项目环境搭建【Docker+k8s】十二 || kubernetes Ingress Controller
我们的目的就是将入口统一,不在通过LoadBalance等方式将端口暴露出来,而是使用Ingress提供的反向代理、负载均衡功能作为我们的唯一入口。Ingress Controller有很多种,我们选择最熟悉的Nginx来处理请求。Ingress-nginx安装文档,本文中主要选择nodePort和hostNetwork两种部署方式进行介绍。
- nodePort部署模式中需要部署的ingress-controller容器较少,一个集群可以部署几个就可以了。
而hostNetwork模式需要在每个节点部署一个ingress-controller容器,因此总起来消耗资源较多。 - nodePort模式主要占用的是svc的nodePort端口。而hostNetwork则需要占用物理机的80和443端口。
- 通过nodePort访问时,nginx接收到的http请求中的source ip将会被转换为接受该请求的node节点的ip,而非真正的client端ip。
而使用hostNetwork的方式,ingress-controller将会使用的是物理机的DNS域名解析(即物理机的/etc/resolv.conf)。而无法使用内部的比如coredns的域名解析。
1、安装Ingress-nginx(nodePort模式)
下载Nginx Controller配置文件。
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.26.1/deploy/static/mandatory.yaml
#github地址
https://github.com/kubernetes/ingress-nginx/tree/nginx-0.26.1/deploy/static/mandatory.yaml
通过资源文件部署
[root@yn101-22 ingress]# kubectl apply -f mandatory.yaml
#输出如下
namespace/ingress-nginx created
configmap/nginx-configuration created
configmap/tcp-services created
configmap/udp-services created
serviceaccount/nginx-ingress-serviceaccount created
clusterrole.rbac.authorization.k8s.io/nginx-ingress-clusterrole created
role.rbac.authorization.k8s.io/nginx-ingress-role created
rolebinding.rbac.authorization.k8s.io/nginx-ingress-role-nisa-binding created
clusterrolebinding.rbac.authorization.k8s.io/nginx-ingress-clusterrole-nisa-binding created
deployment.apps/nginx-ingress-controller created
通过命令查看ingress-nginx安装情况
#NodePort方式对外提供服务
[root@yn101-22 ingress]# kubectl get pods -n ingress-nginx -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-ingress-controller-69969b98db-tjl84 1/1 Running 0 2m3s 10.244.1.2 yn101-31.host.com <none> <none>
通过ingress-controller对外提供服务,还需手动部署一个servcie,接收集群外部流量。
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.26.1/deploy/static/provider/baremetal/service-nodeport.yaml
#github地址
https://github.com/kubernetes/ingress-nginx/blob/nginx-0.26.1/deploy/static/provider/baremetal/service-nodeport.yaml
#执行yaml
kubectl apply -f service-nodeport.yaml
2、安装Ingress-nginx(hostNetwork模式)
下载Nginx Controller配置文件,本教程选择的版本为v0.26.1,配置文件中查看所需的镜像image: quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.26.1,
国内下载镜像由于网络的原因,提前拉取镜像到本地。
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.26.1/deploy/static/mandatory.yaml
#github地址
https://github.com/kubernetes/ingress-nginx/tree/nginx-0.26.1/deploy/static/mandatory.yaml
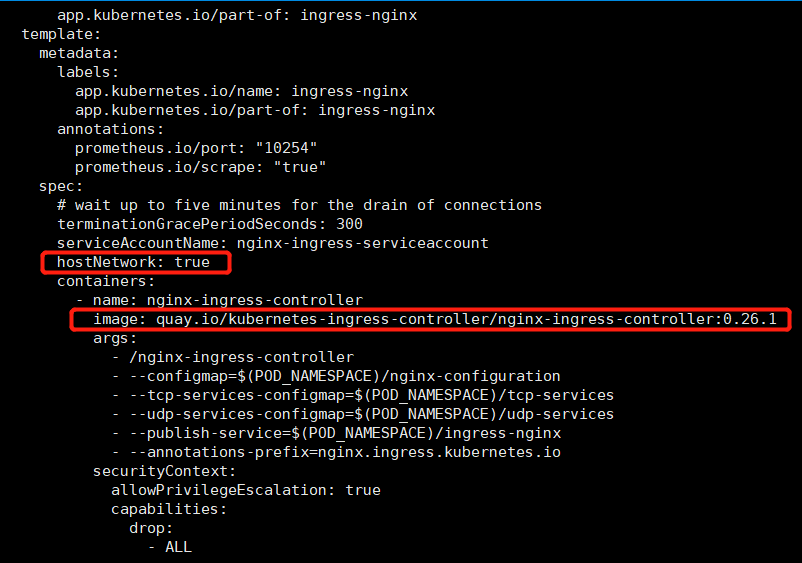
修改配置文件,找到如下位置(搜索serviceAccountName)在下面增加hostNetwork:true
,目的是开启主机网络模式,暴露nginx服务端口80
通过资源文件部署
[root@yn101-22 ingress]# kubectl apply -f mandatory.yaml
#输出如下
namespace/ingress-nginx created
configmap/nginx-configuration created
configmap/tcp-services created
configmap/udp-services created
serviceaccount/nginx-ingress-serviceaccount created
clusterrole.rbac.authorization.k8s.io/nginx-ingress-clusterrole created
role.rbac.authorization.k8s.io/nginx-ingress-role created
rolebinding.rbac.authorization.k8s.io/nginx-ingress-role-nisa-binding created
clusterrolebinding.rbac.authorization.k8s.io/nginx-ingress-clusterrole-nisa-binding created
deployment.apps/nginx-ingress-controller created
通过命令查看ingress-nginx安装情况
#NodePort方式对外提供服务
[root@yn101-22 ingress]# kubectl get pods -n ingress-nginx -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-ingress-controller-69969b98db-tjl84 1/1 Running 0 2m3s 10.244.1.2 yn101-31.host.com <none> <none>
#hostNetwork方式对外提供服务
[root@yn101-22 ingress]# kubectl get pods -n ingress-nginx -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-ingress-controller-6f7bc978b-tzzrj 1/1 Running 0 27m 192.168.101.32 yn101-32.host.com <none> <none>
安装过程中READY状态为0/1,或者STATUS状态不是Running,可用如下命令查看具体错误信息,如果为镜像拉取失败,下载镜像包手动加载。
kubectl describe pod <myapp-pod> -n ingress-nginx
ingress示例:在k8s里面部署一个tomcat,在内网里面不能访问,通过nginx反向代理到tomcat
通过tomcat.yaml资源配置文件部署tomcat,模式更改为ClusterIP,表示只在内网提供服务
apiVersion: apps/v1
kind: Deployment
#元数据
metadata:
name: tomcat-app
spec:
selector:
matchLabels:
app: tomcat
replicas: 2
template:
metadata:
labels:
app: tomcat
spec:
containers:
- name: tomcat
image: tomcat:8.5.43
imagePullPolicy: IfNotPresent
ports:
- containerPort: 8080
---
apiVersion: v1
kind: Service
metadata:
name: tomcat-http
spec:
ports:
- port: 8080
targetPort: 8080
# ClusterIP NodePort LoadBalancer
type: ClusterIP
selector:
app: tomcat
查看服务启动,可以看到服务暴露模式为ClusterIP,对内服务的端口为8080,没有对外暴露端口,所以在内网是访问不到的
[root@yn101-22 service]# kubectl apply -f tomcat.yml
deployment.apps/tomcat-app created
[root@yn101-22 service]# kubectl get pods
NAME READY STATUS RESTARTS AGE
tomcat-app-54ccd97f96-9d6x4 1/1 Running 0 2m5s
tomcat-app-54ccd97f96-kr5ds 1/1 Running 0 2m5s
[root@yn101-22 service]# kubectl get deployment
NAME READY UP-TO-DATE AVAILABLE AGE
tomcat-app 2/2 2 2 2m19s
[root@yn101-22 service]# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 3d7h
tomcat-http ClusterIP 10.104.129.49 <none> 8080/TCP 3m4s
部署ingress-nginx,创建一个ingress.yaml的配置文件
apiVersion: extensions/v1beta1 #networking.k8s.io/v1betal
kind: Ingress
metadata:
name: nginx-web
#namespace: default
annotations:
#指定ingress controller的类型
kubernetes.io/ingress.class: "nginx"
#指定我们的roles的path可以使用正则表达式
nginx.ingress.kubernetes.io/use-regex: "true"
#连接超时时间,默认为5s
nginx.ingress.kubernetes.io/proxy-send-timeout: "600"
#后端服务器回转数据超时时间,默认60s
nginx.ingress.kubernetes.io/proxy-read-timeout: "600"
#客户端上传文件最大大小,默认20m
nginx.ingress.kubernetes.io/proxy-body-timeout: "100m"
#URL重写
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
#路由规则
rules:
#主机名,只能是域名
- host: ingress.yn.com #生产中该域名应当可以被公网解析
http:
paths:
- path:
backend:
#后台部署的service name
serviceName: tomcat-http
#后台部署的service port
servicePort: 8080
部署ingress入口路由规则,通过ingress.yn.com域名进行访问tomcat
[root@yn101-22 ingress]# kubectl apply -f ingress.yml
ingress.extensions/nginx-web created
[root@yn101-22 ingress]# kubectl get ingress
NAME HOSTS ADDRESS PORTS AGE
nginx-web ingress.yn.com 80 8s
所以,通过Ingress访问的逻辑为:Client Request -> Ingress-service(通过NodePort暴露端口) -> Ingress -> Service -> Deployment
3、学习交流QQ群【883210148】
4、关注微信公众号,免费获取文档及资源