Security and Cryptography in Python - Hash Functions(1)
Security and Cryptography in Python - Hash Functions(1)
Properties of a Hash Function
- It is an one-way deterministic function
- The output is dependent on all input bits
- Output is uniformly distributed
- "Impossible" (difficult) make a collision
Use of Hash Functions
- Digital signature
- Shadow files (passwords)
- HMAC
- Make deterministic identifiers
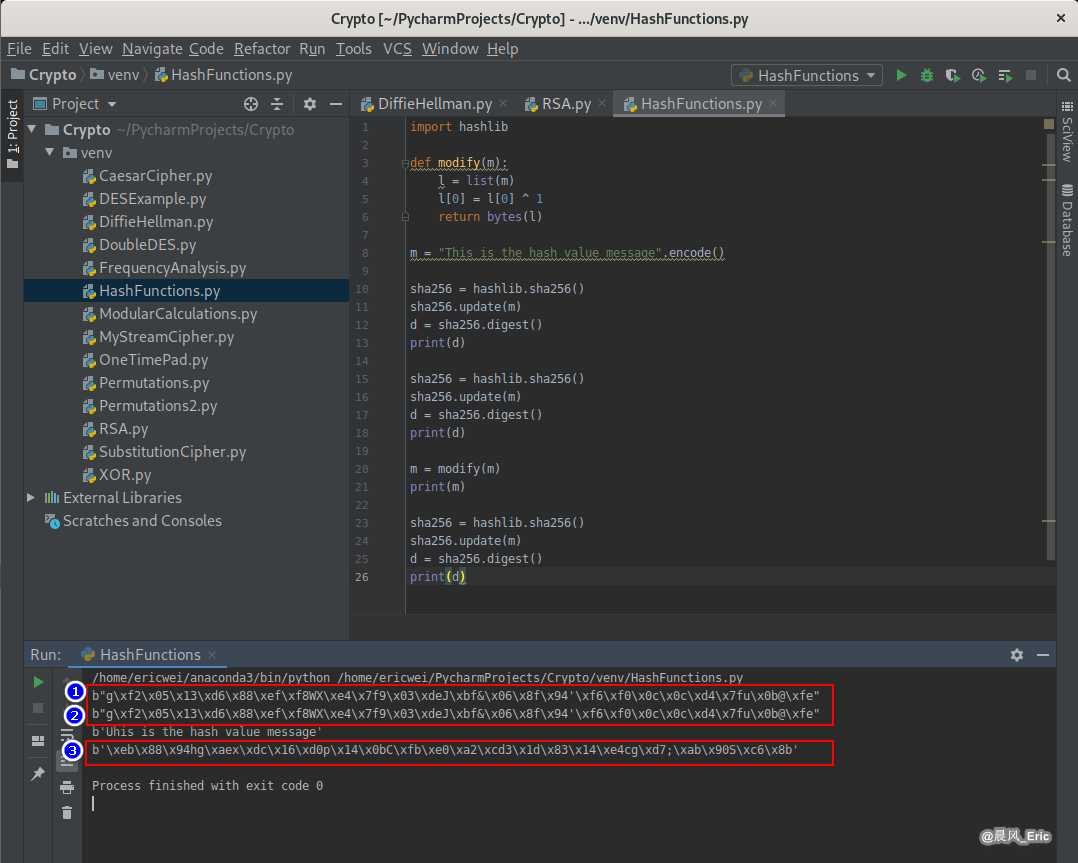
Code in Python:
import hashlib
def modify(m):
l = list(m)
l[0] = l[0] ^ 1
return bytes(l)
m = "This is the hash value message".encode()
sha256 = hashlib.sha256()
sha256.update(m)
d = sha256.digest()
print(d)
sha256 = hashlib.sha256()
sha256.update(m)
d = sha256.digest()
print(d)
m = modify(m)
print(m)
sha256 = hashlib.sha256()
sha256.update(m)
d = sha256.digest()
print(d)
Running Result:
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号