NGFW-虚拟系统与站点建立IPSec
一,环境简介
1.1拓扑图
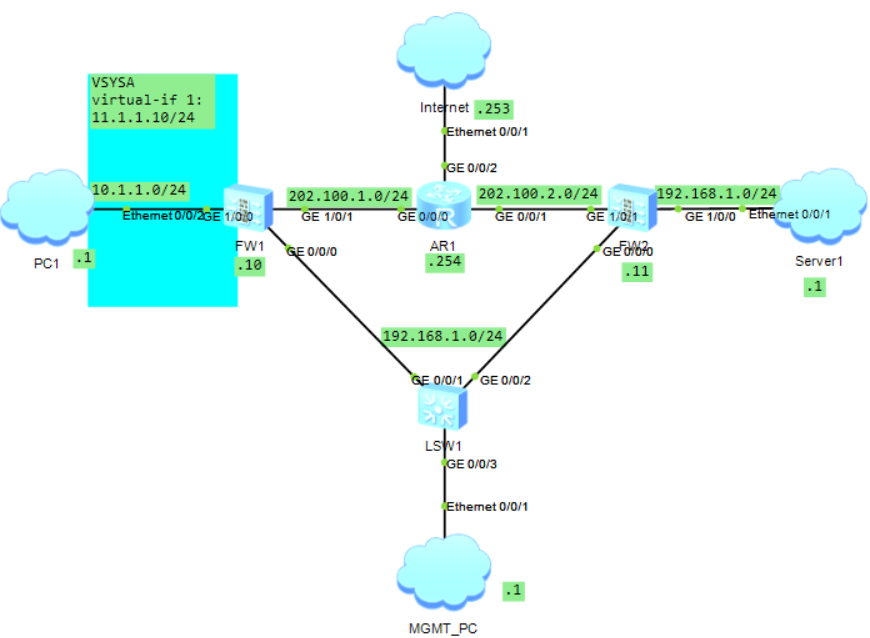
1.2桥接虚拟网卡
1.MGMT_PC
2.PC1
3.Server1
4.Internet
1.3实验需求
在FW1上配置虚拟系统,并为虚拟系统分配物理接口。物理接口连接虚拟系统的内网PC。在虚拟系统中配置与FW建立IPSec VPN。实验分为两种场景,一种是对端IP固定的且可以在公网种寻址的,第二种是虚拟系统一方是不固定并且在与FW2的链路中是穿越NAT的(做的时候建立失败,后续更新)。
二,固定地址的实验配置
2.1基础配置
2.1.1AR1
[AR1]interface GigabitEthernet 0/0/0 [AR1-GigabitEthernet0/0/0]ip address 202.100.1.254 24 [AR1-GigabitEthernet0/0/0]interface GigabitEthernet 0/0/1 [AR1-GigabitEthernet0/0/1]ip address 202.100.2.254 24 [AR1-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/2 [AR1-GigabitEthernet0/0/2]ip address 202.100.10.254 24 [AR1]ip route-static 0.0.0.0 0 202.100.10.253
[AR1]ip route-static 202.100.3.13 32 202.100.1.10
2.1.2 FW1(根系统)
1.创建虚拟系统并分配资源(本人没有实战和项目经验,对于分配资源的数值没有感觉)
[FW1]vsys enable [FW1]resource-class vsysa [FW1-resource-class-vsysa]resource-item-limit session reserved-number 500 maximum 600 [FW1-resource-class-vsysa]resource-item-limit policy reserved-number 100 [FW1-resource-class-vsysa]resource-item-limit bandwidth 1 inbound [FW1-resource-class-vsysa]resource-item-limit bandwidth 1 outbound [FW1-resource-class-vsysa]vsys name VSYSA 1 [FW1-vsys-VSYSA]assign interface GigabitEthernet 1/0/0 [FW1-vsys-VSYSA]assign resource-class vsysa
2.配置IP地址及安全区域
[FW1]interface GigabitEthernet 1/0/1 [FW1-GigabitEthernet1/0/1]ip address 202.100.1.10 24 [FW1-GigabitEthernet1/0/1]service-manage ping permit [FW1]firewall zone trust [FW1-zone-trust]add interface virtual-if 0 [FW1-zone-trust]firewall zone untrust [FW1-zone-untrust]add interface GigabitEthernet 1/0/1 [FW1-zone-untrust]ip route-static 0.0.0.0 0 202.100.1.254 [FW1]ip route-static 202.100.3.13 32 vpn-instance VSYSA
3.配置安全策略需要调用的对象
[FW1]ip service-set ISAKMP type object [FW1-object-service-set-ISAKMP]service protocol udp source-port 500 destination-port 500 [FW1-object-service-set-ISAKMP]ip address-set ipsec type object [FW1-object-address-set-ipsec]address 202.100.2.11 mask 32 [FW1-object-address-set-ipsec]address 202.100.3.13 mask 32
4.配置安全策略放行虚拟系统的流量
[FW1]security-policy [FW1-policy-security]rule name ipsec [FW1-policy-security-rule-ipsec]rule name ipsec [FW1-policy-security-rule-ipsec]source-zone trust untrust [FW1-policy-security-rule-ipsec]destination-zone untrust trust [FW1-policy-security-rule-ipsec]source-address address-set ipsec [FW1-policy-security-rule-ipsec]destination-address address-set ipsec
[FW1-policy-security-rule-ipsec]service ISAKMP esp [FW1-policy-security-rule-ipsec]action permit
2.1.2 FW2
1.IP,安全区域及静态路由
[FW2]interface GigabitEthernet 1/0/0 [FW2-GigabitEthernet1/0/0]ip address 192.168.1.11 24 [FW2-GigabitEthernet1/0/0]service-manage ping permit [FW2-GigabitEthernet1/0/0]interface GigabitEthernet 1/0/1 [FW2-GigabitEthernet1/0/1]ip address 202.100.2.11 24 [FW2-GigabitEthernet1/0/1]service-manage ping permit [FW2]firewall zone trust [FW2-zone-trust]add interface GigabitEthernet 1/0/0 [FW2-zone-trust]firewall zone untrust [FW2-zone-untrust]add interface GigabitEthernet 1/0/1 [FW2]ip route-static 0.0.0.0 0 202.100.2.254
2.安全策略需要调用的对象
[FW2]ip service-set ISAKMP type object [FW2-object-service-set-ISAKMP]service 0 protocol udp source-port 500 destination-port 500 [FW2-object-service-set-ISAKMP]ip address-set ipsec type object [FW2-object-address-set-ipsec]address 202.100.3.13 mask 32 [FW2-object-address-set-ipsec]address 202.100.2.11 mask 32 [FW2-object-address-set-ipsec]ip address-set vpn_pc type object [FW2-object-address-set-vpn_pc]address 10.1.1.0 mask 24 [FW2-object-address-set-vpn_pc]address 192.168.1.0 mask 24
3.安全策略
[FW2]security-policy [FW2-policy-security]rule name ipsec [FW2-policy-security-rule-ipsec]source-zone local untrust [FW2-policy-security-rule-ipsec]destination-zone local untrust [FW2-policy-security-rule-ipsec]source-address address-set ipsec [FW2-policy-security-rule-ipsec]destination-address address-set ipsec [FW2-policy-security-rule-ipsec]service ISAKMP esp [FW2-policy-security-rule-ipsec]action permit [FW2-policy-security]rule name vpn_pc [FW2-policy-security-rule-vpn_pc]source-zone trust untrust [FW2-policy-security-rule-vpn_pc]destination-zone untrust trust [FW2-policy-security-rule-vpn_pc]source-address address-set vpn_pc [FW2-policy-security-rule-vpn_pc]destination-address address-set vpn_pc [FW2-policy-security-rule-vpn_pc]action permit
2.2虚拟系统配置
2.2.1配置IP,安全区域和静态路由
[FW1-VSYSA]interface GigabitEthernet 1/0/0 [FW1-VSYSA-GigabitEthernet1/0/0]ip address 10.1.1.10 24 [FW1-VSYSA-GigabitEthernet1/0/0]service-manage ping permit [FW1-VSYSA]interface Virtual-if 1 [FW1-VSYSA-Virtual-if1]ip address 202.100.3.13 24 [FW1-VSYSA]firewall zone trust [FW1-VSYSA-zone-trust]add interface GigabitEthernet 1/0/0 [FW1-VSYSA-zone-trust]firewall zone untrust [FW1-VSYSA-zone-untrust]add interface Virtual-if 1 [FW1-VSYSA-zone-untrust]ip route-static 0.0.0.0 0 public
2.2.2配置安全策略需要调用的对象
[FW1-VSYSA]ip service-set ISAKMP type object [FW1-VSYSA-object-service-set-ISAKMP]service protocol udp source-port 500 destination-port 500 [FW1-VSYSA-object-service-set-ISAKMP]ip address-set ipsec type object [FW1-VSYSA-object-address-set-ipsec]address 202.100.3.13 mask 32 [FW1-VSYSA-object-address-set-ipsec]address 202.100.2.11 mask 32 [FW1-VSYSA-object-address-set-ipsec]ip address-set vpn_pc type object [FW1-VSYSA-object-address-set-vpn_pc]address 10.1.1.0 mask 24 [FW1-VSYSA-object-address-set-vpn_pc]address 192.168.1.0 mask 24
2.2.3配置安全策略放行IPSec协商及加密流量内的通信
[FW1-VSYSA]security-policy [FW1-VSYSA-policy-security]rule name ipsec [FW1-VSYSA-policy-security-rule-ipsec]source-zone local untrust [FW1-VSYSA-policy-security-rule-ipsec]destination-zone local untrust [FW1-VSYSA-policy-security-rule-ipsec]source-address address-set ipsec [FW1-VSYSA-policy-security-rule-ipsec]destination-address address-set ipsec [FW1-VSYSA-policy-security-rule-ipsec]service ISAKMP esp [FW1-VSYSA-policy-security-rule-ipsec]action permit [FW1-VSYSA-policy-security]rule name vpn_pc [FW1-VSYSA-policy-security-rule-vpn_pc]source-zone trust untrust [FW1-VSYSA-policy-security-rule-vpn_pc]destination-zone trust untrust [FW1-VSYSA-policy-security-rule-vpn_pc]source-address address-set vpn_pc [FW1-VSYSA-policy-security-rule-vpn_pc]destination-address address-set vpn_pc [FW1-VSYSA-policy-security-rule-vpn_pc]action permit
2.3IPSec配置
2.3.1VSYSA
[FW1-VSYSA]ike proposal 1 [FW1-VSYSA-ike-proposal-1]dis this 2022-10-26 02:54:00.070 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # return [FW1-VSYSA]ike peer fw2 [FW1-VSYSA-ike-peer-fw2]pre-shared-key Huawei@123 [FW1-VSYSA-ike-peer-fw2]ike-proposal 1 [FW1-VSYSA-ike-peer-fw2]undo version 2 [FW1-VSYSA-ike-peer-fw2]remote-address 202.100.2.11 [FW1-VSYSA-ike-peer-fw2]acl number 3000 [FW1-VSYSA-acl-adv-3000]rule permit ip source 10.1.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 [FW1-VSYSA-ipsec-proposal-1]dis this 2022-10-26 02:55:35.200 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # return [FW1-VSYSA-ipsec-proposal-1]ipsec policy ipsec1 1 isakmp [FW1-VSYSA-ipsec-policy-isakmp-ipsec1-1]security acl 3000 [FW1-VSYSA-ipsec-policy-isakmp-ipsec1-1]ike-peer fw2 [FW1-VSYSA-ipsec-policy-isakmp-ipsec1-1]proposal 1 [FW1-VSYSA-Virtual-if1]ipsec policy ipsec1
2.3.1FW2
[FW2]ike proposal 1 [FW2-ike-proposal-1]dis this 2022-10-26 03:01:03.210 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # return [FW2-ike-proposal-1]ike peer fw1 [FW2-ike-peer-fw1]remote-address 202.100.3.13 [FW2-ike-peer-fw1]undo version 2 [FW2-ike-peer-fw1]pre-shared-key Huawei@123 [FW2-ike-peer-fw1]ike-proposal 1 [FW2-ike-peer-fw1]acl number 3000 [FW2-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 [FW2]ipsec proposal 1 [FW2-ipsec-proposal-1]dis this 2022-10-26 03:03:10.360 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # return [FW2-ipsec-proposal-1]ipsec policy ipsec1 1 isakmp [FW2-ipsec-policy-isakmp-ipsec1-1]security acl 3000 [FW2-ipsec-policy-isakmp-ipsec1-1]ike-peer fw1 [FW2-ipsec-policy-isakmp-ipsec1-1]ike-peer fw1 [FW2]interface GigabitEthernet 1/0/1 [FW2-GigabitEthernet1/0/1]ipsec policy ipsec1
2.4测试现象
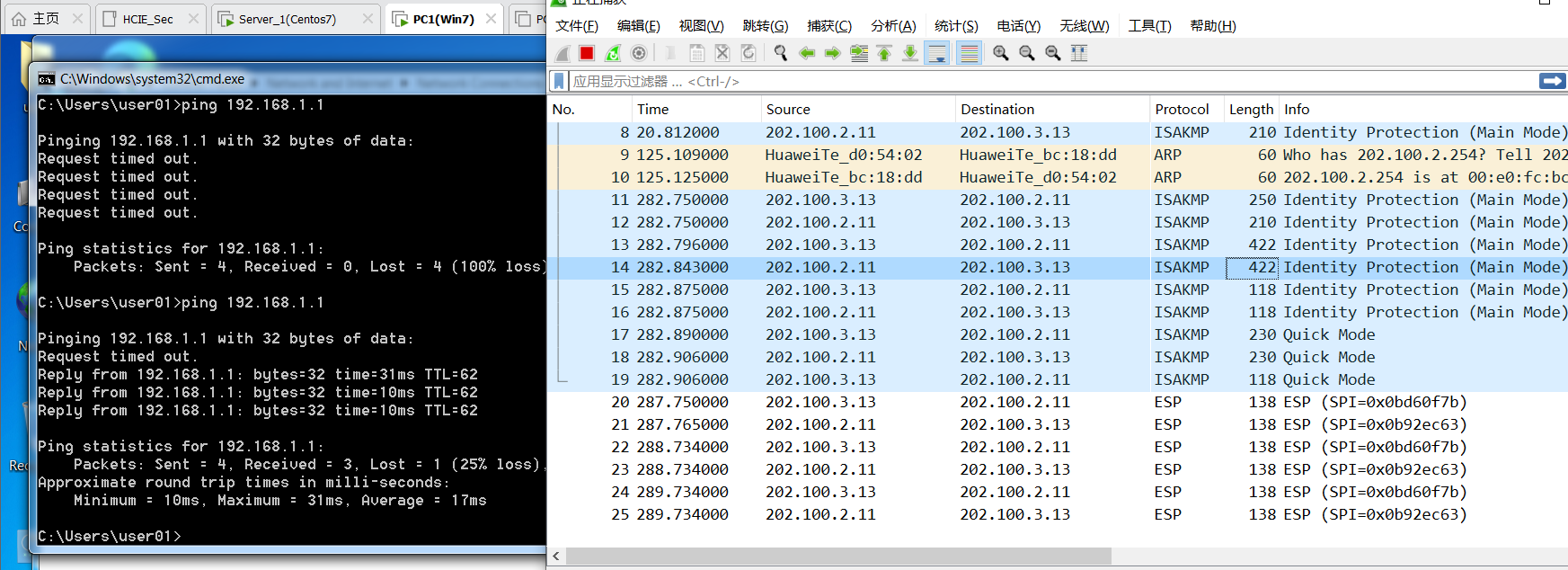
1.使用PC1与Server1通信并抓包发现完成了IPSec的通信
2.查看IKE SA,确实是由VSYSA发起的
[FW1-VSYSA]display ike sa 2022-10-26 03:14:09.510 IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------------------------------------------------------------------ 3 202.100.2.11:500 - RD|ST|A v1:2 IP 202.100.2.11 2 202.100.2.11:500 - RD|ST|A v1:1 IP 202.100.2.11 Number of IKE SA : 2 ------------------------------------------------------------------------------------------------------------------------------------ Flag Description: RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING
3.查看IPSec加密解封装,也确实是三个包
[FW1-VSYSA]display ipsec statistics 2022-10-26 03:14:56.180 IPSec statistics information: Number of IPSec tunnels: 1 Number of standby IPSec tunnels: 0 the security packet statistics: input/output security packets: 3/3 input/output security bytes: 180/180 input/output dropped security packets: 0/0 the encrypt packet statistics: send chip: 3, recv chip: 3, send err: 0 local cpu: 3, other cpu: 0, recv other cpu: 0 intact packet: 3, first slice: 0, after slice: 0 the decrypt packet statistics: send chip: 3, recv chip: 3, send err: 0 local cpu: 3, other cpu: 0, recv other cpu: 0 reass first slice: 0, after slice: 0
4.查看IPSec sa,可以看见IPSec的配置,NAT穿越并未置一。
[FW1-VSYSA]dis ipsec sa 2022-10-26 03:15:45.160 ipsec sa information: =============================== Interface: Virtual-if1 =============================== ----------------------------- IPSec policy name: "ipsec1" Sequence number : 1 Acl group : 3000 Acl rule : 5 Mode : ISAKMP ----------------------------- Connection ID : 3 Encapsulation mode: Tunnel Holding time : 0d 0h 5m 11s Tunnel local : 202.100.3.13:500 Tunnel remote : 202.100.2.11:500 Flow source : 10.1.1.0/255.255.255.0 0/0-65535 Flow destination : 192.168.1.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 198578043 (0xbd60f7b) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/3289 Max sent sequence-number: 4 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 3/180 [Inbound ESP SAs] SPI: 194178147 (0xb92ec63) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/3289 Max received sequence-number: 1 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 3/180 Anti-replay : Enable Anti-replay window size: 1024
5.查看会话表
VSYSA:
[FW1-VSYSA]display firewall session table verbose 2022-10-26 03:17:11.200 Current Total Sessions : 3 icmp VPN: VSYSA --> public ID: c387f05d761c998a4b6358a6b4 Zone: trust --> untrust TTL: 00:00:20 Left: 00:00:17 Recv Interface: GigabitEthernet1/0/0 Interface: Virtual-if1 NextHop: 0.0.0.0 MAC: 0000-0000-0000 <--packets: 0 bytes: 0 --> packets: 1 bytes: 60 10.1.1.1:1 --> 192.168.1.1:2048 PolicyName: vpn_pc esp VPN: VSYSA --> VSYSA ID: c487f05d761c63815d06358a52d Zone: untrust --> local TTL: 00:10:00 Left: 00:03:30 Recv Interface: Virtual-if1 Interface: InLoopBack0 NextHop: 127.0.0.1 MAC: 0000-0000-0000 <--packets: 0 bytes: 0 --> packets: 3 bytes: 372 202.100.2.11:0 --> 202.100.3.13:0 PolicyName: ipsec udp VPN: VSYSA --> VSYSA ID: c487f05d761c8c020386358a6af Zone: untrust --> local TTL: 00:02:00 Left: 00:01:57 Recv Interface: Virtual-if1 Interface: InLoopBack0 NextHop: 127.0.0.1 MAC: 0000-0000-0000 <--packets: 5 bytes: 1,068 --> packets: 6 bytes: 1,164 202.100.2.11:500 --> 202.100.3.13:500 PolicyName: ipsec
FW1根系统:
[FW1]display firewall session table verbose 2022-10-26 03:18:07.460 Current Total Sessions : 2 udp VPN: public --> VSYSA ID: c387f05d761c7e8df26358a6af Zone: untrust --> trust TTL: 00:02:00 Left: 00:01:01 Recv Interface: GigabitEthernet1/0/1 Interface: Virtual-if0 NextHop: 0.0.0.0 MAC: 0000-0000-0000 <--packets: 5 bytes: 1,068 --> packets: 6 bytes: 1,164 202.100.2.11:500 --> 202.100.3.13:500 PolicyName: ipsec esp VPN: public --> VSYSA ID: c487f05d761c56022dd6358a52d Zone: untrust --> trust TTL: 00:10:00 Left: 00:09:08 Recv Interface: GigabitEthernet1/0/1 Interface: Virtual-if0 NextHop: 0.0.0.0 MAC: 0000-0000-0000 <--packets: 0 bytes: 0 --> packets: 6 bytes: 744 202.100.2.11:0 --> 202.100.3.13:0 PolicyName: ipsec
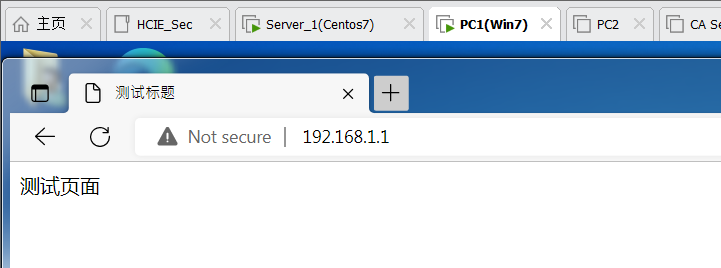
6,经过隧道加密,PC1同样可以访问http服务






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· AI 智能体引爆开源社区「GitHub 热点速览」
· 写一个简单的SQL生成工具