aardio爬虫) 实战篇:逆向有道翻译web接口
前言
之前的文章把js引擎(aardio封装库) 微软开源的js引擎(ChakraCore))写好了,这篇文章整点js代码来测一下bug。测试网站:https://fanyi.youdao.com/index.html#/
逆向思路
逆向思路可以看有道翻译js逆向(MD5加密,AES加密)附完整源码,逆向我就不赘述了。这篇文章说一下怎么将文章中给的Python代码翻译成aardio调用和扣js代码用ChakraCore调用。
扣js代码
有道翻译的js是webpack,扣webpack主要有两个内容,一个是加载器函数,还有就是实际调用的函数。这个可以去看b站志远一期的内容,讲的很详细。
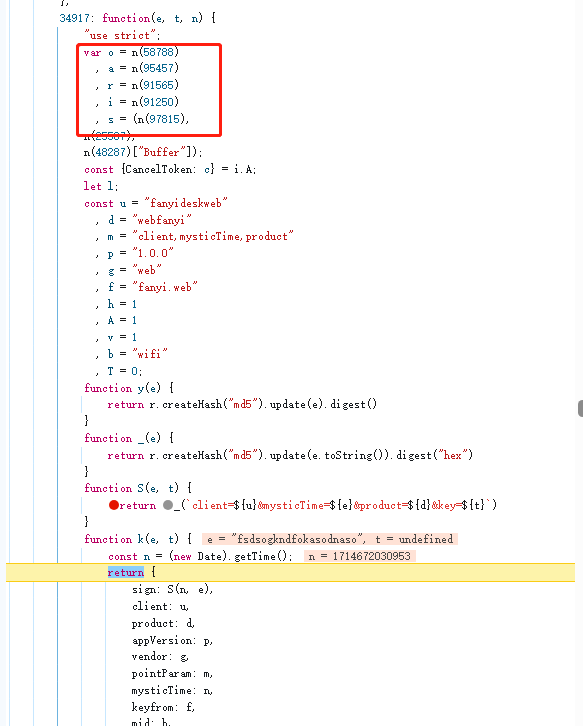
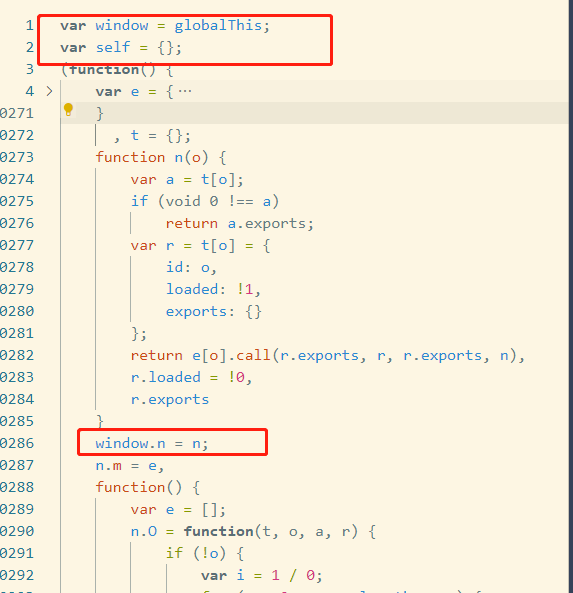
这个我看了下,把整个js放到nodejs里执行就行,不需要扣函数,函数和函数之间关联太多了,扣反而不方便。上面补个window,然后导出成全局函数。
91565这个函数在另一个js文件里,把整个大对象拿下来和e合并一下。
然后就可以直接调用
var r = n(91565)
console.log(r.createHash("md5").update("11111111").digest("hex"))
再封装两个函数给外部调用:
function md5(content){
let r = n(91565);
return r.createHash("md5").update(content).digest("hex");
};
function aes_cbc_decrypt(key, iv, content){
let r = n(91565);
let o = r.createHash("md5").update(key).digest();
let a = r.createHash("md5").update(iv).digest() ;
let i = r.createDecipheriv("aes-128-cbc", o, a);
let c = i.update(content, "base64", "utf-8");
return c += i.final("utf-8");
};
测试了封装的ChakraCore库,有个莫名其妙的bug:如果不在js里调用这两个函数,那你再aardio使用run或者callFunction调用可能会报错,测试了半天也没找到具体原因,主要是ChakraCore的文档有点少。
没办法,目前只能在javaScript里先调用一次,这个bug后面看看能不能解决
var decodeiv = "ydsecret://query/iv/C@lZe2YzHtZ2CYgaXKSVfsb7Y4QWHjITPPZ0nQp87fBeJ!Iv6v^6fvi2WN@bYpJ4";
var decodekey = "ydsecret://query/key/B*RGygVywfNBwpmBaZg*WT7SIOUP2T0C9WHMZN39j^DAdaZhAnxvGcCY6VYFwnHl";
var text = "";
// 需要先在js里调用一次,不然aardio调用报错
md5("1111")
aes_cbc_decrypt(decodekey, decodeiv, text)
用ChakraCore调用的完整代码(js文件我放到了aardio-extlibs那个github仓库里作为ChakraCore的用例):
import console;
import kirequests;
import ChakraCore;
io.open()
var core = ChakraCore()
core.start()
core.run(string.load("./有道翻译.js"))
var client = "fanyideskweb";
var product = "webfanyi";
var key = "fsdsogkndfokasodnaso";
var signStr = `client=%s&mysticTime=%s&product=%s&key=%s`;
// 先请求主页获取cookie
var session = kirequests.session();
var url = "https://fanyi.youdao.com/index.html"
var resp = session.get(url);
// 要翻译的内容
var word = "中国";
// 内容是什么语言
var from = "auto";
// 想翻译成什么语言
var to = "";
var webtranslateApi = "https://dict.youdao.com/webtranslate";
var timestamp = tostring(tonumber(time())) + string.random(3,"1234567890");
var postData = {
"i": word,
"from": from,
"to": to,
"domain": "0",
"dictResult": "true",
"keyid": product,
"client": client,
"product": product,
"appVersion": "1.0.0",
"vendor": "web",
"pointParam": "client,mysticTime,product",
"mysticTime": timestamp,
"keyfrom": "fanyi.web",
"mid": "1",
"screen": "1",
"model": "1",
"network": "wifi",
"abtest": "0",
"yduuid": "abcdefg"
}
var s = string.format(signStr, client,timestamp,product,key)
postData["sign"] = core.callFunction("window.md5",s);
var resp = session.post(url=webtranslateApi,data=postData);
// 开始解密
var decodeiv = "ydsecret://query/iv/C@lZe2YzHtZ2CYgaXKSVfsb7Y4QWHjITPPZ0nQp87fBeJ!Iv6v^6fvi2WN@bYpJ4";
var decodekey = "ydsecret://query/key/B*RGygVywfNBwpmBaZg*WT7SIOUP2T0C9WHMZN39j^DAdaZhAnxvGcCY6VYFwnHl";
var result = core.callFunction("window.aes_cbc_decrypt", decodekey, decodeiv,resp.text)
console.log(result)
console.pause(true);
aardio实现
这里在给个不用ChakraCore用上篇文章写的aes库调用的代码。
import console;
import kirequests;
import kicrypt.aes;
import crypt;
import crypt.bin;
var client = "fanyideskweb";
var product = "webfanyi";
var key = "fsdsogkndfokasodnaso";
var signStr = `client=%s&mysticTime=%s&product=%s&key=%s`;
// 先请求主页获取cookie
var session = kirequests.session();
var url = "https://fanyi.youdao.com/index.html"
var resp = session.get(url);
// 要翻译的内容
var word = "hello";
// 内容是什么语言
var from = "auto";
// 想翻译成什么语言
var to = "";
var webtranslateApi = "https://dict.youdao.com/webtranslate";
var timestamp = tostring(tonumber(time())) + string.random(3,"1234567890");
var postData = {
"i": word,
"from": from,
"to": to,
"domain": "0",
"dictResult": "true",
"keyid": product,
"client": client,
"product": product,
"appVersion": "1.0.0",
"vendor": "web",
"pointParam": "client,mysticTime,product",
"mysticTime": timestamp,
"keyfrom": "fanyi.web",
"mid": "1",
"screen": "1",
"model": "1",
"network": "wifi",
"abtest": "0",
"yduuid": "abcdefg"
}
postData["sign"] = crypt.md5(string.format(signStr, client,timestamp,product,key),false);
var resp = session.post(url=webtranslateApi,data=postData);
// 开始解密
var decodeiv = "ydsecret://query/iv/C@lZe2YzHtZ2CYgaXKSVfsb7Y4QWHjITPPZ0nQp87fBeJ!Iv6v^6fvi2WN@bYpJ4";
var decodekey = "ydsecret://query/key/B*RGygVywfNBwpmBaZg*WT7SIOUP2T0C9WHMZN39j^DAdaZhAnxvGcCY6VYFwnHl";
var key = string.unhex(crypt.md5(decodekey,false),"")
var iv = string.unhex(crypt.md5(decodeiv,false),"")
var aesObj = kicrypt.aes(key, iv);
var data = crypt.bin.decodeUrlBase64(resp.text)
var result = aesObj.decrypt(data, kicrypt.aes.CBC)
console.log(result)
console.pause(true);
本文由博客一文多发平台 OpenWrite 发布!





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY