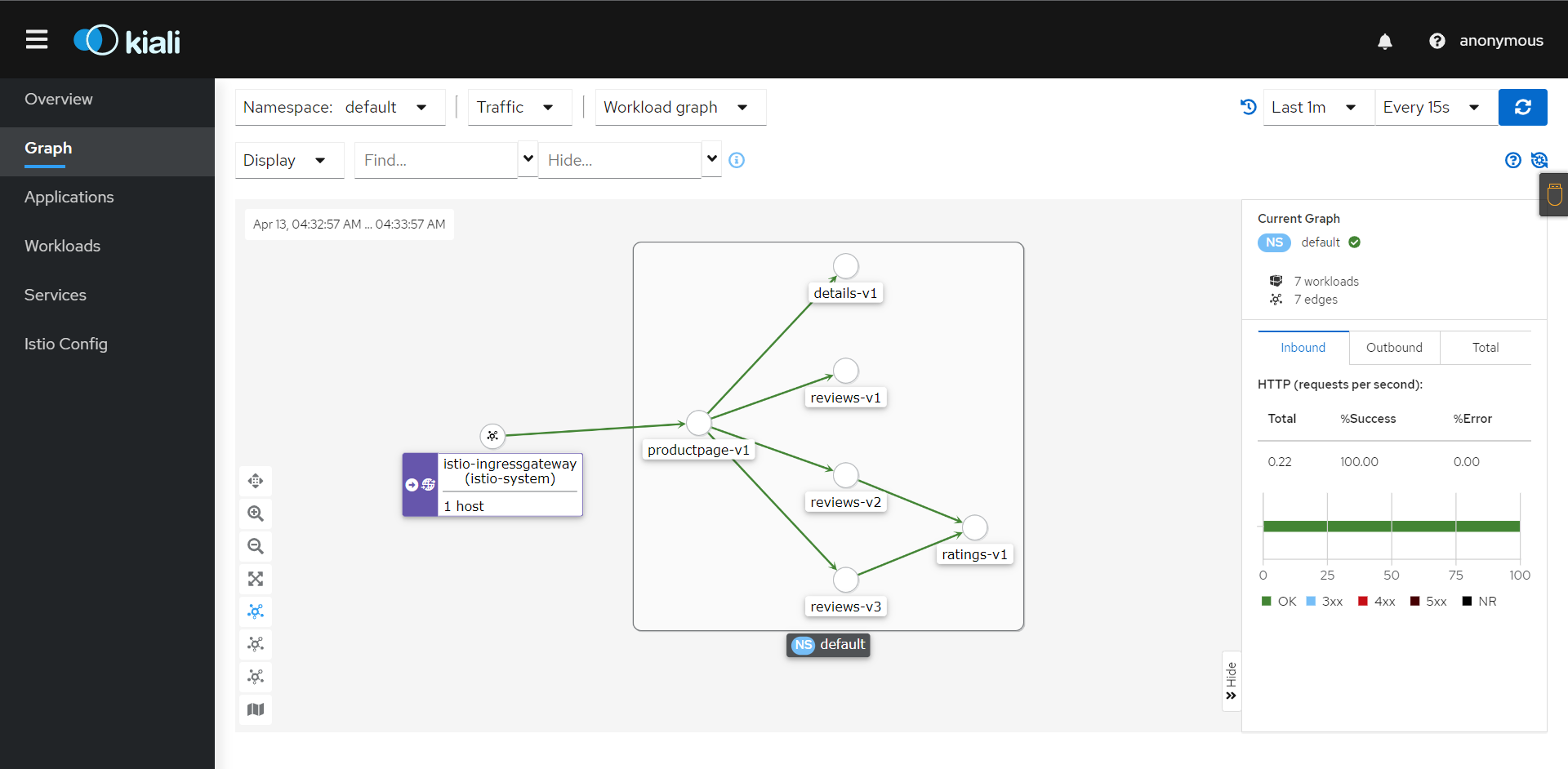
4:查看Grafana数据
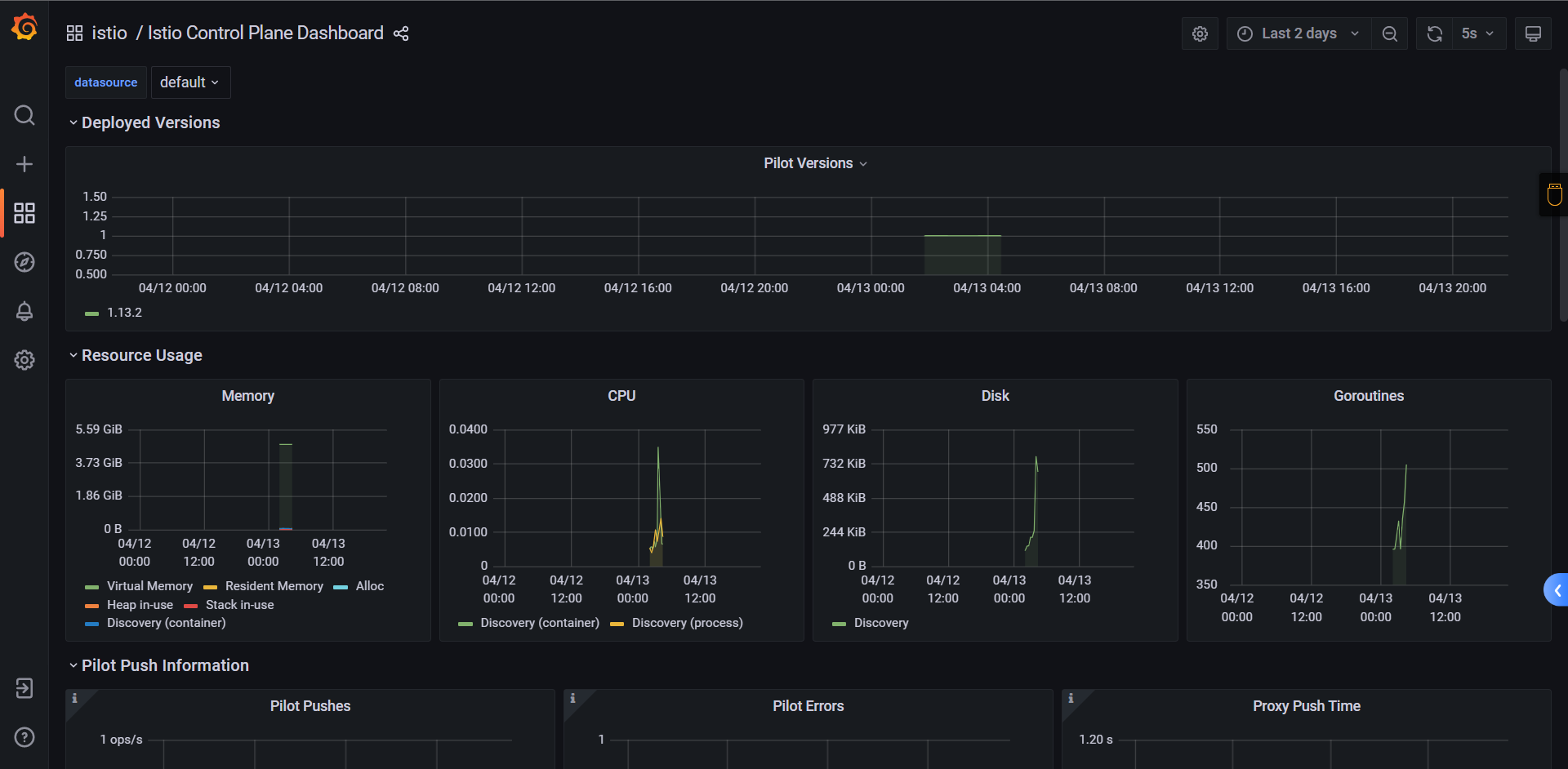
5:Istio卸载
# 删除服务
[root@k8s-master istio-1.13.2]# kubectl delete -f istio-1.13.2/samples/bookinfo/platform/kube/bookinfo.yaml
[root@k8s-master istio-1.13.2]# kubectl delete -f istio-1.13.2/samples/bookinfo/networking/bookinfo-gateway.yaml
# 删除Istio
[root@k8s-master istio-1.13.2]# kubectl delete -f samples/addons
[root@k8s-master istio-1.13.2]# istioctl manifest generate --set profile=demo | kubectl delete --ignore-not-found=true -f -
[root@k8s-master istio-1.13.2]# kubectl delete namespace istio-system
[root@k8s-master istio-1.13.2]# kubectl label namespace default istio-injection-






 浙公网安备 33010602011771号
浙公网安备 33010602011771号