HNCTF 2022 WEEK3
[HNCTF 2022 WEEK3]Double
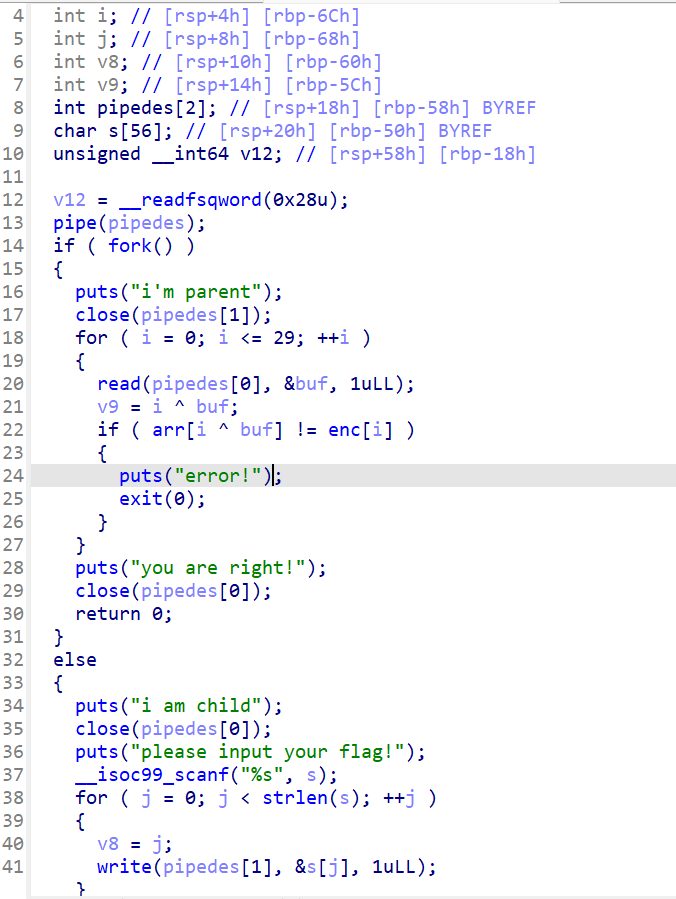
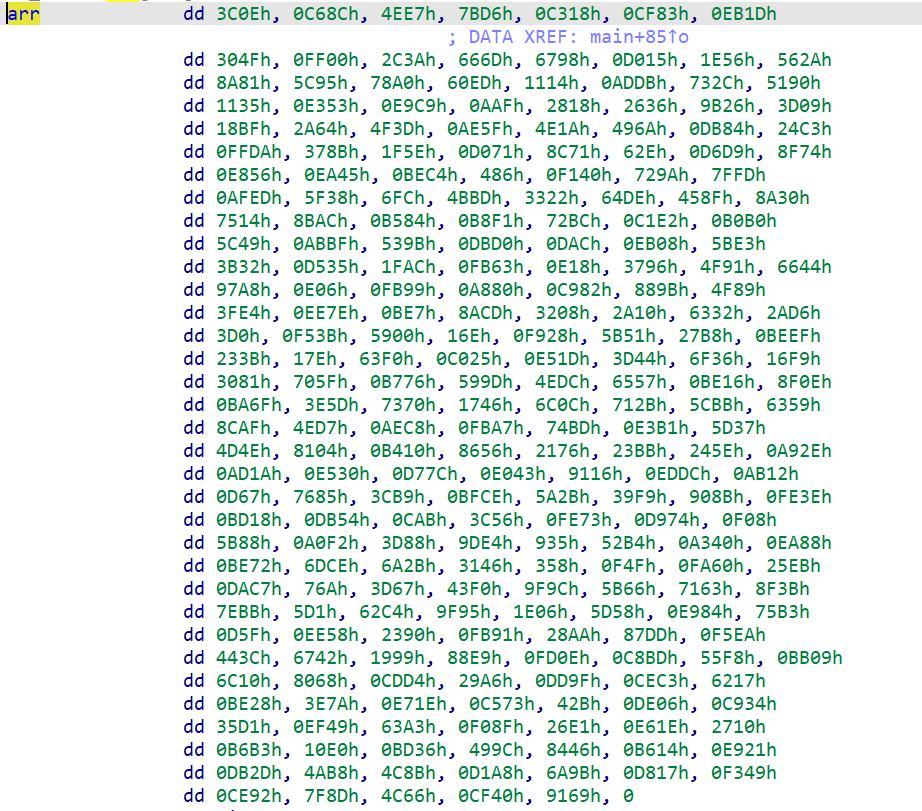
一个简单的异或,arr为
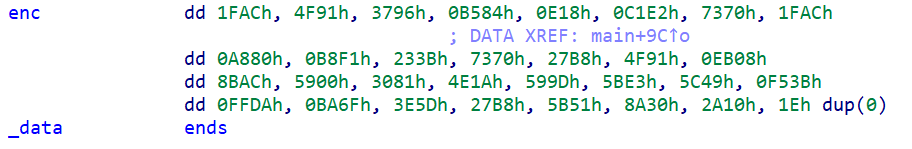
enc为
导出数据,编写脚本
enc = [0x1FAC, 0x4F91, 0x3796, 0x0B584, 0x0E18, 0x0C1E2, 0x7370, 0x1FAC, 0x0A880, 0x0B8F1, 0x233B, 0x7370, 0x27B8, 0x4F91, 0x0EB08, 0x8BAC, 0x5900, 0x3081, 0x4E1A, 0x599D, 0x5BE3, 0x5C49, 0x0F53B, 0x0FFDA, 0x0BA6F, 0x3E5D, 0x27B8, 0x5B51, 0x8A30, 0x2A10, 0x1E]
arr = [15374,50828,20199,31702,49944,53123,60189,12367,65280,11322,26221,26520,53269,7766,22058,35457,23701,30880,24813,4372,44507,29484,20880,4405,58195,59849,2735,10264,9782,39718,
15625,6335,10852,20285,44639,19994,18794,56196,9411,65498,14219,8030,53361,35953,1582,55001,36724,59478,59973,48836,1158,61760,29338,32765,45037,24376,1788,19389,13090,25822,
17807,35376,29972,35756,46468,47345,29372,49634,45232,23625,43967,21403,56272,3500,60168,23523,15154,54581,8108,64355,3608,14230,20369,26180,38824,3590,64409,43136,51586,
34971,20361,16356,61054,3047,35533,12808,10768,25394,10966,976,62779,22784,366,63784,23377,10168,48879,9019,382,25584,49189,58653,15684,28470,5881,12417,28767,46966,22941,
20188,25943,48662,36622,47727,15965,29552,5958,27660,28971,23739,25433,36015,20183,44744,64423,29885,58289,23863,19790,33028,46096,34390,8566,9147,9310,43310,44314,58672,
55164,57411,37142,60892,43794,3431,30341,15545,49102,23083,14841,37003,65086,48408,56148,3243,15446,65139,55668,3848,23432,41202,15752,40420,2357,21172,41792,60040,48754,
28110,27179,12614,856,3919,64096,9707,56007,1898,15719,17392,40860,23398,29027,36667,32443,1489,25284,40853,7686,23896,59780,30131,3423,61016,9104,64401,10410,34781,
62954,17468,26434,6553,35049,64782,51389,22008,47881,27664,32872,52692,10662,56735,52931,25111,48680,15994,59166,50547,1067,56838,51508,13777,61257,25507,61583,9953,
58910,10000,46771,4320,48438,18844,33862,46612,59681,56109,19128,19595,53672,27291,55319,62281,52882,32653,19558,53056,37225,0]
flag = ""
for i in range(30):
flag += chr(arr.index(enc[i]) ^ i)
print(flag)
#NSSCTF{I_Have_D0ub1e_Pr0cess!}
[HNCTF 2022 WEEK3]Try2debugPlusPlus

后面是一个tea加密,前面是一个dododo函数
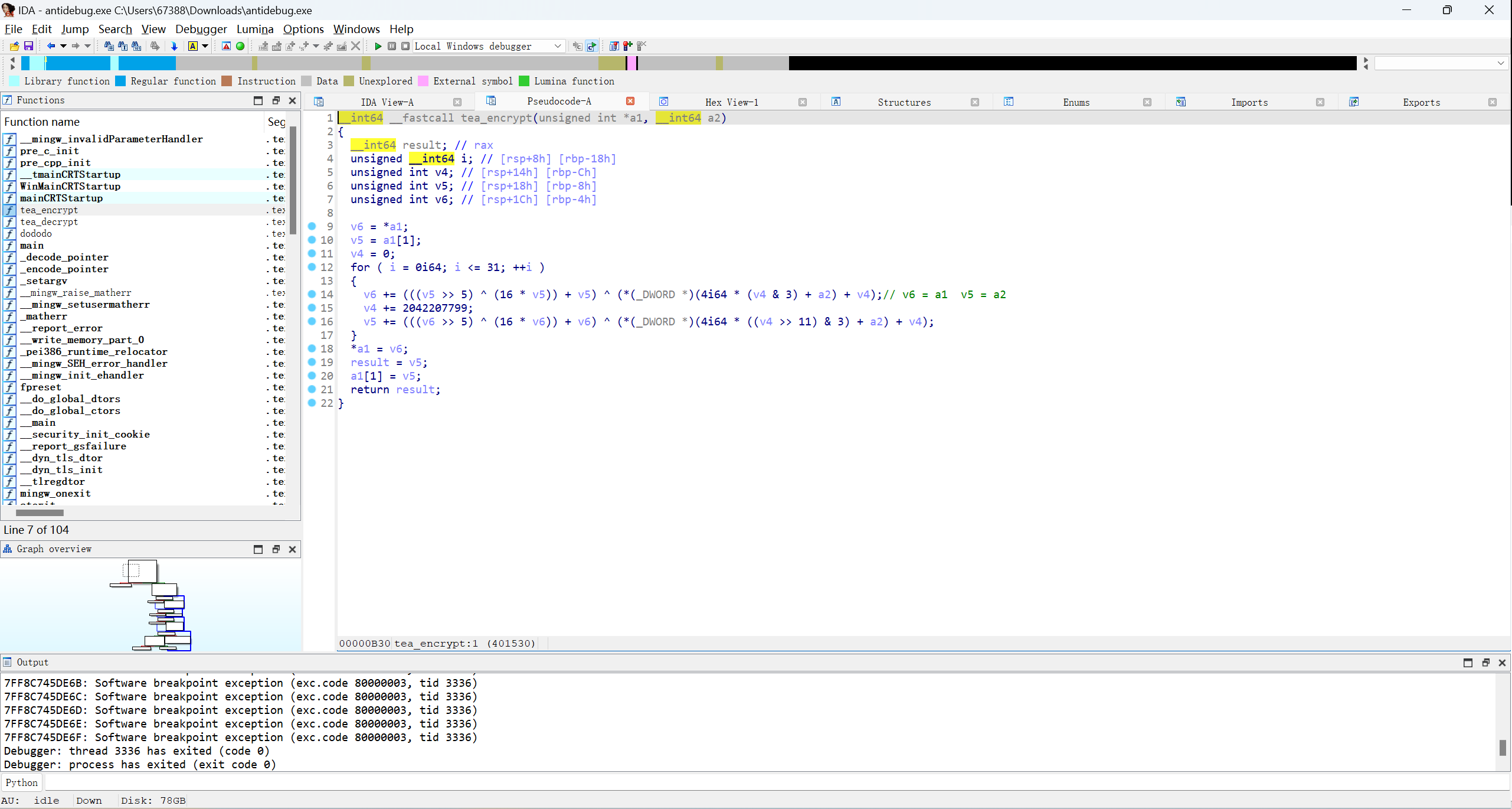
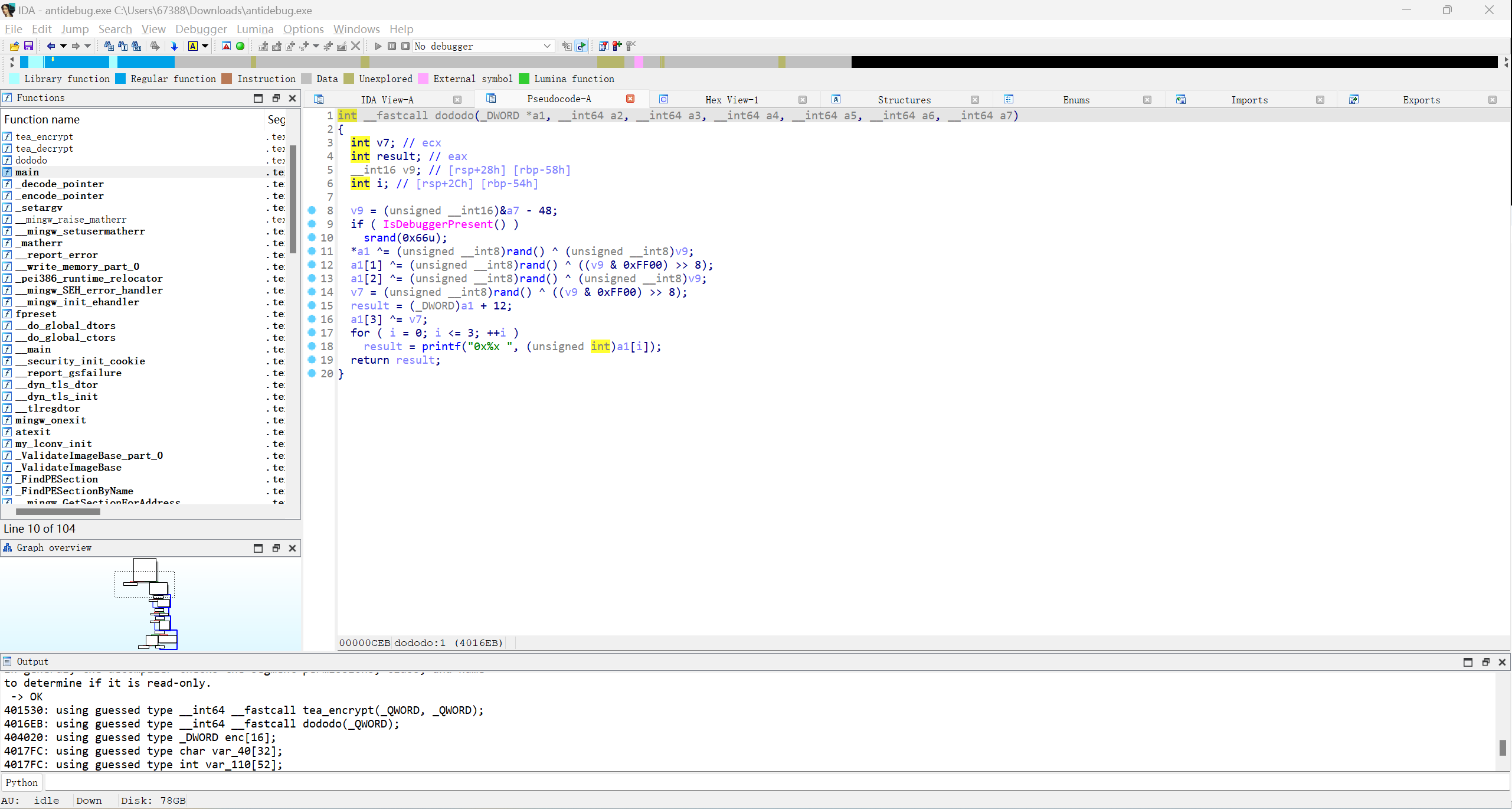
对v6进行了加密,因此无法直接获得enc和key的值,动态调试看看
在main函数处下断点,在第一个exit处f7,然后f8跳过
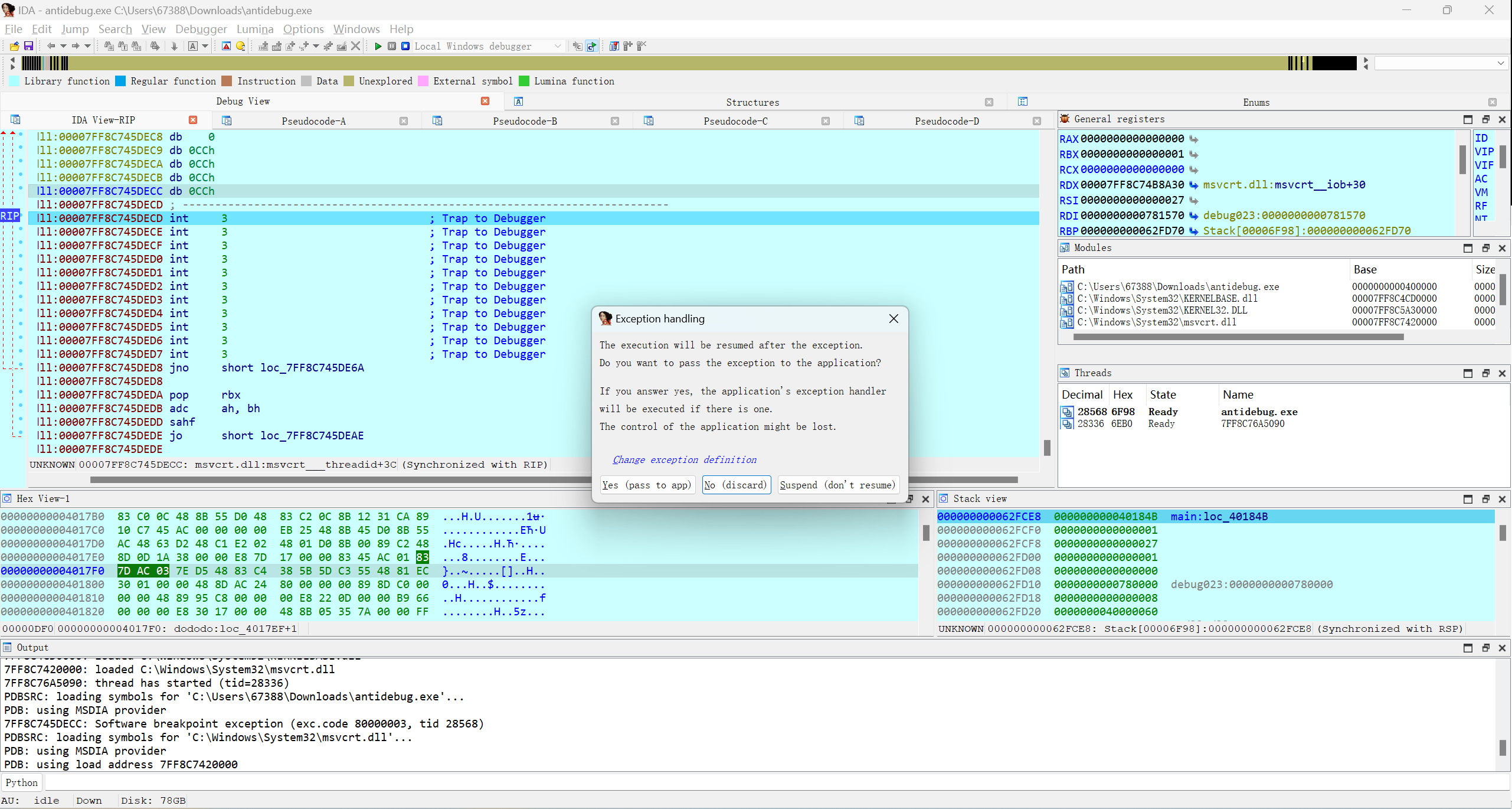
看到了key值
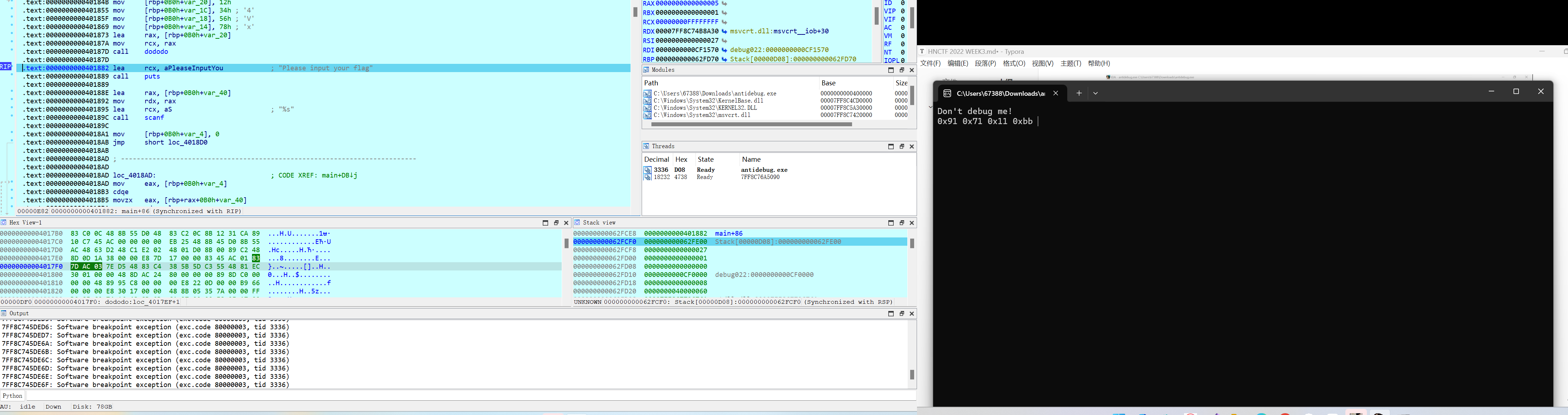

再看enc的值
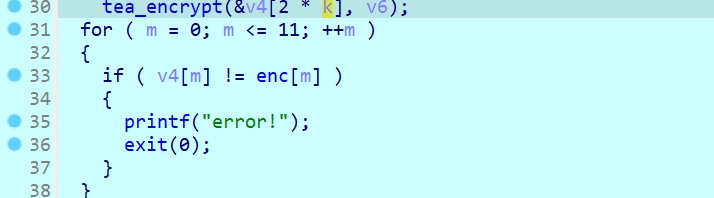
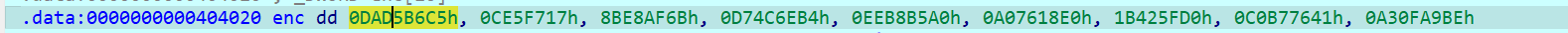
可以开始编写脚本了
#include <iostream>
#include <stdio.h>
#include <stdint.h>
using namespace std;
int main()
{
unsigned int enc[12] = { 0x0DAD5B6C5, 0x0CE5F717, 0x8BE8AF6B, 0x0D74C6EB4, 0x0EEB8B5A0, 0x0A07618E0, 0x1B425FD0, 0x0C0B77641, 0x0A30FA9BE,0x0CB4F5089, 0x0EBF9EC1D, 0x0F870EF3D, };
unsigned int key[4] = { 0x91 ,0x71 ,0x11 ,0xbb, };
unsigned int a1, a2;
for (int i = 0; i < 6; i++)
{
a1 = enc[2 * i];
a2 = enc[2 * i + 1];
long dt = 2042207799 * 32;
for (int j = 0; j < 32; ++j)
{
a2 -= (((a1 * 16) ^ (a1 >> 5)) + a1) ^ (dt + key[(dt >> 11) & 3]);
dt -= 2042207799;
a1 -= (((a2 * 16) ^ (a2 >> 5)) + a2) ^ (dt + key[(dt & 3)]);
}
enc[2 * i] = a1;
enc[2 * i + 1] = a2;
}
for (int i = 0; i <12; i++)
{
printf("%X\n", enc[i]);
}
}
//#_Ant!+Debu9
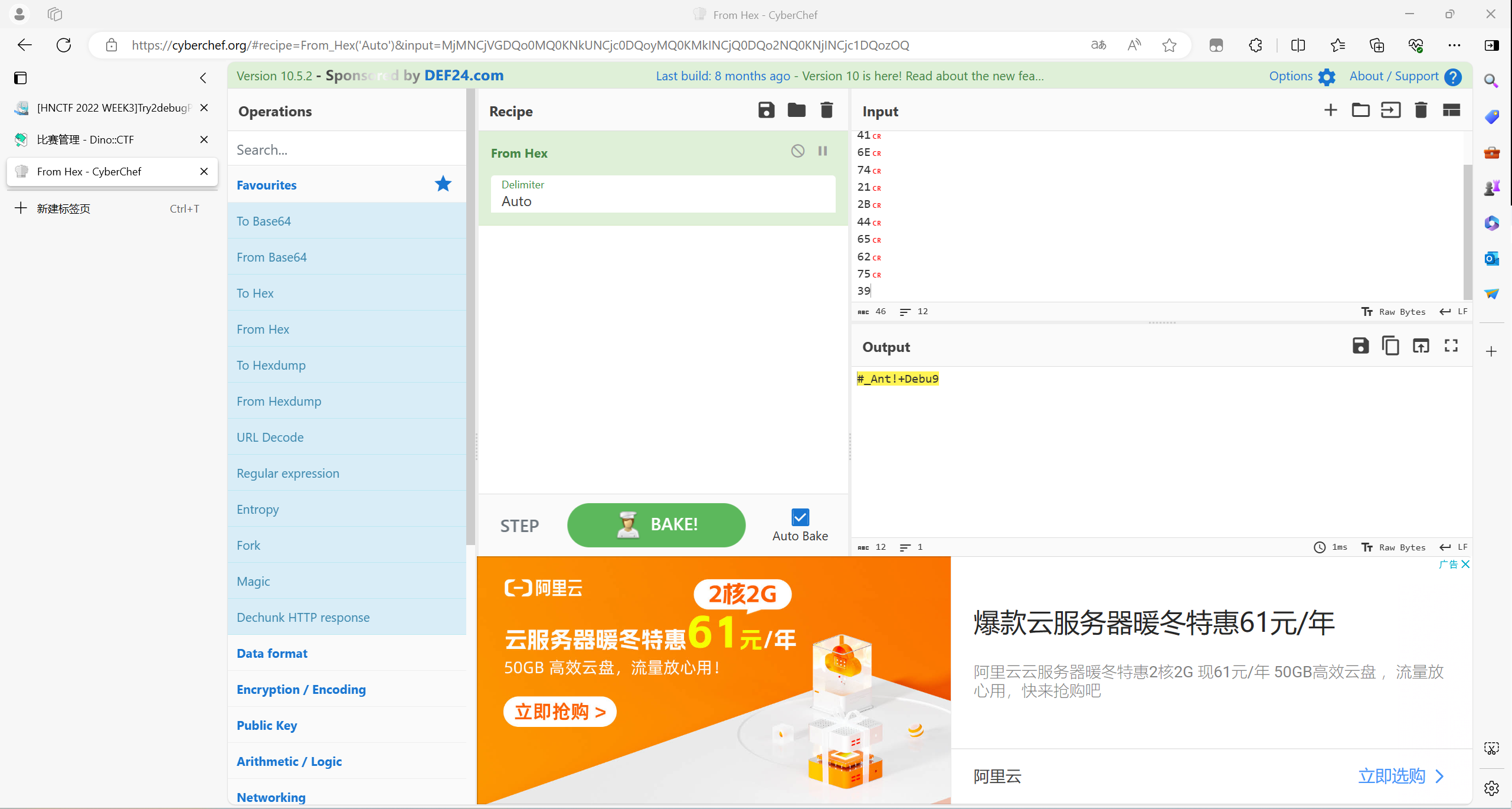
[HNCTF 2022 WEEK3]What's 1n DLL?
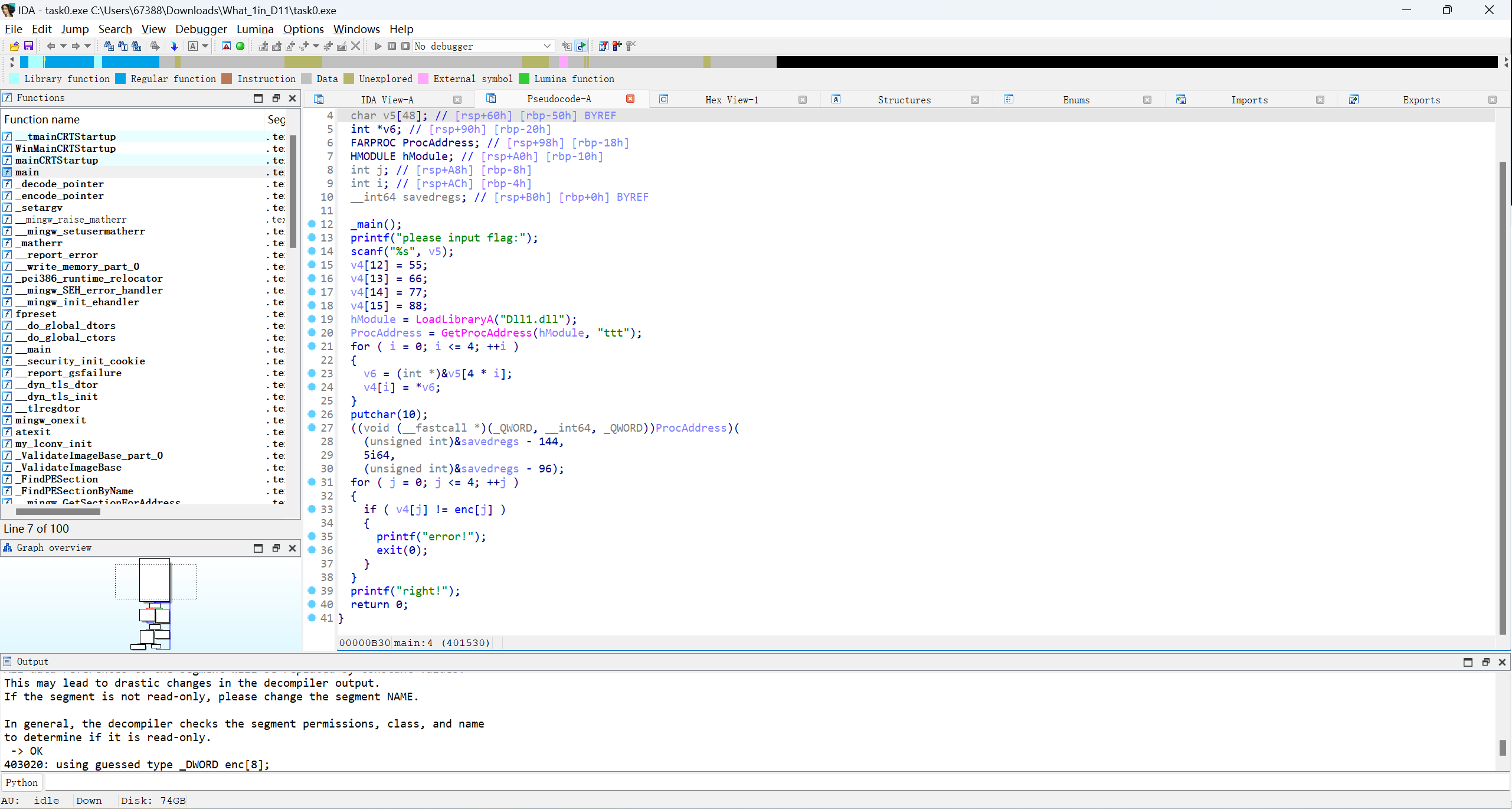
这里用 LoadLibrary 加载了Dll1.dll的动态链接库,之后用 GetProcAddress函数来获取加载Dll1.dll,来获取其中名为ttt的函数地址,之后将其保存在ProcAddress变量中。
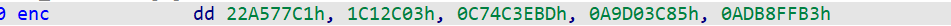
在这个exe文件里可以发现enc的值和key的值
接着分析dll文件
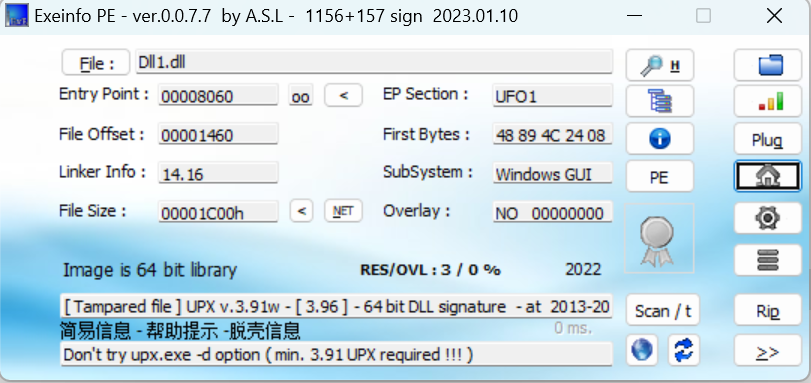
发现dll有upx壳,尝试自动脱壳
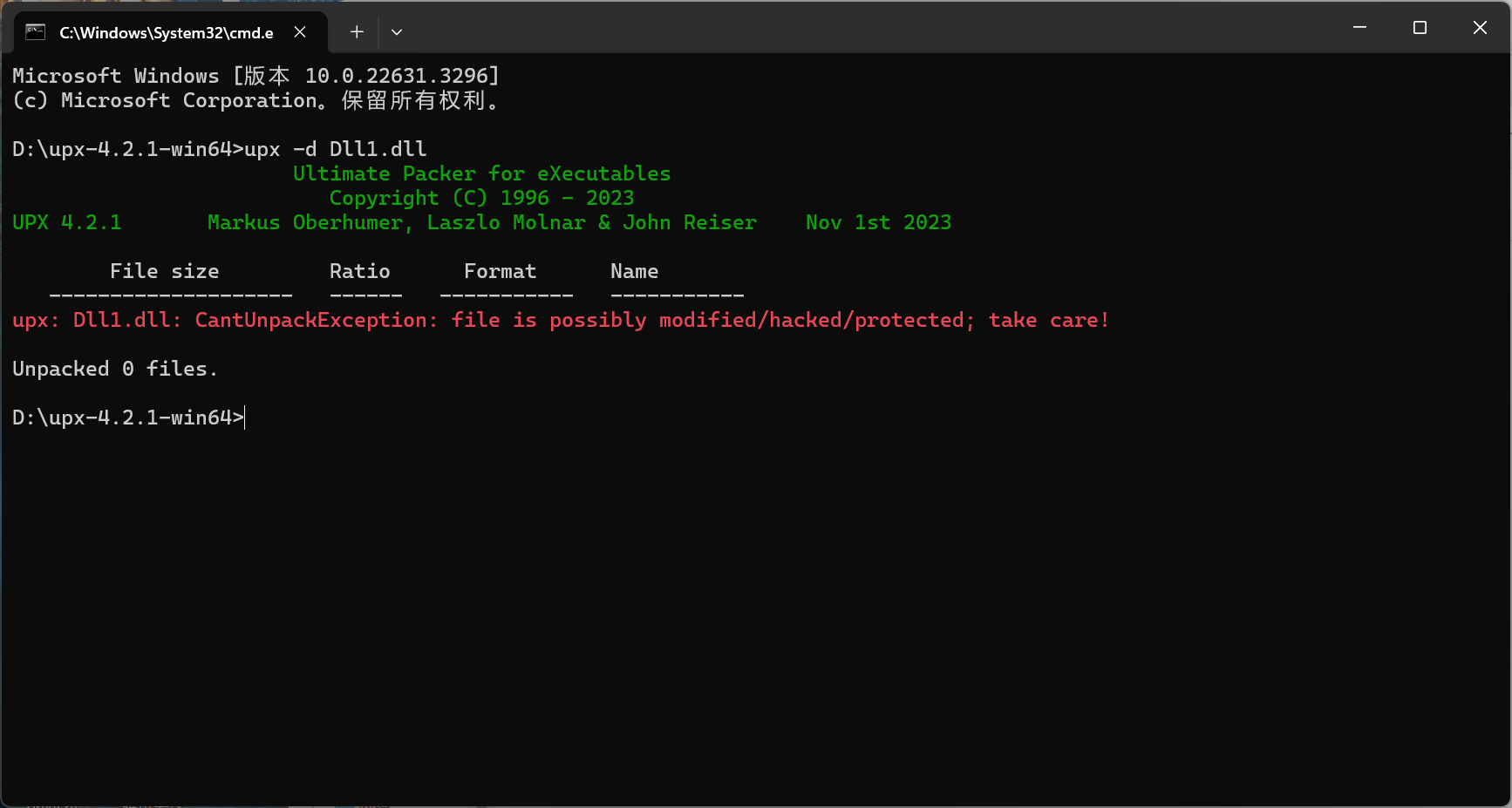
不可以自动脱壳,放进010中查看
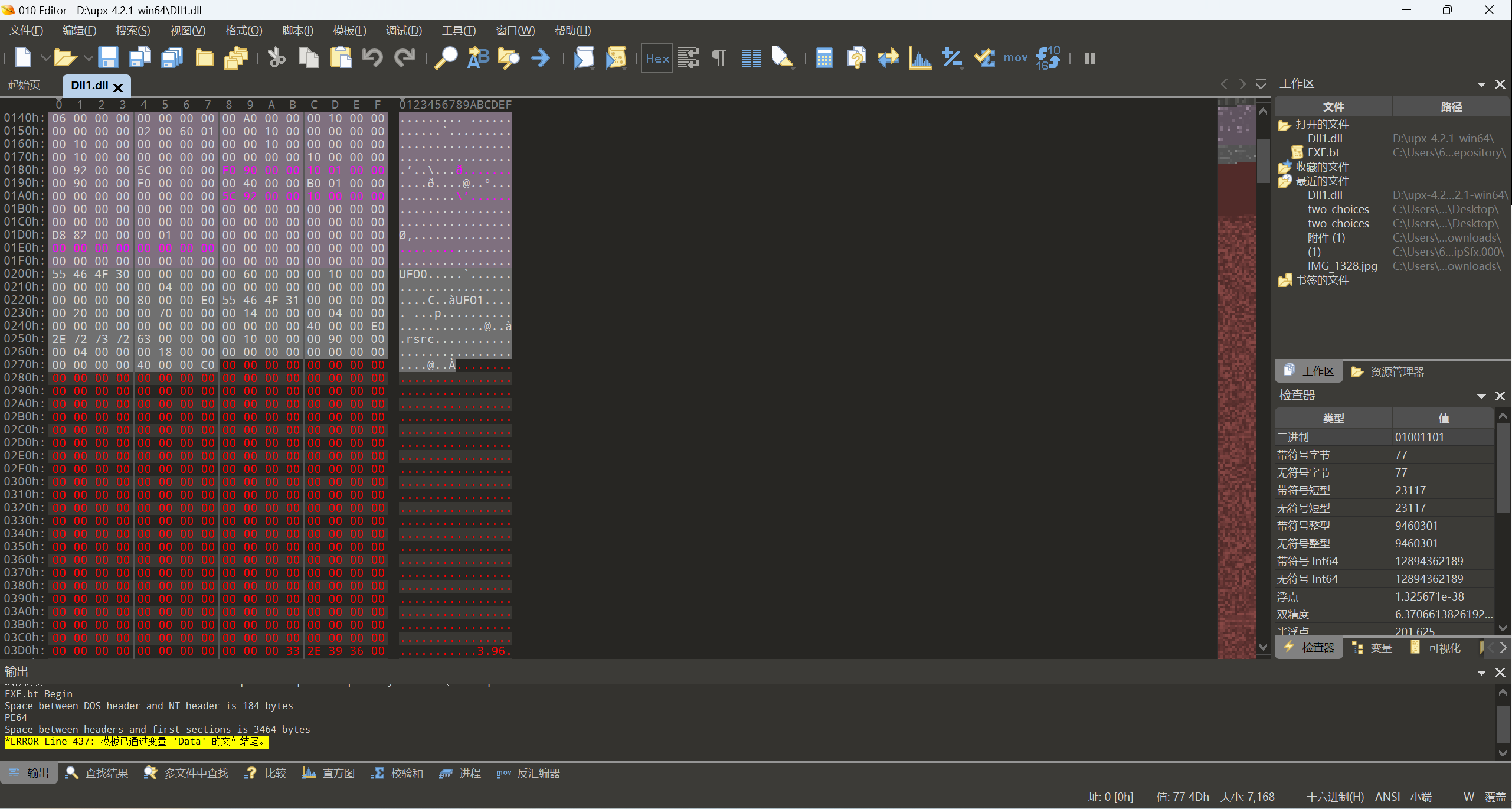
将此处的UFO改成UPX就可以了
再用IDA打开,找到ttt函数
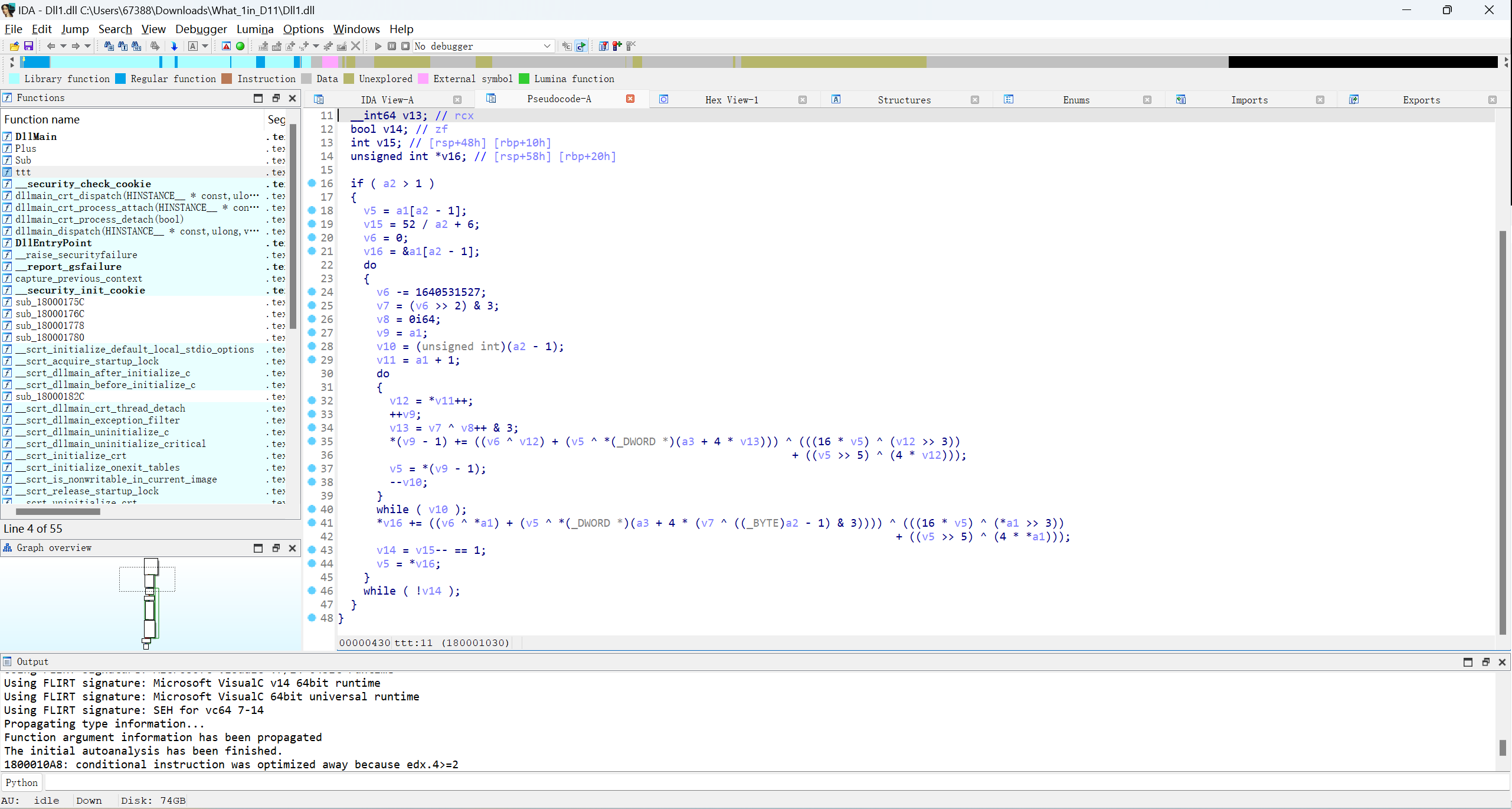
发现是一个XXTEA加密,编写脚本
#include <stdbool.h>
#include <stdio.h>
#define MX ((z >> 5 ^ y << 2) + (y >> 3 ^ z << 4) ^ (sum ^ y) + (k[p & 3 ^ e] ^ z))
bool xxtea(unsigned int* v, int n, unsigned int* k)
{
unsigned int z = v[n - 1], y = v[0], sum = 0, e, DELTA = 0x9e3779b9;
unsigned int p, q;
n = -n;
q = 6 + 52 / n;
sum = q * DELTA;
while (sum != 0)
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
z = v[p - 1], y = v[p] -= MX;
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
}
return 1;
}
int main(int argc, char const* argv[])
{
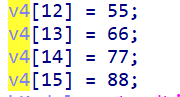
unsigned int v[5] = { 0x22a577c1,0x1c12c03,0xc74c3ebd,0xa9d03c85,0xadb8ffb3 };
unsigned int key[4] = { 55,66,77,88 };
int n = 5;
xxtea(v, -n, key);
char* p = (char*)v;
for (int i = 0; i < 20; i++)
{
printf("%c", *p);
p++;
}
return 0;
}
//NSSCTF{He110_w0r1d!}
[HNCTF 2022 WEEK3]Help_Me!
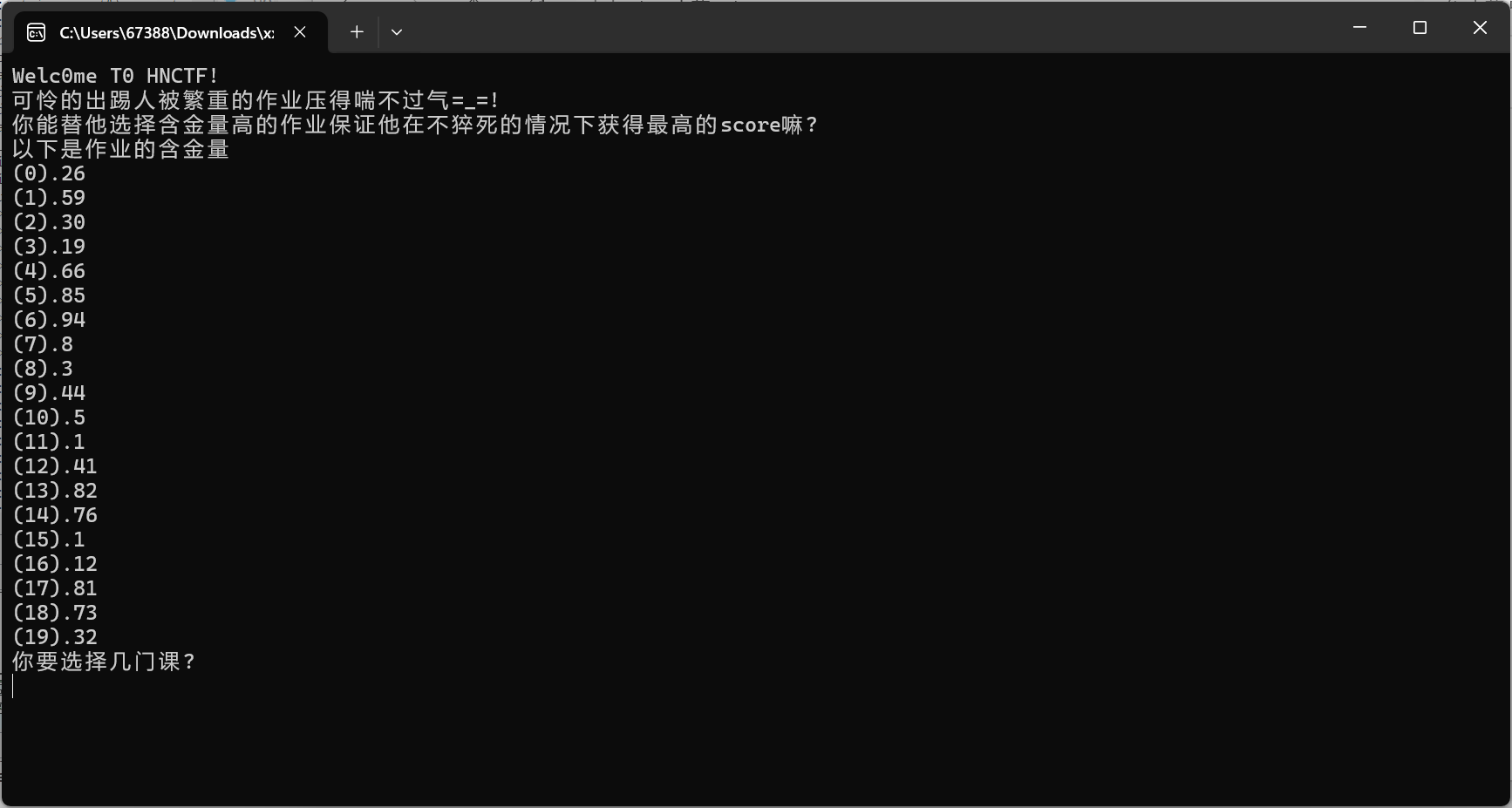
查阅资料发现是一个动态规划问题,背包问题
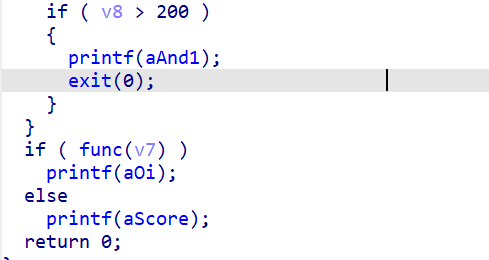
如果超过200,就会直接嗝屁,点进func函数里看看
查看背包问题相关文章后写出脚本
values = [26,59,30,19,66,85,94,8,3,44,5,1,41,82,76,1,12,81,73,32,0]
weights = [71,34,82,23,1,88,12,57,10,68,5,33,37,69,98,24,26,83,16,26,0]
capacity = 200
def package(weights, values, capacity):
n = len(weights)
dp = [[0] * (capacity + 1) for _ in range(n + 1)]
for i in range(1, n + 1):
for w in range(capacity + 1):
if weights[i - 1] <= w:
dp[i][w] = max(dp[i - 1][w], dp[i - 1][w - weights[i - 1]] + values[i - 1])
else:
dp[i][w] = dp[i - 1][w]
nunbers = []
i, w = n, capacity
while i > 0 and w > 0:
if dp[i][w] != dp[i - 1][w]:
nunbers.append(i - 1)
w -= weights[i - 1]
i -= 1
return dp[n][capacity], nunbers
max_value, nunbers = package(weights, values, capacity)
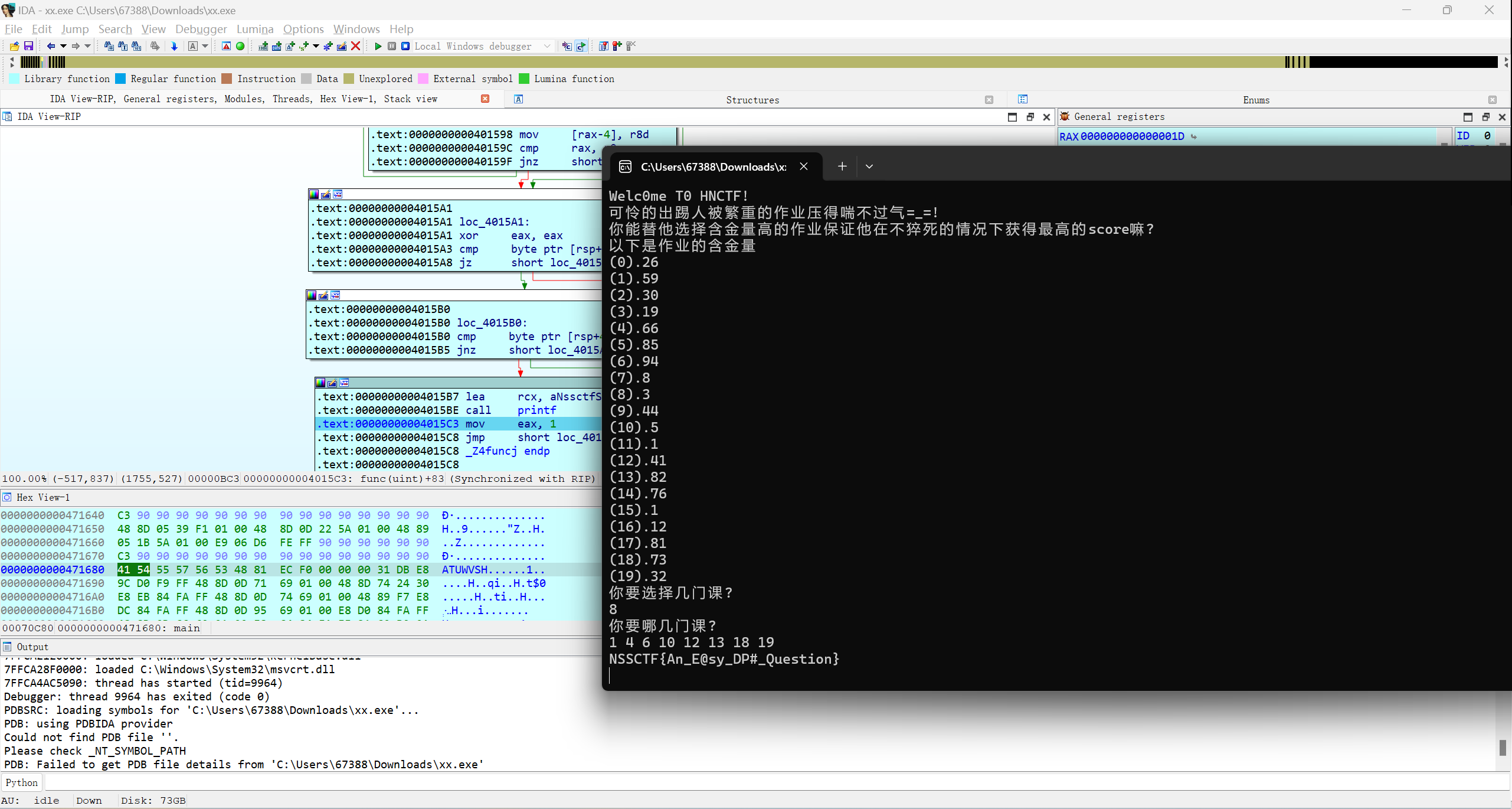
print("最大含金量:", max_value)
print("作业编号:", nunbers[::-1])
# 最大含金量: 452
# 作业编号: [1, 4, 6, 10, 12, 13, 18, 19]
输入进去后发现它直接退出来了,所以我们下断点,动调
[HNCTF 2022 WEEK3]CM2
下载下来以后是一个安装包
我们直接安装一手
先查看exe文件
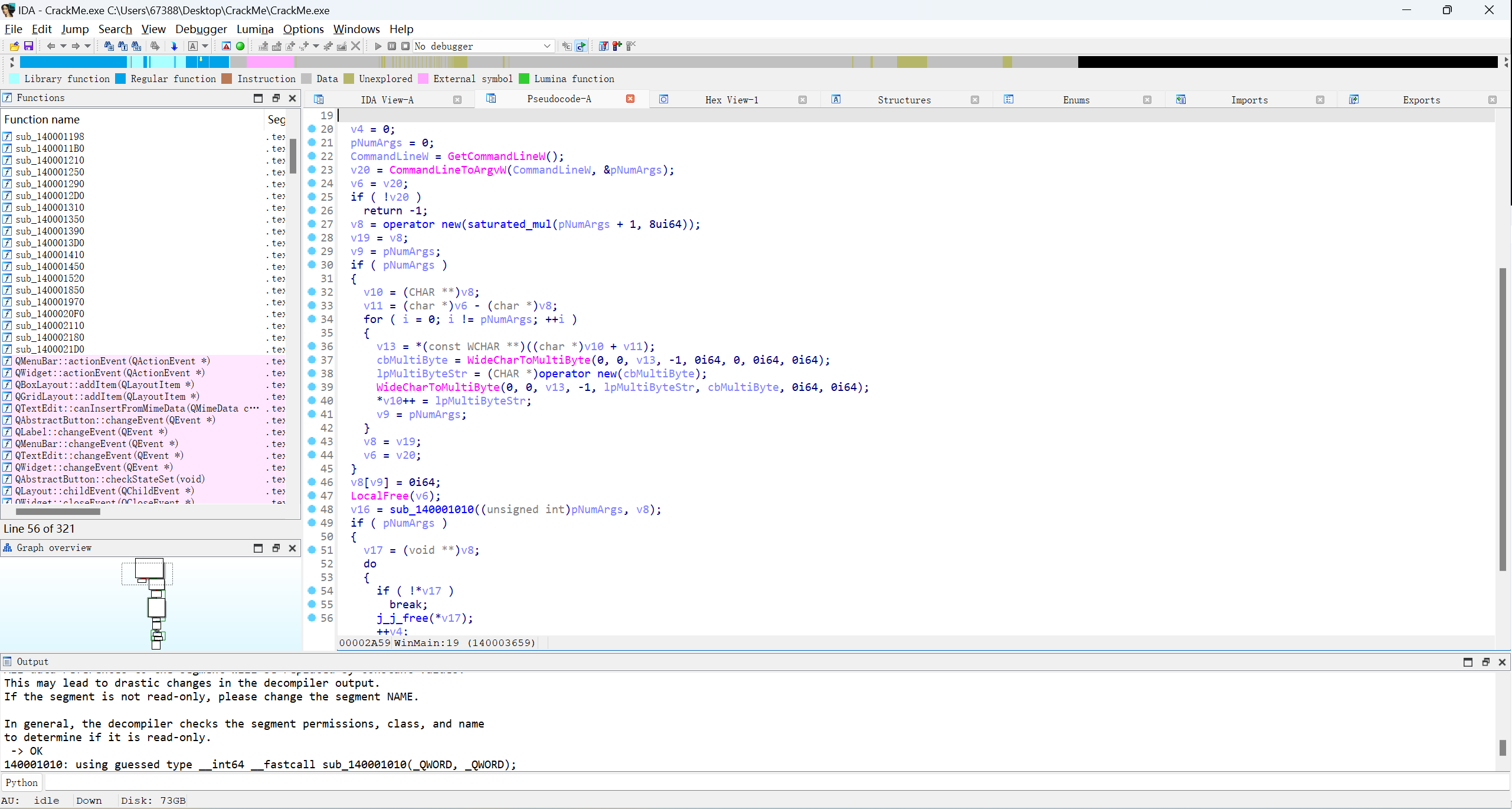
在String里看到了admin
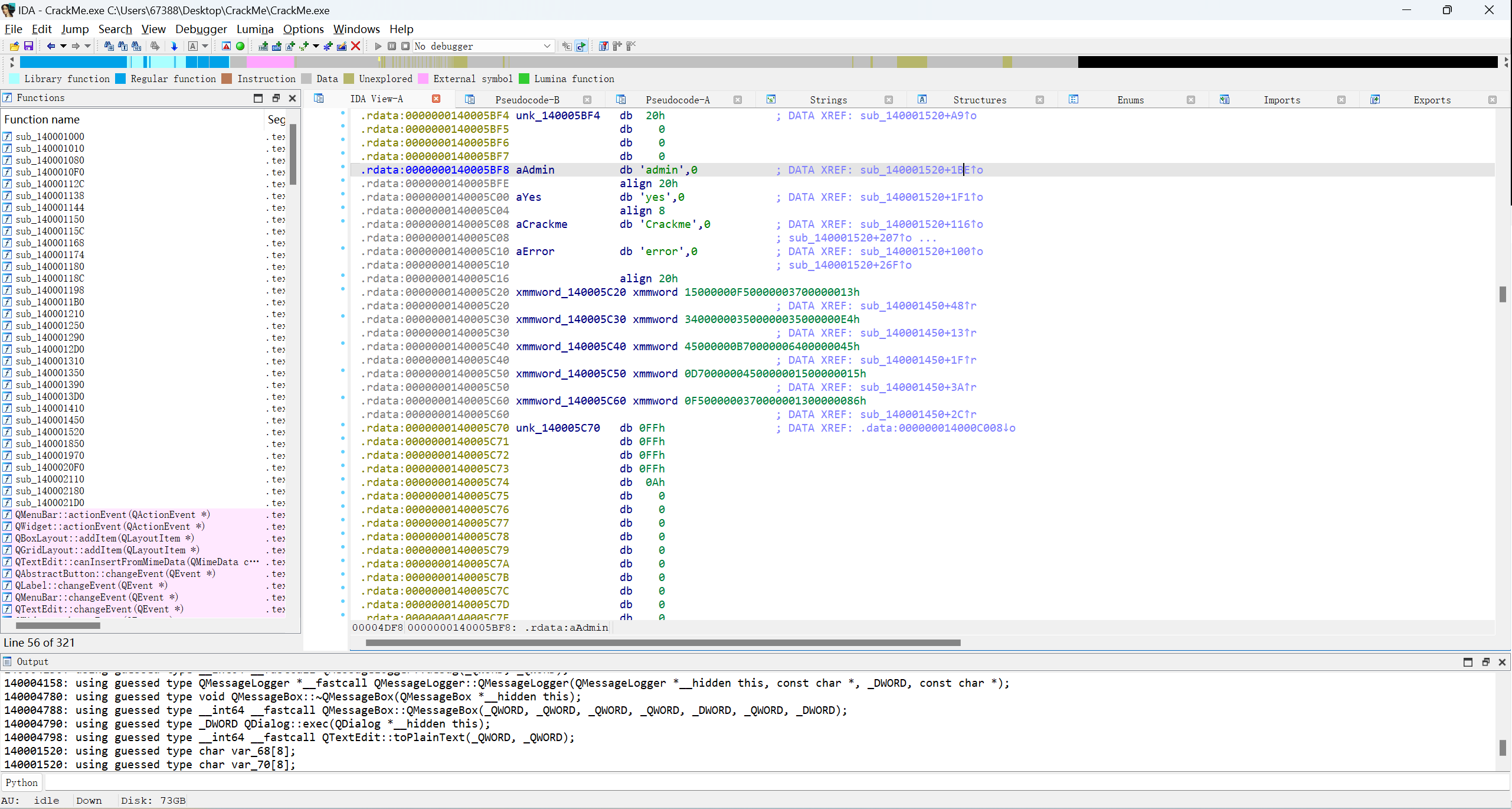
发现用户名为admin,再来找找flag,直接查看admin的那段函数
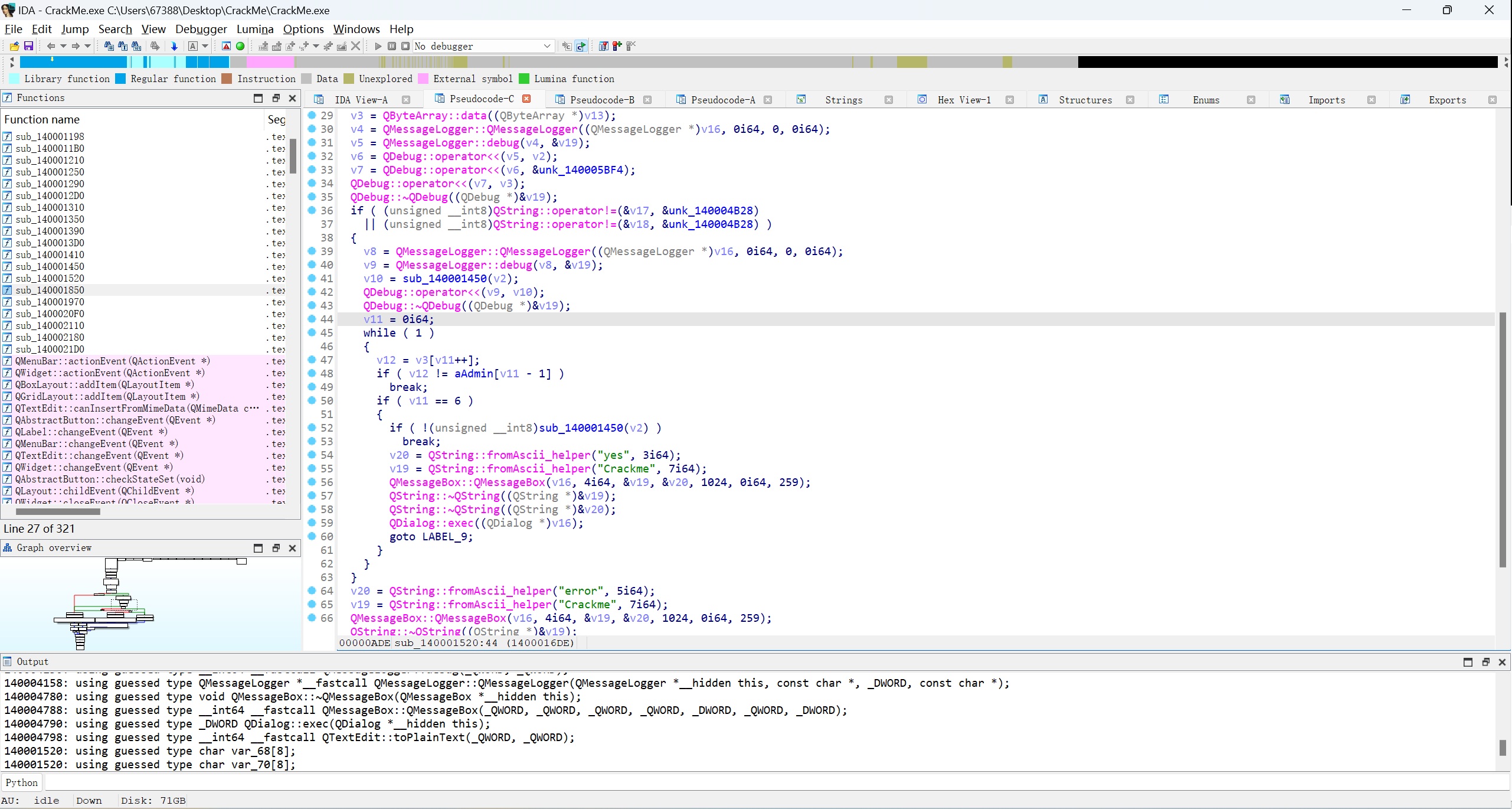
发现关键函数sub_140001450,点进去查看
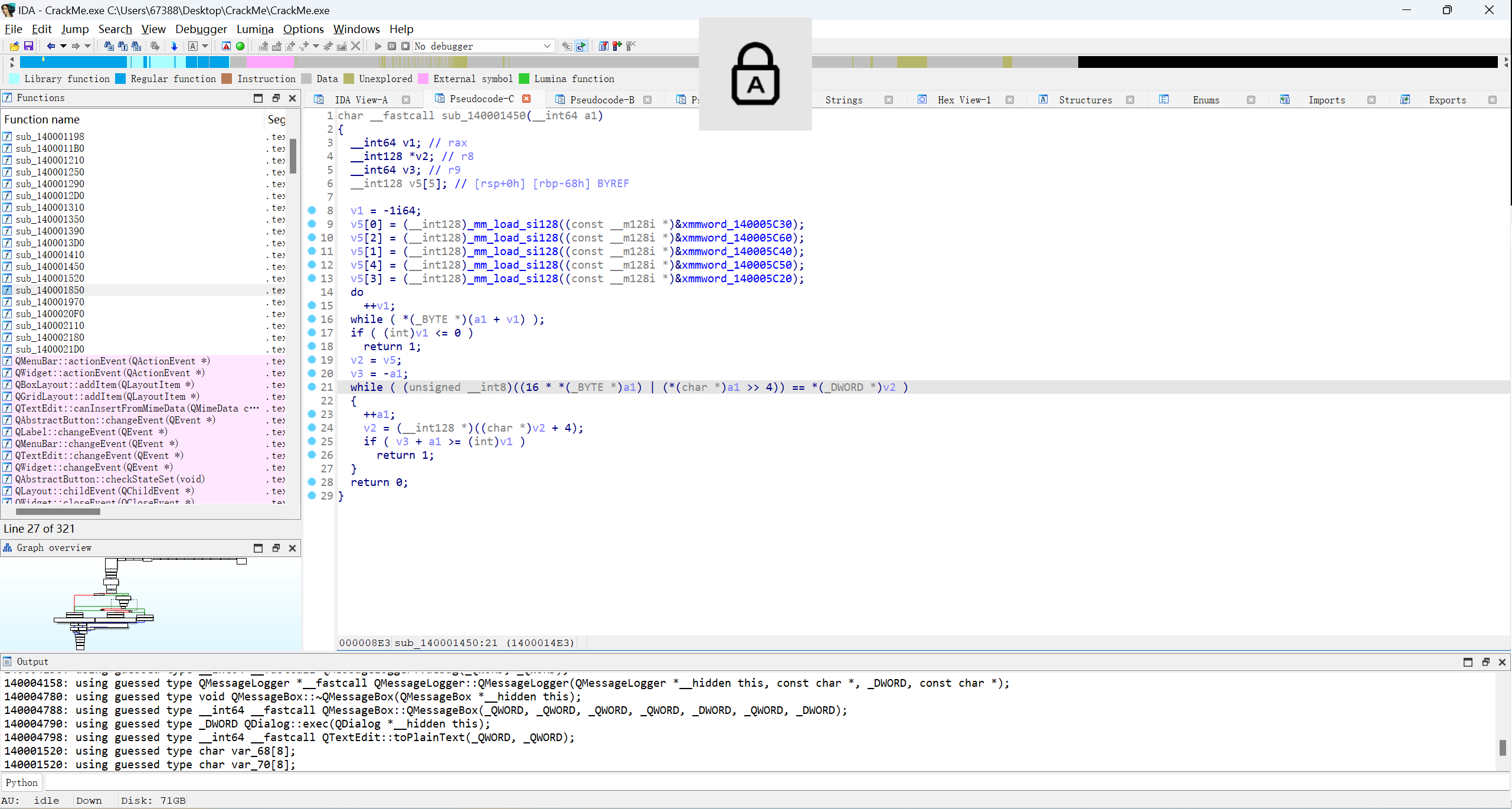
发现只有一段加密,动调看v5
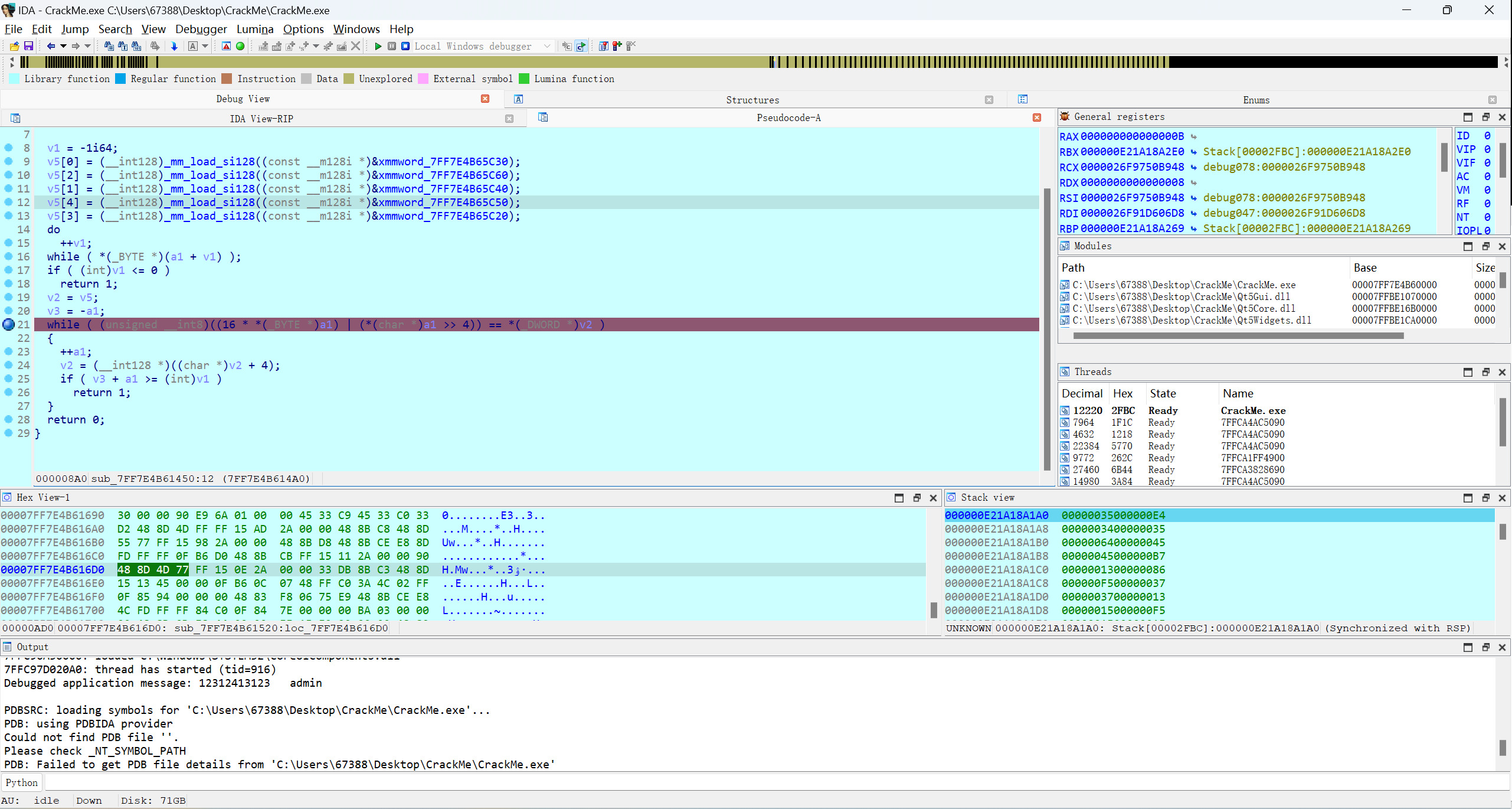
由于__int128是(128/8)=16,16*5个v5为80,DWORD为4字节,所以一共有20个数组
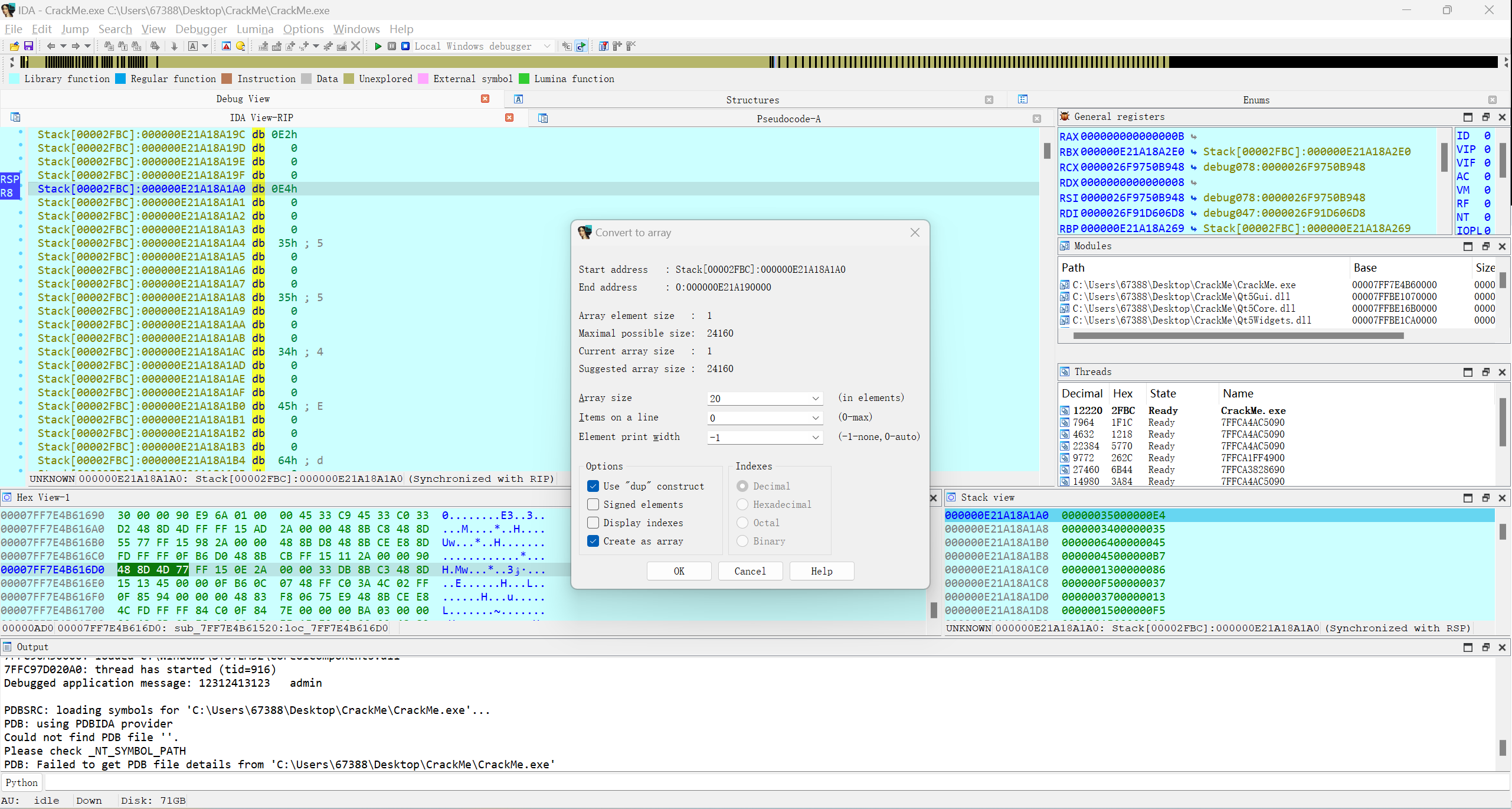
先转换成ddshift+8 ,Array size为20
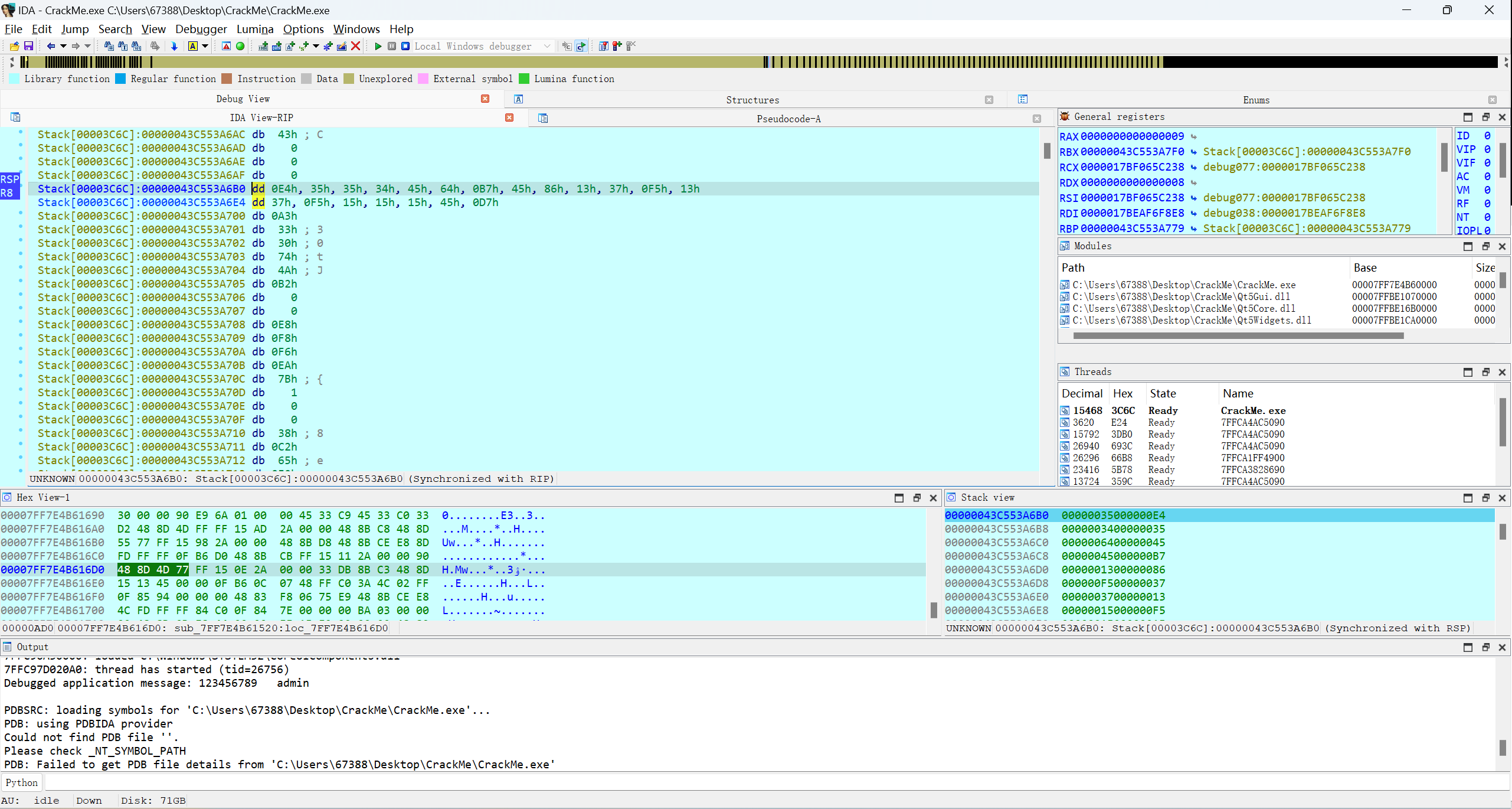
然后convert为DWORD
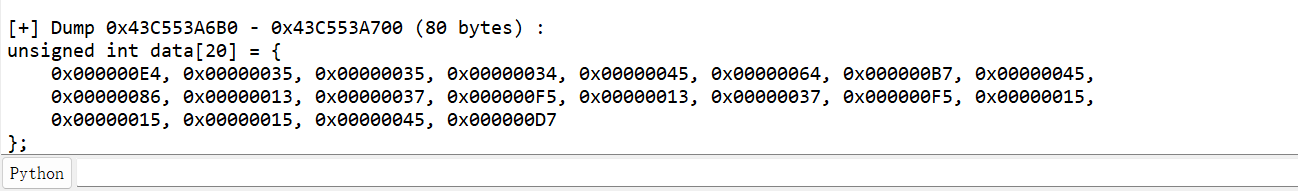
开始编写脚本
data = [0x000000E4, 0x00000035, 0x00000035, 0x00000034, 0x00000045, 0x00000064, 0x000000B7, 0x00000045, 0x00000086, 0x00000013, 0x00000037, 0x000000F5, 0x00000013, 0x00000037, 0x000000F5, 0x00000015, 0x00000015, 0x00000015, 0x00000045, 0x000000D7]
for i in range(0,len(data),4):
for j in range(i,i+4):
t1=bin(data[j])[2:].zfill(8)
t2=int(t1[4:]+t1[:4],2)
print(chr(t2),end='')
#NSSCTF{Th1s_1s_QQQT}



【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步