NewStarCTF(Reserve) WEEK1
easy_RE
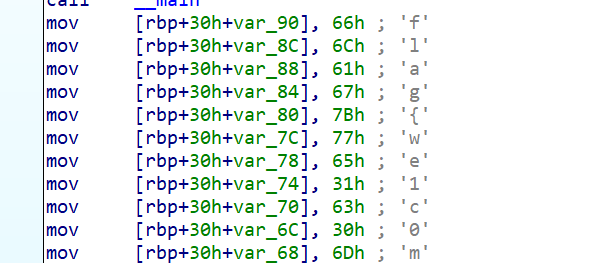
咳
有UPX壳,先脱壳
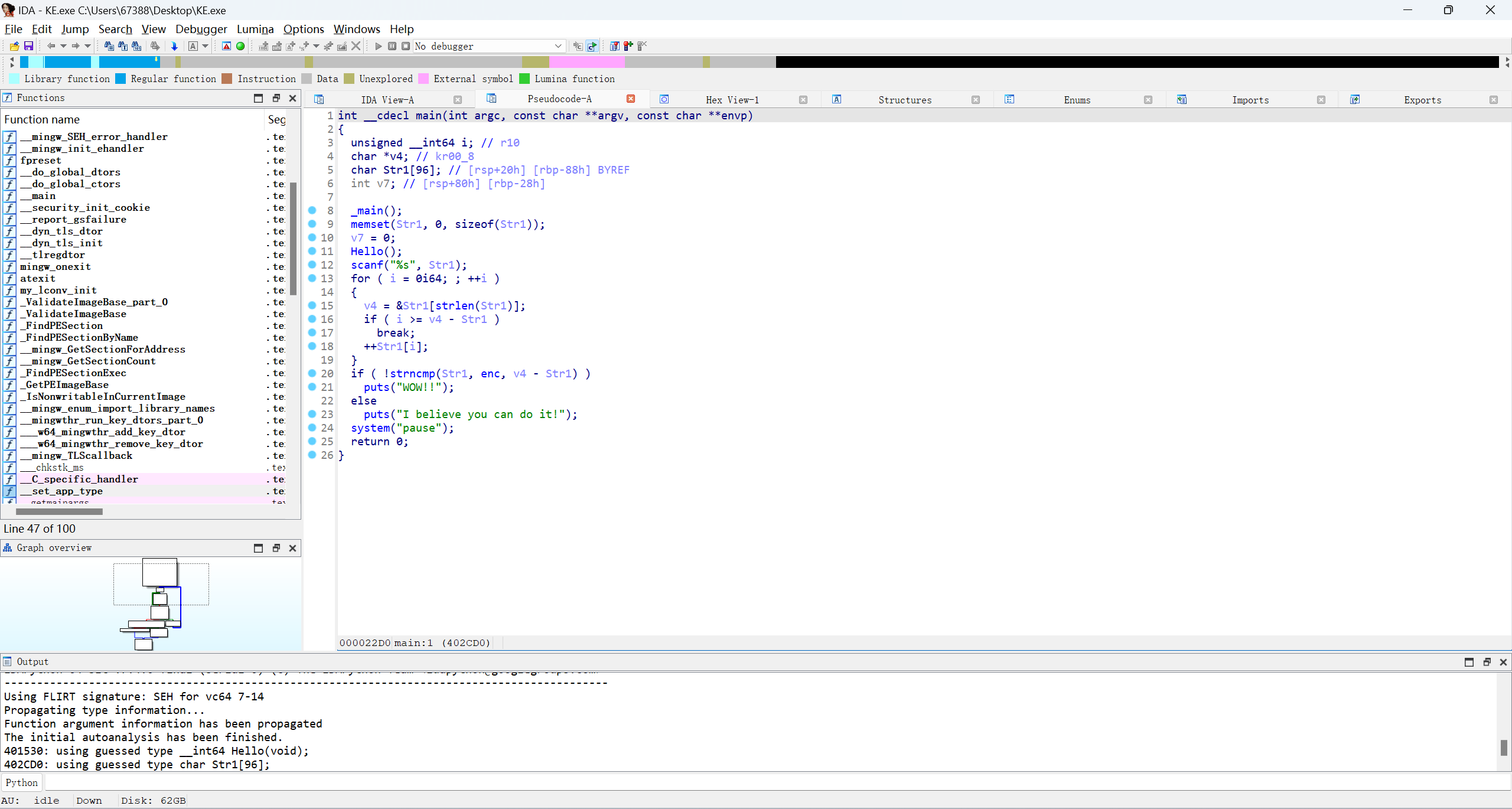
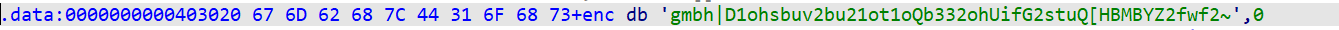
enc = "gmbh|D1ohsbuv2bu21ot1oQb332ohUifG2stuQ[HBMBYZ2fwf2~"
flag = ''
for i in enc:
b = (ord(i)-1)
flag += chr(b)
print(flag)
#flag{C0ngratu1at10ns0nPa221ngTheF1rstPZGALAXY1eve1}
Segments
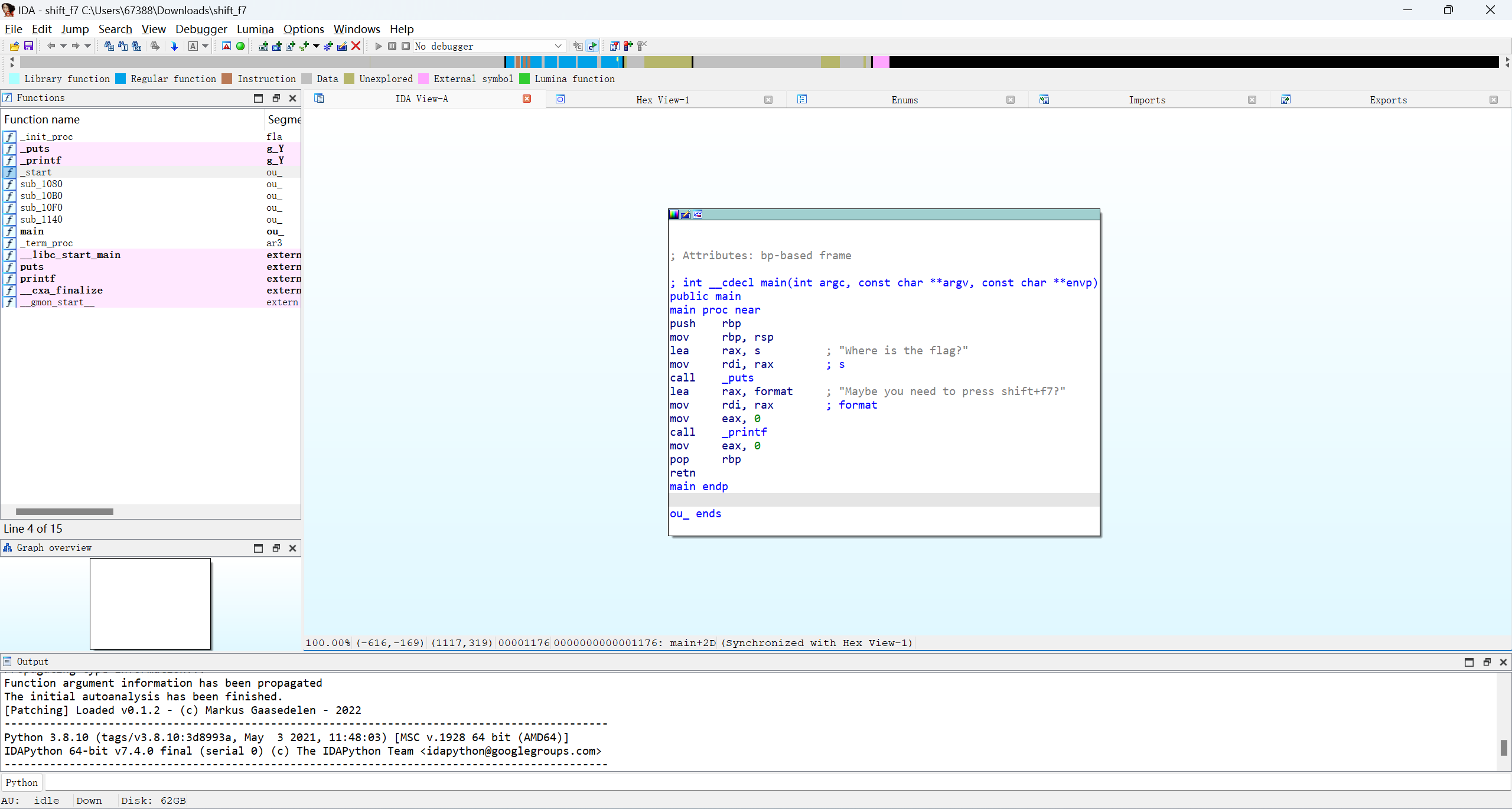
segments用shift+f7调出
ELF
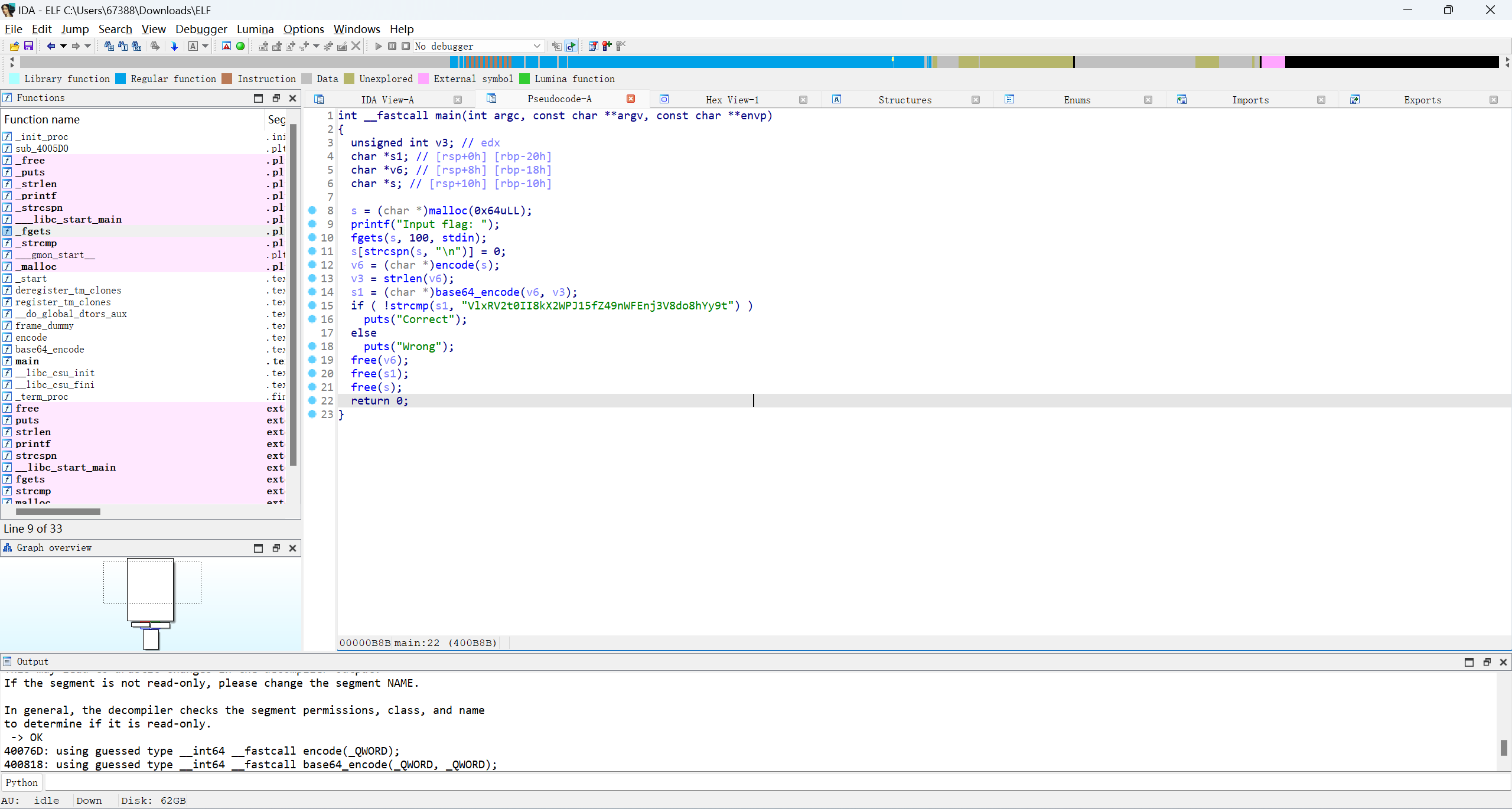
一个encode加密
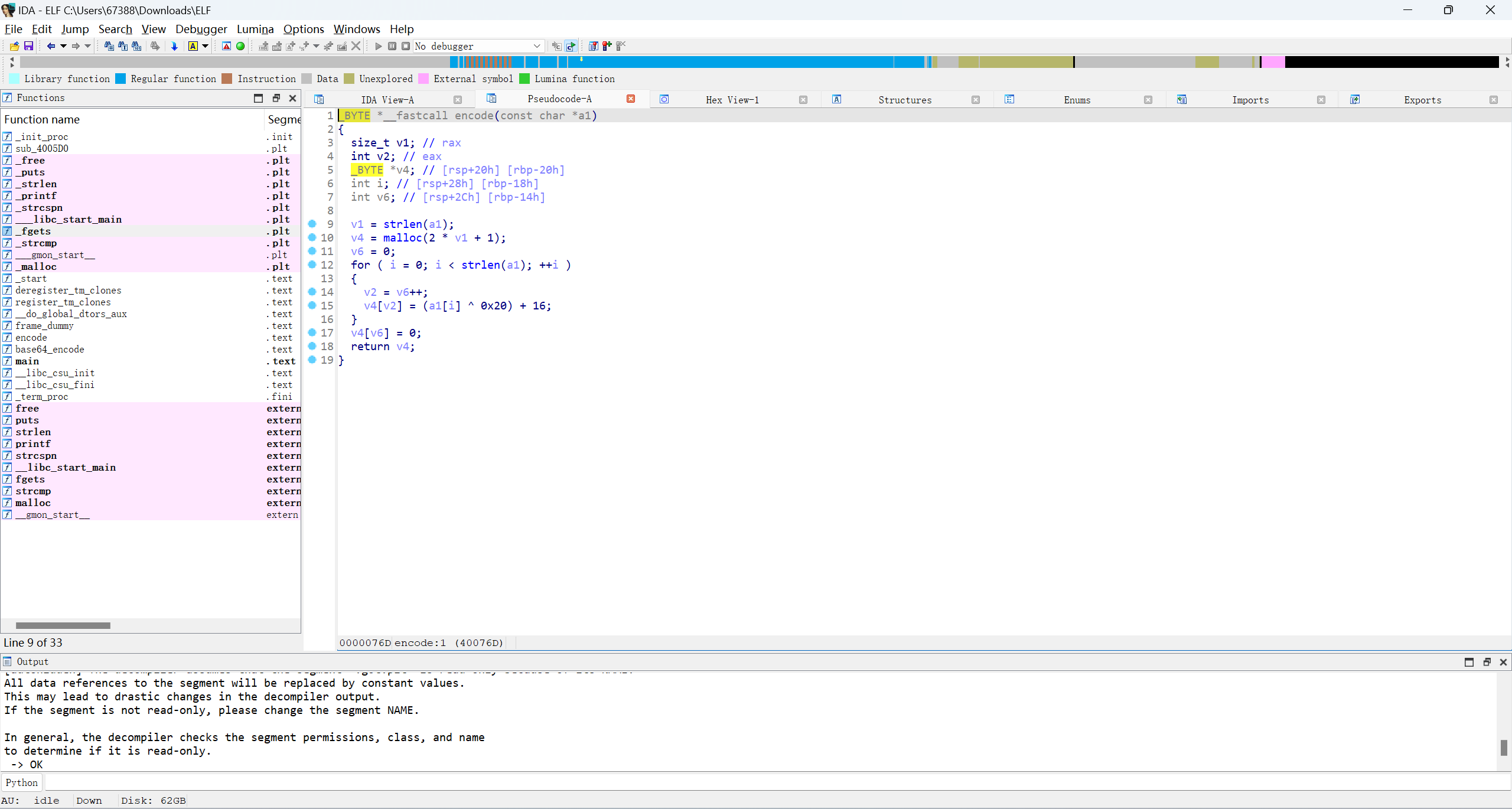
一个base64加密
先base64解密,再写encode解密
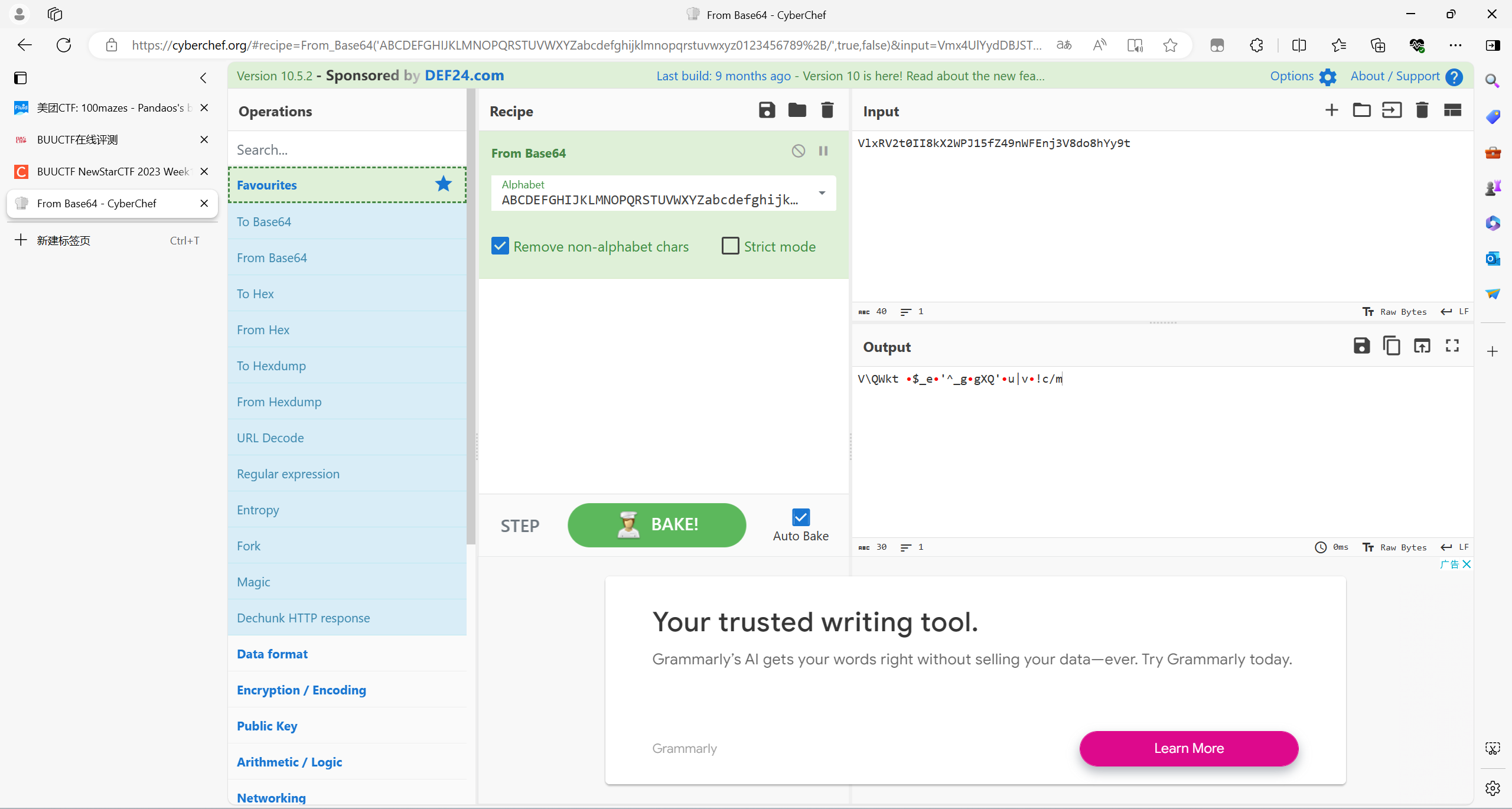
CyberChef解出来不对,用python脚本去解
import base64
encoded_str = "VlxRV2t0II8kX2WPJ15fZ49nWFEnj3V8do8hYy9t"
decoded_bytes = base64.b64decode(encoded_str)
print(decoded_bytes)
#V\\QWkt \x8f$_e\x8f'^_g\x8fgXQ'\x8fu|v\x8f!c/m
enc = "V\\QWkt \x8f$_e\x8f'^_g\x8fgXQ'\x8fu|v\x8f!c/m"
flag = ''
for i in enc:
b = (ord(i)-16)^0x20
flag += chr(b)
print(flag)
# flag{D0_4ou_7now_wha7_ELF_1s?}
Endian
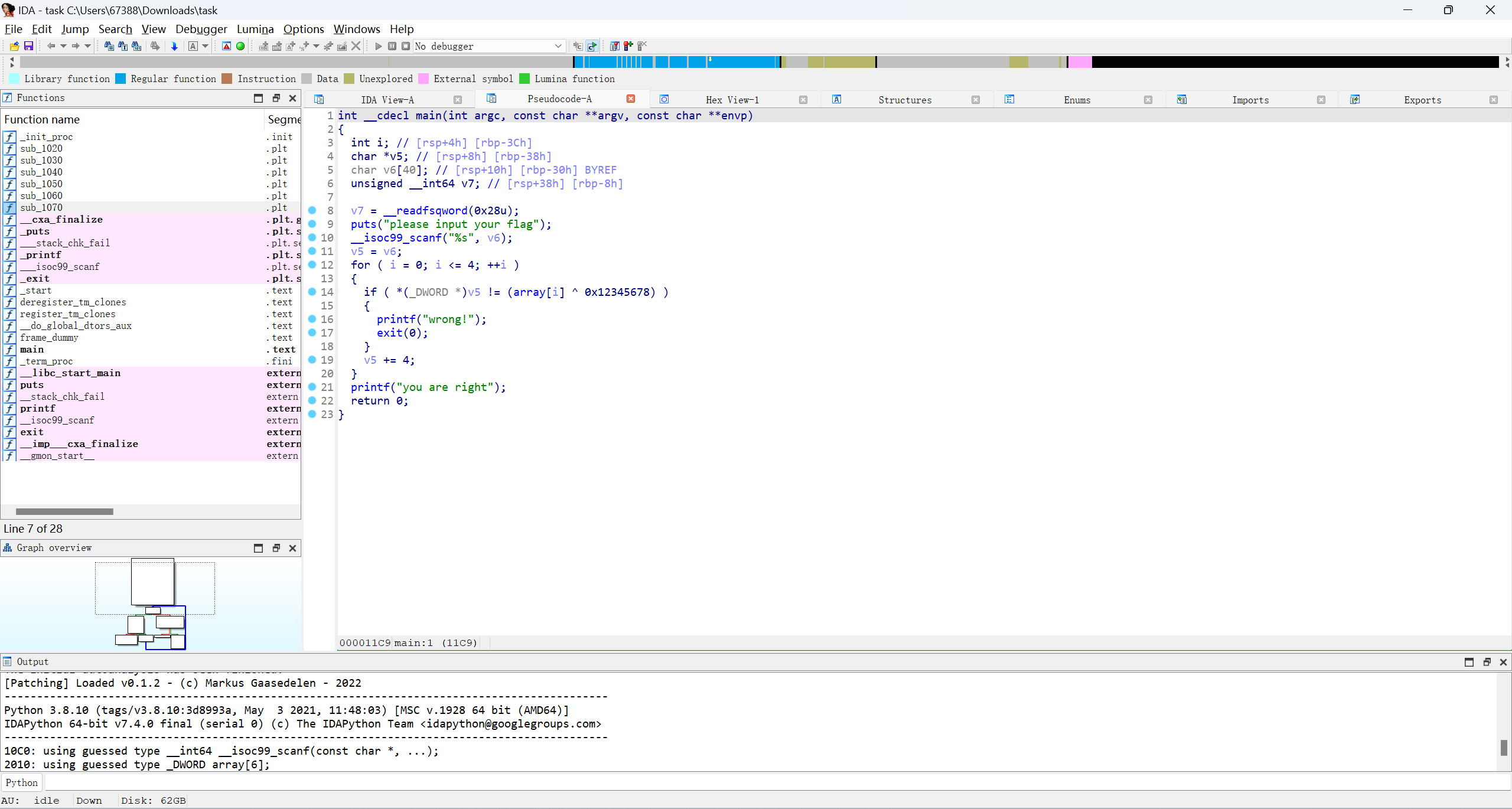

编写脚本
enc = [0x75553A1E, 0x7B583A03, 0x4D58220C, 0x7B50383D, 0x736B3819]
flag = ""
for i in range(0,5):
flag += (enc[i]^0x12345678).to_bytes(4, 'little').decode('utf-8')
print(flag)
# flag{llittl_Endian_a}
AndroXor
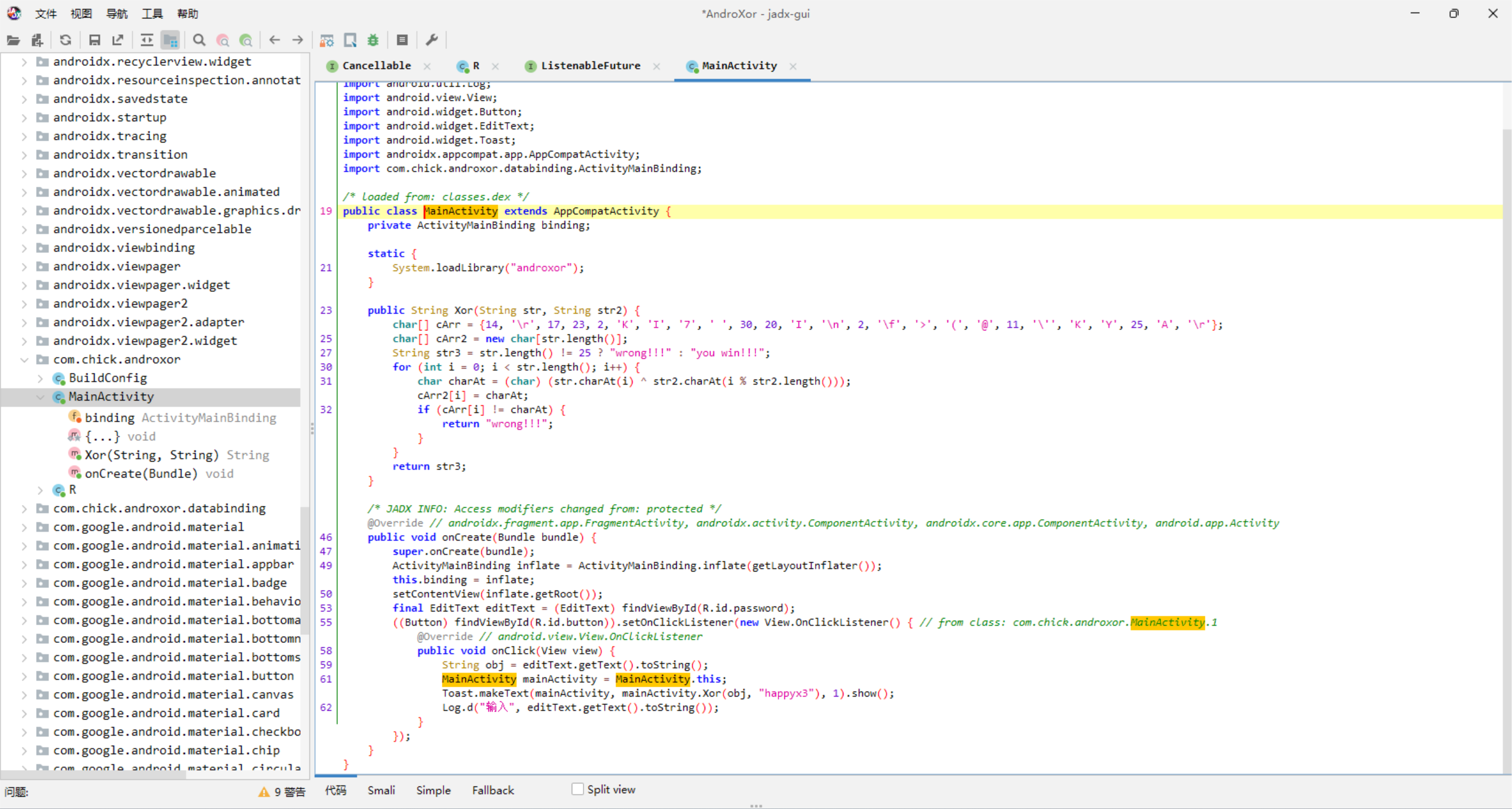
编写脚本
enc = [14,ord('\r'),17,23,2,ord('K'),ord('I'),ord('7'),ord(' '),30,20,ord('I'),ord('\n'),2,ord('\f'),ord('>'),ord('('),ord('@'),11,ord('\''),ord('K'),ord('Y'),25,ord('A'),ord('\r')]
key = 'happyx3'
flag = []
for i in range(len(enc)):
ans = chr(enc[i] ^ ord(key[i % len(key)]))
flag += ans
print("".join(flag))
# flag{3z_And0r1d_X0r_x1x1}
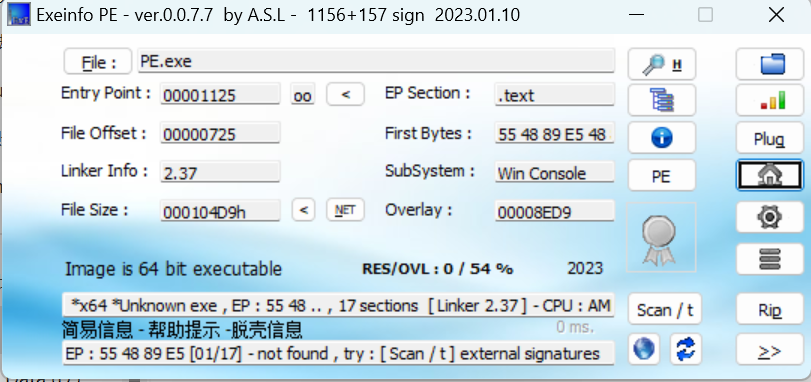
EzPE
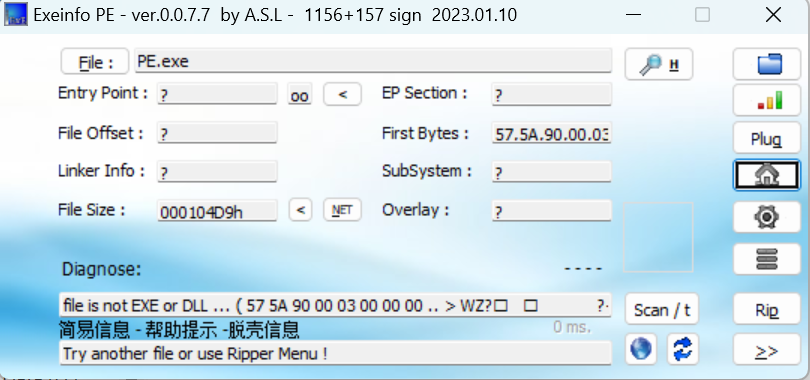
pe文件损坏了
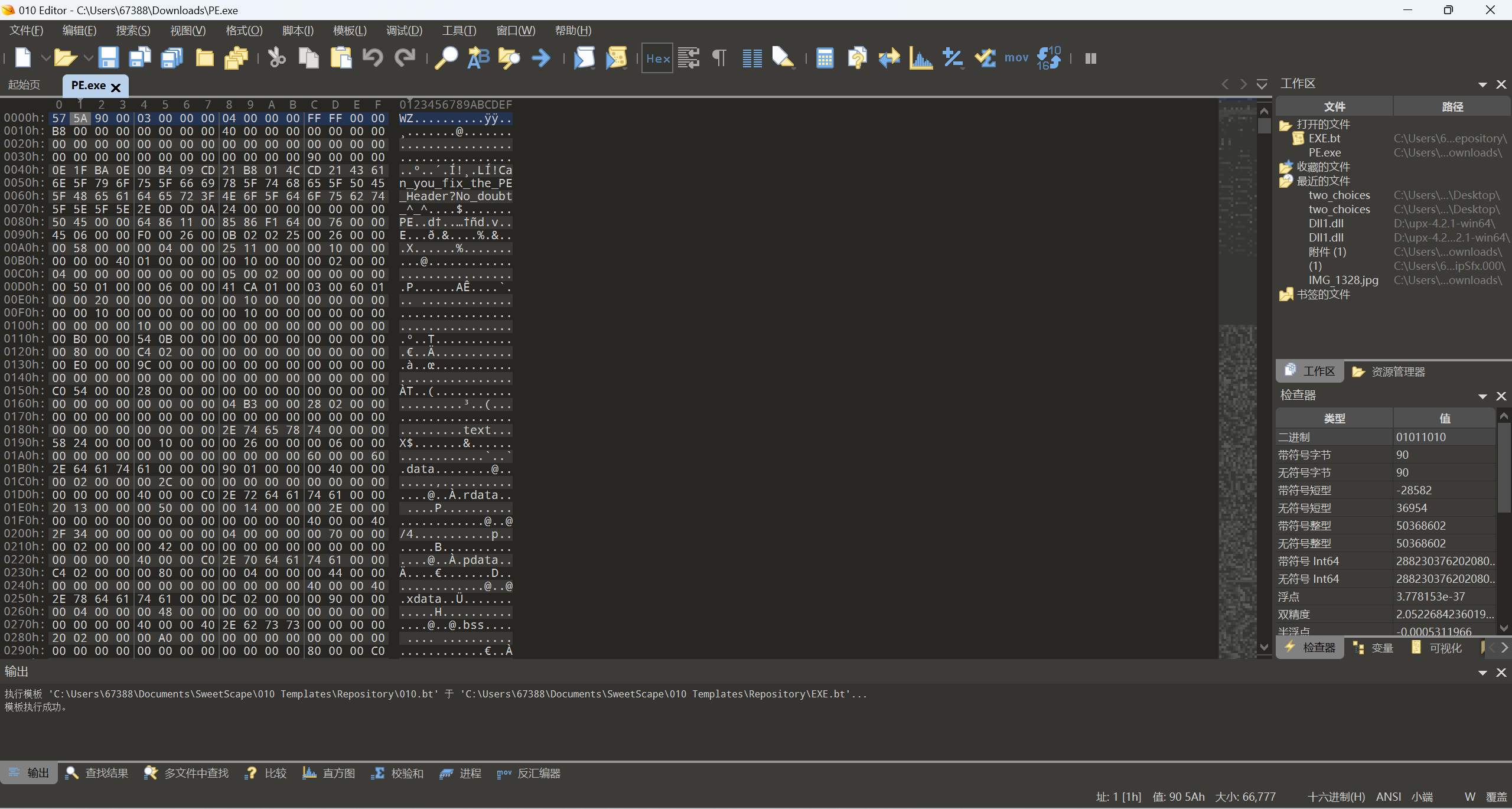
WZ改成MZ,80改成90,文件偏移要指向PE起始处
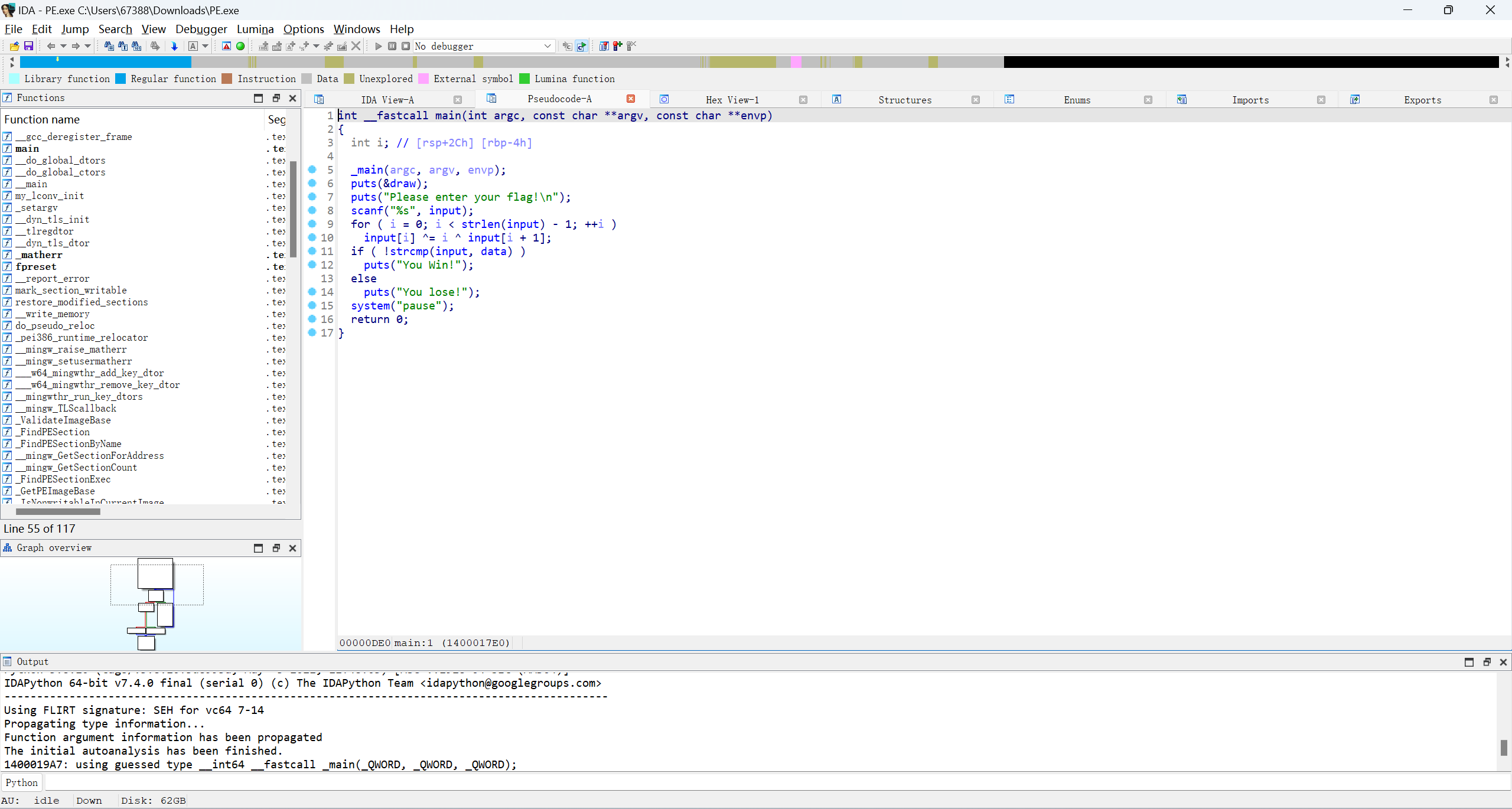
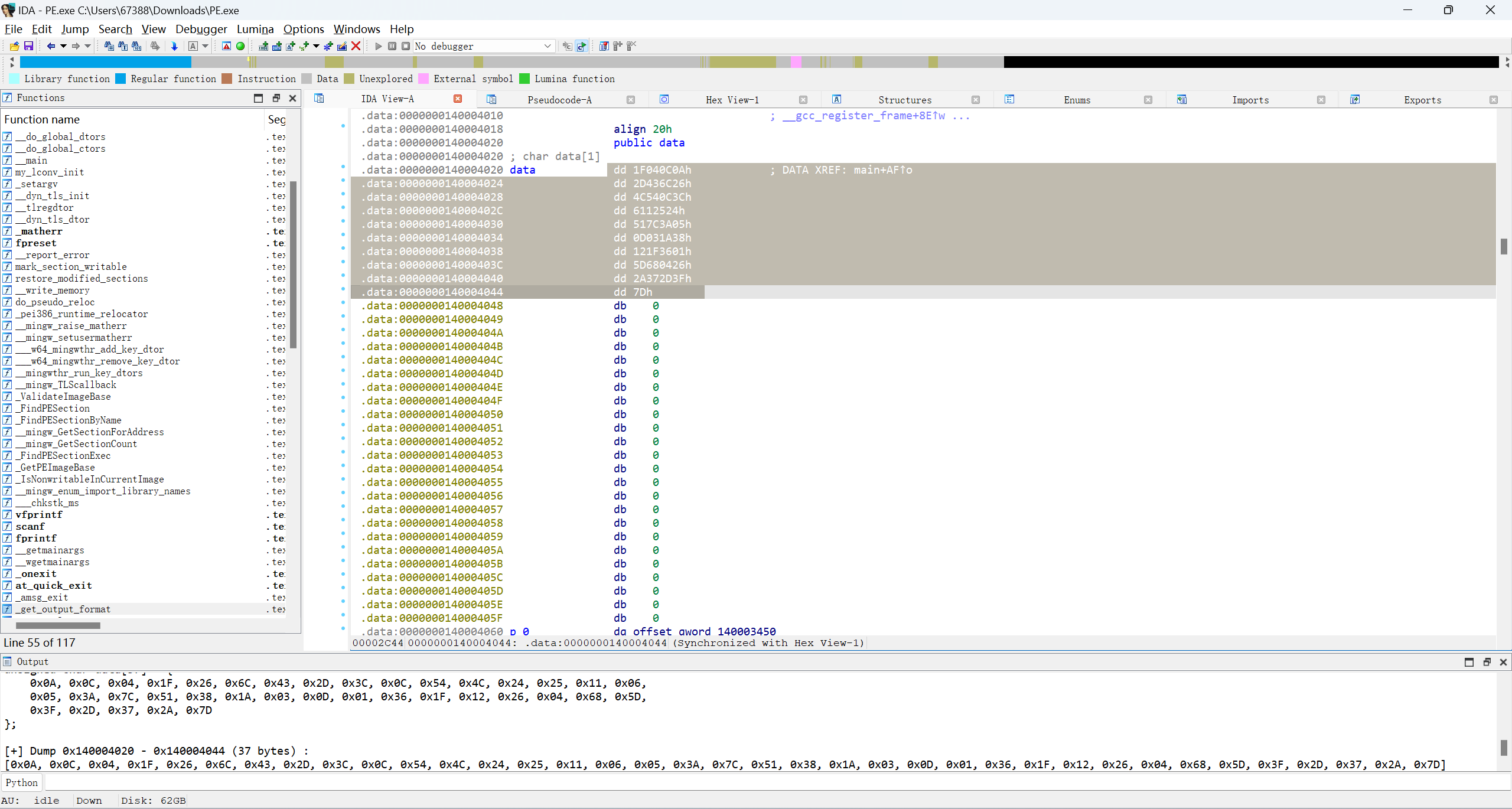
编写脚本
enc = [0x0A, 0x0C, 0x04, 0x1F, 0x26, 0x6C, 0x43, 0x2D, 0x3C, 0x0C, 0x54, 0x4C, 0x24, 0x25, 0x11, 0x06, 0x05, 0x3A, 0x7C, 0x51, 0x38, 0x1A, 0x03, 0x0D, 0x01, 0x36, 0x1F, 0x12, 0x26, 0x04, 0x68, 0x5D, 0x3F, 0x2D, 0x37, 0x2A, 0x7D]
flag = []
for i in range(35, -1, -1):
enc[i] = enc[i + 1] ^ enc[i] ^ i
for i in range(len(enc)):
flag += chr(enc[i])
print("".join(flag))
# flag{Y0u_kn0w_what_1s_PE_File_F0rmat}
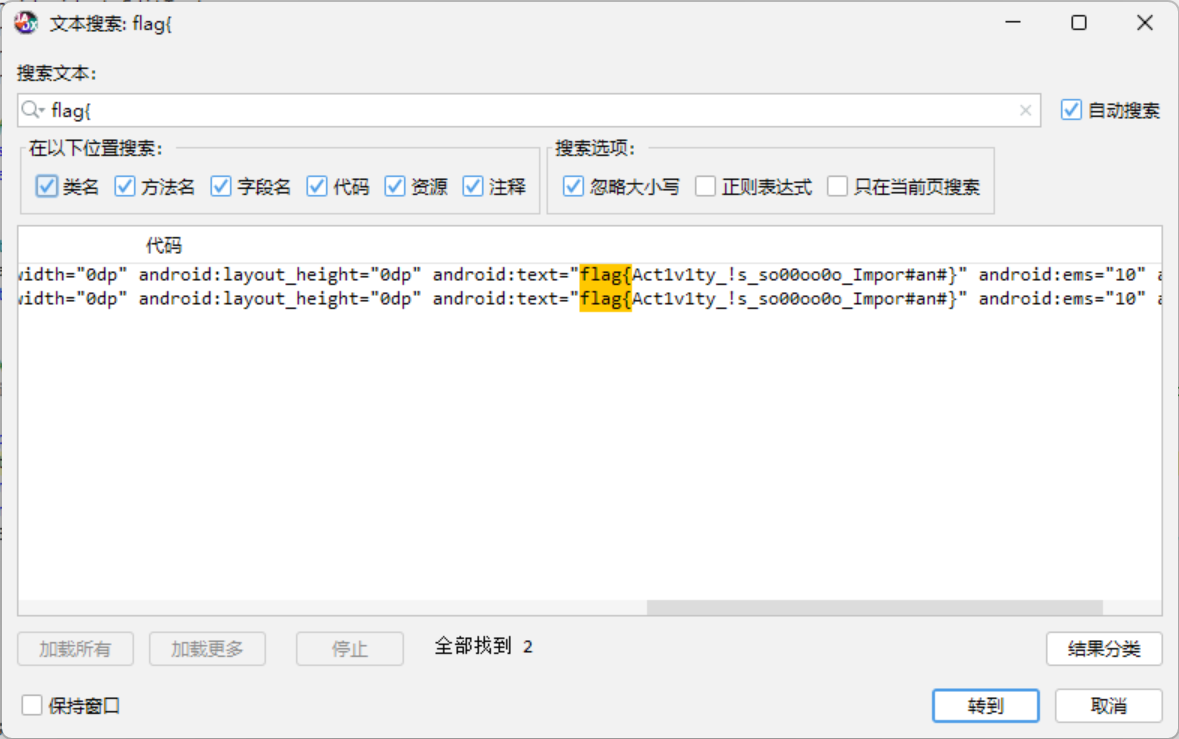
lazy_activtiy
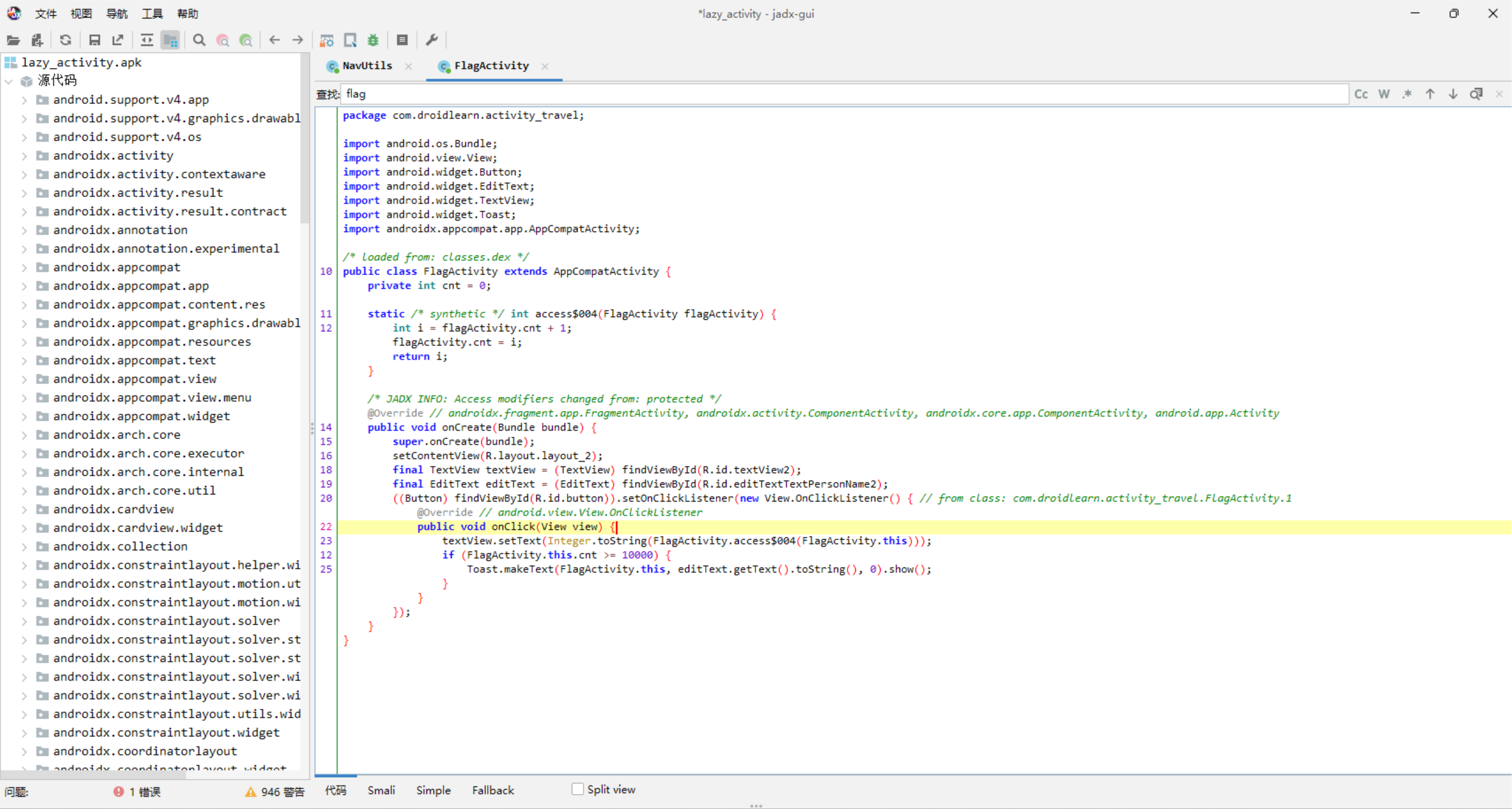
大于10000次
顺着搜下去


 浙公网安备 33010602011771号
浙公网安备 33010602011771号