HNCTF 2022 WEEK2
[HNCTF 2022 WEEK2]e@sy_flower
发现花指令
change type 90 nop掉
在主函数p重构,然后就可以反编译了
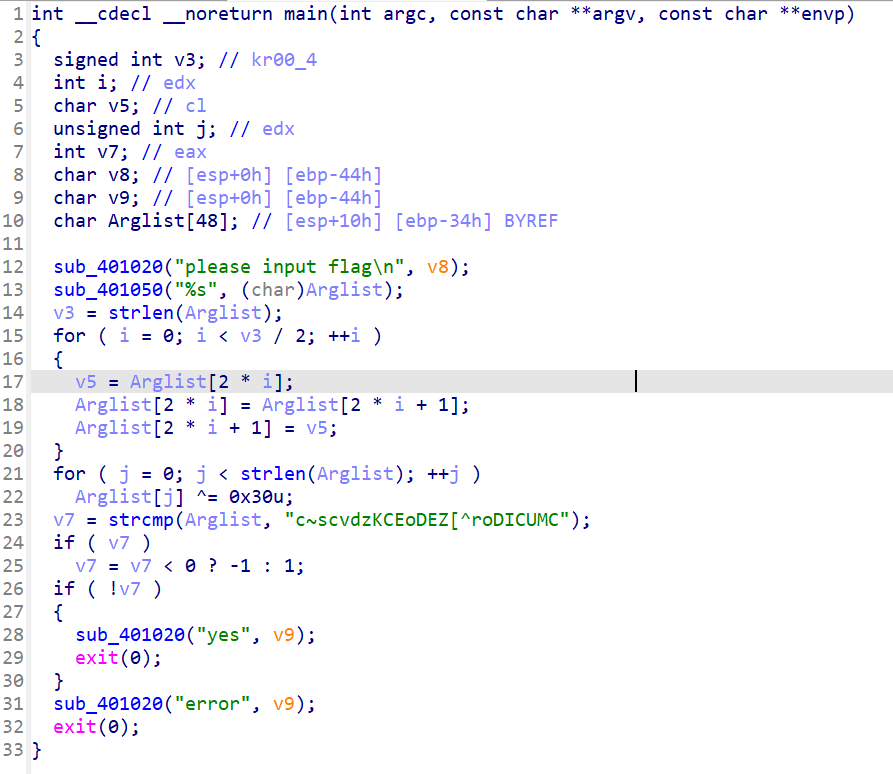
编写脚本
enc = "c~scvdzKCEoDEZ[^roDICUMC"
flag = [1] * 24
for j in range(24):
flag[j] = chr(ord(enc[j]) ^ 48)
for i in range(12):
v5 = flag[2 * i + 1]
flag[2 * i + 1] = flag[2 * i]
flag[2 * i] = v5
print("".join(flag))
#NSSCTF{Just_junk_Bytess}
[HNCTF 2022 WEEK2]Packet
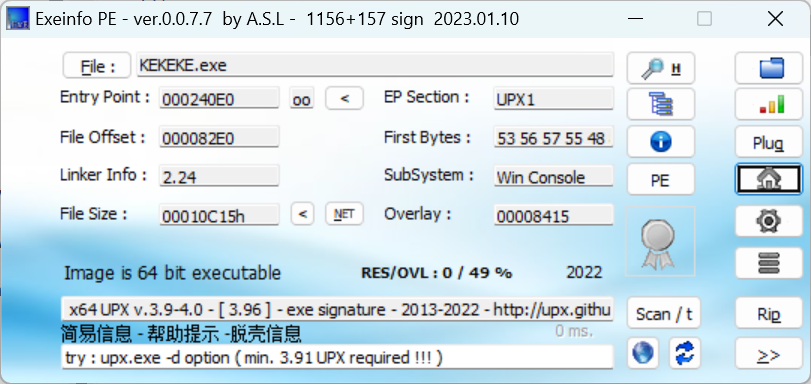
有UPX壳,脱壳
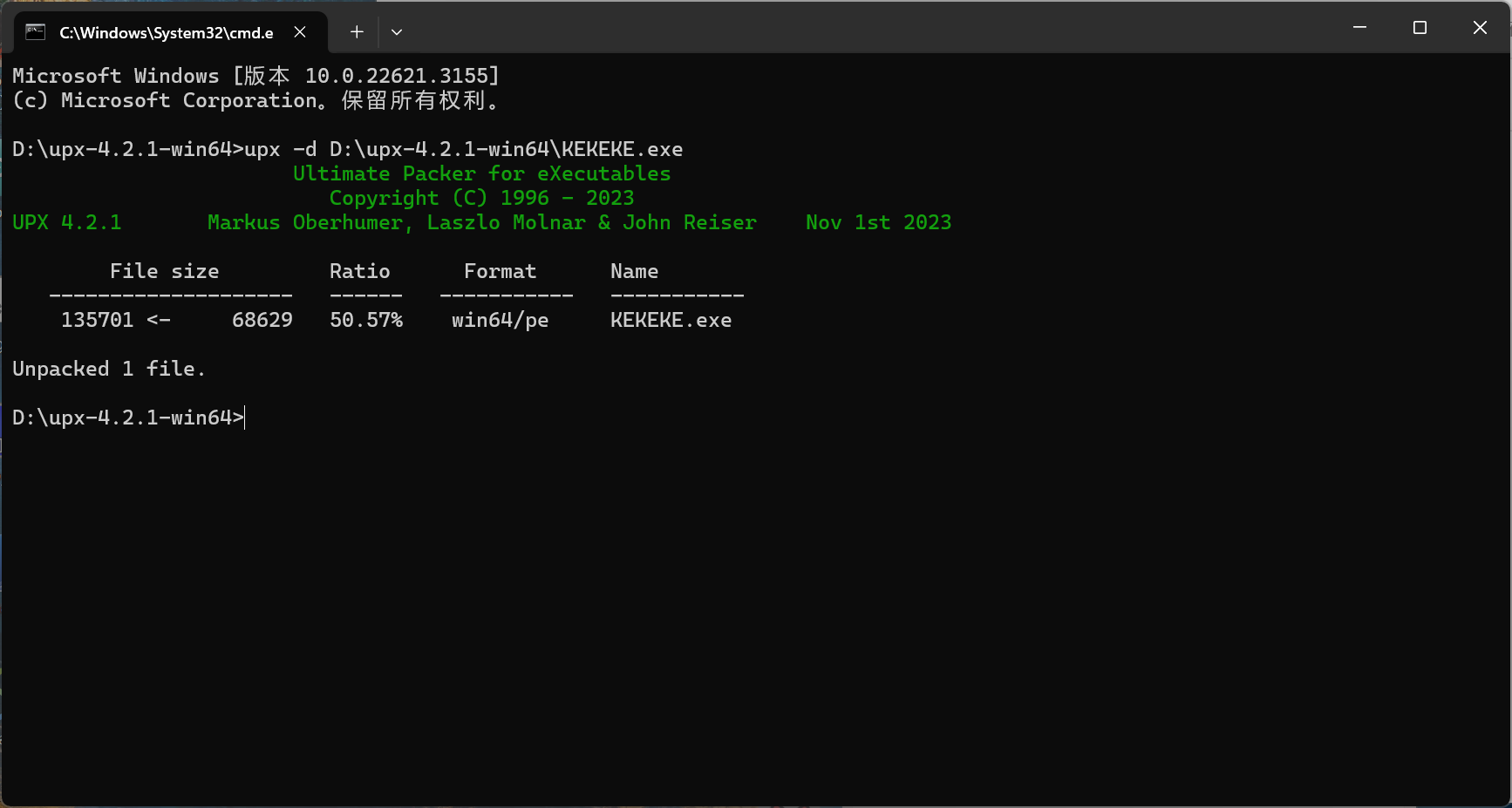
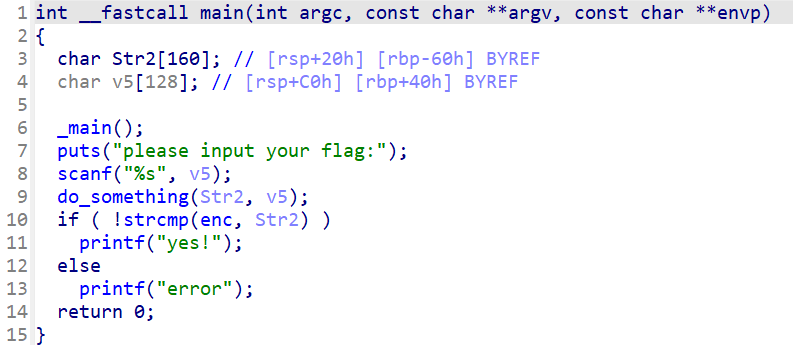
打开do_something查看
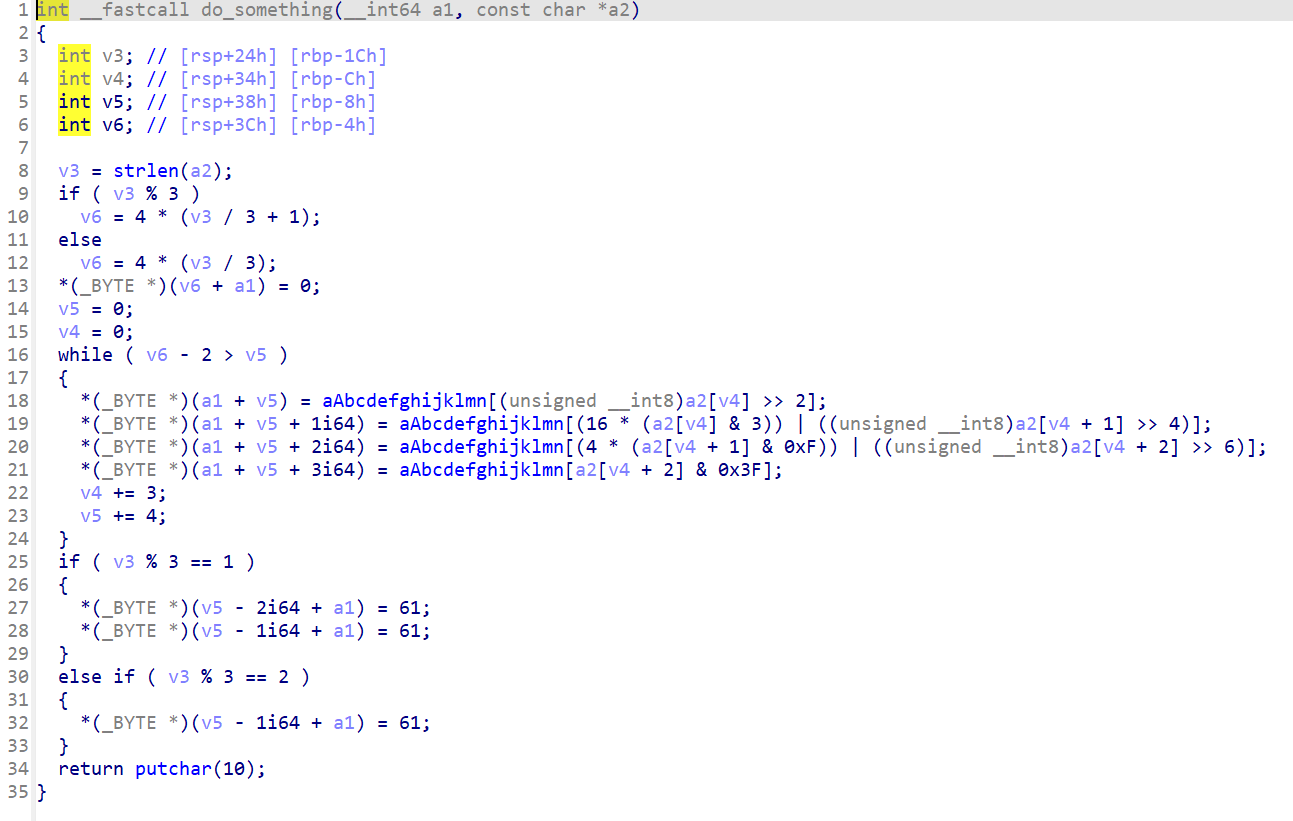
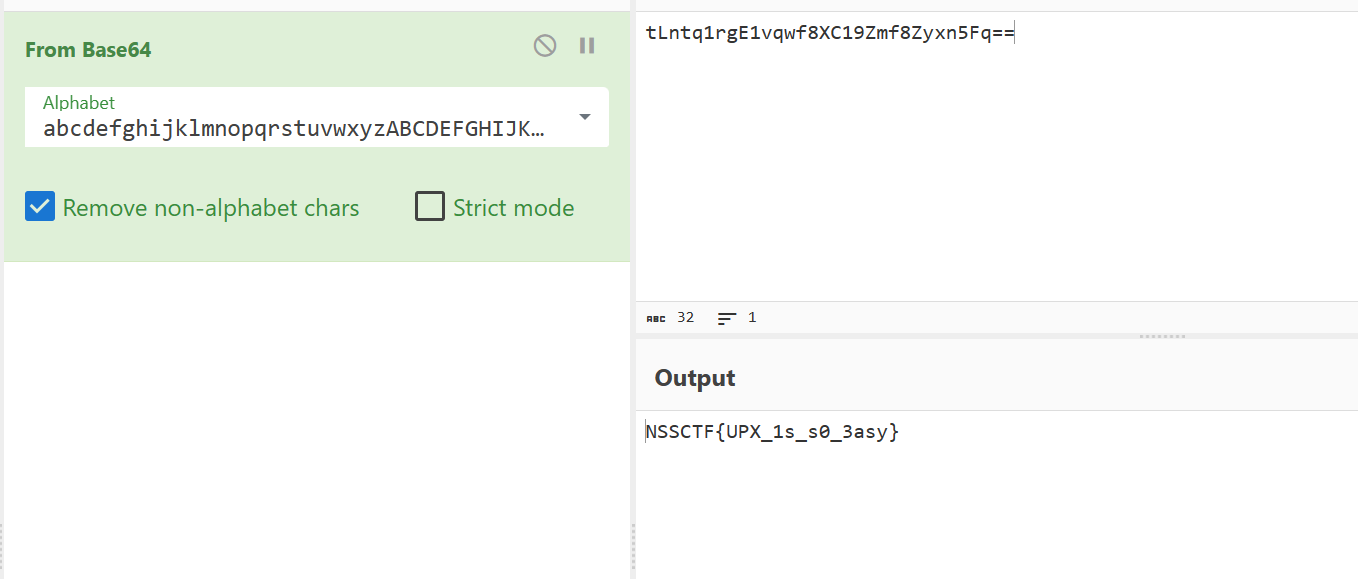
是一个base64
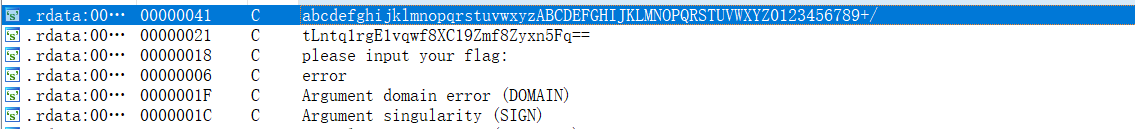
码表,enc都在上边
[HNCTF 2022 WEEK2]TTTTTTTTTea
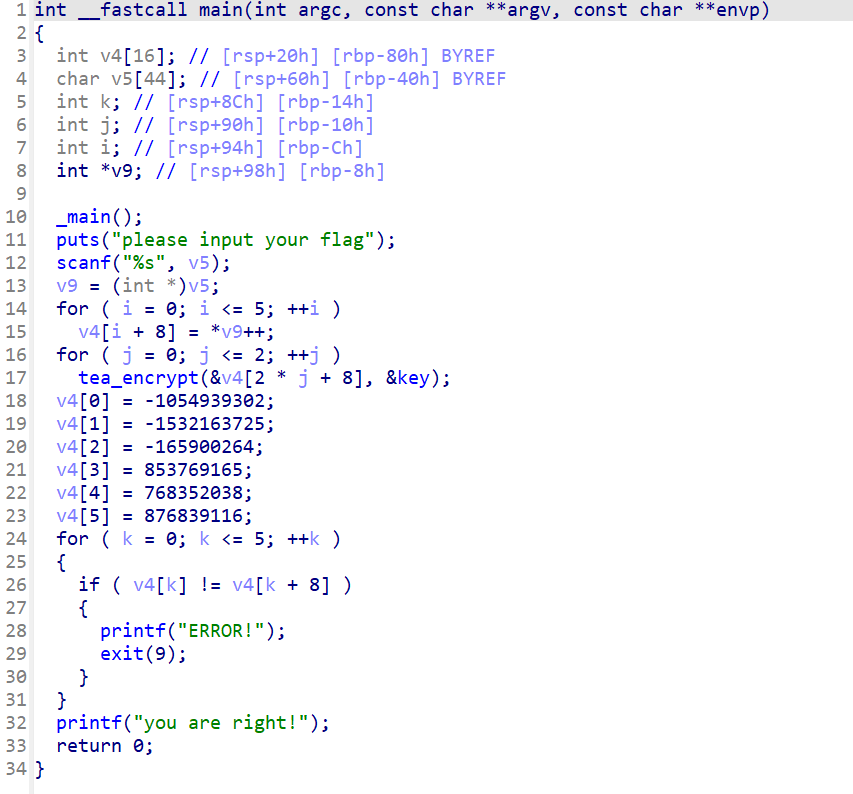
听名字就知道是tea加密,点开key看看,将db转换成dd
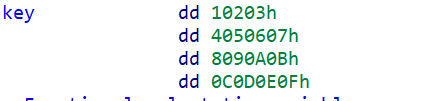
在打开加密函数看看
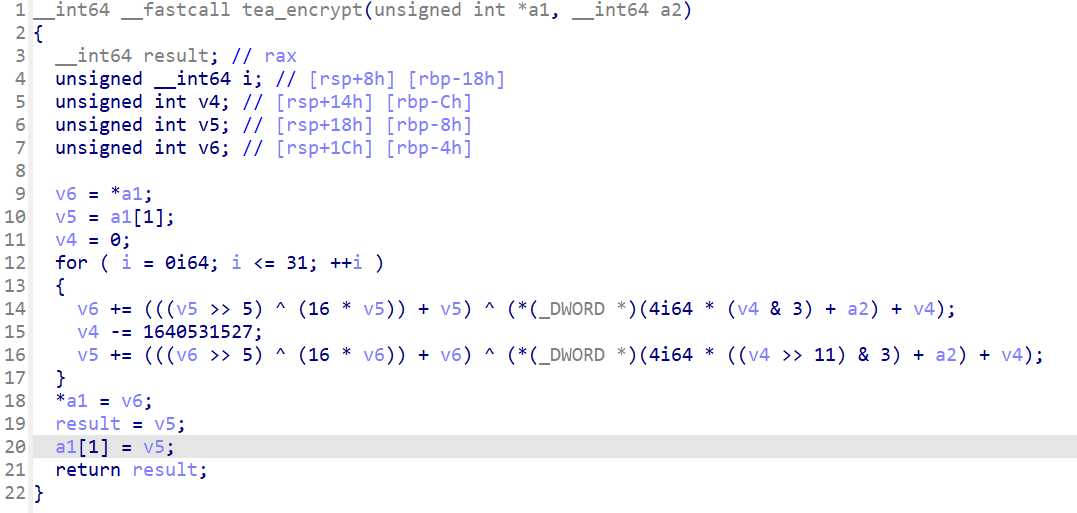
接下来就可以编写脚本了
#include <iostream>
#include <stdio.h>
#include <stdint.h>
using namespace std;
int main()
{
uint32_t enc[6] = { 0xC11EE75A, 0xA4AD0973, 0xF61C9018, 0x32E37BCD, 0x2DCC1F26, 0x344380CC, };
uint32_t key[4] = { 0x10203, 0x4050607, 0x8090A0B, 0x0C0D0E0F, };
uint32_t a1, a2;
for (int i = 0; i <= 2; i++)
{
a1 = enc[2 * i];
a2 = enc[2 * i + 1];
uint32_t dt = -1640531527 * 32;
for (int j = 0; j < 32; ++j)
{
a2 -= (((a1 >> 5) ^ (16 * a1)) + a1) ^ (key[(dt >> 11) & 3] + dt);
dt += 1640531527;
a1 -= (((a2 >> 5) ^ (16 * a2)) + a2) ^ (key[dt & 3] + dt);
enc[2 * i] = a1;
enc[2 * i + 1] = a2;
}
}
for (int i = 0; i < 6; i++)
{
printf("%X\n", enc[i]);
}
return 0;
}
//NSSCTF{Tea_TEA_TeA_TEa+}
[HNCTF 2022 WEEK2]来解个方程?
打开check函数看看
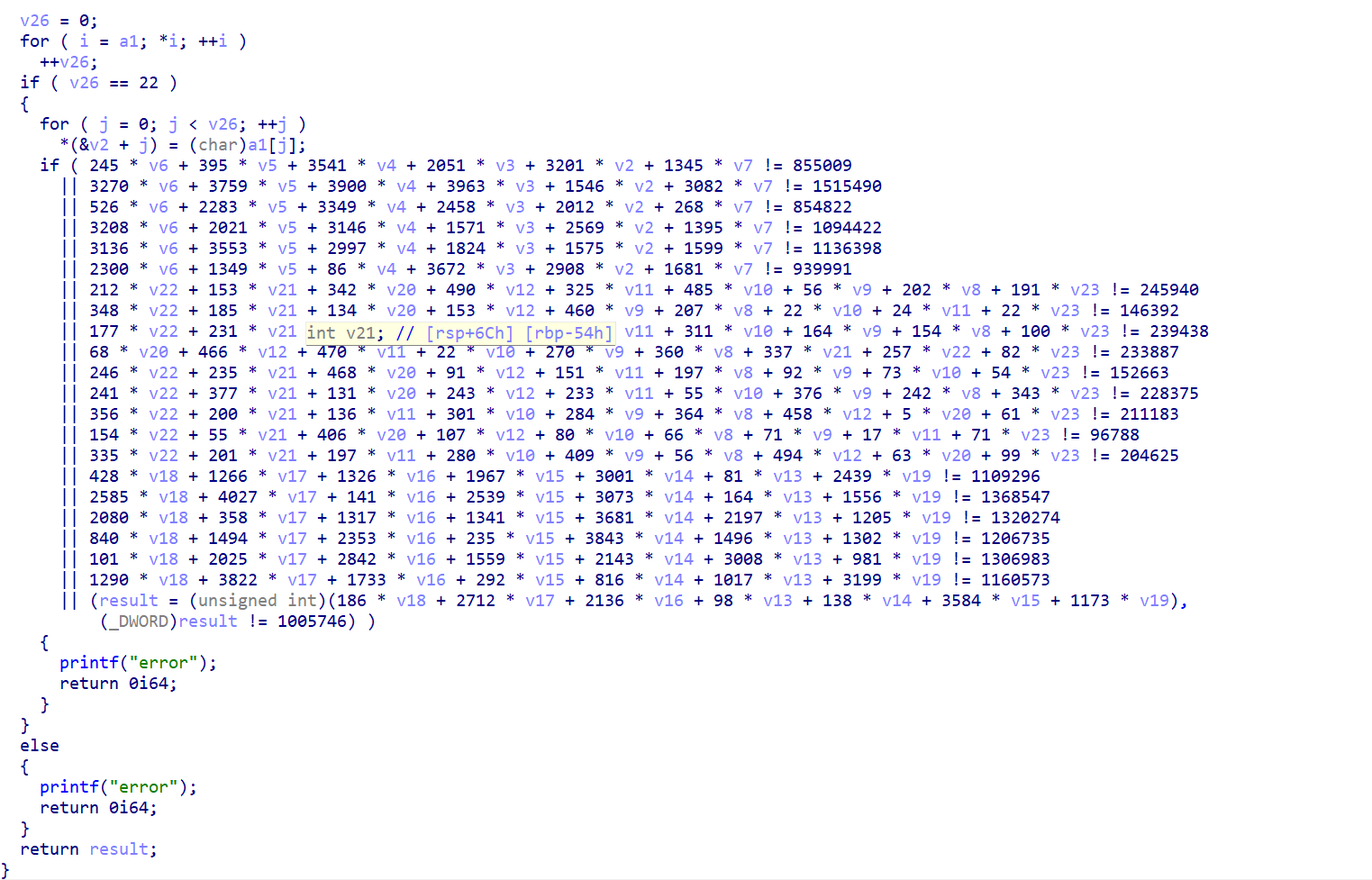
这么看来是要用z3去解方程组了,那么编写脚本
from z3 import *
s = Solver()
v2,v3,v4,v5,v6,v7,v8,v9,v10,v11,v12,v13,v14,v15,v16,v17,v18,v19,v20,v21,v22,v23 = Ints('v2 v3 v4 v5 v6 v7 v8 v9 v10 v11 v12 v13 v14 v15 v16 v17 v18 v19 v20 v21 v22 v23')
allints = [
245 * v6 + 395 * v5 + 3541 * v4 + 2051 * v3 + 3201 * v2 + 1345 * v7 == 855009,
3270 * v6 + 3759 * v5 + 3900 * v4 + 3963 * v3 + 1546 * v2 + 3082 * v7 == 1515490,
526 * v6 + 2283 * v5 + 3349 * v4 + 2458 * v3 + 2012 * v2 + 268 * v7 == 854822,
3208 * v6 + 2021 * v5 + 3146 * v4 + 1571 * v3 + 2569 * v2 + 1395 * v7 == 1094422,
3136 * v6 + 3553 * v5 + 2997 * v4 + 1824 * v3 + 1575 * v2 + 1599 * v7 == 1136398,
2300 * v6 + 1349 * v5 + 86 * v4 + 3672 * v3 + 2908 * v2 + 1681 * v7 == 939991,
212 * v22 + 153 * v21 + 342 * v20 + 490 * v12 + 325 * v11 + 485 * v10 + 56 * v9 + 202 * v8 + 191 * v23 == 245940,
348 * v22 + 185 * v21 + 134 * v20 + 153 * v12 + 460 * v9 + 207 * v8 + 22 * v10 + 24 * v11 + 22 * v23 == 146392,
177 * v22 + 231 * v21 + 489 * v20 + 339 * v12 + 433 * v11 + 311 * v10 + 164 * v9 + 154 * v8 + 100 * v23 == 239438,
68 * v20 + 466 * v12 + 470 * v11 + 22 * v10 + 270 * v9 + 360 * v8 + 337 * v21 + 257 * v22 + 82 * v23 == 233887,
246 * v22 + 235 * v21 + 468 * v20 + 91 * v12 + 151 * v11 + 197 * v8 + 92 * v9 + 73 * v10 + 54 * v23 == 152663,
241 * v22 + 377 * v21 + 131 * v20 + 243 * v12 + 233 * v11 + 55 * v10 + 376 * v9 + 242 * v8 + 343 * v23 == 228375,
356 * v22 + 200 * v21 + 136 * v11 + 301 * v10 + 284 * v9 + 364 * v8 + 458 * v12 + 5 * v20 + 61 * v23 == 211183,
154 * v22 + 55 * v21 + 406 * v20 + 107 * v12 + 80 * v10 + 66 * v8 + 71 * v9 + 17 * v11 + 71 * v23 == 96788,
335 * v22 + 201 * v21 + 197 * v11 + 280 * v10 + 409 * v9 + 56 * v8 + 494 * v12 + 63 * v20 + 99 * v23 == 204625,
428 * v18 + 1266 * v17 + 1326 * v16 + 1967 * v15 + 3001 * v14 + 81 * v13 + 2439 * v19 == 1109296,
2585 * v18 + 4027 * v17 + 141 * v16 + 2539 * v15 + 3073 * v14 + 164 * v13 + 1556 * v19 == 1368547,
2080 * v18 + 358 * v17 + 1317 * v16 + 1341 * v15 + 3681 * v14 + 2197 * v13 + 1205 * v19 == 1320274,
840 * v18 + 1494 * v17 + 2353 * v16 + 235 * v15 + 3843 * v14 + 1496 * v13 + 1302 * v19 == 1206735,
101 * v18 + 2025 * v17 + 2842 * v16 + 1559 * v15 + 2143 * v14 + 3008 * v13 + 981 * v19 == 1306983,
1290 * v18 + 3822 * v17 + 1733 * v16 + 292 * v15 + 816 * v14 + 1017 * v13 + 3199 * v19 == 1160573,
186 * v18 + 2712 * v17 + 2136 * v16 + 98 * v13 + 138 * v14 + 3584 * v15 + 1173 * v19 == 1005746,
]
s.add(allints)
flag = []
if s.check() == sat:
ans = s.model()
flag.append(ans[v2])
flag.append(ans[v3])
flag.append(ans[v4])
flag.append(ans[v5])
flag.append(ans[v6])
flag.append(ans[v7])
flag.append(ans[v8])
flag.append(ans[v9])
flag.append(ans[v10])
flag.append(ans[v11])
flag.append(ans[v12])
flag.append(ans[v13])
flag.append(ans[v14])
flag.append(ans[v15])
flag.append(ans[v16])
flag.append(ans[v17])
flag.append(ans[v18])
flag.append(ans[v19])
flag.append(ans[v20])
flag.append(ans[v21])
flag.append(ans[v22])
flag.append(ans[v23])
print(flag)
realflag = [78, 83, 83, 67, 84, 70, 123, 112, 105, 112, 95, 105, 110, 115, 116, 64, 108, 108, 95, 90, 51, 125]
endflag = ''.join(chr(i) for i in realflag)
print(endflag)
#NSSCTF{pip_inst@ll_Z3}
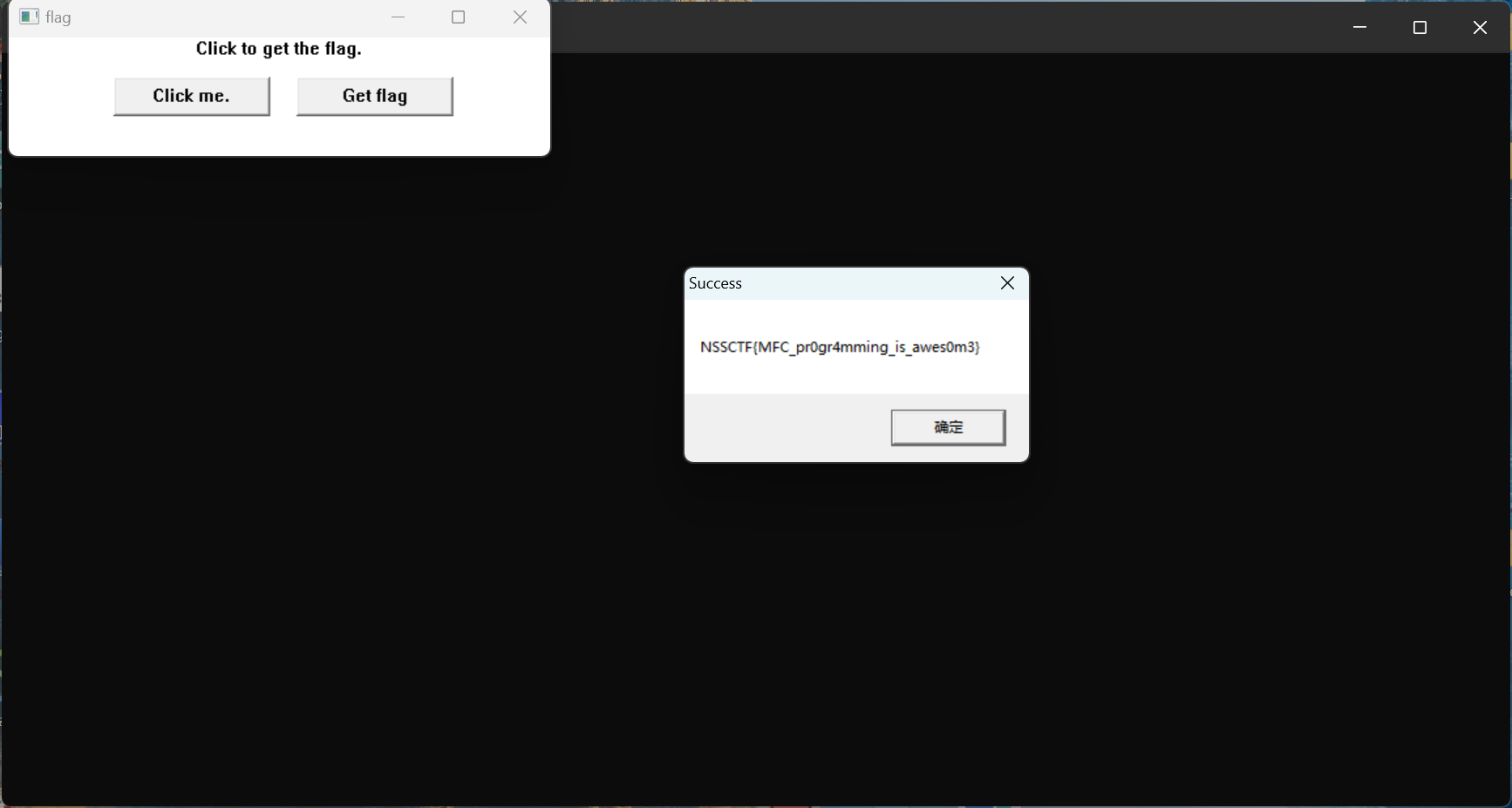
[HNCTF 2022 WEEK2]getflag
要点击多次才能拿到flag,那么我们可以直接去修改他的check函数
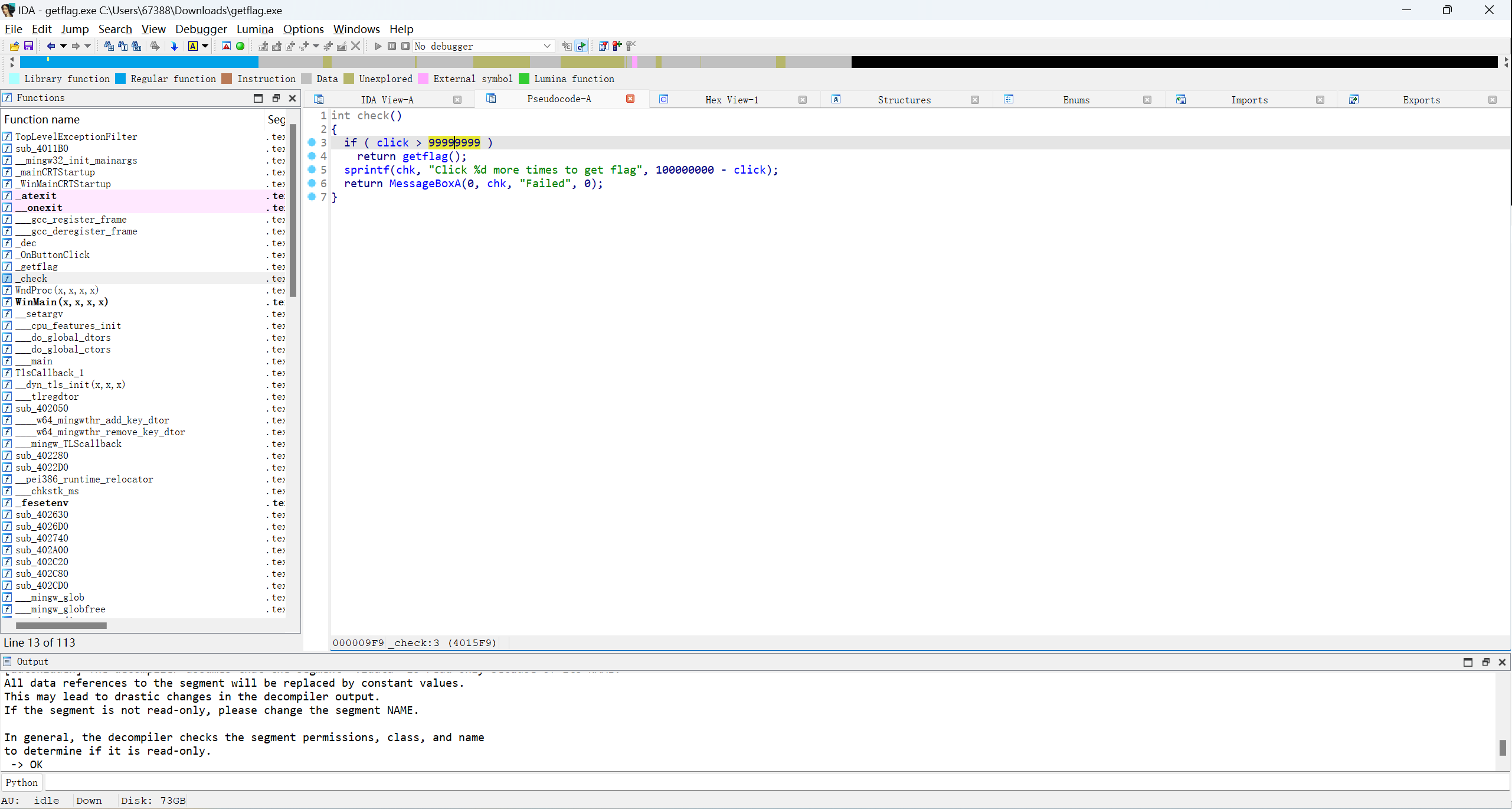
把99999999修改成1就行了(或者将jg改为jle,即将">"改为"<"),在汇编中找到指定位置
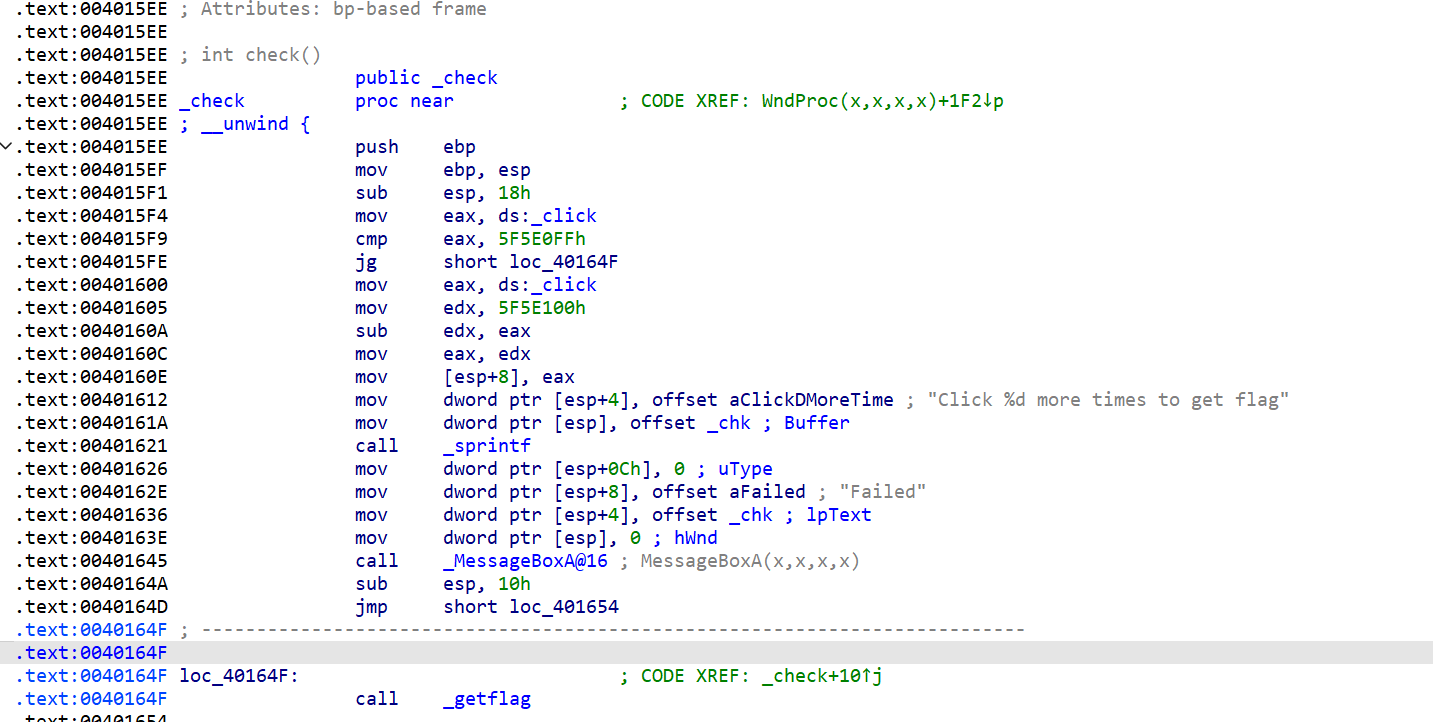
右键Assemble将99999999改为1
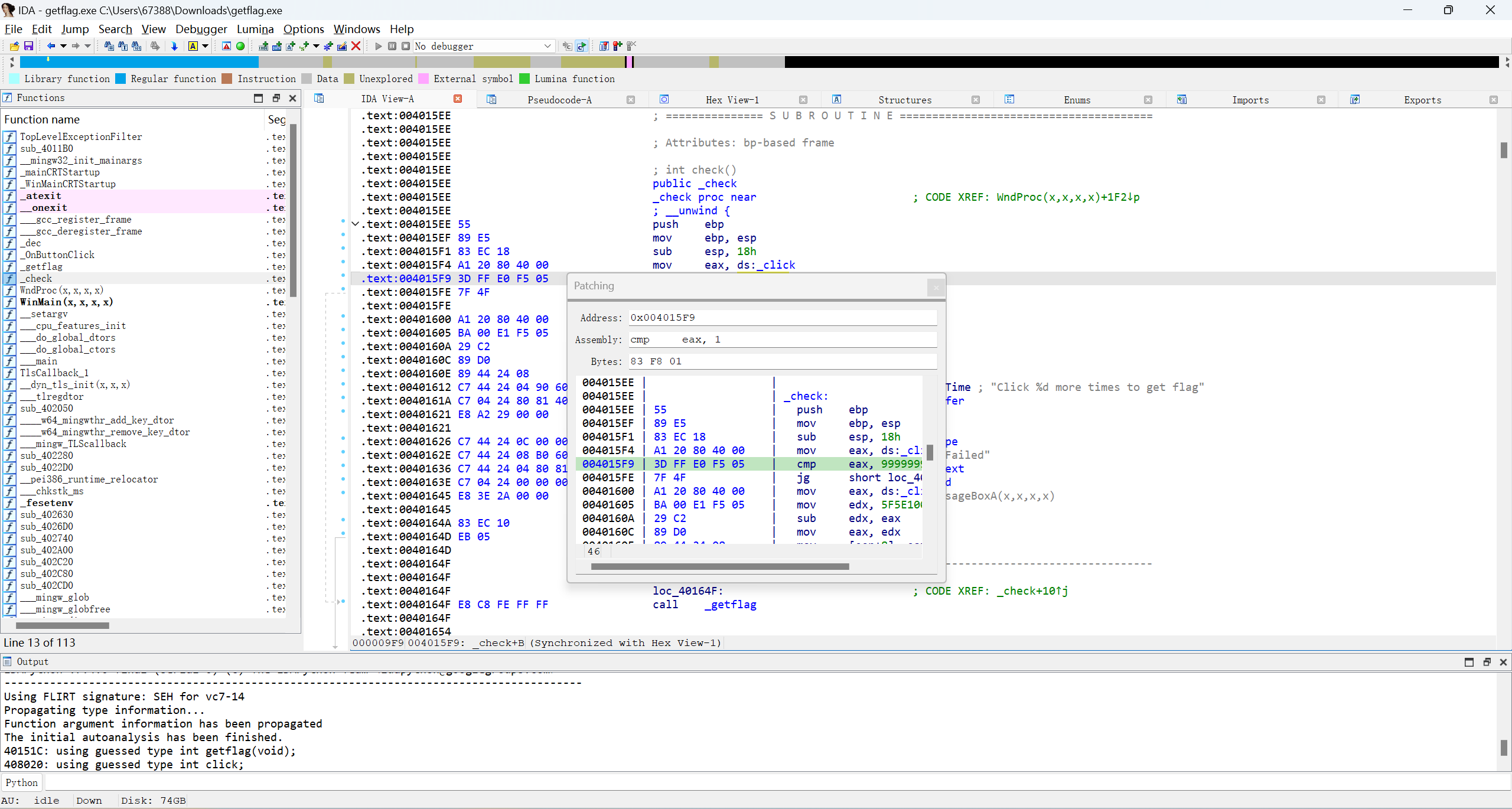
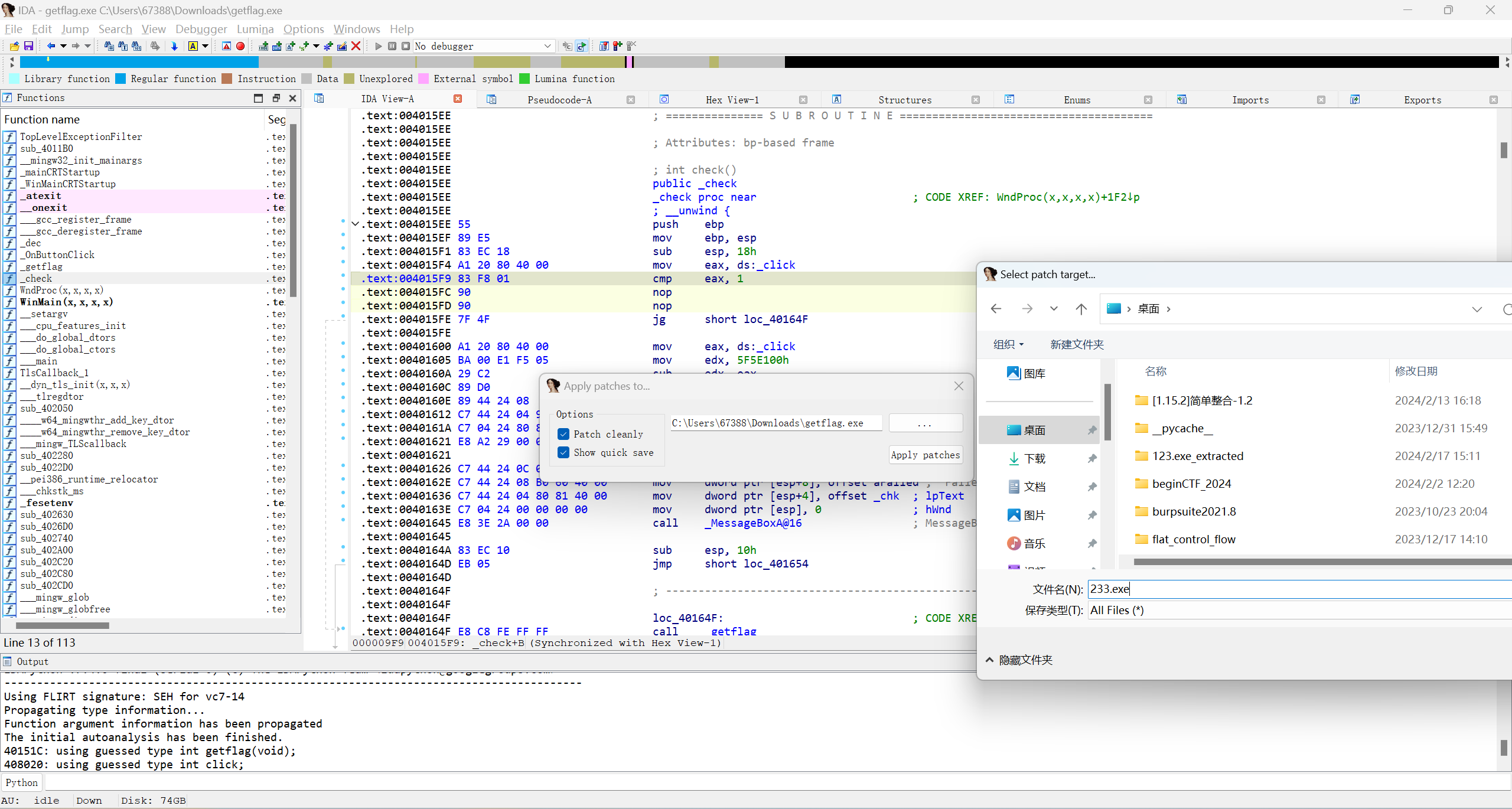
再在patch program中的apply patches to里修改
[HNCTF 2022 WEEK2]Easy_Android
首先使用jadx打开下载文件,关键代码如下图
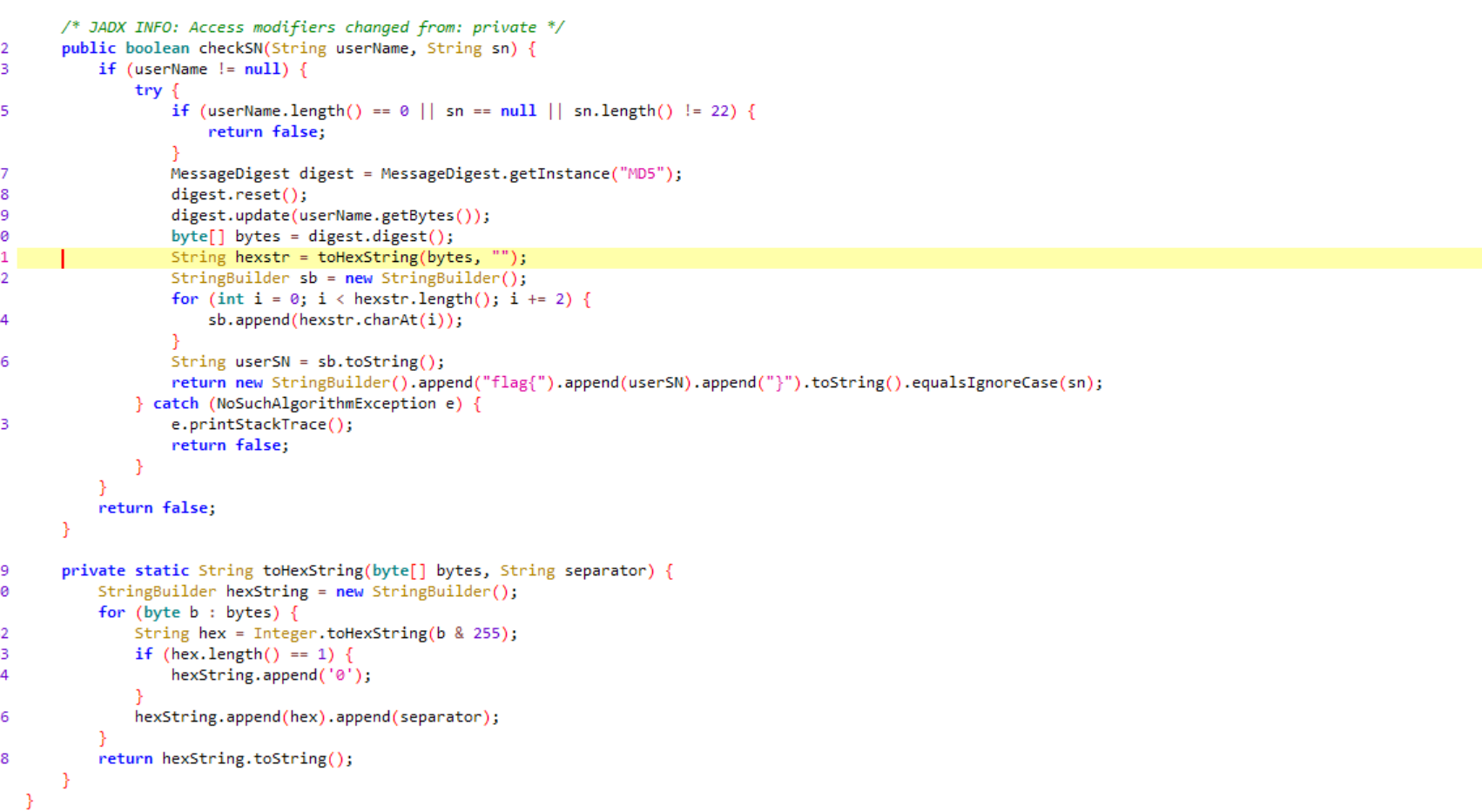
首先将username通过一个MD5加密,然后再在下一个for循环里取奇数构成flag
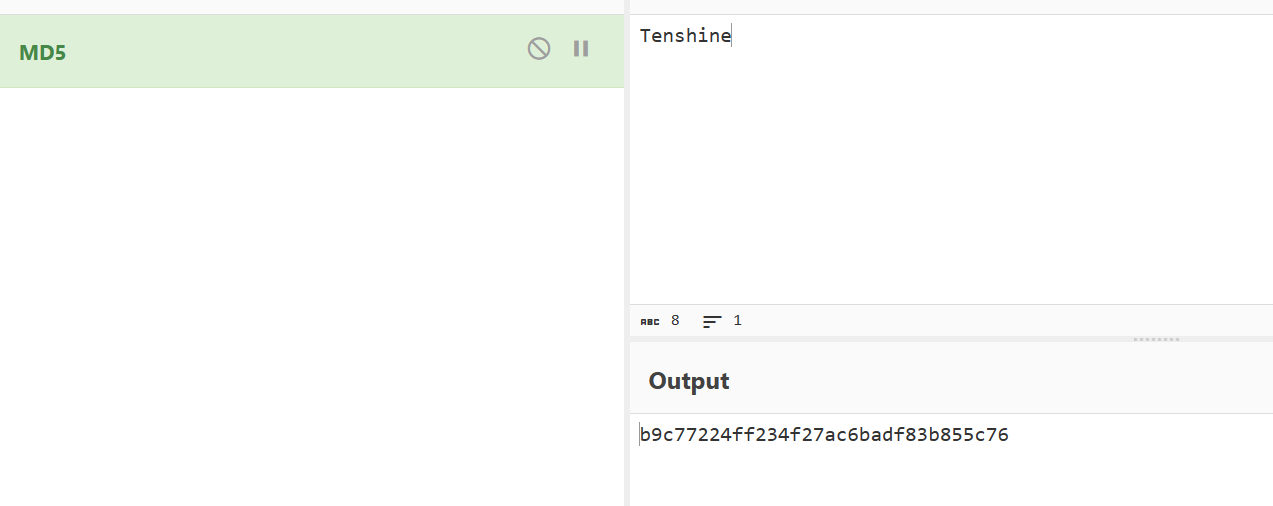
那么编写脚本
enc = 'b9c77224ff234f27ac6badf83b855c76'
flag = []
for i in range(0,len(enc),2):
flag.append(enc[i])
print("".join(flag))
#bc72f242a6af3857
[HNCTF 2022 WEEK2]Try2Bebug_Plus
下载下来后是一个elf文件
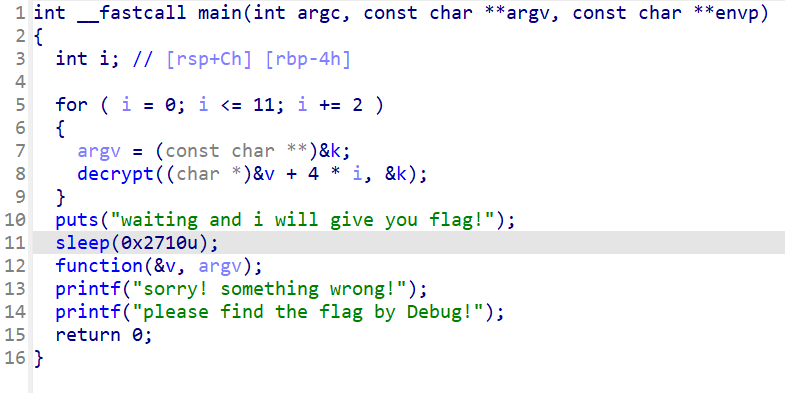
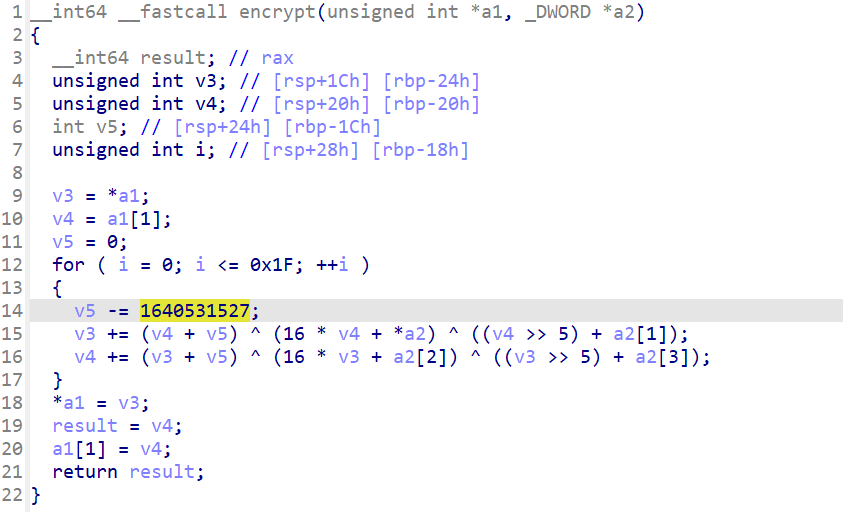
打开encrypt函数是一个TEA加密
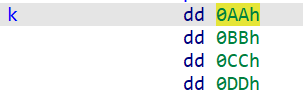
key是这个
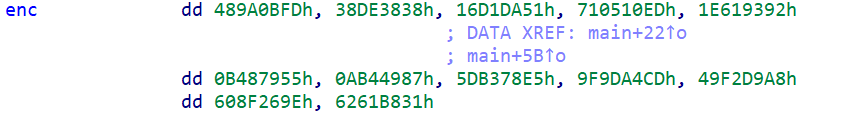
enc是这个
然后看到function函数有一个异或
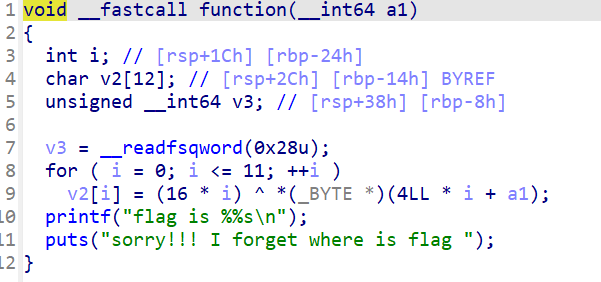
那么可以编写脚本了
#include <stdio.h>
#include <string.h>
#include <stdint.h>
int main(void)
{
uint32_t enc[12] = { 0x489A0BFD, 0x38DE3838, 0x16D1DA51, 0x710510ED, 0x1E619392, 0x0B487955, 0x0AB44987, 0x5DB378E5, 0x9F9DA4CD, 0x49F2D9A8, 0x608F269E, 0x6261B831, };
uint32_t key[4] = { 0x0AA, 0x0BB, 0x0CC, 0x0DD, };
uint32_t v1, v2, sum;
unsigned char flag[12];
for (int k = 0; k < 12; k += 2)
{
v1 = enc[k];
v2 = enc[k + 1];
sum = -1640531527 * 32;
for (int i = 0; i < 32; ++i)
{
v2 -= (v1 + sum) ^ (16 * v1 + key[2]) ^ ((v1 >> 5) + key[3]);
v1 -= (v2 + sum) ^ (16 * v2 + *key) ^ ((v2 >> 5) + key[1]);
sum += 1640531527;
}
enc[k] = v1;
enc[k + 1] = v2;
}
for (int i = 0; i < 12; i++)
{
flag[i] = (enc[i]) ^ (16 * i);
printf("%c", flag[i]);
}
}
//th1s_1s_flag



