*reverse*_练习1__elrond32
今日学习61
1.
老样子,拿到题后,找字符串

双击进入,f5反编译
找到关键函数,这个
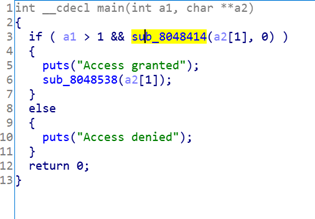
函数就是flag的关键所在,被允许进入后的函数,和判断函数非常关键



根据手算,以及a1%8来得知key的大小为8,
Key[105,115,101,110,103,97,114,100]
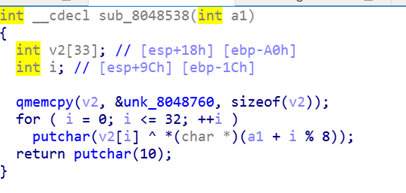

print(flag)
key=[105,115,101,110,103,97,114,100]
v2=[0x0F,0x1F,0x04,0x09,0x1C,0x12,0x42,0x09,0x0C,0x44,0x0D,0x07,0x09,0x06,0x2D,0x37,0x59,0x1E,0x00,0x59,0x0F,0x08,0x1C,0x23,0x36,0x07,0x55,0x02,0x0C,0x08,0x41,0x0A,0x14]
flag=''
for i in range(33):
flag+=chr(v2[i]^key[i%8])
print(flag)
得出Flag
flag{s0me7hing_S0me7hinG_t0lki3n}


