Penetration Test - Select Your Attacks(16)
Miscellaneous privilege escalation
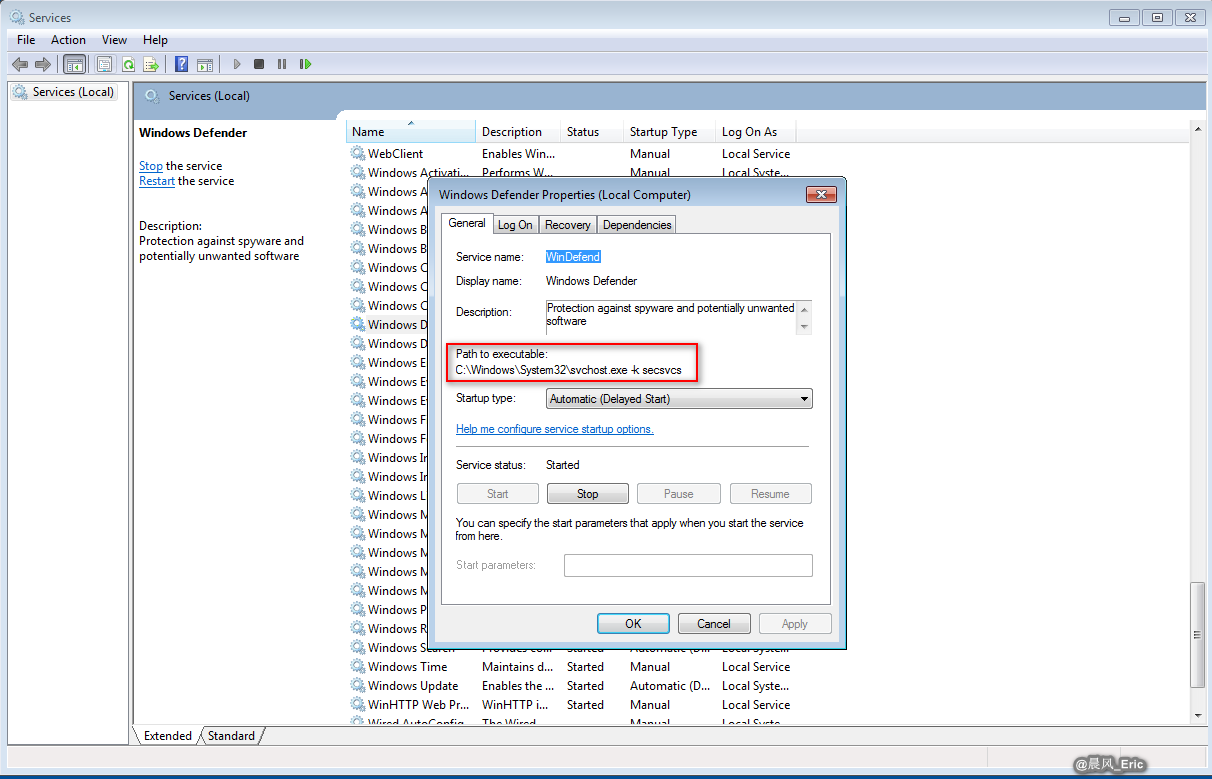
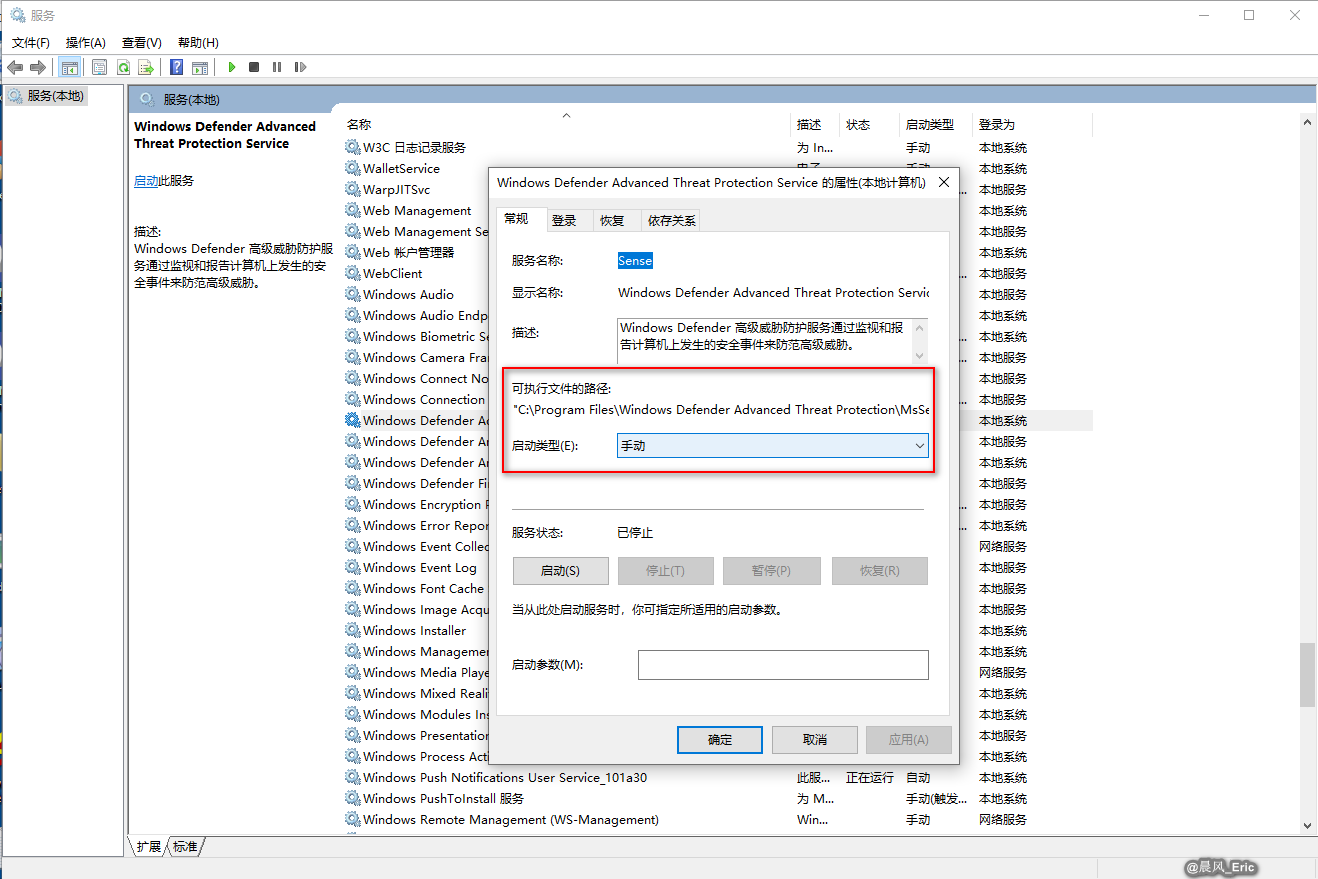
EXPLOITABLE SERVICES
- Unquoted service paths
- Allow abbreviated attack paths(without spaces)
PRIVILEGE ESCALATION
- Unsecure file/folder permissions - root installs allow read/write by any user
- Keylogger
- Records every keystroke
- Scheduled tasks
- Attacker may add new task to run persistently with elevated privileges
- Kernel exploits
- Unpatched systems are vulnerable
QUICK REVIEW
- Unquoted service paths and writable services can allow for service exploits.
- Look for files and folders that allow excessive read/write permissions
- Footprinting can provide information on kernel vulnerabilities
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号