Simplecheck
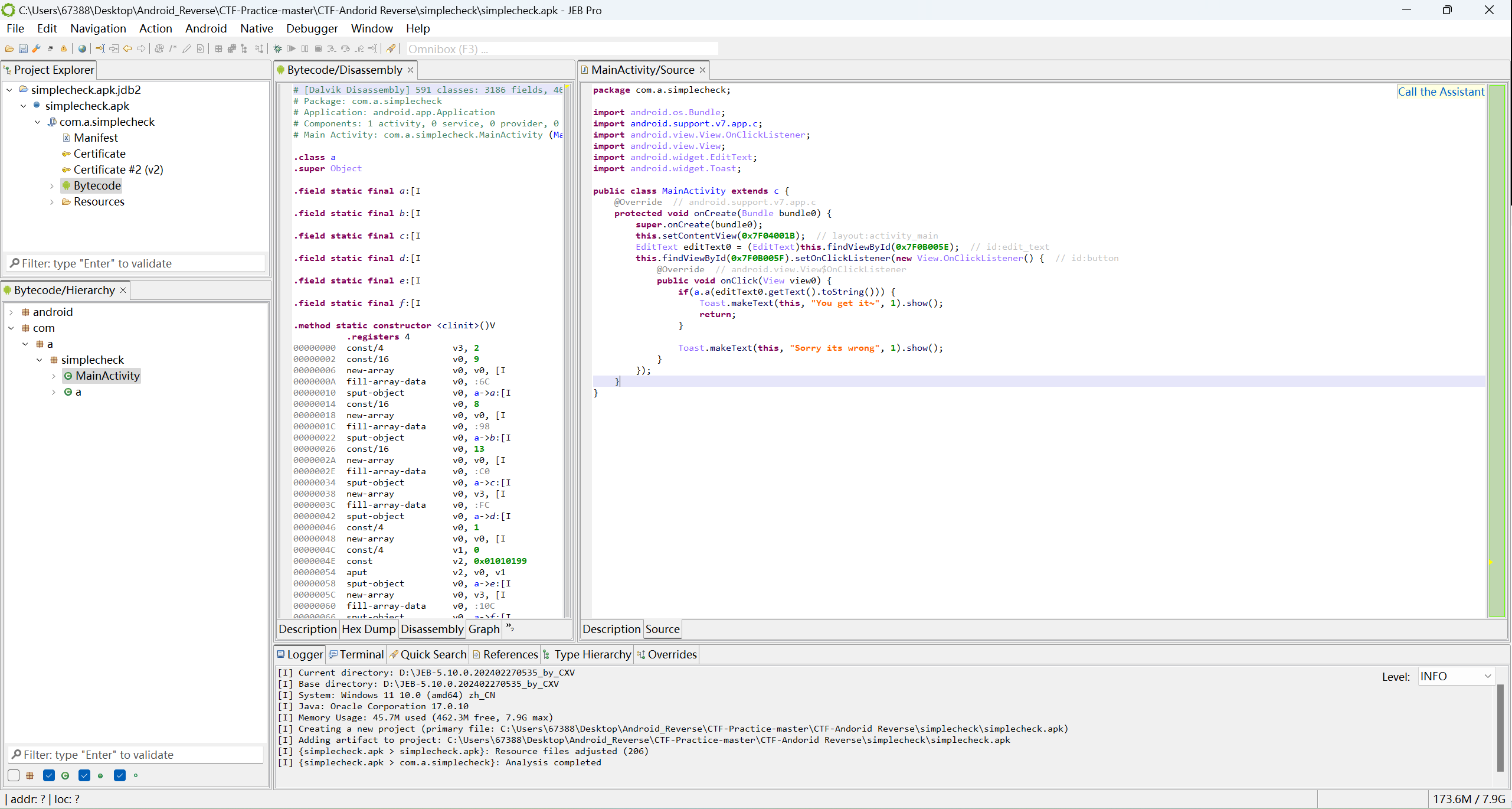
点开a函数,是一个check函数
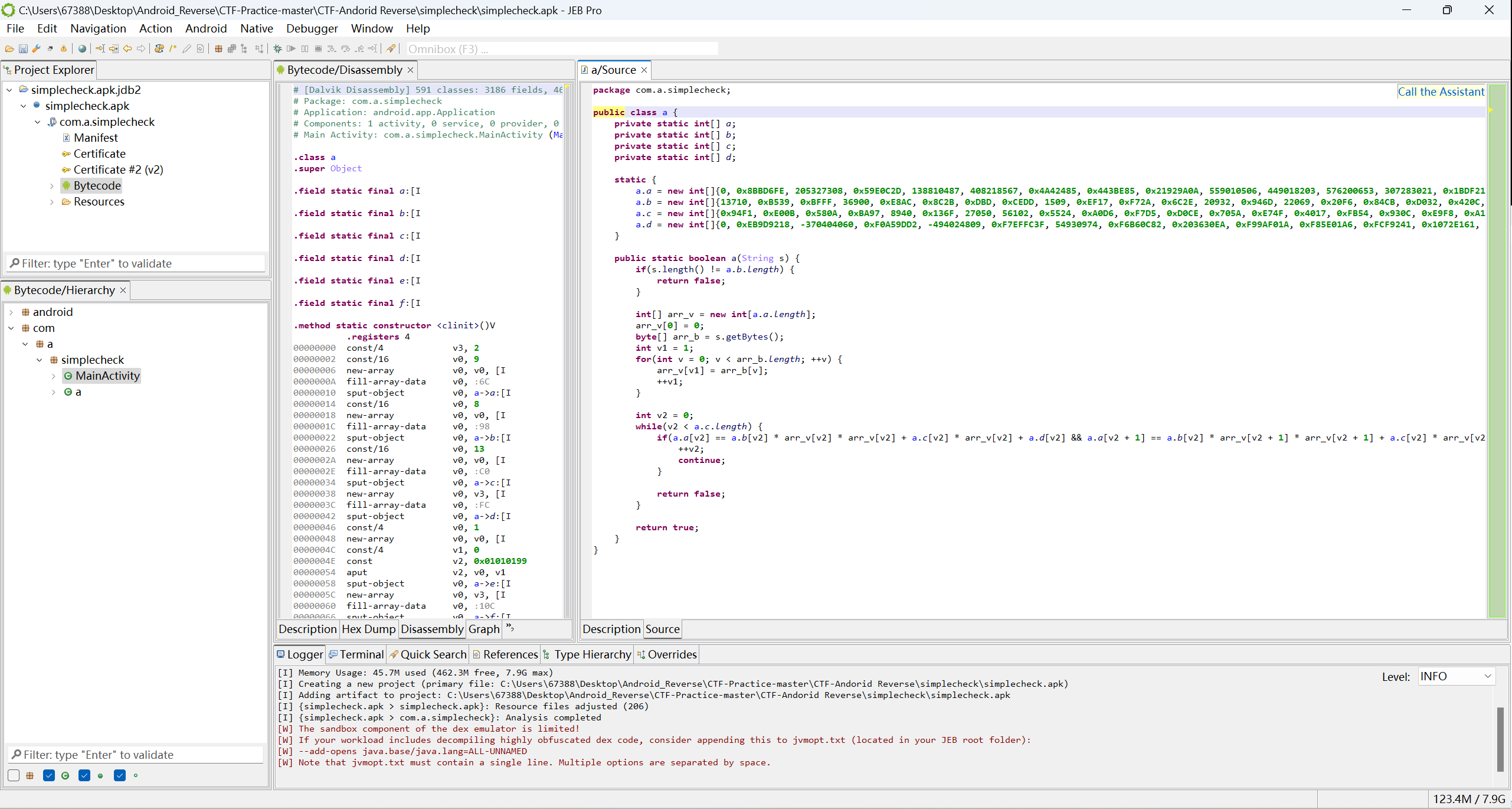
编写脚本
a = [0, 0x8BBD6FE, 205327308, 0x59E0C2D, 138810487, 408218567, 0x4A42485, 0x443BE85, 0x21929A0A, 559010506, 449018203, 576200653, 307283021, 0x1BDF218B, 314806739, 0x1459AAFB, 0x1459AAFB, 0x1C039BBC, 0x18E61B76, 342206934, 392460324, 382290309, 0xB0F0211, 364788505, 210058699, 0xBCF56CF, 0x1580960D, 440064477, 0x1310B245, 0x284EE4B3, 0x1732EFAB, 0x3175430D, 0x1FE113C4, 0x197B593C, 0x33806C28]
b = [13710, 0xB539, 0xBFFF, 36900, 0xE8AC, 0x8C2B, 0xDBD, 0xCEDD, 1509, 0xEF17, 0xF72A, 0x6C2E, 20932, 0x946D, 22069, 0x20F6, 0x84CB, 0xD032, 0x420C, 30902, 0xFC5A, 0xFA1C, 0x73BD, 0x67A9, 0x2EFA, 31610, 0xBDFF, 0x4E00, 0xB256, 0xCB04, 0xFDBC, 0xB0ED, 0xFCF0, 0x90F4]
c = [0x94F1, 0xE00B, 0x580A, 0xBA97, 8940, 0x136F, 27050, 56102, 0x5524, 0xA0D6, 0xF7D5, 0xD0CE, 0x705A, 0xE74F, 0x4017, 0xFB54, 0x930C, 0xE9F8, 0xA13C, 0x6528, 27501, 0x9820, 0x90AF, 0x9545, 0xF192, 0xA9E9, 0x2405, 9879, 0x3864, 60468, 0x4DD6, 0xB85E, 8406, 0xFC9A]
d = [0, 0xEB9D9218, -370404060, 0xF0A59DD2, -494024809, 0xF7EFFC3F, 54930974, 0xF6B60C82, 0x203630EA, 0xF99AF01A, 0xF85E01A6, 0xFCF9241, 0x1072E161, 119059597, 202392013, 0x10E88ED9, 0x786F15C, -68971076, 0xF91DD26, 0xBC673D6, 0xFF3B4367, -10293675, 0x598502B, 0x7406995, 0x9FB416F, 0x758311F, 221507, 0xF6EB9D4, 180963987, 107841171, 41609001, 0x107B88B5, 0xA21BFA2, 0x1075D862]
flag = ""
for m in range(1, 34):
for i in range(0,127):
if(a[m] == b[m] * i * i + c[m] * i + d[m]) | (a[m] == b[m-1] * i * i + c[m-1] * i + d[m-1]):
flag += chr(i)
break
print(flag)
但是这个flag是有问题的
经过我的验证,发现是JEB写出的d的数据有误,我们复制JADX中的数据即可得出正确flag
a = [0, 0x8BBD6FE, 205327308, 0x59E0C2D, 138810487, 408218567, 0x4A42485, 0x443BE85, 0x21929A0A, 559010506, 449018203, 576200653, 307283021, 0x1BDF218B, 314806739, 0x1459AAFB, 0x1459AAFB, 0x1C039BBC, 0x18E61B76, 342206934, 392460324, 382290309, 0xB0F0211, 364788505, 210058699, 0xBCF56CF, 0x1580960D, 440064477, 0x1310B245, 0x284EE4B3, 0x1732EFAB, 0x3175430D, 0x1FE113C4, 0x197B593C, 0x33806C28]
b = [13710, 0xB539, 0xBFFF, 36900, 0xE8AC, 0x8C2B, 0xDBD, 0xCEDD, 1509, 0xEF17, 0xF72A, 0x6C2E, 20932, 0x946D, 22069, 0x20F6, 0x84CB, 0xD032, 0x420C, 30902, 0xFC5A, 0xFA1C, 0x73BD, 0x67A9, 0x2EFA, 31610, 0xBDFF, 0x4E00, 0xB256, 0xCB04, 0xFDBC, 0xB0ED, 0xFCF0, 0x90F4]
c = [0x94F1, 0xE00B, 0x580A, 0xBA97, 8940, 0x136F, 27050, 56102, 0x5524, 0xA0D6, 0xF7D5, 0xD0CE, 0x705A, 0xE74F, 0x4017, 0xFB54, 0x930C, 0xE9F8, 0xA13C, 0x6528, 27501, 0x9820, 0x90AF, 0x9545, 0xF192, 0xA9E9, 0x2405, 9879, 0x3864, 60468, 0x4DD6, 0xB85E, 8406, 0xFC9A]
d = [0, -341994984, -370404060, -257581614, -494024809, -135267265, 54930974, -155841406, 540422378, -107286502, -128056922, 265261633, 275964257, 119059597, 202392013, 283676377, 126284124, -68971076, 261217574, 197555158, -12893337, -10293675, 93868075, 121661845, 167461231, 123220255, 221507, 258914772, 180963987, 107841171, 41609001, 276531381, 169983906, 276158562]
flag = ""
for m in range(1, 34):
for i in range(0,127):
if(a[m] == b[m] * i * i + c[m] * i + d[m]) | (a[m] == b[m-1] * i * i + c[m-1] * i + d[m-1]):
flag += chr(i)
break
print(flag)
Androideasy
后缀改成apk后拖入JEB中
public class MainActivity extends AppCompatActivity {
private EditText editText;
private byte[] s;
public MainActivity() {
this.s = new byte[]{0x71, 0x7B, 0x76, 0x70, 108, 94, 99, 72, 38, 68, 72, 87, 89, 72, 36, 0x76, 100, 78, 72, 87, 0x79, 83, 101, 39, 62, 94, 62, 38, 107, 0x73, 106};
}
public boolean check() {
byte[] arr_b = this.editText.getText().toString().getBytes();
if(arr_b.length != this.s.length) {
return false;
}
int i = 0;
while(i < this.s.length && i < arr_b.length) {
if(this.s[i] == (arr_b[i] ^ 23)) {
++i;
continue;
}
return false;
}
return true;
}
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
this.setContentView(0x7F04001B);
this.editText = (EditText)this.findViewById(0x7F0B0057);
this.findViewById(0x7F0B0058).setOnClickListener(new View.OnClickListener() {
@Override
public void onClick(View v) {
if(MainActivity.this.check()) {
Toast.makeText(this, "You got the flag!", 1).show();
return;
}
Toast.makeText(this, "Sorry your flag is wrong", 1).show();
}
});
}
}
用python脚本爆破
a = [0x71, 0x7B, 0x76, 0x70, 108, 94, 99, 72, 38, 68, 72, 87, 89, 72, 36, 0x76, 100, 78, 72, 87, 0x79, 83, 101, 39, 62, 94, 62, 38, 107, 0x73, 106]
flag = ""
for i in range(0,31):
for j in range(0, 127):
if a[i] == j ^ 23:
flag += chr(j)
print(flag)
[HZNUCTF 2023 preliminary]easyAPK
JEB打开,找到login函数
package com.example.easyapk;
import android.content.Intent;
import android.os.Bundle;
import android.view.View.OnClickListener;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
import java.security.InvalidAlgorithmParameterException;
import java.security.InvalidKeyException;
import java.security.NoSuchAlgorithmException;
import javax.crypto.BadPaddingException;
import javax.crypto.Cipher;
import javax.crypto.IllegalBlockSizeException;
import javax.crypto.NoSuchPaddingException;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
public class llooggiinn extends AppCompatActivity {
Button loginBtn;
EditText passwdEt;
Button signBtn;
static String str1;
static String str2;
EditText userEt;
static {
llooggiinn.str1 = "admin";
}
public static byte[] decrypt(byte[] data, byte[] key, byte[] iv) throws NoSuchPaddingException, NoSuchAlgorithmException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException, InvalidAlgorithmParameterException {
Cipher cipher0 = Cipher.getInstance("AES/CBC/PKCS5Padding");
cipher0.init(2, new SecretKeySpec(key, "AES"), new IvParameterSpec(iv));
return cipher0.doFinal(data);
}
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
this.setContentView(0x7F0B001D);
this.userEt = (EditText)this.findViewById(0x7F0801A2);
this.passwdEt = (EditText)this.findViewById(0x7F08011D);
this.loginBtn = (Button)this.findViewById(0x7F0800D0);
this.signBtn = (Button)this.findViewById(0x7F08014E);
llooggiinn.str2 = "reiseasy";
this.loginBtn.setOnClickListener(new View.OnClickListener() {
@Override
public void onClick(View view) {
String s = llooggiinn.this.userEt.getText().toString();
String s1 = llooggiinn.this.passwdEt.getText().toString();
if((s1.equals("") | s.equals("")) != 0) {
Toast.makeText(llooggiinn.this, "想空手套白狼?没门!", 0).show();
return;
}
if((s.equals("admin")) && (s1.equals(llooggiinn.str2))) {
Intent intent = new Intent(llooggiinn.this, ffuucc.class);
llooggiinn.this.startActivity(intent);
Toast.makeText(llooggiinn.this, "恭喜你,离成功又进一步", 0).show();
return;
}
Toast.makeText(llooggiinn.this, "用户名或密码不正确", 0).show();
}
});
this.signBtn.setOnClickListener(new View.OnClickListener() {
@Override
public void onClick(View view) {
Toast.makeText(llooggiinn.this, "不支持注册喵~\n快去找登录名和密码", 0).show();
}
});
}
@Override
protected void onStart() {
super.onStart();
}
}
这里JEB直接帮我们省了一个AES解密步骤,直接将用户名和密码告诉我们了
用户名是str1 = admin,密码是str2 = reiseasy
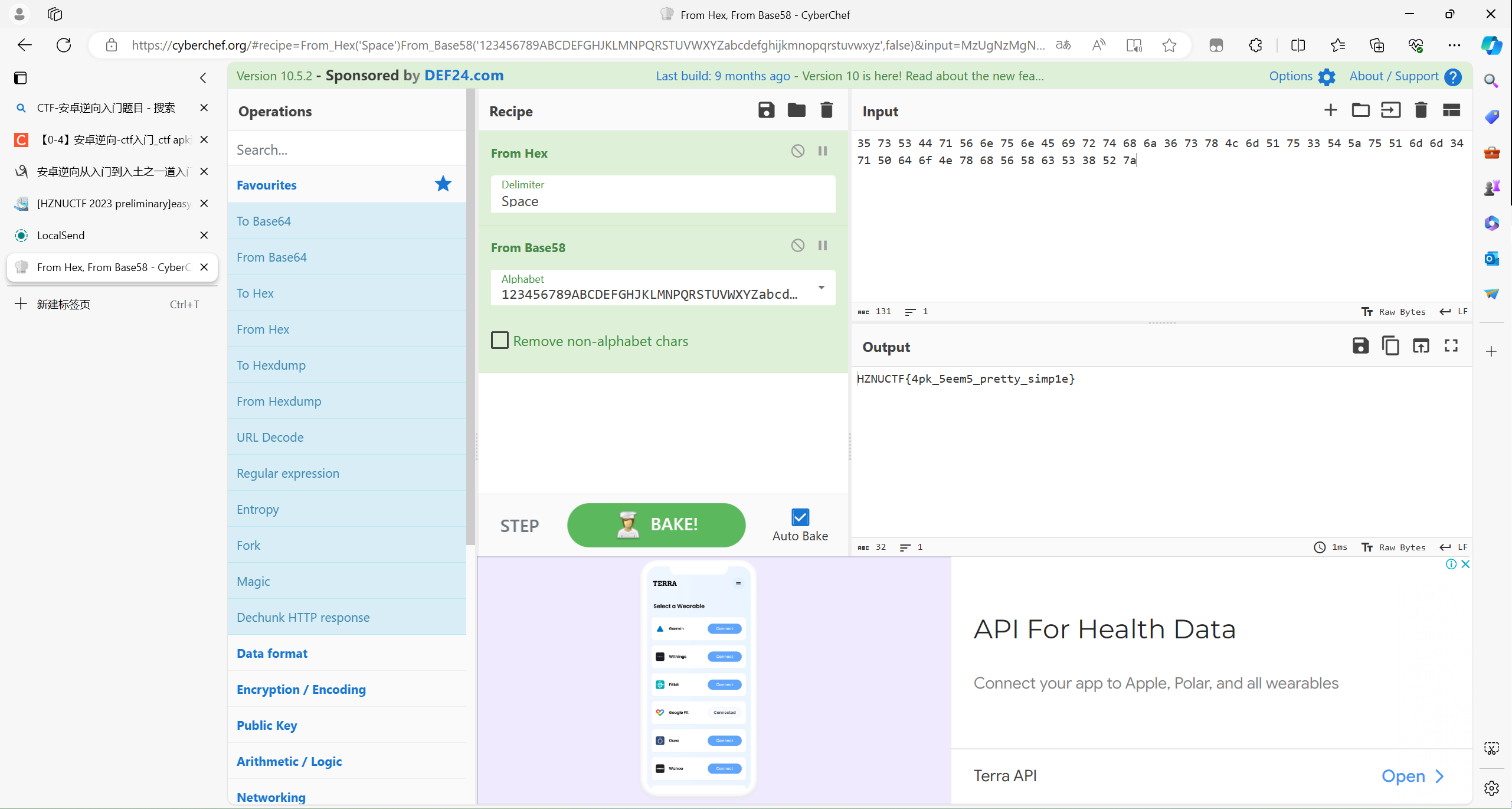
在手机端输入后得到以下图片
Android2
JEB打开看到MainActivity
package com.example.ilililililil;
import android.os.Bundle;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
public class MainActivity extends AppCompatActivity {
public static Encoder encoder;
public static MainActlvity mainActlvity;
@Override
protected void onCreate(Bundle bundle0) {
super.onCreate(bundle0);
this.setContentView(0x7F0B001C);
Button button0 = (Button)this.findViewById(0x7F080057);
EditText editText0 = (EditText)this.findViewById(0x7F080090);
MainActivity.encoder = new Encoder();
MainActivity.mainActlvity = new MainActlvity();
button0.setOnClickListener((View view0) -> {
System.out.println(MainActivity.encoder.encode(editText0.getText().toString()));
if(MainActivity.encoder.encode(editText0.getText().toString()).equals("棿棢棢棲棥棷棊棐棁棚棨棨棵棢棌")) {
Toast.makeText(this, "YES", 0).show();
return;
}
Toast.makeText(this, "NO", 0).show();
});
}
}
我们再看到Encoder函数
package com.example.ilililililil;
public class Encoder {
private int key;
public Encoder() {
this.key = 0x75BCD15;
}
public String encode(String s) {
StringBuilder stringBuilder0 = new StringBuilder();
char[] arr_c = s.toCharArray();
for(int v = 0; v < arr_c.length; ++v) {
stringBuilder0.append(((char)(arr_c[v] ^ this.key)));
}
return stringBuilder0.toString();
}
}
直接写脚本
enc = "棿棢棢棲棥棷棊棐棁棚棨棨棵棢棌"
key = 0x75BCD15
flag = ""
for i in range(len(enc)):
flag += chr(ord(enc[i]) ^ key & 0xFFFF)
print(flag)
但是发现这个flag不对,怀疑是数据错了
经过一番查找,发现第二个MainActivity里有一个换key的操作
![image-20240418213539237]()
我们修改key后重新运行一下
enc = "棿棢棢棲棥棷棊棐棁棚棨棨棵棢棌"
key = 0x3ADE68B1
flag = ""
for i in range(len(enc)):
flag += chr(ord(enc[i]) ^ key & 0xFFFF)
print(flag)
检测一下
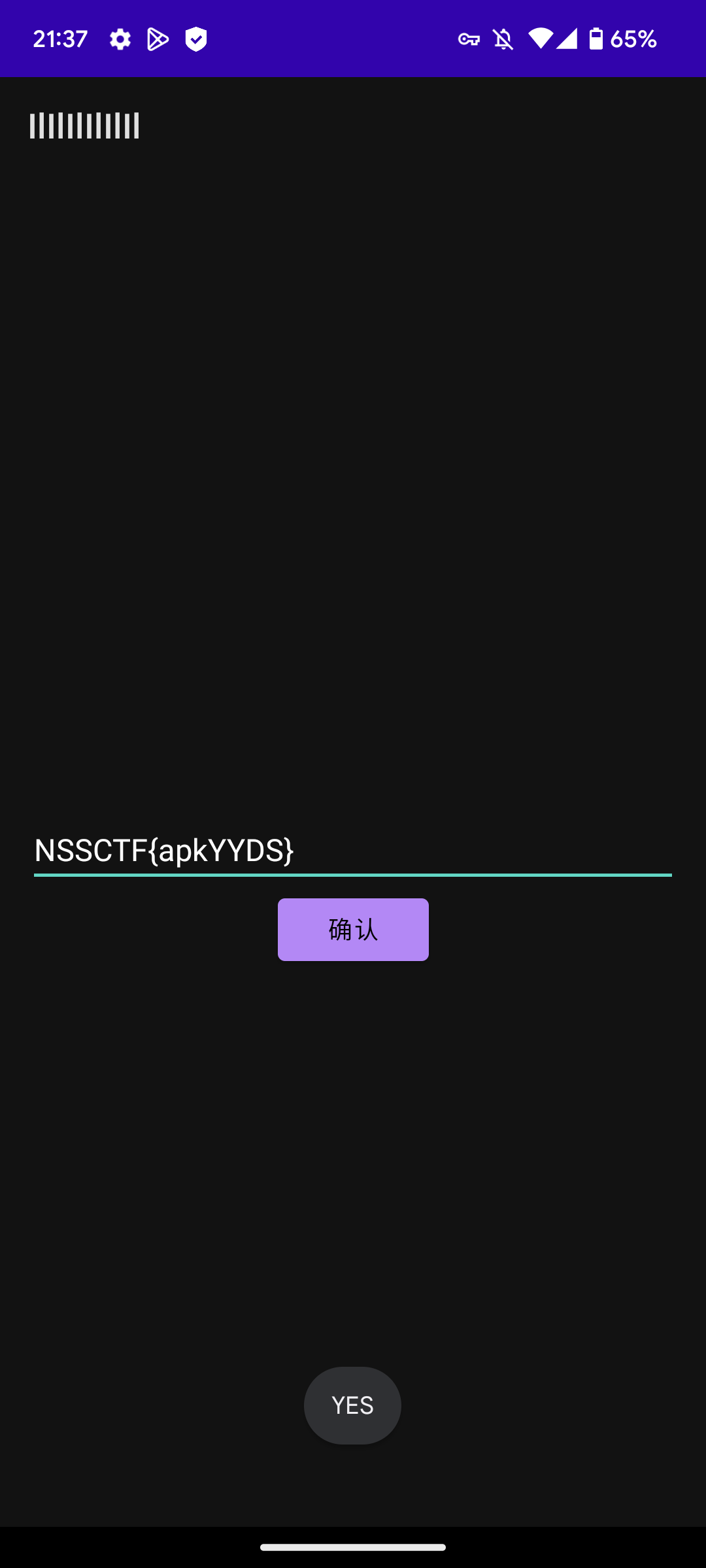
[NSSCTF 2nd]MyAPK
用JEB打开看到主函数
package com.moible.r15;
import android.content.Context;
import android.os.Bundle;
import android.view.View.OnClickListener;
import android.view.View;
import android.widget.Button;
import android.widget.TextView;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
import java.util.Timer;
import java.util.TimerTask;
public class main extends AppCompatActivity {
private TextView info;
private Button start;
private Boolean started;
private Button stop;
private int success;
private Timer timer;
private TimerTask timerTask;
private Toast ts;
public main() {
this.started = Boolean.valueOf(false);
this.success = 0;
}
String getit(String input) {
int g;
int f;
int d;
int v12;
byte[] message;
int[] T = new int[0x40];
for(int i = 0; i < 0x40; ++i) {
T[i] = (int)(((long)(Math.abs(Math.sin(i + 1)) * 4294967296.0)));
}
byte[] arr_b = input.getBytes();
int messageLength = arr_b.length;
int numBlocks = (messageLength + 8 >>> 6) + 1;
byte[] paddedMessage = new byte[numBlocks << 6];
System.arraycopy(arr_b, 0, paddedMessage, 0, messageLength);
paddedMessage[messageLength] = (byte)0x80;
for(int i = 0; i < 8; ++i) {
paddedMessage[(numBlocks << 6) - 8 + i] = (byte)(((int)(((long)messageLength) * 8L >>> i * 8)));
}
int[] arr_v1 = {0x98BADCFE, 0xEFCDAB89, 0x10325476, 0x67452301};
int i = 0;
while(i < numBlocks) {
int[] block = new int[16];
for(int j = 0; j < 16; ++j) {
int index = (i << 6) + (j << 2);
block[j] = paddedMessage[index] & 0xFF | (paddedMessage[index + 1] & 0xFF) << 8 | (paddedMessage[index + 2] & 0xFF) << 16 | (paddedMessage[index + 3] & 0xFF) << 24;
}
int a = arr_v1[0];
int b = arr_v1[1];
int c = arr_v1[2];
int d = arr_v1[3];
int j = 0;
while(j < 0x40) {
if(j < 16) {
message = arr_b;
v12 = messageLength;
d = d;
f = ~b & d | b & c;
g = j;
}
else {
message = arr_b;
v12 = messageLength;
d = d;
if(j < 0x20) {
f = d & b | ~d & c;
g = (j * 5 + 1) % 16;
}
else if(j < 0x30) {
f = b ^ c ^ d;
g = (j * 3 + 5) % 16;
}
else {
f = (~d | b) ^ c;
g = j * 7 % 16;
}
}
int d = c;
c = b;
b += Integer.rotateLeft(a + f + block[g] + T[j], 7);
a = d;
++j;
d = d;
arr_b = message;
messageLength = v12;
T = T;
block = block;
}
arr_v1[0] += a;
arr_v1[1] += b;
arr_v1[2] += c;
arr_v1[3] += d;
++i;
messageLength = messageLength;
T = T;
}
byte[] hash = new byte[16];
for(int i = 0; i < 4; ++i) {
hash[i * 4] = (byte)(arr_v1[i] & 0xFF);
hash[i * 4 + 1] = (byte)(arr_v1[i] >>> 8 & 0xFF);
hash[i * 4 + 2] = (byte)(arr_v1[i] >>> 16 & 0xFF);
hash[i * 4 + 3] = (byte)(arr_v1[i] >>> 24 & 0xFF);
}
StringBuilder sb = new StringBuilder();
for(int i = 0; i < 16; ++i) {
sb.append(String.format("%02x", ((int)(hash[i] & 0xFF))));
}
return sb.toString();
}
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
this.setContentView(layout.hello);
this.stop = (Button)this.findViewById(id.stop);
this.start = (Button)this.findViewById(id.start);
this.info = (TextView)this.findViewById(id.info);
this.start.setOnClickListener(new View.OnClickListener() {
@Override
public void onClick(View v) {
main.this.start.setEnabled(false);
main.this.started = Boolean.valueOf(true);
Timer timer0 = new Timer();
main.this.timer = timer0;
com.moible.r15.main.1.1 main$1$10 = new TimerTask() {
Double cnt;
{
this.cnt = (double)0.0;
}
@Override
public void run() {
TextView textView0 = main.this.info;
Double d = this.cnt;
this.cnt = (double)(((double)d) + 1.0);
textView0.setText(String.format("%.3fs", ((double)(((double)d) / 1000.0))));
}
};
main.this.timerTask = main$1$10;
main.this.timer.scheduleAtFixedRate(main.this.timerTask, 0L, 1L);
}
});
this.stop.setOnClickListener(new View.OnClickListener() {
@Override
public void onClick(View v) {
if(!main.this.timerTask.cancel()) {
main.this.timerTask.cancel();
main.this.timer.cancel();
}
main.this.start.setEnabled(true);
if(main.this.info.getText() == "66.666s") {
Context context0 = main.this.getBaseContext();
StringBuilder stringBuilder0 = new StringBuilder().append("flag是:NSSCTF{");
String s = (String)main.this.info.getText();
Toast toast0 = Toast.makeText(context0, stringBuilder0.append(main.this.getit(s)).append("}").toString(), 1);
main.this.ts = toast0;
}
else {
Toast toast1 = Toast.makeText(main.this.getBaseContext(), "时间错误,请再接再厉!", 1);
main.this.ts = toast1;
}
main.this.ts.show();
}
});
}
}
中间说的要为66.666s秒,直接把主函数的加密部分照抄下来,把时间设成66.666s,就可以了
class main{
public static String getit(String input) {
int i;
int messageLength;
byte[] message;
int g;
int messageLength2;
int f;
int[] T = new int[0x40];
for (int i1 = 0; i1 < 0x40; i1++) {
T[i1] = (int)((long)(Math.abs(Math.sin(i1 + 1)) * 4294967296.0));
}
byte[] arr_b = input.getBytes();
int d = arr_b.length;
int numBlocks = ((d + 8) >>> 6) + 1;
int totalLength = numBlocks << 6;
byte[] paddedMessage = new byte[totalLength];
System.arraycopy(arr_b, 0, paddedMessage, 0, d);
paddedMessage[d] = Byte.MIN_VALUE;
long messageBits = d * 8;
int i2 = 0;
while (true) {
i = 8;
if (i2 >= 8) {
break;
}
paddedMessage[(totalLength - 8) + i2] = (byte) (messageBits >>> (i2 * 8));
i2++;
}
int[] state = {0x98BADCFE, 0xEFCDAB89, 0x10325476, 0x67452301};
int i4 = 0;
while (i4 < numBlocks) {
int[] block = new int[16];
for (int j = 0; j < 16; j++) {
int index = (i4 << 6) + (j << 2);
block[j] = (paddedMessage[index] & 255) | ((paddedMessage[index + 1] & 255) << i) | ((paddedMessage[index + 2] & 255) << 16) | ((paddedMessage[index + 3] & 255) << 24);
}
int a = state[0];
int b = state[1];
int c = state[2];
int j2 = 0;
int d2 = state[3];
while (j2 < 64) {
if (j2 < 16) {
message = arr_b;
messageLength = d;
messageLength2 = d2;
f = ((~b) & messageLength2) | (b & c);
g = j2;
} else {
message = arr_b;
messageLength = d;
messageLength2 = d2;
if (j2 < 32) {
f = (messageLength2 & b) | ((~messageLength2) & c);
g = ((j2 * 5) + 1) % 16;
} else if (j2 < 48) {
f = (b ^ c) ^ messageLength2;
g = ((j2 * 3) + 5) % 16;
} else {
f = ((~messageLength2) | b) ^ c;
g = (j2 * 7) % 16;
}
}
int temp = messageLength2;
int d3 = c;
c = b;
b += Integer.rotateLeft(a + f + block[g] + T[j2], 7);
a = temp;
j2++;
d2 = d3;
arr_b = message;
d = messageLength;
T = T;
block = block;
}
int messageLength3 = d;
int messageLength4 = d2;
state[0] = state[0] + a;
state[1] = state[1] + b;
state[2] = state[2] + c;
state[3] = state[3] + messageLength4;
i4++;
d = messageLength3;
T = T;
i = 8;
}
byte[] hash = new byte[16];
for (int i5 = 0; i5 < 4; i5++) {
hash[i5 * 4] = (byte) (state[i5] & 255);
hash[(i5 * 4) + 1] = (byte) ((state[i5] >>> 8) & 255);
hash[(i5 * 4) + 2] = (byte) ((state[i5] >>> 16) & 255);
hash[(i5 * 4) + 3] = (byte) ((state[i5] >>> 24) & 255);
}
StringBuilder sb = new StringBuilder();
for (int i6 = 0; i6 < hash.length; i6++) {
sb.append(String.format("%02x", Integer.valueOf(hash[i6] & 255)));
}
return sb.toString();
}
public static void main(String[] args) {
String my = "66.666s";
System.out.println(getit(my));
}
}









【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 25岁的心里话
· 闲置电脑爆改个人服务器(超详细) #公网映射 #Vmware虚拟网络编辑器
· 零经验选手,Compose 一天开发一款小游戏!
· 通过 API 将Deepseek响应流式内容输出到前端
· AI Agent开发,如何调用三方的API Function,是通过提示词来发起调用的吗