Wireshark for Ethical Hackers - 7
Networking of Sniffing Crash Theory Practice - Part 3
Active Sniffing vs. Passive Sniffing
- Active Sniffing relies on sending some frames, performing MITM-attacks
- Passive Sniffing means that the sniffing host only sniffs
- Unicasts may be sniffed within the Collision domain
- Broadcasts and (sometimes) multicasts may be sniffed within the whole Broadcast domain(VLAN)
- Totally passive sniffing
- Ways to perform the totally passive sniffing:
- Receive-only UTP cable (Wall jack)
- Tap: L1 device - Allows to view malformed frames, L1/L2 errors. Professional taps may support 1 Gbit, 10 Gbit or better
- Firewall: outbound
- Manipulations with TCP/IP: Disable TCP/IP on Windows, no IP address on Linux
- Technologies like Port Mirroring
- Ways to perform the totally passive sniffing:
View Telnet passwords
- Client-server protocol
- Used for the remote administration
- TCP port 23
- No encryption
- Use SSH if possible
- Still popular
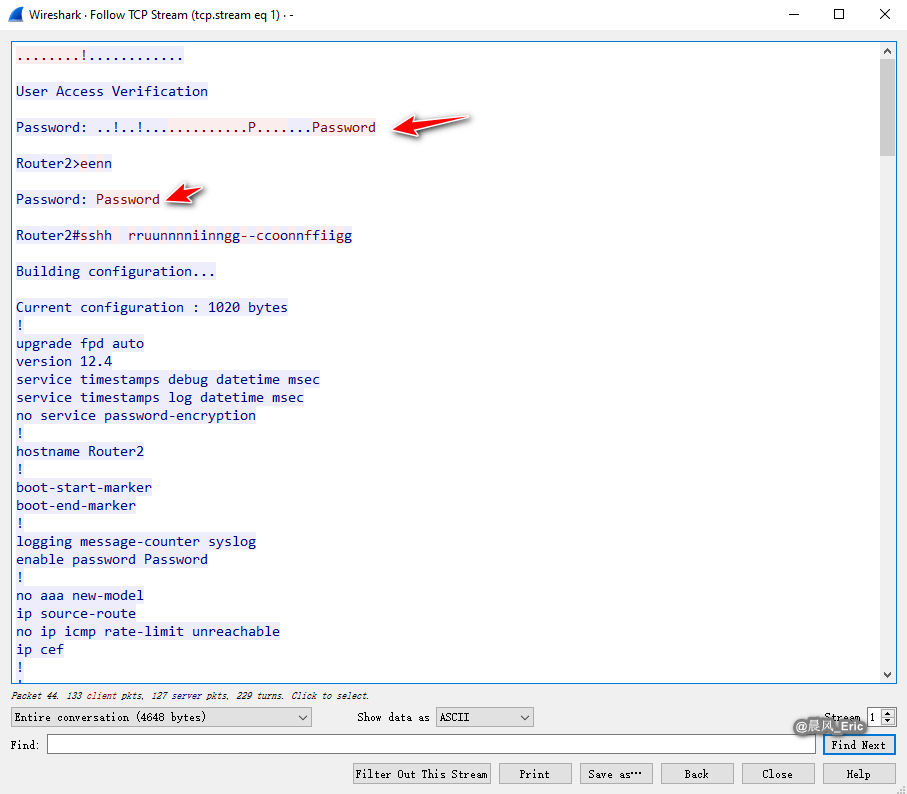
Practice case: The user telnets to Router2 from Router 1, types his passwords and then views the router configuration. The eavesdropper with Wireshark will try to sniff this and get the passwords.
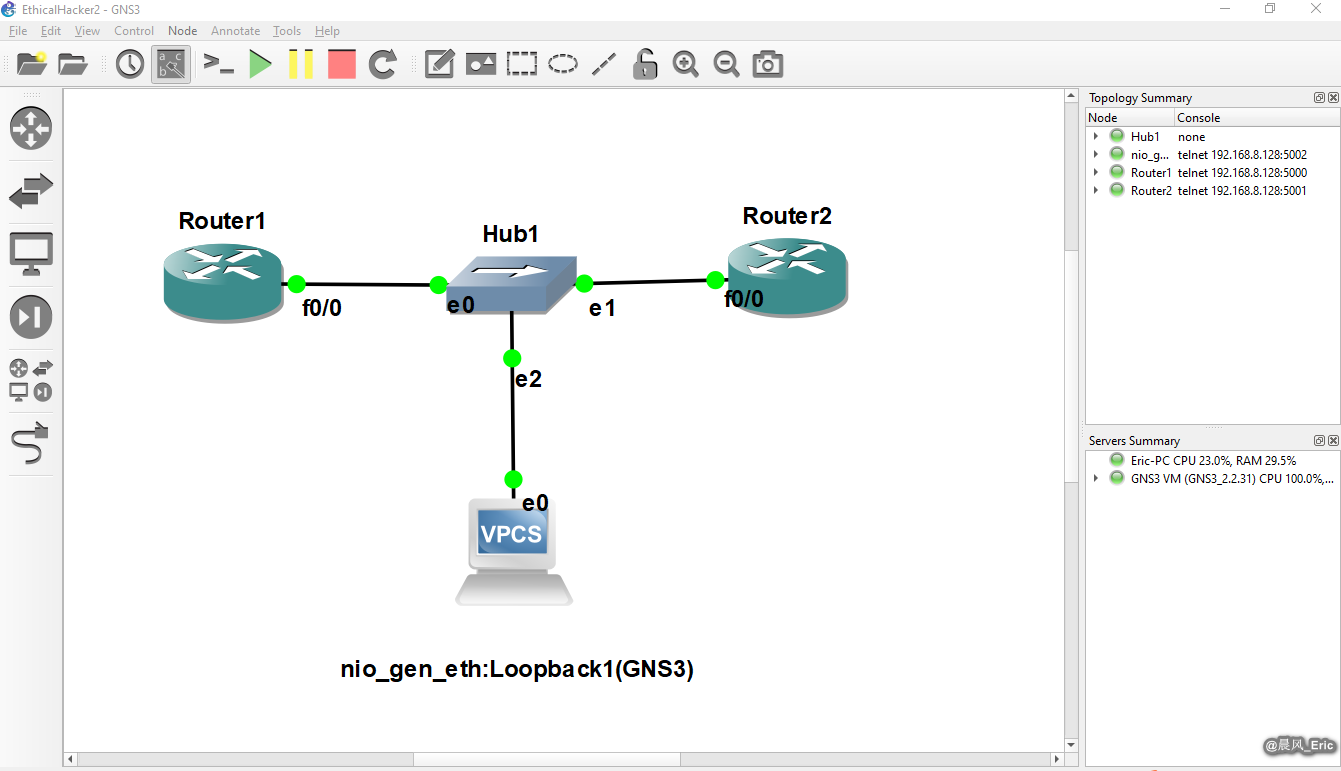
Set up a testing lab.
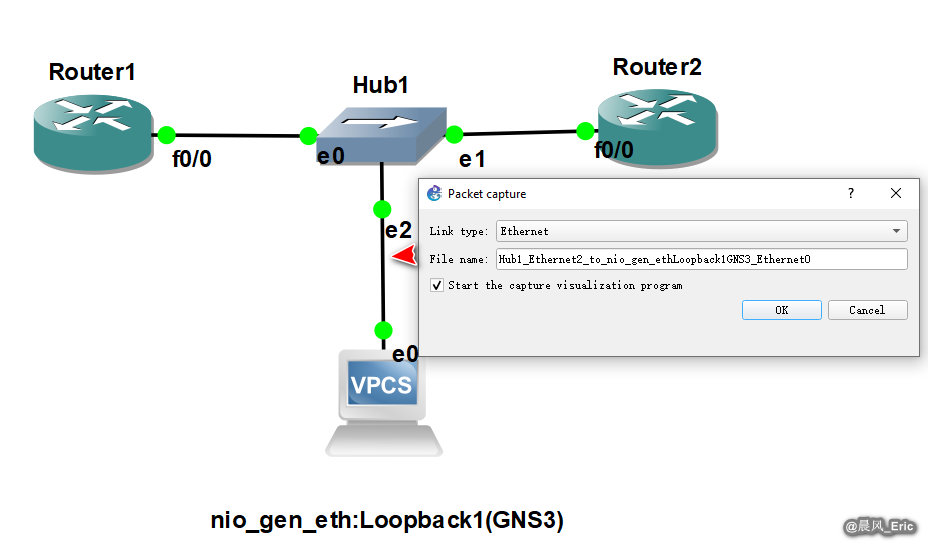
Start Wireshark to capture packet.
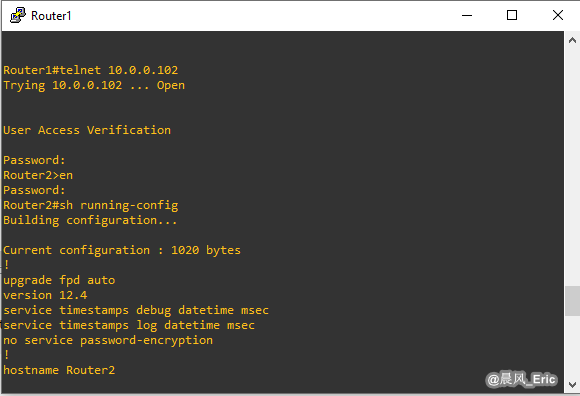
Run the console on Router1.
Router1#telnet 10.0.0.102
Trying 10.0.0.102 ... Open
User Access Verification
Password:
Router2>en
Password:
Router2#sh running-config
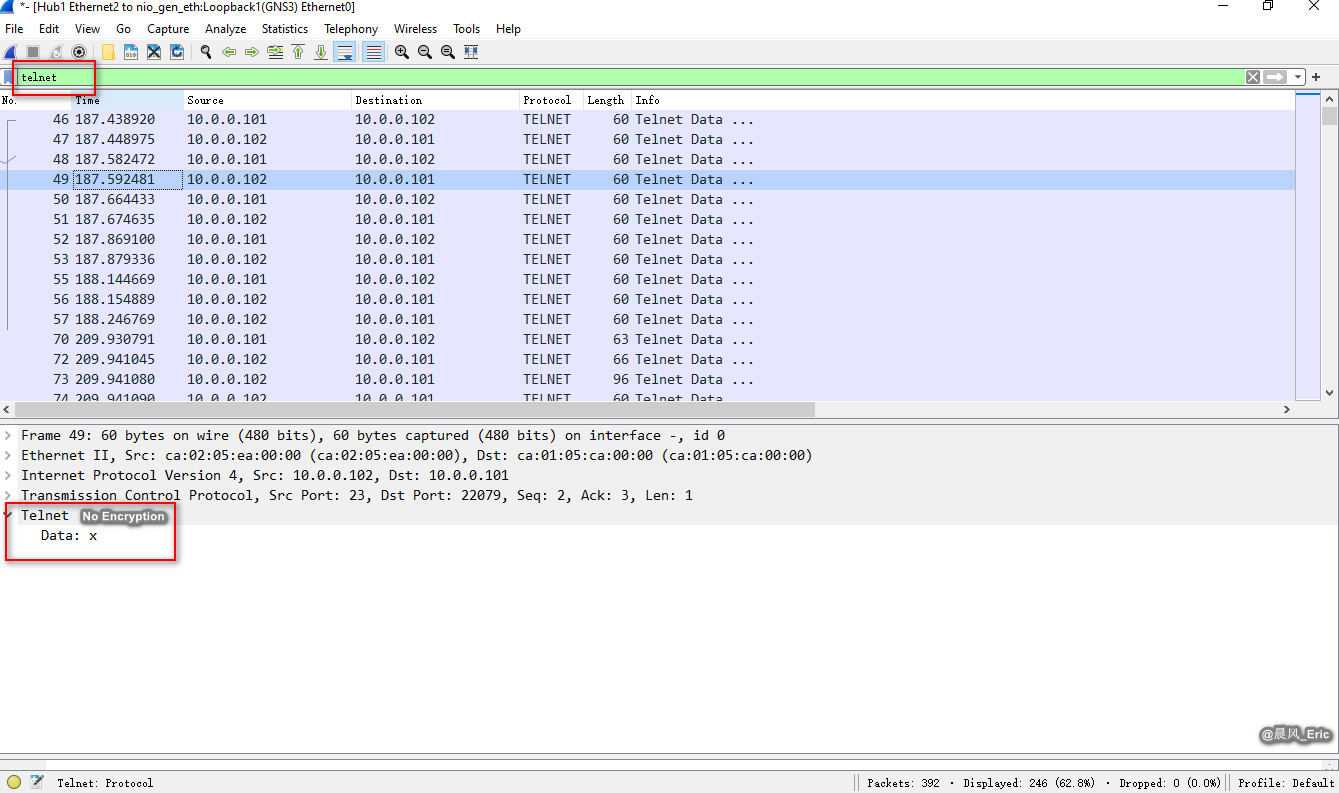
Stop capture and filter "telnet".
Right click and select "Follow TCP stream". We can the password - Password
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号