OSCP Security Technology - Post-Exploit Password Attacks
OSCP Security Technology - Post-Exploit Password Attacks
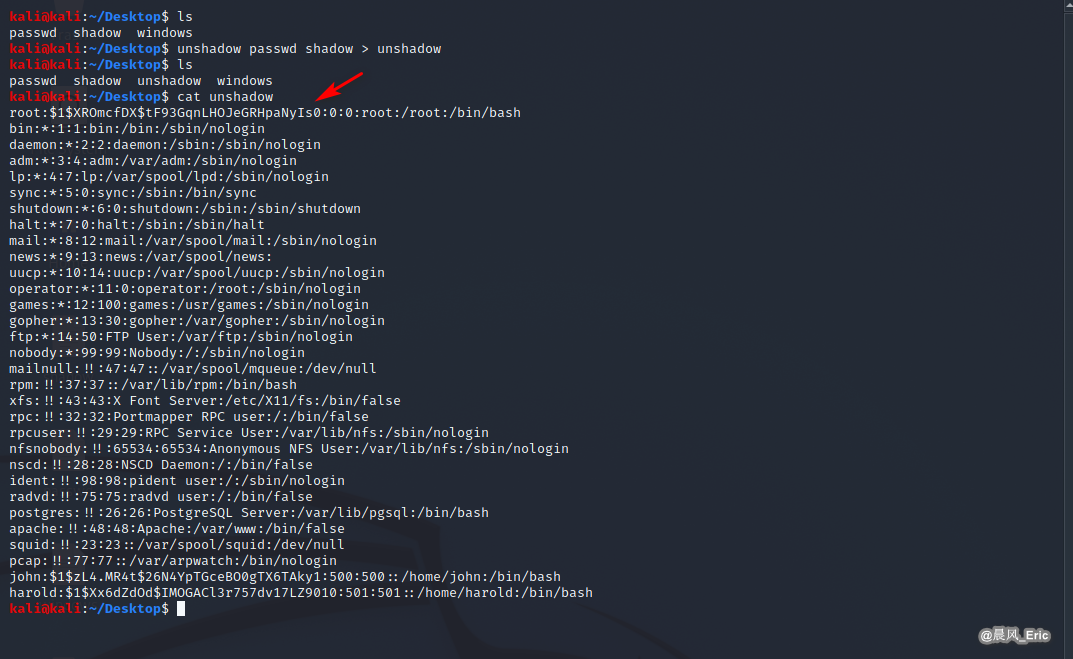
Find the three passwords files saved previously.
John
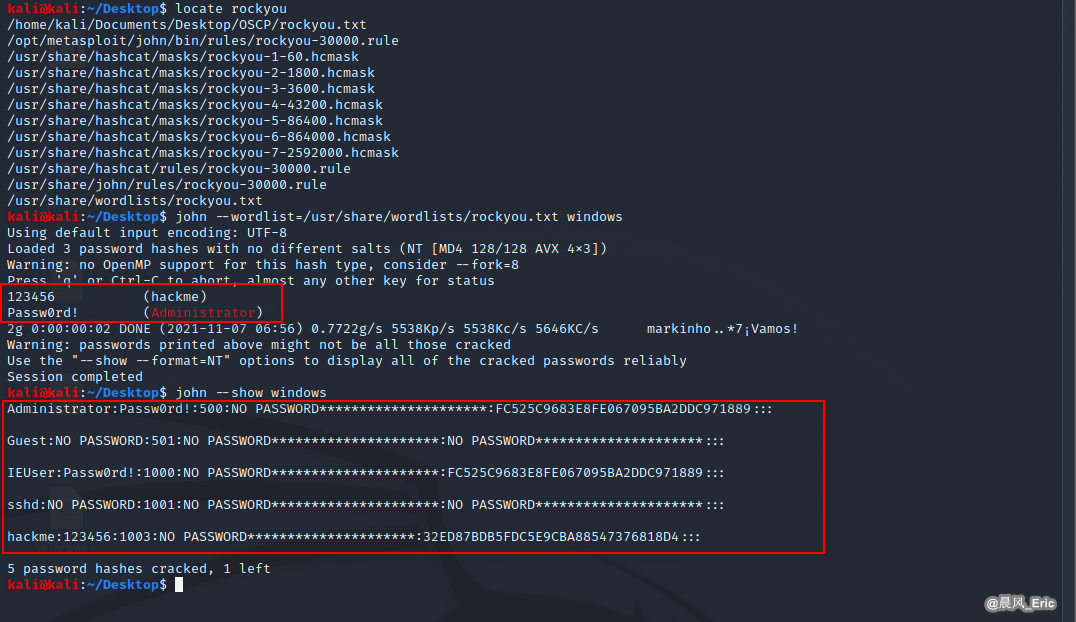
locate rockyou
john --wordlist=/usr/share/wordlists/rockyou.txt windows
john --show windows
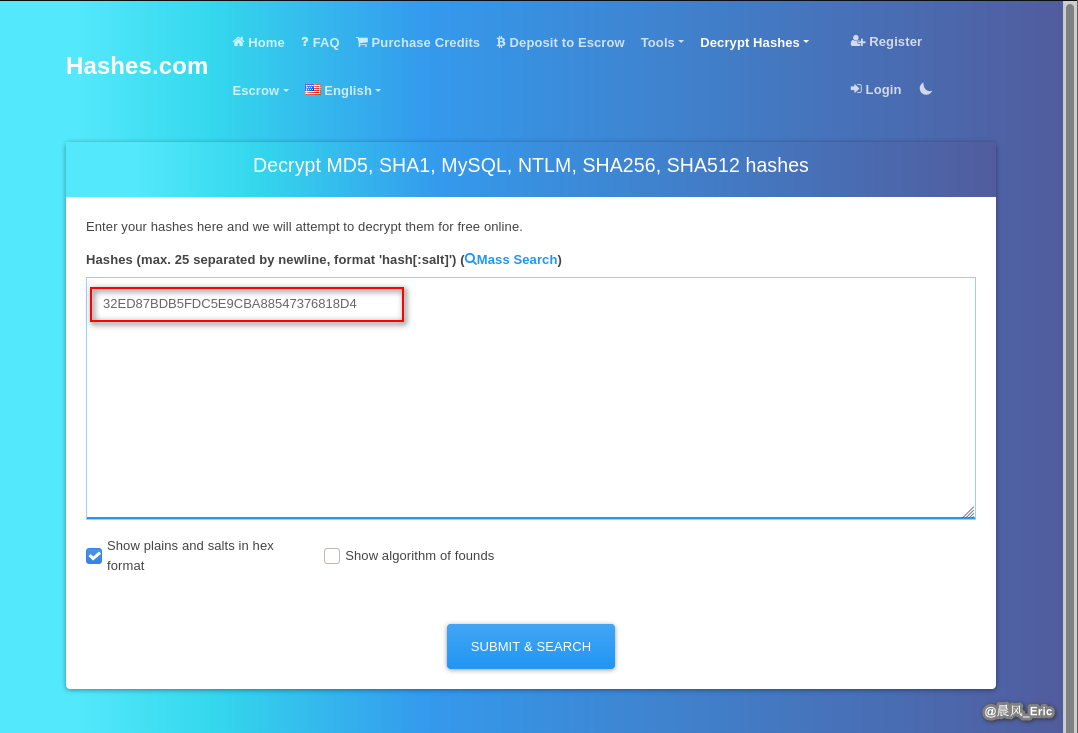
Online hash cracker
HashKiller:
https://hashes.com/en/decrypt/hash
Crack station:
Submit the Hashes.(NTLM Cracker)
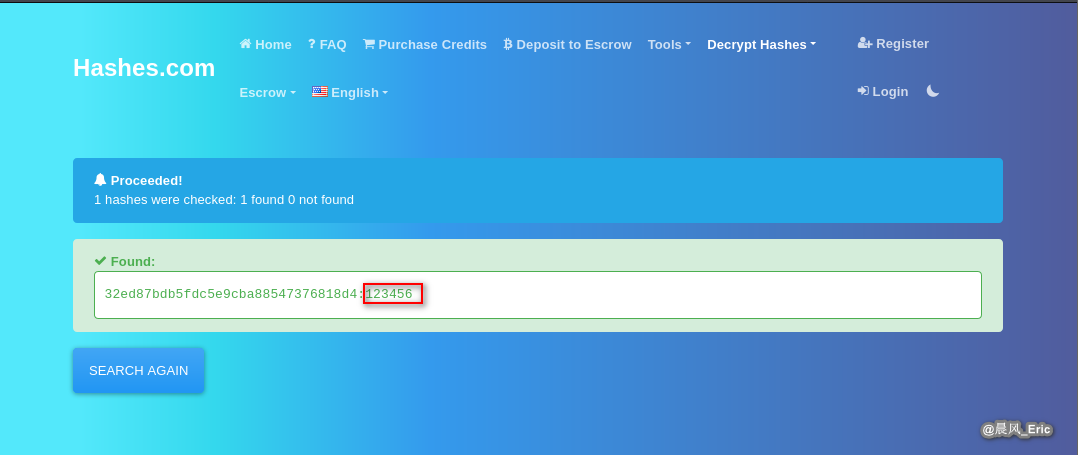
Get result. (Plaint password text)
Unshadow Linux password
unshadow passwd shadow > unshadow
john --rules --wordlist=/usr/share/wordlists/rockyou.txt unshadow
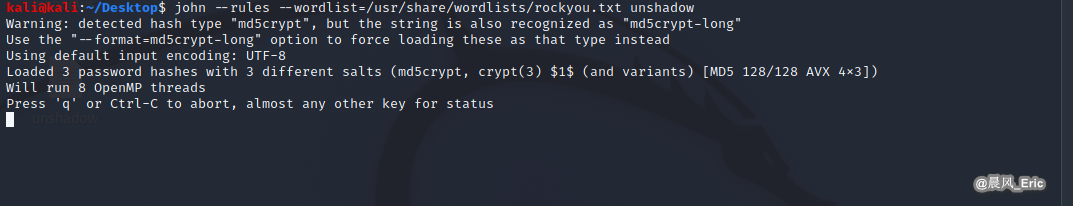
It's too slow, let us try hashcat...
hashcat -m 500 /usr/share/wordlists/rockyou.txt unshadow --force
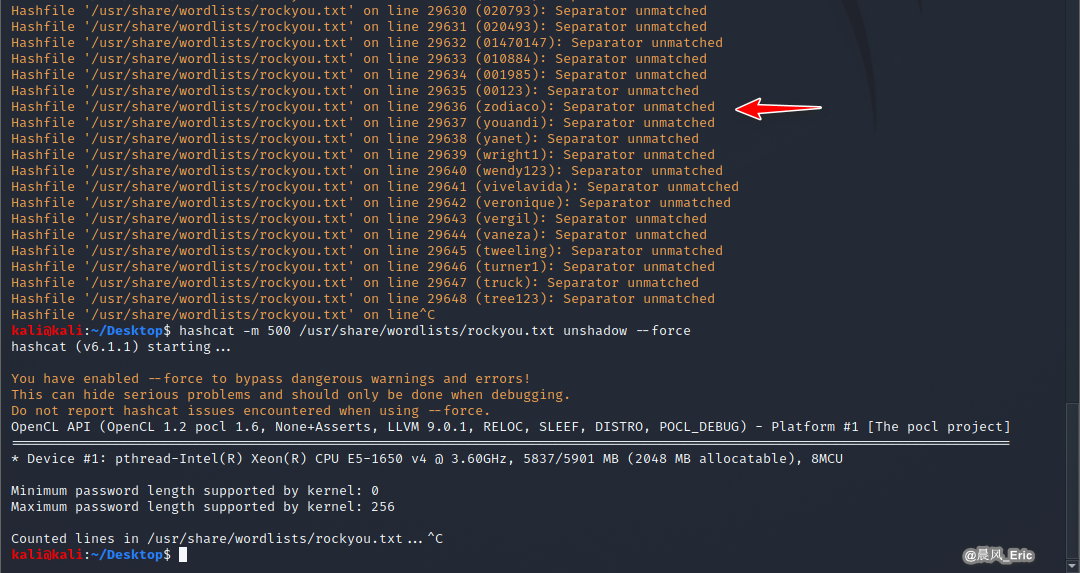
VM OS is not good to crack password...
Hashcat - Advanced password recovery
Download and unzip hashhack on windows. And try to get rockyou.txt and unshadow files here.
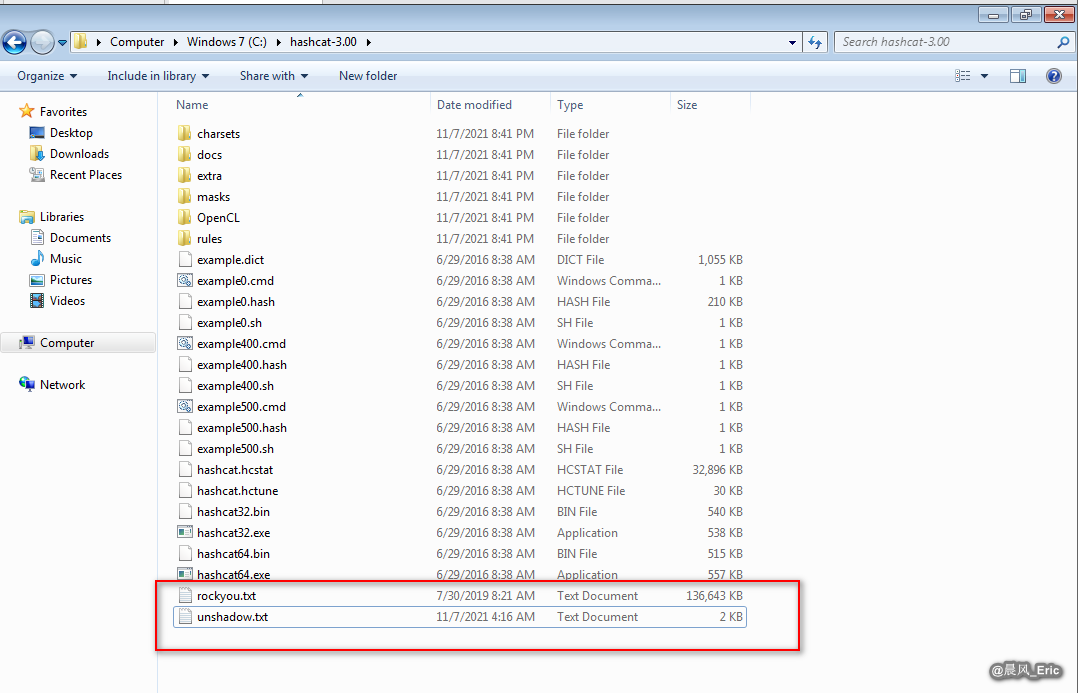
hashcat64.exe -m 500 unshadow.txt rockyou.txt
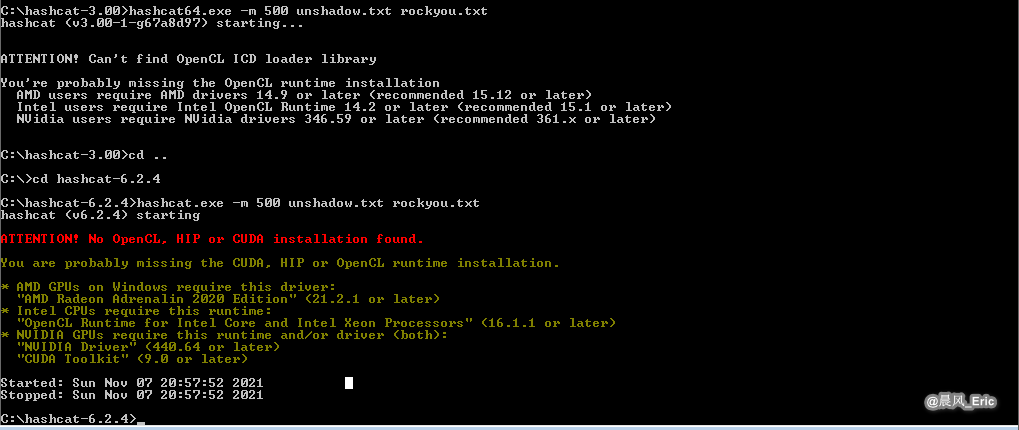
Can not run it on VM, so let try it on physical computer.
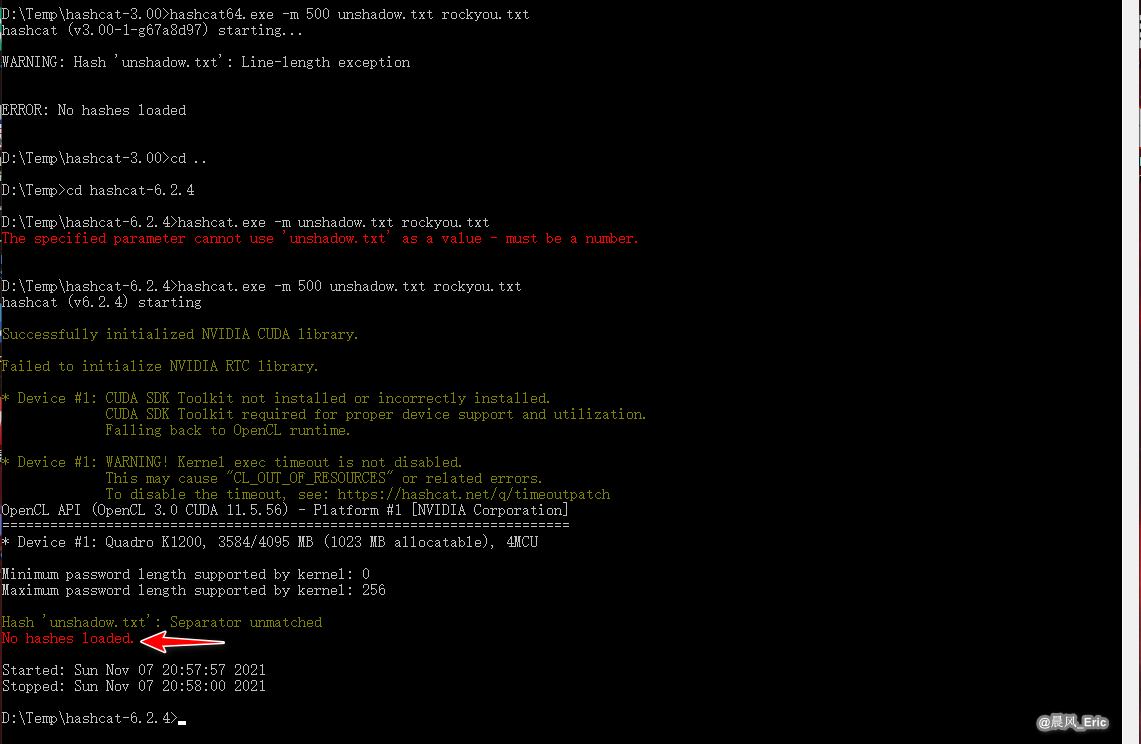
We got the result - No hashes loaded finally.
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号