Ingress-nginx开启Auth认证+SSL证书配置
1:环境
| 集群 | 版本 | 插件版本 |
|---|---|---|
| Kubernetes | 1.23.3 | 1.1.3 |
2:未配置
[root@k8s-master ingress]# cat demo.yaml
apiVersion: v1
kind: Namespace
metadata:
name: nginx
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
namespace: nginx
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:alpine
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: nginx
namespace: nginx
spec:
type: ClusterIP
selector:
app: nginx
ports:
- name: http
port: 80
targetPort: 80
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx
namespace: nginx
spec:
ingressClassName: nginx
rules:
- host: demo.kubernetes-devops.cn
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx
port:
number: 80
# 这里模拟一个隐私主页,首先不打开认证,我们来看一下
[root@k8s-master ingress]# kubectl get pod,svc,ingress
NAME READY STATUS RESTARTS AGE
pod/nginx-9fbb7d78-zgpxk 2/2 Running 0 27m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 172.1.0.1 <none> 443/TCP 83d
service/nginx ClusterIP 172.1.238.14 <none> 80/TCP 27m
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress.networking.k8s.io/nginx nginx demo.kubernetes-devops.cn 10.0.0.12 80 27m
# 查看一下
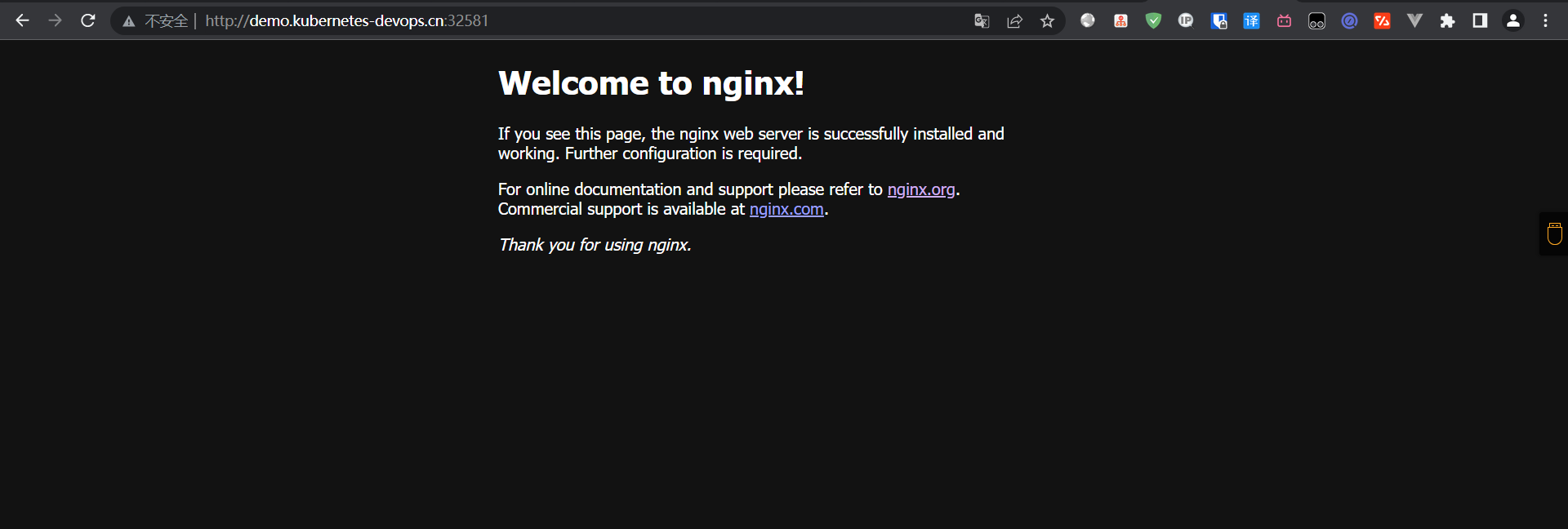
3:配置Auth
这里可以看到,直接可以访问到,接下里我们打开Auth认证模块
# 在此之前我们需要先生成一个配置文件来创建一个secrets
[root@k8s-master ingress]# yum install -y httpd # 这里需要使用htpasswd
[root@k8s-master ingress]# mkdir auth
[root@k8s-master ingress]# cd auth/
[root@k8s-master auth]# htpasswd -c auth admin # htpasswd -c <filename> <useradmin>
New password: # 输入密码
Re-type new password: # 再次输入密码
Adding password for user admin
[root@k8s-master auth]# ls
auth # 此处生成文件
# 创建 secret
[root@k8s-master auth]# kubectl create secret generic auth --from-file=basic-auth
# kubectl create secret generic <secretname> --from-file=<htpasswd_name>
secret/basic-auth created
# 配置Ingress认证
[root@k8s-master ingress]# kubectl get secrets
NAME TYPE DATA AGE
auth Opaque 1 70s
[root@k8s-master ingress]# cat demo.yaml
...
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx
annotations:
nginx.ingress.kubernetes.io/auth-type: basic # 开启basic认证
nginx.ingress.kubernetes.io/auth-secret: auth # 写入secretname
nginx.ingress.kubecnetes.io/auth-realm: 'Authentication Required - foo'
spec:
ingressClassName: nginx
rules:
- host: demo.kubernetes-devops.cn
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx
port:
number: 80
# 部署
[root@k8s-master ingress]# kubectl apply -f demo.yaml
deployment.apps/nginx unchanged
service/nginx unchanged
ingress.networking.k8s.io/nginx configured
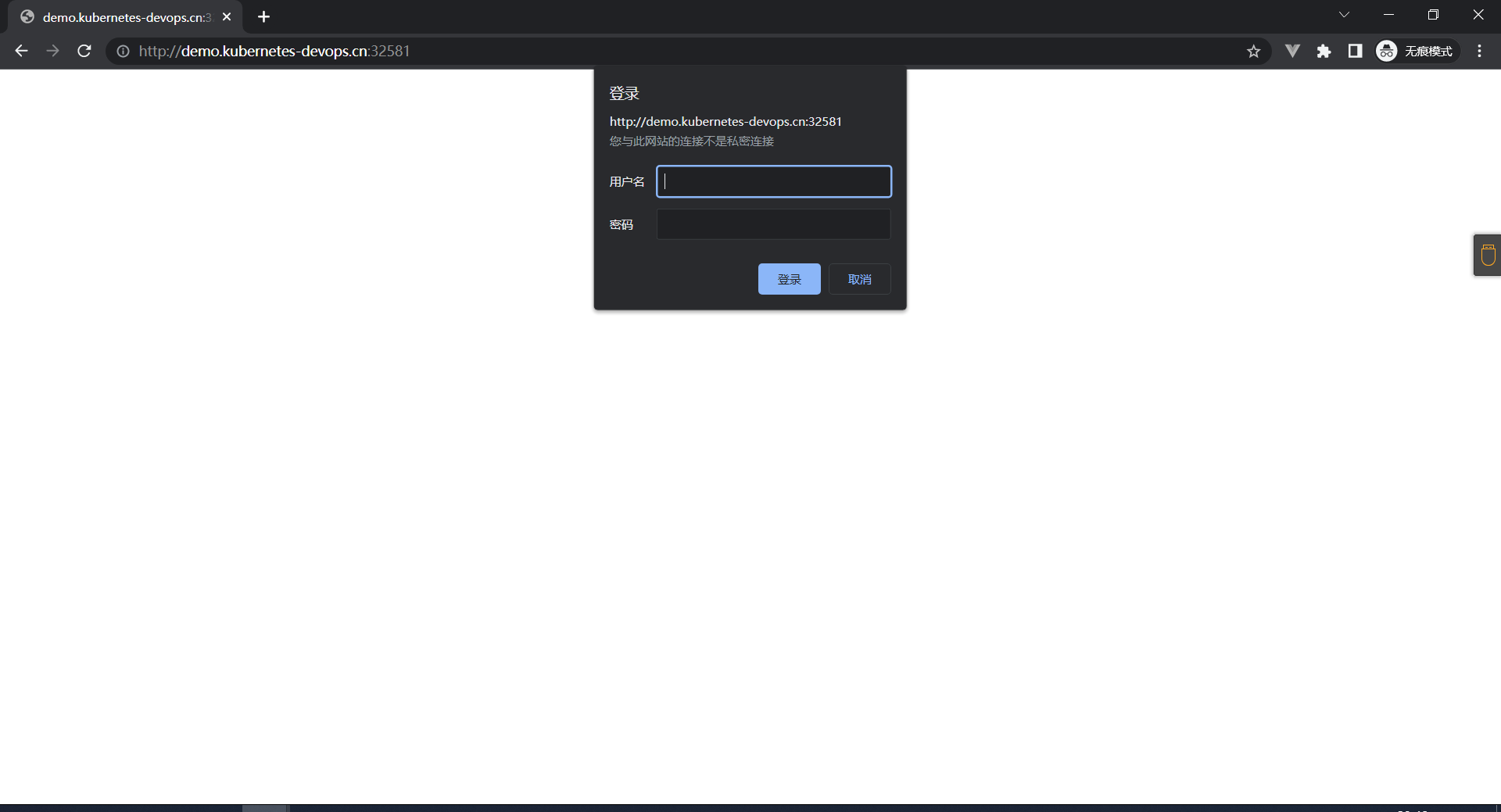
# 测试如下
账号:htpasswd时配置的账号
密码:自己htpasswd的时候配置的密码
# 第一种
[root@k8s-master ingress]# curl -X GET http://admin:123@demo.kubernetes-devops.cn:32581 -I
HTTP/1.1 200 OK
Date: Tue, 19 Apr 2022 15:53:37 GMT
Content-Type: text/html
Content-Length: 615
Connection: keep-alive
last-modified: Tue, 28 Dec 2021 18:48:00 GMT
etag: "61cb5be0-267"
accept-ranges: bytes
x-envoy-upstream-service-time: 0
x-envoy-decorator-operation: nginx.default.svc.cluster.local:80/*
# 第二种
[root@k8s-master ingress]# curl -u admin:123 -X GET http://admin:123@demo.kubernetes-devops.cn:32581 -I
HTTP/1.1 200 OK
Date: Tue, 19 Apr 2022 15:54:45 GMT
Content-Type: text/html
Content-Length: 615
Connection: keep-alive
last-modified: Tue, 28 Dec 2021 18:48:00 GMT
etag: "61cb5be0-267"
accept-ranges: bytes
x-envoy-upstream-service-time: 1
x-envoy-decorator-operation: nginx.default.svc.cluster.local:80/*
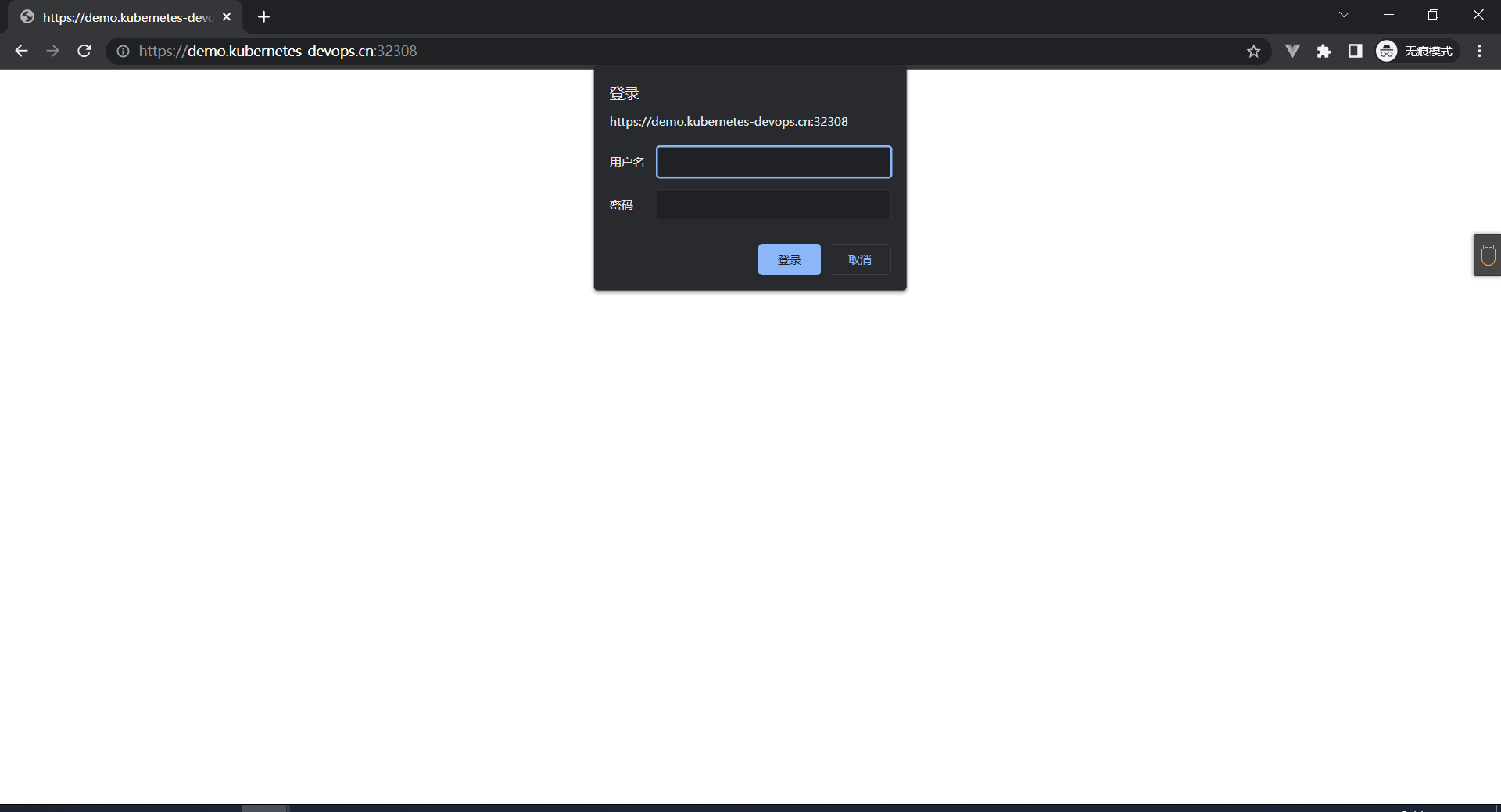
4:配置SSL访问
首先我们需要有证书的pem和key
[root@k8s-master ssl]# ls
server.key server.pem
创建TLS secret
[root@k8s-master ssl]# kubectl get secrets
NAME TYPE DATA AGE
---
nginx-ssl kubernetes.io/tls 2 6s
让后在Nginx引用
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: auth
nginx.ingress.kubecnetes.io/auth-realm: 'Authentication Required - foo'
spec:
ingressClassName: nginx
tls:
- hosts:
- demo.kubernetes-devops.cn
secretName: nginx-ssl
rules:
- host: demo.kubernetes-devops.cn
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx
port:
number: 80
部署测试
[root@k8s-master ingress]# kubectl apply -f demo.yaml
deployment.apps/nginx unchanged
service/nginx unchanged
ingress.networking.k8s.io/nginx configured
[root@k8s-master ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 172.1.106.113 <none> 80:32581/TCP,443:32308/TCP 5d
ingress-nginx-controller-admission ClusterIP 172.1.3.220 <none> 443/TCP 5d
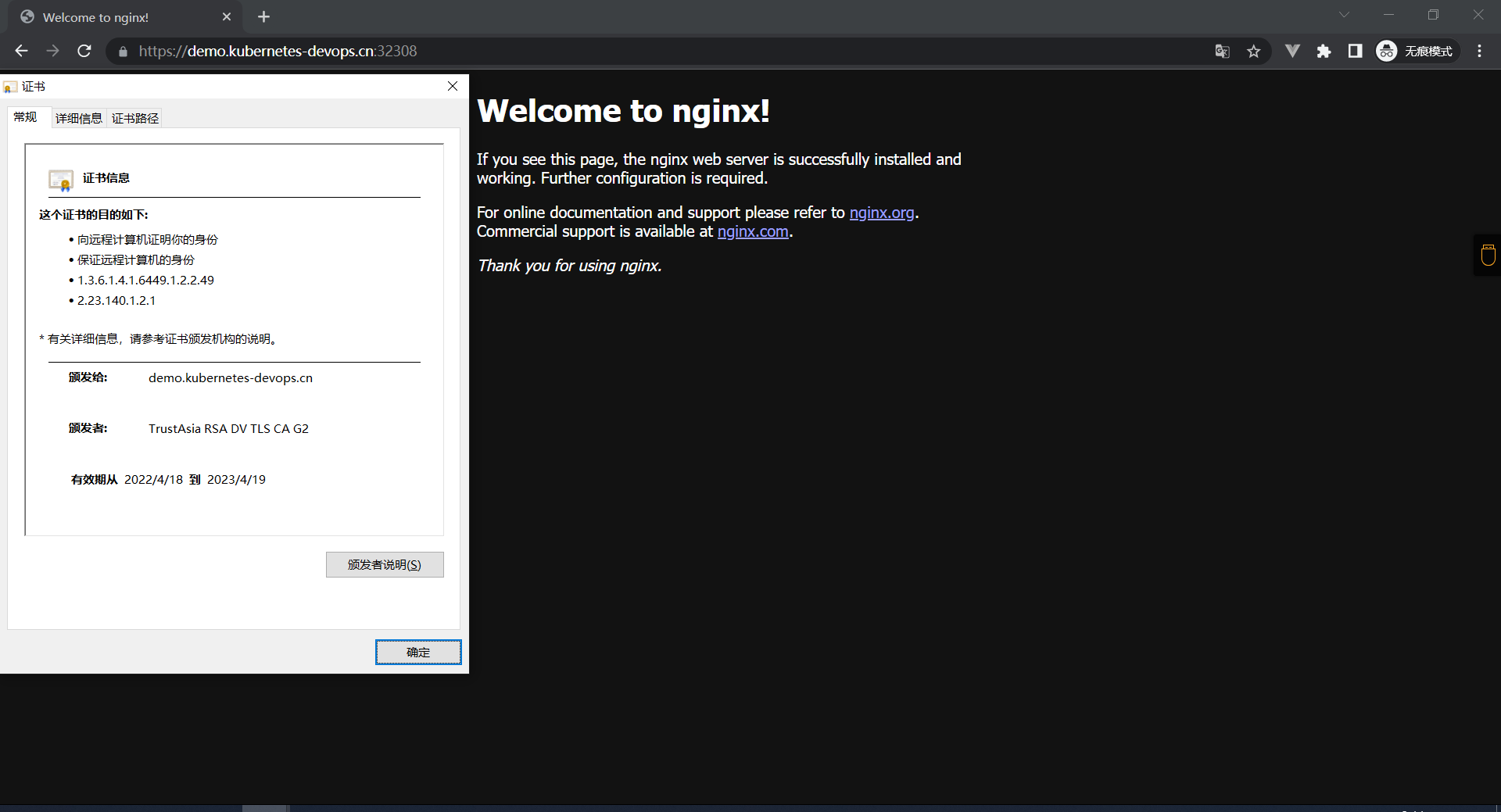
因为这里开启了SSL 所以我们要访问Ingress映射的443端口了
[root@k8s-master ingress]# curl -X GET https://admin:123@demo.kubernetes-devops.cn:32308 -I
HTTP/1.1 200 OK
Date: Tue, 19 Apr 2022 16:10:18 GMT
Content-Type: text/html
Content-Length: 615
Connection: keep-alive
last-modified: Tue, 28 Dec 2021 18:48:00 GMT
etag: "61cb5be0-267"
accept-ranges: bytes
x-envoy-upstream-service-time: 0
x-envoy-decorator-operation: nginx.default.svc.cluster.local:80/*
Strict-Transport-Security: max-age=15724800; includeSubDomains
[root@k8s-master ingress]# curl -u admin:123 -X GET https://demo.kubernetes-devops.cn:32308 -I
HTTP/1.1 200 OK
Date: Tue, 19 Apr 2022 16:10:43 GMT
Content-Type: text/html
Content-Length: 615
Connection: keep-alive
last-modified: Tue, 28 Dec 2021 18:48:00 GMT
etag: "61cb5be0-267"
accept-ranges: bytes
x-envoy-upstream-service-time: 1
x-envoy-decorator-operation: nginx.default.svc.cluster.local:80/*
Strict-Transport-Security: max-age=15724800; includeSubDomains


 浙公网安备 33010602011771号
浙公网安备 33010602011771号